Warehouse security
SharpEagle has been recognized as a key player in the global forklift 360-degree camera market, highlighted in the recent Forklift 360-Degree Camera Global Market Report by The Business Research Company. SharpEagle's advanced Bird's-Eye View Camera System leverages AI-powered stitching technology to deliver seamless 360-degree panoramic views around forklifts. This innovative solution enhances industrial safety by minimizing blind spots, improving situational awareness, and reducing accident ri...
WAGNER Group GmbH has been awarded the GIT SECURITY AWARD 2026 in the "Fire protection" category. The award was given for the innovative OxyReduct F-Line oxygen reduction system, which actively prevents the outbreak of open fires under defined conditions. The system expands on the proven method of oxygen reduction with hydrogen-based fuel cell technology, which also enables an emission-free energy supply. The key advancement lies in the combination of a protective atmosphere and a self-suf...
SharpEagle Technology, a globally recognized pioneer in industrial safety solutions, now reinforced its standing as a premier provider of overhead crane safety lighting systems, with a deep understanding of the unique challenges faced by industries utilizing overhead cranes. SharpEagle delivers not just products, but comprehensive solutions designed to elevate safety standards, optimize workflows, and instill confidence in demanding operational environments. SharpEagle's Overhead Crane Safety...
SharpEagle Technology has been recognized for the “Machine Learning/AI Project of the Year” at the 2025 Digital Technology Leaders Awards. This recognition highlights the company’s innovative use of AI to enhance safety and efficiency across industries, positioning it among the pioneering tech innovators of the year. SharpEagle’s great achievements SharpEagle has earned its place among the industry’s most forward-thinking technology pioneers UK, Middlesex, July...
DNAKE, a provider of home and building video intercom systems and communications solutions, has officially opened its first US office in downtown Los Angeles. The establishment of this office opens a new chapter for the company as both a strategic upgrade for DNAKE's global expansion and its ability to better serve customers in the important North American market. Los Angeles will now serve as a critical hub for the company's global operations with the new office serving as a bridge betwe...
iDenfy, a US-based fraud prevention and identity verification company best known for its AI-powered RegTech automation solutions, partners with Reppublika Data Analytics & Technologies, a pioneer European software firm providing innovative SaaS solutions to the market research industry. iDenfy’s identity verification software will help the business verify all customers who are conducting surveys online while detecting fraudulent users with fake personal details or other renderings, of...
News
nShift, the pioneer in parcel delivery management software, announces the launch of Emissions Tracker. Calculating the CO2 emissions associated with each shipment, the new solution makes it possible for e-commerce and multichannel retailers to comply with sustainability disclosure rules, prove environmental credentials to customers, and see where they can reduce emissions from shipping. Emissions Tracker data helps retailers comply with emissions reporting rules, including the EU Corporate Sustainability Reporting Directive (CSRD) coming into force in mid-2024. The new regulation is expected to affect around 50,000 businesses trading in the EU, which will become subject to mandatory sustainability reporting. Customers prefer to shop sustainably Emissions Tracker makes it easy to generate detailed, actionable sustainability reports 81% of shoppers want to buy from brands that demonstrate sustainability. However, as many as 40% of consumers are distrustful of brands' environmental claims. Emissions Tracker provides clear, trustworthy data that helps retailers clearly demonstrate their improvement. Mattias Gredenhag, CTO at nShift said, "Pressure from customers and regulators alike means having a clear picture of their emissions is a necessity for retailers today. Emissions Tracker makes it easy to generate detailed, actionable sustainability reports. This simplifies the compliance burden and saves time for CFOs and other stakeholders doing annual reporting. What is more, retailers can use Emissions Tracker insights to engage customers in their sustainability story and accelerate their progress to net zero." Benefits for retailers and warehouses All carrier data is collated into one reporting tool and built into an easy-to-use template nShift Emissions Tracker has been designed to simplify the process of emissions reporting. All carrier data is collated into one reporting tool and built into an easy-to-use template. Calculations are done at the shipment level, giving retailers the ability to drill into shipping data, compile accurate reports, and identify quick wins for emissions reduction. For retailers already using nShift's delivery management, Emissions Tracker provides access to emissions data for all historical shipments, so they can make comparisons with previous months and years. Additional benefits of Emissions Tracker nShift Emissions Tracker brings the following additional benefits: Efficiency: Quickly and easily report on last-mile and transport emissions at the click of a button with no additional analysis needed Reliability: Emissions data the business can depend on. All collected in one place in a standardized format Credibility: Peace of mind knowing the calculations are accurate and free from mistakes of manual error. The solution uses standard tariffs developed by the Network for Transport Measures (NTM) Accuracy: Emissions data are calculated based on CO2e (carbon dioxide equivalent–a more accurate and comprehensive measure than CO2 alone) Transparency: Increase customer loyalty and brand recognition by becoming trusted and transparent when it comes to emissions GLEC Framework Gredenhag concluded, "We believe greener deliveries drive better business growth. Alongside tracking and managing emissions, we help retailers offer sustainable delivery options, provide offset schemes and charitable giving through deliveries, and clearly badge sustainable delivery options at checkout." nShift Emissions Tracker conforms to internationally recognized standards, including ISO 14083 and the Global Logistics Emissions Council (GLEC) Framework.
From 10 to 13 October, the global airport community will gather for the 24th edition of inter airport Europe at the Munich Trade Fair Centre in Germany. The event returns with an impressive line-up of well over 400 airport suppliers from 37 countries, including seven national pavilions and more than 100 new exhibitors. Live exhibits Visitors can look forward to plenty of live exhibits in the halls and Outdoor Area and a new 600 square meter GSE Experience Area. An exciting event program including Technical Seminars, Innovation Awards, and the co-located inter airport FOCUS, The Sustainability Summit provides interesting opportunities to further engage with new technologies and suppliers, all dedicated to improving airport performance while delivering a return on investment. New economic importance inter airport Europe has developed into the most senior gathering of global airport operators, airlines, CAAs, service suppliers The Munich Trade Fair Centre will once again turn into the world’s biggest hub for exploring and sourcing new technology, equipment, and services for better airports. Over nearly 50 years, inter airport Europe has developed into the most senior gathering of global airport operators, airlines, CAAs, service suppliers, investors, and other experts in this sector. The upcoming event marks another milestone for the airport industry which is currently rising to new economic importance with a multitude of opportunities and challenges. Airport professionals Airport professionals from more than 100 countries have already registered as visitors, including key representatives from AENA, Air France, Deutsche Lufthansa, Fraport AG, Heathrow Airport, İGA Istanbul Airport, Oman Airports, Shell Aviation, WISAG, and many more. Over four exhibition days, they can explore an excellent cross-section of technologies and services for the entire airport supply chain, including airside operations, terminal management, passenger services, baggage handling, safety and security, airport IT, air traffic control, airport maintenance, and environmental management. Insights into technology innovations Networking and knowledge platform on how to develop, embed, and integrate sustainability strategies An impressive program of accompanying events offers additional insights into technology innovations about wider market trends. These include Technical Seminars, Innovation Insight Sessions, the prestigious Innovation Awards, and the co-located inter airport FOCUS Sustainability Summit, a two-day, high-profile networking and knowledge platform on how to develop, embed, and integrate sustainability strategies into every aspect of airport life. Roadmap to airport operations “Co-locating exhibition and summit is an exciting opportunity for us to provide more value to the global airport community. Both events naturally complement each other, providing attendees with a great roadmap to future-proof their airport operations,” says Olaf Freier, Portfolio Director Transport of inter airport Europe, on behalf of show organizer RX. “The co-location offers new and encouraging perspectives that will help pave the way for innovation, resilience, and sustainability at future airports.” inter airport Europe at a glance: Indoor and outdoor stands with live equipment Over 30% of exhibitors are newcomers on the inter airport show floor, forming an impressive line-up A large show floor in halls B5, and B6, and the adjacent outdoor area invite visitors to discover more than 400 suppliers who deliver advanced airport equipment, technology, and services across the globe. The top five exhibitor countries are Germany, Italy, the United Kingdom, France, and the Netherlands, with 37 countries represented in total. Over 30% of exhibitors are newcomers on the inter airport show floor, forming an impressive line-up of well-known international brands alongside promising startups and scaleups. A new 600 square meter GSE Experience Area, sponsored by Weihai Guangtai Airport Equipment, will offer visitors the opportunity to see the latest equipment for aprons and runways live and in action. National Pavilions and First-time Exhibitors Several National Pavilions will feature this year – Italy, France, the UK, the Netherlands, Finland, and newcomer Spain, all showcasing some of their countries’ finest tech companies and products. Long-term show partner GATE (The Airport Technology Network) will be hosting a number of its members at their dedicated GATE Pavilion