Perimeter security - News
ProdataKey (PDK), manufacturer of the cloud access control platform built for mobile, and InvictusXP, developer of a community technology platform for residents and building managers, have joined forces to create an all-in-one mobile solution for multi-tenant properties. Residents, guests, and visitors can now interact with PDK access control readers throughout their buildings using the same Invictus mobile app that they use for community notifications, virtual concierge services, visitor video...
The Secretary of Homeland Security, Alejandro N. Mayorkas has released the following statement announcing that the Department of Homeland Security has approved a temporary and targeted Jones Act Waiver, in order to address Puerto Rico’s needs as recovery efforts from Hurricane Fiona continue. The Secretary of Homeland Security’s statement - “In support of the Puerto Rican people, as they continue to recover from Hurricane Fiona, I have approved a temporary and targeted Jones A...
Exabeam, a global cybersecurity solutions provider and creator of New-Scale SIEM for advancing security operations, has announced a ground-breaking cloud-native portfolio of products that enables security teams everywhere to ‘Detect the Undetectable’. New-Scale SIEM is a powerful combination of cloud-scale security log management, industry-renowned behavioral analytics, and an automated investigation experience. New-Scale SIEM Built on the cloud-native Exabeam Security Operations...
Smart lock dealers are likely aware of the benefits that smart locks can bring to owners of rental vacation homes during the summertime –chief among them being the hands-free, key-free handoff from owners to renters. With a connected smart lock in place, and remote locking and unlocking controlled through a smart phone or tablet, property owners no longer have to take the time to come to the property to physically deliver a key. They can open the door remotely, from anywhere, as well as g...
The consortium led by Airbus and Capgemini was selected by the French Ministry of the Interior and Overseas territories for the role of Package 2 integrator for the Réseau Radio du Futur (RRF – radio network of the future), the secure and resilient broadband network for domestic security and emergency rescue forces. This pioneer project, led by France, is key to modernising domestic security forces. More than ever, this contract reinforces Airbus’ position as European leader...
For most business owners, business is more than just livelihood–it's the culmination of years spent dreaming and planning. With that in mind, it only makes sense to protect the business with the smartest security system on the market. For the modern business still with traditional security systems, there are four typical challenges. Huge investment Traditional intelligent security systems often need companies to invest in multiple independent subsystems and independent servers. C...
Aiphone Corporation, the international manufacturer of intercom and security communication products, is pleased to announce that its IX Series intercoms are compatible with the Genetec™ Security Center, a unified IP security platform that provides users with a single interface between multiple security devices and their data. This integration enables Aiphone IX Series customers to easily incorporate their video intercom systems as part of a larger unified security platform. Security Cente...
Moxa Launches Industrial Intrusion Prevention Systems on its All-in-one Secure Routers to Protect Critical Infrastructure. Moxa is excited to launch industrial intrusion detection/prevention systems (IDS/IPS) on its alongside the MXsecurity industrial security management software, expanding its product portfolio with advanced cybersecurity and purpose-built management solutions. The EDR-G9010 Series is an all-in-one secure router with firewall/NAT/VPN/switch functionality. Next-Generation fire...
With the announcement of the acquisition of Authlogics, Intercede expands its product portfolio to cover the entire range of authentication options from ‘Passwords to PKI’. Intercede use the ‘authentication pyramid’ to describe the various levels of security that differing authentication mechanisms provide, with PKI and FIDO at the top of the pyramid as the most secure due to their combination of private/public key cryptography, secure hardware, and multiple factors to i...
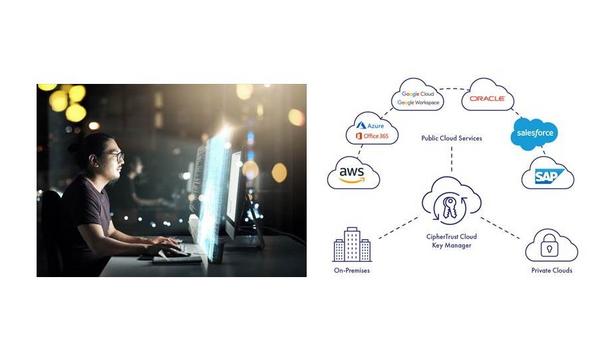
Thales announces the latest innovations of CipherTrust Cloud Key Manager that help organizations address digital sovereignty requirements across major public clouds including Amazon Web Services, Google Cloud, Microsoft Azure, Oracle Cloud, SAP, and Salesforce. Organizations that leverage these cloud providers can now leverage CipherTrust Cloud Key Manager’s Bring Your Own Key (BYOK) capabilities for enhanced data security and encryption key ownership. According to the 2022 Thales Cloud S...
EG Electronics, a specialist electronics technology solution provider of automation, energy, smart cities, and industrial IoT applications, will be co-exhibiting with their partner Bi-Search International at Electronica 2022 – the trade fair and conference for electronics. This year, Electronica will take place from 15-18 November 2022 at the Trade Fair Center, Munich, Germany, where EG Electronics and Bi-Search International will showcase their latest transparent OLED display technology...