again. In addition, there will be two First-time Exhibitor pavilions specifically dedicated to companies new to inter airport Europe. Opening and Innovations Awards Ceremony The spotlight on best practices, technologies, and partnerships that drive innovation and excellence The inter airport Europe Innovation Awards celebrate the achievements of the many inventors and technical pioneers within the exhibitor community, putting the spotlight on best practices, technologies, and partnerships that drive innovation and excellence for better airports. The winners will be announced at the Opening and Innovation Awards Ceremony on Tuesday, 10th October, 11:00 - 12:00, at the Seminar Theatre in Hall B5. Welcoming presentations include speeches from Nicola Hamann, Managing Director at RX, Kay Bärenfänger, President at GATE Alliance, and Jost Lammers, CEO at Munich Airport. Seminar Programme: Three days of expert talks The free-to-attend inter airport Europe Seminar features a selection of technical talks on pioneering solutions and approaches to pressing airport issues, including the Innovation Insight Sessions featuring participants of the Innovation Awards. The 15-to-30-minute sessions will touch on key aspects of the passenger experience and passenger journey, baggage handling, security systems, as well as ramp and terminal management. The technical seminars will run between 10 - 12 October at the Seminar Theatre in Hall B5, stand B5-1580. Visit the show website for the full seminar agenda. inter airport FOCUS – The Sustainability Summit The Sustainability Summit offers two days of top-tier education, networking, and collaboration opportunities The co-located inter airport FOCUS – The Sustainability Summit offers two days of top-tier education, networking, and collaboration opportunities for aviation stakeholders looking to develop, discuss, or initiate sustainability measures required to reach their net zero commitments, including sustainable airport operations, net-zero infrastructure, and new mobility concepts. inter airport FOCUS takes place on 11 and 12 October at the Press Centre East Entrance (Rooms 1A, 1B, 2). The Summit tickets can be purchased online or on-site and also include free entry to the inter airport Europe exhibition and seminars. For the full summit program, please visit inter airport FOCUS. Visitor tools, Matchmaking Visitors are invited to use the Exhibitor List Tool and Online Show Preview to search for products and companies that are of particular interest to them. Once registered, visitors have access to the inter airport Europe Matchmaking Platform, allowing them to send or receive meeting invitations based on their business requirements. Meetings can be arranged at the exhibitor’s stand or in the dedicated meeting lounge in Hall B6, stand B6-590. Hosted Buyer Programme The Hosted Buyer Programme offers a tailored networking experience with industry pioneers The Hosted Buyer Programme offers a tailored networking experience with industry pioneers from airfield construction, ground handling, ground support equipment, interior design, hardware and software solutions, terminal infrastructure, and operations in the 2023 group. It focuses on growing markets and emerging regions, with buyers from UAE, India, Kenya, South Africa, Saudi Arabia, and Ghana, and it is an excellent opportunity to open up new markets for exhibitors. Venue, tickets, and opening times inter airport Europe 2023, the 24th International Exhibition for Airport Equipment, Technology, Design, and Services, takes place in halls B5, B6, and the adjacent outdoor area at the Munich Trade Fair Centre in Germany. Access to the exhibition halls is via Entrance East. Please visit the Online Travel Hub for further information on transport, accommodation, and visa. Show opening hours are from 9:00 AM to 5:00 PM on Tuesday, Wednesday, and Thursday (10 to 12 October), and from 9:00 AM to 3:00 PM on Friday (13 October). Visitors can register via the Online Ticket Shop and benefit from a reduced price when purchasing their ticket in advance. Day tickets cost €42 online or €52 on-site; season tickets cost €62 online or €72 on-site.
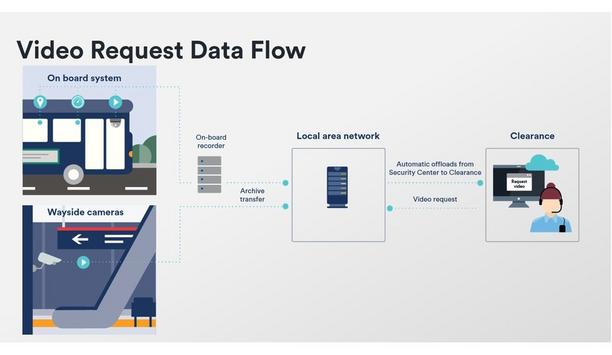
Genetec Inc., a pioneering technology provider of unified security, public safety, operations, and business intelligence solutions, announced that its Genetec Clearance™ digital evidence management system now enables the remote retrieval of video recordings from physical security systems across transit agency sites and fleets to help speed up investigations. The capability is enabled by the integration of Clearance with the Genetec Security Center Fleet Monitoring™ module. Using a browser-based system, agencies can now link all their on-board and landside data into a unified solution to manage evidence and streamline the sharing of recordings with internal departments and external partners. Genetec Clearance These requests are still often delivered on physical media, adding to the cost and delay of the process Transit security teams devote considerable time and resources to assist with requests from their legal and claims departments, law enforcement agencies, and parties that require access to video recordings captured by their camera systems. These requests are still often delivered on physical media, adding to the cost and delay of the process. Genetec Clearance eliminates the time-consuming, costly process of dispatching transit personnel to vehicles and stations, transferring video to external drives, and delivering it to requesting parties. All requests are centrally and securely tracked within Clearance and go through the agency’s approval process to ensure they are aligned with governance policies before the video is shared. On-board systems Internal departments and external parties order recordings from station cameras From a web browser, internal departments and external parties can now request recordings from station cameras and on-board systems, and review video from the same application. Exports from on-board systems include vehicle telematic data, which can be reviewed alongside video uploads. This data, such as vehicle speed, brake, and turn signal activation, can be shared with attorneys and other authorized parties, helping to assess a scene and provide further analysis of events. “Transit security teams have the complex duty of managing highly distributed operations to ensure the safety of commuters and transit employees day in and day out,” said Erick Ceresato Product Group Director, Genetec Inc. Genetec Clearance integration Erick Ceresato added, “By automating the steps involved to fulfill video requests, and reducing the time it takes to deliver video evidence to reviewers, Genetec solutions free up security teams to focus on mission-critical activities. Having a unified security environment across stations and vehicle fleets opens the door to this kind of efficiency and removes bottlenecks that have traditionally impeded access to this data.” The Genetec Clearance integration with the Fleet Monitoring module will be available in October 2023 and is being showcased at the APTA Expo at the Genetec booth #3510.
ISS (Intelligent Security Systems), a global provider of video intelligence and data awareness solutions, announced that industry veterans Dennis Connor and Jason Lloyd have joined the company as its new Director of Program Management NA and Regional Business Manager for the Midwest respectively. Dennis Connor's responsibilities Connor, who most recently served as Program/Project Manager for CX (customer experience) Initiatives at ADT, will spearhead the development of new end-user and partner deployment methodologies for ISS. He will simultaneously work with the company’s sales, engineering, manufacturing, and R&D teams to create and foster other customer engagement programs. Work experience Connor has an extensive background in similar initiatives throughout his time in the security industry, beginning in the early 2000s as Program Manager, Returns and Repairs Operations, at Tyco International. He would go on to work at the company in various leadership positions for the next 14 years, overseeing its transition from a Bermuda-domiciled organization with a U.S. headquarters in New Jersey to being a Swiss-based company. AI-powered video analytics ISS is in a tremendous position to take advantage of the third wave of video surveillance innovation" “As the preeminent developer of AI-powered video analytics globally, ISS is in a tremendous position to take advantage of the third wave of video surveillance innovation the industry currently finds itself in,” said Connor. “I have a lot of operational experience to bring to the table and ISS, in a sense, represents just a larger version of what I have gone through in the past establishing program management initiatives at other firms.” Jason Lloyd's responsibilities Lloyd, who most recently served as Regional Sales Manager at Vicon, will be responsible for driving the sales and business development efforts for ISS across the Midwest. Prior to Vicon, Lloyd headed up a low-voltage division at ADT for just over a decade. High-trust video intelligence solutions My goal is to exceed customer expectations and demonstrate how they can leverage our neural network technology" “Being laser-focused on customer service and providing high-trust video intelligence solutions that are solving actual security and business challenges today was one of the factors that most appealed to me about ISS,” said Lloyd. “My goal is to exceed customer expectations and demonstrate how they can leverage our industry-pioneering neural network technology to keep their businesses safe.” Matt comments “ISS is experiencing incredible growth, not only in North America, but globally, and bringing in experienced team members will be critical to our continued growth,” explained Matt Powell, Managing Director for North America at ISS. “With Jason, we gain a well-respected face, and voice of our partners, in the Midwest. And in Dennis, we gain an experienced program manager who will ensure that we speak the language of success to our integration partners and customers alike." Integration in the value chain The experience of both Jason and Dennis shows that we are dedicated to a new approach to the North American market" "Solution creators must strive to do a better job of speaking ‘integration’ to our integrators, pulling them into the value chain instead of pushing them out." "That begins with the relationships we build and our value propositions to our partners and customers. The experience of both Jason and Dennis show that we are dedicated to a new approach to the North American market and continued growth of ISS.” Education Connor, who has a degree in industrial engineering from Virginia Polytechnic Institute and State University and is also Six Sigma/Lean DMAIC Master Black Belt and Scrum Master certified, resides in Orlando. Lloyd, PSP, PMP, who is based in Chicago and holds Lenel Master and Genetec certifications.
The Security Industry Association (SIA) has launched a new learning management system (LMS) – SIAcademy as part of its efforts to advance industry professionalism through premier education and training. SIAcademy SIAcademy is a living library of on-demand training and professional development programs designed to enhance security professionals’ industry knowledge, technical skills, and overall job performance. The new LMS offers a modern, simple, and centralized place to access role-based training, certification prep materials, and other relevant educational content anytime, anywhere, and on any device. Dynamic learning tools It offers immense growth opportunities for those who prioritize their professional development" “The launch of the SIAcademy learning management system and course catalog is a milestone within SIA and for the security industry,” said Dr. Elli Reges, SIA’s director of learning and development. “This robust new platform offers dynamic learning tools to help learners and employers harness and unleash individual performance potential through customizable learning pathways and strategic investments in human capital, and it offers immense growth opportunity for those who prioritize their professional development.” Features of the LMS SIAcademy, powered by the cloud, delivers on-demand e-learning offerings and live online courses. Features of the new system include: Easy accessibility and a mobile-friendly interface. Interactive engagement tools and gamification. Continuing education credits. When accessing SIAcademy, members can find content such as: SIA’s Security Project Management (SPM) training. SIA’s Security Cornerstones series is designed for new employee onboarding. A microlearning series created to propel young professionals’ knowledge and growth. A training course on the federal grants life cycle and security-related grant programs. On-demand SIAcademy LIVE! courses on video security, access control, sales, and more. Materials and guidelines to help members prepare for the Security Industry Cybersecurity Certification (SICC) exam. Key learning objections SIA member companies will be able to create their customizable microsites “I think learners will be very pleased with the new capabilities of SIAcademy! It allows us to facilitate more engagement through discussion boards and other features and reinforce key learning objectives with interactive gamification tools,” said DeAndre Thornton, SIA’s manager of learning and development. Through SIAcademy’s microsite capability, which SIA plans to make available shortly, SIA member companies will be able to create their customizable microsites, on which they can build their own content and license content from SIA’s LMS to develop learning plans for their teams, partners and/or clients. SST Apprenticeship program SIA’s new Security Systems Technician (SST) Apprenticeship program, using the SIAcademy microsite capability, will provide participating employers with access to more than 100 hours of curated e-learning content. SIA members are invited to contribute educational course content that is product-agnostic and vendor-neutral to support apprentice knowledge and skill development in designated competency areas.
According to the U.S. Occupational Safety and Health Administration (“OSHA”), hospitals are considered one of the most dangerous places to work in America. In fact, OSHA describes hospitals as generally “hazardous” places to work, contributing to missed days of work and adding to the high cost of healthcare. In 2019, OSHA reported, “U.S. hospitals recorded 221,400 work-related injuries and illnesses, a rate of 5.5 work-related injuries and illnesses for every 100 full-time employees. This is almost twice the rate for private industry as a whole.” Nursing assistants were among the occupations with the highest rates of musculoskeletal disorders of all occupations in 2020, with 15,360 cases. Musculoskeletal disorders comprised 52% of all days away from work cases for nursing assistants. Additionally, hospitals are more hazardous than the generally dangerous construction and manufacturing industries. Healthcare worker shortages The perception of hospital safety in the workforce has also declined beginning in 2020, as the COVID-19 pandemic placed tremendous pressure on the healthcare system due in part to workforce fatigue and healthcare worker shortages, which lead in part to poor patient outcomes. The perception of hospital safety in the workforce has also declined beginning in 2020 The patient caregiving workforce also has a stressful, unpredictable work environment and a “do no harm” culture that may require repeated overexertion, lifting, transferring, and repositioning of patients; may result in accidents like needlesticks and medicine errors; and may give rise to other concerns like co-worker, patient, or visitor violence. Such workplace stressors may also lead to fatigue, sick days, patient care errors, and poor infection control. OSHA reports Likewise, OSHA reports hospital workplace tasks such as manual lifting impacts safety in at least two ways: when job tasks such as manual lifting can injure caregivers, and when such tasks risk or result in unintended falls, fractures, bruises, and skin tears to patients. Video surveillance is core to the healthcare facility's health and safety High-performing healthcare facilities combine the management of patient safety risks right along with worker safety risks when assessing the core elements of a safety and health management system. Video management software (VMS) for video surveillance is a highly-valued tool in the safety and health management system toolbox. Video technology is available for broad use by leadership for the following reasons: Video provides indicators of quality and quantity. HR can review workforce performance by medical staff. Legal, compliance, and audit teams can investigate alleged violations or resolve disputes. Workplace trainers can offer real-life examples and testimonials used in training. Risk managers can predict, identify, and assess risk. Supervisors can proactively prevent or reduce occurrences of various hazardous incidents. For example, the incident investigation may be enhanced with a video management system that offers recorded video archives for evidentiary preservation and retention, supporting root cause analysis and supporting analysis of legal risk. These video archives are also useful to the whole team when considering post-incident “lessons learned” and training. XProtect® VMS Video surveillance may also serve as a deterrent to internal and external thefts including, for example: when workforce members know active surveillance is in place in drug dispensing rooms or sensitive records areas, or to deter thieves who look for opportunities to steal inside the facility or in the parking lot. Milestone Systems has a history of working with healthcare organizations to provide a video technology platform that works with IP cameras, door access control, IoT sensors, and other security and healthcare technology at work throughout the hospital and clinic. XProtect® VMS is open platform software that integrates with many diverse tools, keeping people and property safe in any healthcare environment. General rights of privacy regulatory concerns Medical staff may welcome surveillance when they understand it enhances their safety in the workplace These days, most workers, patients, and visitors to healthcare facilities expect to see obvious video surveillance in public areas of the facility and parking areas. The video cameras offer some assurance that active monitoring of the facility occurs and that the buildings have sophisticated safety controls in place. Medical staff may welcome surveillance when they understand it enhances their safety in the workplace. A myriad of regulatory requirements, such as HIPAA and state privacy laws generally allow video surveillance in public and worker-only spaces without explicit consent, as there is no expectation of privacy in these areas. However, capturing audio along with video requires deeper analysis to avoid running afoul of two-party consent laws. Of course, adequate governance considering a multitude of regulatory concerns is a must, including workforce policy and public notices of the use of video surveillance in the facilities’ Notice of Privacy Practices or other posted privacy notices. Hospital’s regulatory requirements Numerous regulatory bodies, such as the Joint Commission, the American Hospital Association, and HIPAA regulators support the use of video surveillance in private areas, such as patient rooms, treatment areas, triage, and in the ER in some circumstances. Video surveillance may also be used to support a hospital’s regulatory requirements under HIPAA, OSHA, and the Joint Commission. Video surveillance is used to support a hospital’s requirements under HIPAA, OSHA, and Joint Commission Types of hazards employees are exposed to, the severity of the hazards, and the risk the hazards pose to employees are all considered in determining methods of hazard prevention, elimination, and control. According to the Joint Commission hospital accreditation standards, the hospital should take action to minimize or eliminate identified safety and security risks in the physical environment. HIPAA or general privacy laws The Health Information Portability and Accountability Act of 1996, commonly known as HIPAA, is the sweeping patient-centric federal confidentiality law requiring healthcare providers and facilities, among others, to address the following: Safeguard protected health information (PHI) by limiting the use or disclosure of PHI to that which is permitted or required, Reasonably secure electronic PHI, and Provide notice of unauthorized use of disclosure of unsecured PHI, such as a data breach. There is generally no expectation of privacy under HIPAA or general privacy laws in public or worker-only facility locations. Thus, location and surveillance methods must be carefully analyzed under HIPAA, especially for use in exam and treatment areas, during telehealth visits, and in meetings or messaging applications. HIPAA Privacy Regulation Specifically, if the use of video surveillance passes muster under the HIPAA Privacy Regulation and there is a permissible or required use of PHI disclosure, the VMS platform must be assessed for risk for certain vulnerabilities and mitigations and for sufficient information security controls, including: technical security controls, such as encryption and retention, physical security controls, such as location, tampering, role-based access, and audit controls for video archives, and administrative security controls, such as vendor business associate agreements, facility policies, and procedures for handling video and training on such requirements. In addition, each of these controls should ensure the confidentiality, integrity, and availability of ePHI (e.g., electronic full-face images captured in electronic video format). Insurance Insurance premium rates, including rates for cybersecurity and regulatory defense continue to rise Insurance premium rates, including rates for cybersecurity and regulatory defense continue to rise. Having a video security system in place may offer relief to rising insurance premiums. Some liability and workers’ compensation insurance carriers may offer discounts or best premium rates for evidence of certain safety, privacy, and security controls. Many carriers are routinely requesting companies to complete the carrier’s privacy and security assessment. This includes sharing details about privacy and compliance programs and describing video security measures. Ask the insurance carrier or broker for more details. How Milestone Systems supports safety and health management Milestone Systems and its diverse network of partners have experience in solving problems for the healthcare industry and focus on developing positive business outcomes for customers, such as supporting the complex challenge of ensuring the privacy and security of healthcare facilities, medical staff, patients, and visitors. Milestone Systems’ XProtect® VMS allows organizations to capture and preserve video evidence In traditional uses, Milestone Systems’ XProtect® VMS allows organizations to capture and preserve video evidence; conduct forensic, legal, and regulatory investigations of the video; and improve its security posture by using video archives in post-incident lessons learned and training. XProtect open platform Milestone Systems’ ongoing and most recent technological advancements include incorporating unique video analytics, integration with IoT sensors, and other innovations in conjunction with the partner community. The modern approach to security helps be proactive and helps predict, prevent, and identify problems early. If interested in learning more about Milestone Systems and the XProtect open platform, schedule a demonstration with one of the representatives to discuss desired business outcomes.


Expert commentary
The average business owner or investor has some kind of security precaution in place, especially in the after-hours when there are fewer deterrents to inhibit criminal activity. Security guards, video surveillance systems, motion sensor lights, or even just fake cameras placed around the property are some of the common options people choose. Future of overnight security Smart business owners are starting to realize, however, that some of these traditional security measures are becoming antiquated and no longer cutting. The now and future of overnight security is in remote guarding. Pioneered by companies like Los Angeles-based Elite Interactive Solutions, which was founded back in 2007, remote guarding is revolutionizing the overnight security business. Minimizing criminal activity Remote guarding is fast becoming the most popular choice among commercial end-user property owners Remote guarding utilizes a combination of cutting-edge technology, “digital guards,” highly trained security agents, and local law enforcement if and when necessary to minimize the potential of criminal activity. For those adequately enlightened to its overwhelmingly impressive crime prevention capabilities, remote guarding is fast becoming the most popular choice among commercial end-user property owners to secure and protect their investments. What Is Remote Guarding? Remote guarding is a revolutionary concept and increasing trend in security systems that utilize a combination of methods to effectively analyze potential threats to property. Cameras and/or other monitoring devices running highly advanced algorithmic software are installed in strategic areas or vulnerable places onsite and remotely located security agents are immediately notified of any activity within a designated perimeter of the property. A blend of AI, cybersecurity, and video analytics When properly deployed by an expert provider, the technology stack includes a proprietary blend of video analytics, artificial intelligence, cybersecurity, and more. Done right, “noise” is effectively filtered out, allowing agents to act on legitimate alerts and achieve zero false alarms communicated to first responders. Today, there are a lot of terms and descriptions tossed around about remote guarding, remote video, virtual guarding, etc., but those attributes must be present to represent the true definition of the offering and its many virtues. Realtime situational awareness Many systems have a two-way speaker that allows the security agent to give a verbal warning When specially trained security agents are alerted to trespassers, possible intruders, or other suspicious activity, they analyze the situation in real time and determine the necessary level of action. Many systems have a two-way speaker that allows the security agent to give a verbal warning, known as a voice-down, to the individual(s) that they are being watched. Most perpetrators, often believing the response is emanating directly from security personnel on the property itself rather than from a remote command center, flee immediately. However, if the threat persists, the security agent enlists local law enforcement to get on the scene. Customized remote guarding When properly deployed, remote guarding systems are also customized to specific properties. A team of consultants visits the client’s property to evaluate its vulnerabilities and where to best place cameras and/or other monitoring devices for system efficacy. Traditional Security Shortfalls According to Keith Bushey, a retired commander for the Los Angeles Police Department, there is much frustration between law enforcement officers and potential victims of crime due to the historically unreliable performance of traditional burglar alarm systems and central monitoring stations. He states about 90% of security-related calls are false alarms, a problem that has been well-documented through the years. Onsite challenges When a legitimate emergency does occur, the perpetrators have often already done their damage When a legitimate emergency does occur, the perpetrators have often already done their damage and/or escaped by the time law enforcement arrives. Onsite security guards are not the remedy either as they bring their own set of issues and challenges. Unexpected costs Traditional security systems can also have unexpected costs. The cost is not only in the security guards’ paycheck or the cost of the equipment itself. The cost comes when an actual incident occurs. In worst-case scenarios, the security guard(s) are injured, the business suffers inventory loss, and/or damage is sustained to the property. The medical and other costs for the security guard(s), the loss of inventory, property damage, deployment of law enforcement resources, and possible fallout of legal expenses all add up. Even in the best-case scenario, false alarm expenses incur if law enforcement is dispatched. These, among many others, are some of the primary issues that remote guarding resoundingly answers as a superior alternative. A Bounty of Benefits Remote guarding systems have been proven to cut costs and be more effective than traditional security systems. Even though the monthly monitoring costs of remote guarding are significantly higher than traditional intrusion detection system monitoring, the much higher effectiveness in crime reduction, elimination of false alarms, and augmenting or replacement of manned guards result in a substantially higher return on investment (ROI) to the end user. Easy tracking of threats The security cameras already have their image captured on record, making them easier to track down For example, case studies have demonstrated reduced security costs for clients by 60%, on average. These reductions have come from the costs of security staff, inventory, or property loss, plus saving money on insurance premiums and deductibles. The nature of remote guarding reduces the risk and costs of false alarms, with professional security agents able to determine an actual threat before law enforcement is called. In a rare instance when a perpetrator escapes before law enforcement arrives or can detain the individual(s), the security cameras already have their image captured on record, making them easier to track down and identify. Reduction of false alarms The significant reduction in false alarms is greatly appreciated by law enforcement, as it allows them to focus on real emergencies or crises. Better relationships are also developed between clients and law enforcement, as remote guarding systems are highly reliable in providing accurate and real-time information to officers as they approach the scene. In short, it assists law enforcement in doing their job more effectively, as well as more safely thanks to having eyewitness information before engaging in an active crime scene. Partnership When you combine the decreased cost with the increased efficiency and success rate, it is easy to see why many commercial end-user property owners across the country are making the shift to remote guarding. It’s also an outstanding opportunity for professional security dealers and integrators to partner with a remote guarding services provider to bring a superior solution to their end customers and pick up a recurring monthly revenue stream in the process.
It’s no secret that the data security sector is constantly changing. It has an annual CGR of about 12.3%. Future trends in data security Much of this has to do with the rise of cybercrime in recent years, with reports showing that cyberattacks happen as often as every 39 seconds. To combat the growing rate of cybercrime, data security has been on the rise. As we journey further into this era, it becomes evident that a spectrum of significant trends is molding the future of data security. This exploration delves into a selection of these trends, unraveling their importance and the potential implications they carry 1. AI security tools will increase Artificial Intelligence is also being used in the development of smart attacks and malware The introduction of Artificial Intelligence in the data security industry brought significant changes, especially in cybersecurity. AI has been the golden standard for face detection, natural language processing, automated threat detection, and automated security systems. Additionally, Artificial Intelligence is also being used in the development of smart attacks and malware, bypassing even the latest security protocols in data control. And as time progresses, AI security tools will flourish and dominate the scene. Let’s take a more in-depth look at three of the top AI security tools. Targeted attack analysis tool Manufacturers utilize targeted attack analysis tools to uncover targeted and stealthy attacks. Artificial Intelligence can be applied to the program’s capabilities, processes, and knowledge. For instance, Symantec launched this tool to combat the Dragon 2.0 attack in 2022. The phishing attack reprimanded multiple energy companies while trying to gain access to their operational networks. Targeted Attack Analysis Tools can analyze incidents and look for similarities from previous situations. They also help detect suspicious activities and collect all the necessary data to determine whether a specific action is malicious. Intercept X tool Results from the Intercept X Tool feature high accuracy and a low false positive rate Sophos, a British security hardware and software company, launched the Intercept X Tool. It engages a neural network that records and analyses data like a human brain. Sophos’ Intercept X Tool can extract features from a single file and perform a deep analysis. It detects malicious activities within 20 milliseconds. Plus, it’s also trained to work on bi-directional sharing and real-world feedback of threat intelligence. Results from the Intercept X Tool feature high accuracy and a low false positive rate. IBM Watson Technology IBM’s QRadar Advisor uses IBM Watson Technology, a unique AI tool for fighting cyber attacks. Artificial Intelligence can auto-investigate activities and indicators for potential exploitation or compromise. With cognitive reasoning, IBM Watson Technology can present critical insights to accelerate the response cycle. Security analysts can utilize this technology to search for threat incidents, reducing the risk of letting them fly under the radar. 2. Blockchain as a security solution It guarantees no points of failure or hackable entrances that can expose datasets inside the system Blockchain is a type of distributed ledger technology (DLT) that aims to establish trust within an untrusting ecosystem. Today it’s one of the most robust cybersecurity technologies in the industry. Blockchain utilizes a decentralized ledger system, but your team members can still gain access to transparent information in the cloud. Members can also record, pass along, and view necessary transactional data in the blockchain. The entire blockchain process maintains data integrity within the system while establishing trust among team members. It guarantees no points of failure or hackable entrances that can expose datasets inside the system. Cybersecurity, biometrics Cybersecurity primarily benefits from these features because blockchain can create a secure and robust wall between data and hackers. On top of that, blockchain ledgers can include biometrics like fingerprints and retina scans. These prevent hackers from accessing any private data. Because blockchain is decentralized, it also limits hackable data. Together with the technology’s record-keeping system, each node is provided insight into data manipulation exposing real-time cybercrime attempts. 3. Increased and widened access control Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data Access control is critical in data security. More than a valuable security tool, business leaders can use access control to regulate people accessing any given resource. A company with an IT security setting can control who has the liberty to edit certain files. One of the primary goals of access control is to minimize threats or attacks to organizations and businesses to keep people and data secure. Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data protection laws. Benefits The benefits of increased and widened access control include: Identifying who can access and control your data at specific time intervals. Protecting data from overwriting, accidental deletion, and malicious intent. User permissions that can be readily changed. Compliance and regulation with data privacy laws. Central management of access to data through a reporting portal or a dashboard. Multi-factor authentication Access control comes in various types and systems, so it’s critical to know the features of what you’re looking for. The most common type is multi-factor authentication or MFA. It involves multiple steps before logging in, requiring the user to enter other relevant information besides the password. Some other examples of information include biometrics, answering a security question, or entering a code sent to the user’s email address. Two-factor authentication, role-based access control Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession. Another type of access control is role-based access control. In this setup, only one individual can set up access guidelines and grant permissions to specific team members within an organization. 4. Greater use of the zero-trust security model The zero-trust security model is a framework that requires every user within and outside the organization to undergo authentication, authorization, and validation. These are all essential to ensure proper security configuration before access is granted to the company’s applications and data. A zero-trust model assumes that anyone can cause data breaches and that a traditional network edge is not taken into effect. Moreover, it addresses the following modern-day challenges: Hybrid cloud environments. Security of remote workers. Ransomware threats. This framework utilizes the combination of multiple advanced technologies, including: A risk-based multi-factor authentication. Endpoint security. Identity protection. Cloud workload technology. The zero-trust model uses all these innovative tools for system identification, user verification, access consideration, and system security maintenance. Constant validation and monitoring Enforcing strict policies and compliance with data privacy laws are also essential Additionally, it also considers data encryption, email security, and asset verification before establishing connections with applications. The architecture of a zero-trust framework requires constant validation and monitoring of the users and the devices they are using. Enforcing strict policies and compliance with data privacy laws are also essential. More importantly, the zero trust architecture requires all organizations to be aware of all their available services and accounts to gain complete control of data handling and manipulation. 5. Increased privacy regulations Privacy regulations and policies guide organizations in proper data control, handling, and security. These policies guide organizations in proper data control, handling, and security. As a responsible business owner, you must comply with these regulations to avoid legal issues. With cybersecurity attacks becoming common, expect increased and stricter privacy regulations to be released in the next few years. While current policies are still taken into effect, various modifications and adjustments will occur to compete with the rising numbers of data breaches, thefts, data loss, and more. California Privacy Rights Act (CPRA) Currently, the California Privacy Rights Act (CPRA) is the most comprehensive legislation on state data privacy. It only started to take effect on January 1, 2023. The CPRA introduces the following principles: Broad individual consumer rights. Significant duties of people who need to collect sensitive and personal information. Additional definitions of data privacy and security. An individual’s duties include releasing information about data collection to concerned data subjects and proper access, correction, and deletion of information. Final thoughts 2023 is a big year for data security. Trends such as increased adoption of zero-trust policies, a greater reliance on AI security tools, and the implementation of blockchain as a security solution are all things we expect to see shortly. Staying up-to-date with these trends is important for keeping your business current and ensuring that you’re adhering to new and changing regulations. Doing so can give you an edge over the competition and keep you out of legal hot water.
Daniel May of Consort reviews the integration of access control systems in healthcare settings, outlining the benefits and key considerations decision-makers must make throughout product specifications. From patient safety and traversal to the protection of sensitive data and pharmaceuticals, healthcare environments are faced with several operational challenges. And where security remains at the forefront of decision-making, modern access control systems may often hold the answers. Physical security systems Hospitals in particular have developed into multi-faceted spaces that house hundreds to thousands of patients, staff, and visitors at any one time. In England for example, research has found in the three months leading to June 2023, an average of 44,626 people visited major hospital A&E departments each day, with over 16 million attendances typically recorded over the course of a year-not to mention an additional nine million logged at other minor units. For any building, this level of sustained footfall can request severe security difficulties For any building, this level of sustained footfall can invite severe security tests. With that, the need to deploy effective physical security systems in healthcare is clear. And so, as access control continues to become more readily adopted and new products enter the market, decision-makers are reminded to consider the requirements of their building, ensuring they select the solutions most suited to their settings and budget. Security controlled Patient safety will always remain the top priority in healthcare settings, and where matters of health and social care come into question, a diverse set of professional regulatory bodies are tasked with setting and maintaining high standards. When it comes to healthcare premises specifically, patient security and perimeter security often come hand in hand and are amongst the most pressing of challenges that decision-makers must face. To help address operational planning and potential design concerns in the NHS, the Health Building Note (HBN), provides general design guidance for healthcare buildings under HBN 00-01-citing the use of access control measures as a way of maintaining security and protecting the safety of patients, staff, and visitors. Use of access control Hospital buildings control varied levels of access for a number of security purposes Hospital buildings, for example, must control varied levels of access for a number of operational and security purposes. Routine scenarios exist where vulnerable patients are under monitoring and thus refrained from exiting the premises for their own safety, while at the same time, permitted staff must be able to reach their patients and medicines when required. For this, the use of access control is key. Equally, access credentials can also help management teams keep track of those who may be entering or exiting rooms with equipment and pharmaceutical supplies, deterring any unwanted visitors and opportunists in the process. Incorporation of access control systems On a similar note, regulations have set a minimum standard for how personal data should be stored and managed in healthcare environments, giving decision-makers an added responsibility to regulate staff-controlled areas with patient medical records. While instances of personal data breaches are rare, healthcare facilities and professionals are at legal risk should confidential data be found misused or missing. As such, the incorporation of access control systems has become essential in keeping data storage areas secure, with intuitive online systems capable of permitting access to staff with the correct credentials while simultaneously tracking who has requested clearance at digital entry points. HBN guidance Healthcare experts are better fitted to control the sheer volume of people entering and exiting To function effectively, healthcare facilities must always be perceived as safe places by the people who reside within them, and as HBN guidance implies, a unified physical security system can help address key safety and security concerns while enhancing patient and staff experience. Opportunely, access control systems are more accessible and adaptable than ever and combine several technologies such as mechanical locks and automatic doors with electronic access credentials in the form of smartphone apps, badge readers, and biometric scanners. By integrating these systems into the building’s existing infrastructure, healthcare professionals are better equipped to control the sheer volume of people entering and exiting the premises without impairing the general flow of movement and coordination around the facility. Better by design Despite the clear benefits offered to healthcare facilities, there are a number of considerations to be mindful of when choosing an access control solution. Poorly implemented systems can have an adverse effect on security and functionality - quickly costing healthcare organizations time and budget to rectify and replace the inadequate products that don’t meet the building’s requirements. For that reason, decision-makers and design teams are reminded that there is no single solution that fits all healthcare buildings. As such, it’s crucial for decision-makers to understand the systems that are being put in place throughout each of the touchpoints in their facility. Clear collaboration is required during periods of specification, where together, teams can ensure the selected product works on all angles, from meeting fire safety and sustainability standards to aesthetics and scalability. Modern access control products Scalability is a key area that decision-makers must review when selecting access control systemsFrequently overlooked, scalability is a key area that decision-makers must review when selecting access control systems. Such is their diverse nature; healthcare facilities can often change and develop as years go by, and by selecting a system that facilitates growth, such as a cloud-based solution-security and efficiency is long-established. While modern access control products are known for seamless integration, there are some systems that may restrict the ability to use different vendors throughout the remainder of the building’s infrastructure. This, in effect, causes a monopolization of products throughout the estate, which can have an adverse effect on growth by increasing costs and reducing the levels of service associated with the security system already in place. Improve security and safety A scalable and reliable access control system will continue to improve security and safety by adapting to a building’s new requirements-and all while having minimal impact on its operational network. And so, while technology will no doubt continue to influence and transform the access control market, healthcare facilities and their professionals must continue to remain educated on their own systems, ensuring they have the best options in place to keep their patients, staff, and visitors safe and secure for years to come.
Case studies
Honeywell has been selected as the building automation provider for LG Energy Solution’s cylindrical EV battery manufacturing facility being built in Queen Creek, near Phoenix, Arizona. Set for completion in 2026, this state-of-the-art project represents a critical milestone in LG Energy Solution’s strategy to lead EV battery innovation in North America, and it also supports Honeywell’s alignment of its portfolio to three compelling megatrends, including automation and the energy transition. New standard for operational efficiency Deployment of Honeywell’s building automation technologies at the Queen Creek facility Global battery demand is projected to quadruple by 2030 according to Bain, and the deployment of Honeywell’s building automation technologies at the Queen Creek facility will help set a new standard for operational efficiency in high-tech manufacturing environments. This 1.3-million-square-foot standalone facility will integrate a suite of Honeywell technologies to help optimize performance, enhance safety and support sustainability outcomes. Future of automation “By developing and delivering solutions that blend cutting-edge technology and energy management, we are driving the future of automation," said Billal Hammoud, president and CEO of Honeywell Building Automation. "Honeywell’s collaboration with LG Energy Solution demonstrates how advanced building automation can help empower companies to achieve operational excellence in their facilities while also accelerating the shift to a more secure energy future.” Honeywell’s innovative solutions Honeywell’s innovative solutions will provide the Queen Creek facility with the following: Unified Systems Integration: Honeywell’s Enterprise Buildings Integrator platform will help enable seamless control of building management and safety systems via integration into Honeywell Forge, which provides advanced monitoring and analytics. Honeywell Forge, an IoT platform, enables condition-based maintenance to improve the resiliency of critical systems around the clock, helping to reduce unplanned reactive work and help lower energy costs. Its machine learning capabilities will continuously study a building's energy consumption patterns, which will enable LG Energy Solution to automatically adjust the facility to optimal energy-saving settings. Comprehensive Fire and Safety Solutions: Honeywell’s VESDA smoke detection and advanced self-testing fire alarm system offers automated and continuous air sampling enabling early warning of an impending fire hazard, often even before heavy smoke or flames are detected. VESDA and the networked fire alarm solution will be integrated into the facility’s building management system to allow coordinated and near-instant responses from the HVAC system if smoke is detected. Mission Critical Control and Advanced Cybersecurity: The QronoX Programmable Logic Controller will enable LG Energy Solution to enhance operational performance and resilience by providing advanced cybersecurity for its facility. The Honeywell technology will also help ensure asset security and compliance while reducing downtime for critical systems. Honeywell’s scalable solutions are designed to support the future expansion of the project as well, reinforcing its role as a key collaborator in this transformative industrial sector.
The Dutch powerhouse Kramp is one of the biggest suppliers of parts and accessories for Europe’s agricultural sector. Founded in 1951, focusing on simplifying life for those who work the land, Kramp boasts a staggering 590,000+ products, from tractor gears to stable shovels. Kramp’s success hinges on its robust infrastructure. A strategically located network of 11 distribution centers across Europe ensures prompt deliveries, while 24 sales offices provide localized customer support. Localised customer support Challenge- Balancing reliability and installation speed in a temporary warehouse security upgrade. Kramp rented a warehouse covering an area of over 5,000 m2 for approximately three years with a security system installed. However, it needed to be updated to fulfill the Grade 2 insurance requirements. Therefore, the client decided to replace a security system and, at the same time, wanted to install a fire alarm system. Since Kramp is known for the speed of the company’s business processes, the warehouse security system had to be updated and launched as fast as possible to prevent any disruption to the operation. This demanded a solution that could be installed quickly and with minimal costs, yet maintaining quality and reliability. Central monitoring station Ajax wireless security system with third-party device integration for intrusion and fire detection in a large facility Solution - Lankhof Beveiliging proposed Ajax wireless systems for a client’s temporary warehouse to address the requirements for a convenient and flexible solution. Ajax products are quick and easy to install, which is particularly valuable in this case, as everything can be easily moved and reconfigured when needed. For the expansive 5,000 m2 space, Lankhof Beveiliging’s chosen solution involved the implementation of the Hub 2 Plus Jeweller control panel. It has four communication channels (Wi-Fi, Ethernet, and two SIM cards) and supports LTE and photo verification. With such a configuration, up to 200 devices can be added to the hub, making it a perfect fit for a large facility. Integration with the client’s LAN network ensured compliant reporting to the central monitoring station. ReX 2 Jeweller radio signal range extender The ReX 2 Jeweller radio signal range extender was installed to ensure stable communication between Ajax detectors and the hub. The hub’s communication range was sufficient to cover a given perimeter, but the warehouse presented some challenges. Significant radio interference was expected due to its metal walls and many metallic goods stored within. However, the professional installer efficiently designed the system to maintain stable communication throughout the facility, successfully implementing just one range extender. DoorProtect Jeweller Third-party contacts on the overhead doors for vehicles were seamlessly integrated into the Ajax system In terms of intrusion prevention, pedestrian doors were equipped with DoorProtect Jeweller opening detectors for reliable monitoring. Furthermore, third-party contacts on the overhead doors for vehicles were seamlessly integrated into the Ajax system. MotionCam Jeweller detectors were placed around the warehouse to detect movement and capture any possible intrusion, providing additional false alarm verification with a series of pictures available in the Ajax app. KeyPad Plus Jeweller To make the system convenient and easy for the client but also protected from unauthorized access, Lankhof Beveiliging installed KeyPad Plus Jeweller and distributed contactless Pass cards to employees for access to the facility. At the same time, the administration and installation company used straightforward Ajax apps to monitor the system status and implement additional settings. StreetSiren, FireProtect 2 RB and MultiTransmitter Jeweller The module features 18 wired zones for device connection and five contact types of support Installed on all sides of the building, StreetSiren Jeweller sirens provided both deterrence and audible notifications. Fourteen FireProtect 2 RB (Heat/Smoke) Jeweller fire detectors were installed within the business premises to address fire safety. Larger spaces were equipped with new third-party long-beam fire detectors, connected to MultiTransmitter Jeweller. The module, featuring 18 wired zones for device connection and five contact types of support, made it easy to connect the third-party fire detectors. Why Ajax Complex protection against intrusion and fire: An Ajax system offers complete intrusion protection, video surveillance, fire detection, water leak prevention, and automation solutions that can be integrated with wired and wireless detectors. In this case, the solution covered the client’s need for a single intrusion and fire protection system with quick and easy configuration and management in one app. Flexible and quick-to-install wireless solutions: Since the warehouse is temporarily at the company’s disposal, and the client needed to put the warehouse into operation as soon as possible, Ajax wireless devices were the most effective solution to meet these security demands. They are quick, easy to install and configure in the app, and comply with the Grade 2 insurance requirements. In case of a relocation, the entire system can be easily removed and installed at another facility. Large-scale capability with the Jeweller radio protocol: Thanks to the Jeweller proprietary radio protocol, the chosen security solution facilitated a swift and hassle-free implementation in a 5,000 m2 industrial hall. The Jeweller protocol offers reliable two-way communication between a hub and detectors, covering distances of up to 2,000 meters and transmitting alarm signals in less than 0.15 seconds. Products Hub 2 Plus Jeweller: Security system control panel ReX 2 Jeweller: Radio signal range extender that boosts the range of Ajax security system devices MultiTransmitter: Module for connecting wired alarm to Ajax FireProtect 2 RB (Heat/Smoke) Jeweller: Wireless fire detector with heat and smoke sensors MotionCam: Motion detector with a photo camera to verify alarms DoorProtect Jeweller: Wireless opening detector StreetSiren: Wireless outdoor siren with vandalism resistance KeyPad Plus: Wireless touch keypad supporting encrypted contactless cards and key fobs Pass: Encrypted contactless card for keypad
Alarming increases in vehicle thefts, unsolved traffic collisions, and stolen cargo in the Mexican State of Tlaxcala, motivated the Executive Commission of the State Public Security System (CESESP) to expand and upgrade its video security system. To counter the rise in crime, the CESESP sought a flexible, scalable, open-platform video management system (VMS) that could seamlessly incorporate existing cameras as well as over 800 new cameras and edge devices from a range of hardware and software providers. Tlaxcala Located in East-Central Mexico, Tlaxcala is one of 32 states within the Federal Entities of Mexico. With a population of approximately 1,343,000, based on the 2020 census, Tlaxcala is the smallest yet one of the most densely populated states in Mexico. The CESESP of Tlaxcala is tasked with safeguarding residents across the state's 60 municipalities. C4 center C4 center has multiple teams of six security professionals who monitor the system around the clock At the core of all security operations, including the 911 emergency response and 089 confidential tip line, is the CESESP's Control, Command, Communications, and Computing Center (C4). The state’s C4 center has multiple teams of six security professionals who monitor the system around the clock on a large, 24-screen video wall. The C4 also houses the system’s HP and Lenovo servers. Flexibility, scalability, and budget “Flexibility, scalability, and strictly adhering to the budget were top requirements for this critical, state-wide project,” said Maximino Hernández Pulido, Executive Commissioner of the State Public Security System. “We considered a variety of proposals and providers, but we ultimately followed the advice of our integrator, Digital Information Systems, and selected XProtect Corporate from Milestone Systems.” XProtect Corporate The new system includes cameras from Hanwha Vision, Bosch Security and Safety Systems, Hikvision, and Pelco The new system includes cameras from Hanwha Vision, Bosch Security and Safety Systems, Hikvision, and Pelco, all integrated within the system and managed by XProtect Corporate VMS from Milestone Systems. The system is also fully integrated with the BriefCam Video Analytics Platform, delivering video intelligence for system managers to identify, monitor, investigate, and visualize incidents plus video data to make smarter decisions. Efficient and cost-effective integration “Because state officials rely on their video system 24/7, the update needed to be gradual with no downtime. As new cameras were integrated into the Milestone platform, the previous system slowly disappeared,” said Isaac Sánchez Morales, an engineer at Digital Information Systems (SDI), an integrating company. “The XProtect Corporate open platform VMS allowed us to leverage our existing cameras and servers, integrate new equipment and devices, making the process very efficient and cost-effective, and we never had a gap in service.” Data-driven video for fast response times BriefCam video analytics technology The solution detects, identifies, and classifies video metadata to drive more efficient investigations The BriefCam video analytics technology seamlessly integrates into Milestone’s XProtect Smart Client. The solution detects, identifies, and classifies video metadata to drive more efficient investigations and business decisions, such as finding missing persons, investigating vandalism, theft, assaults, accidents, injuries, or acts of violence, as well as extracting and analyzing through heatmaps, dashboards, and visualizations. The analytics have proven beneficial in accelerating investigations, attaining situational awareness, and optimizing operational intelligence for enhanced video search, alerting, and data visualization. Real-time alerts, situational awareness “We installed the BriefCam Insights and Investigator products, and regularly use the platform’s RESPOND and RESEARCH capabilities. One of the advantages of all these XProtect-integrated analytics is that operators do not have to open additional windows or enter new credentials to access them,” said Sánchez. “With this integration of technologies, operators can trigger real-time alerts based on complex object classifications and filter combinations to increase situational awareness meaning authorities can react to events as they unfold.” Proactive policing with LPR With the BriefCam RESPOND solution, object characteristics and license plate recognition tools can be used" Sánchez added, "With the BriefCam RESPOND solution, object characteristics such as vehicle, person, or animal, and license plate recognition tools can be used to trigger rule-based alerts." "These tools can help overcome the challenges of urban video surveillance and drive proactive policing in Tlaxcala." Video technologies reduce state crime rates Following the comprehensive expansion of the security infrastructure, statistics from the Executive Secretariat of the National Public Security Systems revealed Tlaxcala boasted the lowest crime rate nationwide. With the modernized system in place, officials documented a 93% reduction in pilfered freight from transport companies. Similarly, vehicle theft declined by 22.5%. A cost-efficient and flexible way Milestone Interconnect provides a cost-efficient and flexible way to gain central surveillance According to Sánchez and the SDI team, it is expected that each municipality within the territory will soon have its own locally focused VMS. With the use of Milestone Interconnect, all the municipality subsystems will integrate directly with the state-wide platform. Milestone Interconnect provides a cost-efficient and flexible way to gain central surveillance of multiple sites spread across a region. C4 video surveillance operation “The integrated solution delivered through Milestone is a robust, efficient, and secure system that provides all the necessary tools for the C4 video surveillance operation,” added Executive Commissioner Hernández-Pulido. “In addition, the excellent technical and post-sales support from Milestone and SDI has led us to meet the system and performance goals we set for ourselves.”
Amthal has come to the rescue of Katherine Warington School, taking over the support and remote monitoring of fire safety and security services for the benefit of staff, pupils, and visitors. Based in Harpenden, Katherine Warington School is a brand-new secondary school that opened in 2019 and welcomed its first cohort of 180 year-seven students in September of that year, before moving into a completed main building in the summer of 2020. Honeywell Gent solution Following a storm that damaged the school’s fire alarm system, the school consulted with Amthal to rectify the situation. Amthal recommended a specialist Honeywell Gent solution to restore the system to full functionality. Amthal continued to monitor the site remotely, working with the management team to service and support security, which included updating the intruder alarm system and access control. Each is now supported to the highest possible standards to create a safe learning environment enabling "every student to make outstanding progress, whatever their starting point.” Safe and secure learning environment It is also developing as a hub for the local area to enjoy and share in our exceptional facilities" Dean Inns, Katherine Warington School’s Business Manager, said: “Our school fosters a learning culture that rewards effort, inspires learning and engenders a shared belief amongst all members of our school that they are equipped to thrive in a changing world. It is also developing as a hub for the local area to enjoy and share in our exceptional facilities." Dean Inns adds, “To achieve this, we must offer a safe and secure learning environment for our staff, pupils and the wider community. This is where Amthal really came into its own, quickly responding when the storm damaged our life safety systems and continuing to work with us to enhance our security. Our continued collaboration reflects our dedication to maintaining a secure and conducive learning environment." Security and fire safety Amthal’s team works closely with Katherine Warington School and continues to monitor security and fire safety on site. Conducting continuous risk assessments, providing bespoke recommendations and delivering training to staff to ensure the seamless integration and maximum utilization of all safety and security systems in place. Paul Rosenthal, Amthal Sales Director, stated: “Amthal’s expertise in delivering integrated solutions in education settings played a crucial role in securing the project. We were able to identify requirements quickly and efficiently, working around learning environments. The fire safety system, working with our partners at Honeywell Gent ensures early detection capability and enables a prompt response in case of emergencies." Safe educational setting The need for an enhanced intruder alarm was clear, to ensure the protection of the premises" Paul Rosenthal adds, “When we took over the service, support, and remote monitoring, the need for an enhanced intruder alarm was clear, to ensure protection to the premises, in and outside of school hours." He continues, "Our continued partnership has also led to us updating the access control on site as the school continues to support young people to thrive, and welcomes its neighbors from the local area to take advantage of the facilities in a safe educational setting.” Advanced security solutions Independently owned, Amthal Fire & Security is dedicated to satisfying end-user needs for security safety and convenience offering design, installation, service, and remote monitoring of advanced electronic fire and security solutions, including intruder, fire, access, and CCTV systems. Amthal Fire & Security is accredited by the Security Systems and Alarm Inspection Board (SSAIB), United Kingdom Accreditation Services (UKAS), and British Approvals for Fire Equipment (BAFE).
Custom Consoles announces the completion of a control room desk for Opem Security, a pioneering provider of security systems and services. Located at Opem’s headquarters in Milton Keynes, the desk will form part of the round-the-clock monitoring support Opem performs for clients in many locations. Custom Consoles’ experience “We were looking for a robust and ergonomically well-designed desk that would allow our staff to work comfortably and efficiently,” comments Opem Founder and Managing Director, Jason Pelham. Custom Consoles’ experience and industry background are evident in the styling and build quality" He adds, “SteelBase gave us the freedom to specify exactly what we had in mind from a standard range of structural components, including integral accommodation for our computer equipment and video monitor displays. Custom Consoles’ experience and industry background are evident in the styling and build quality. They can also be seen in the attention to detail such as cable management with easy access during initial installation and throughout the desk’s lifetime. Our operators also appreciate being able to position the horizontal and vertical angle of the monitor screens to suit their preferred viewing angle, each screen being mounted on an individually adjustable mounting arm.” SteelBase installations “This is the most recent of many SteelBase installations we have produced for clients in the security, aviation, and industrial process control sectors,” said Custom Consoles Sales Manager, Gary Fuller. He adds, “Working alongside Opem, we designed a 5-meter-wide curved unit comprising seven bays. Each bay has its own front and rear doors and provides vented space for a computer as well as accommodation for up to 6U of rack-mounted technical equipment. The desktop is 1.2 meters in front-to-back depth and incorporates a continuous cable tray running the entire desk width, protected by an easily removable flush-fitting cover panel. Mounting points for data and power sockets are provided in each PC compartment." Cable management SteelBase takes its name from the high-strength steel base frames that form its structural core A structured desking system offering a hard-wearing and ergonomic solution for control room consoles, SteelBase takes its name from the high-strength steel base frames that form its structural core. Desks and related fittings such as equipment pods and side units can be specified and combined from a range of standard powder-coated steel base frames. Cable management is provided throughout the console with access to equipment via hinged removable doors to both front and rear. SteelBase furniture Predrilled monitor arm mounting points are positioned at the rear upper edge of each bay. Careful attention has been paid to styling. SteelBase desktops are available in a choice of 120 cm (standard) or 100 cm (SteelBase Lite) front-to-back sizes with a choice of hard-wearing Marmoleum or laminate work surfaces. All elements of SteelBase are guaranteed against component failure for five years of normal use. SteelBase furniture is designed to meet or exceed the requirements of ISO9241-5, EN527-1, 2, and 3, and BS EN ISO11064.
The Pearl-Qatar is an artificial island located off the coast of Doha, Qatar, and is known for its luxurious residential apartments, villas, and high-end retail shops. Tower 11 is the only residential tower within its parcel and has the longest driveway that leads to the building. The tower is a testament to modern architecture and offers residents exquisite living spaces with stunning views of the Arabian Gulf and the surrounding area. Tower 11 features an array of amenities including a fitness center, swimming pool, jacuzzi, and 24-hour security. The tower also benefits from its prime location, which allows residents easy access to the island's many dining, entertainment, and shopping attractions. The tower's luxurious apartments are available in a variety of sizes and configurations to meet the diverse needs and tastes of its residents. Upgrade to a newer system This outdated system is no longer efficient for meeting the needs of the residents or users of the facility Tower 11 was completed in 2012. The building has been utilizing an old intercom system for years, and as technology has advanced, this outdated system is no longer efficient for meeting the needs of the residents or users of the facility. Due to wear and tear, the system has been prone to occasional malfunctions, which have resulted in delays and frustrations when entering the building or communicating with other residents. As a result, an upgrade to a newer system would not only ensure reliability and enhance the user experience, but it would also provide added security to the building by allowing for better monitoring of who enters and leaves the premises. The solution Whereas 2-wire systems only facilitate calls between two points, IP platforms connect all intercom units and allow communication across the network. Transitioning to IP provides safety, security, and convenience benefits far beyond basic point-to-point calling. However re-cabling for an all-new network would require substantial time, budget, and labor. Rather than replacing cabling to upgrade intercoms, the 2-wire-IP intercom system can leverage current wiring to modernize infrastructure at a lower cost. This optimizes initial investments while transforming capabilities. DNAKE's 2-wire-IP intercom system was chosen as the replacement for the previous intercom setup, providing an advanced communication platform for 166 apartments. At the concierge service center, the IP door station 902D-B9 acts as a smart security and communication hub for residents or tenants with benefits for door control, monitoring, management, elevator control connectivity, and more. User-friendly interface Residents can answer the call, grant access to visitors, and unlock doors using the unlock button The 7-inch indoor monitor (2-wire version), 290M-S8, was installed in every apartment to enable video communication, unlock doors, view video surveillance, and even trigger emergency alerts at the touch of the screen. For communication, a visitor at the concierge service center initiates a call by pressing the call button on the door station. The indoor monitor rings to alert residents about incoming calls. Residents can answer the call, grant access to visitors, and unlock doors using the unlock button. The indoor monitor can incorporate an intercom function, IP camera display, and emergency notification features accessible all through its user-friendly interface. The benefits DNAKE 2-wire-IP intercom system offers features far beyond just fostering direct calls between two intercom devices. Door control, emergency notification, and security camera integration provide value-added benefits for safety, security, and convenience. Other benefits of using the DNAKE 2-wire-IP intercom system include: Easy installation: It's simple to set up with the existing 2-wire cabling, which reduces complexity and costs for installation in both new construction and retrofit applications. Integration with other devices: The intercom system can integrate with other security systems, such as IP cameras or smart home sensors, to manage home security. Remote access: Remote control of the intercom system is ideal for managing property access and visitors. Cost-effective: The 2-wire-IP intercom solution is affordable and allows users to experience modern technology without infrastructure transformation. Scalability: The system can easily be expanded to accommodate new entry points or additional capabilities. New door stations, indoor monitors, or other devices can be added without rewiring, allowing the system to upgrade over time.


Round table discussion
Headlines of violence in our schools are a reminder of the need to keep educational institutions safe. In fact, if there is a positive aspect to the constant bombardment of headlines, it is that it keeps our attention perpetually focused on how to improve school security. But what is the role of physical security systems? As the new school year begins, we asked this week’s Expert Panel Roundtable: Are schools safer because of physical security systems? Why or why not?
As physical security technologies become more complex, it is incumbent on the dealer/integrator to have the skills and expertise needed to ensure that a system operates smoothly. The value of integrators increasingly rests on the skill sets they bring to bear when installing a system. If the skills are missing, there is a problem. We asked this week’s Expert Panel Roundtable: What missing skills among security integrators can cause problems for customers?
Driving the smart homes market is the convenience of simple technology solutions. Almost every home now has a “smart speaker” that makes it easier than ever for homeowners to interface and control their technology. But where does security fit into the new landscape of smart home systems? We asked this week’s Expert Panel Roundtable: What’s new in smart homes and residential security systems?
Products