Bugcrowd, the pioneer in crowdsourced cybersecurity announced it has been authorized by the CVE program as a CVE Numbering Authority (CNA). CVE program The Common Vulnerabilities and Exposures (CVE(r)) program is an international, community-based effort that relies on the community to discover vulnerabilities. The mission of CVE is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. The discovered vulnerabilities are then...
There has been talking about ‘future-proofed’ access control systems over the years. But what do those words mean? Simply, it means the system will remain secure, and provide enough capacity for future data transfer needs and additional devices. More to the point, it protects users' freedom to develop and expand their systems how they want. Users' reader choice has the greatest influence on the future functionality and expandability of their system. So, below, Idesco identifie...
A new study from Juniper Research has found that the total cost of eCommerce fraud to merchants will exceed $48 billion globally in 2023, from just over $41 billion in 2022. It predicted that this growth would be accelerated by the increasing use of alternative payment methods, such as digital wallets and BNPL (Buy-Now-Pay-Later), creating new fraud risks. Online payment fraud The report recommended that fraud prevention vendors focus on building platforms providing A...
New research reveals that the average security leader in the UK and US works 16.5 hours every week over what they are contracted to work. This is an increase of 5 and a half hours compared to the same figures last year (11 hours extra per week in 2021), as observed by email security firm, Tessian, as part of their annual ‘Lost Hours’ report series. Research findings The data also revealed that one in three...
HID, the pioneer in trusted identity solutions, announces its first RAIN RFID reader modules featuring the company’s TSL technology and the innovative STORM command protocol that simplifies embedded software integration. The modules enable developers to create customized reader hardware designs that take full advantage of the superior performance of Impinj E710 and E910 reader chips and their ability to support next-generation RAIN tags. Handheld and wearable devices The HID TSL RAIN RF...
ConnectWise, the software company dedicated to the success of IT solution providers (TSPs), announces the appointment of Raghu Ram Bongula as its new Chief Technology Officer. Bongula brings two decades of leadership with a focus on digital/cloud transformation, building new platforms, and modernizing legacy platforms. Prior to joining ConnectWise, Bongula served as Senior Vice President of Engineering at Global Payments, where he led a team responsible for building new products and platforms t...
Camera, Access Control, and LED lighting devices are rapidly moving towards using IEEE 802.3bt as their PoE standard for high PoE applications. The IEEE 802.3bt includes 8 Classes of PoE up to 90W. During the time this standard was under development, some security products required more power than the existing standards of IEEE 802.3af (15.4W) and IEEE 802.3at (30W) could provide. UPoE This led to the use of none standard types of PoE, such as UPoE which was adopted by most manufacturers, as...
Exterro, Inc., the provider of Legal GRC software, which unifies e-discovery, digital forensics, and data privacy to drive successful, defensible outcomes for in-house legal, IT teams, privacy, and law enforcement worldwide, has introduced Exterro Smart Data Inventory, a new solution designed to help organizations build, monitor and maintain a defensible privacy program based on a single intelligent and dynamic data inventory across record types, assets, 3rd parties, and processing activiti...
Symmetrium, Israeli mobile management and security platform, announces the launch of a closed beta for a selected group of enterprises who wish to transform their mobile enterprise operations and user experience. Since enterprise mobility is a major challenge for organizations undergoing digital transformation, Symmetrium has chosen DTX Europe 2022 as the formal launch site for its closed beta. BYOD solution As remote work doubled in 2022, alongside Bring-Your-Own-Device (BYOD) whic...
DigiCert, Inc., the provider of digital trust, announces that its Root Certificate Authority (CA) is approved by the Connectivity Standards Alliance (Alliance) for Matter device attestation. As the first Matter-approved root CA, also known as a Product Attestation Authority (PAA), DigiCert can now provide rapid time to market for smart home manufacturers looking to earn the Matter seal on their products. A multi-year participant in Matter, DigiCert contributed its expertise to the security and...
Originally scheduled to run from 30 November - 2 December 2022 at the Bangkok International Trade & Exhibition Centre, Messe Frankfurt’s technology fairs in Thailand will be held from 1 - 3 November 2023. The decision was made to allow the security, lighting, and building industries adequate time to recover. In addition, the Thailand Lighting Fair will be merged into the Thailand Building Fair to capitalize on the success of the fair’s smart city approach from previous editions....
Check Point® Software Technologies Ltd., a provider of cybersecurity solutions globally, has released the results from a new survey of the SMB cybersecurity market, conducted by research firm - Analysys Mason. It sought to uncover how SMBs are emerging from the pandemic, and how their business and technology needs are changing. The survey revealed that, while SMBs understand the need to invest in technology to support growth in the world of hybrid working, unfortunately, many fail to...
Ground Labs, the provider of data discovery solutions, announced its recognition as Compliance Software Solution Provider of the Year in the 6th annual CyberSecurity Breakthrough Awards. These honors acknowledge innovation, hard work, and success in a range of information security categories. The program attracted more than 4,100 nominations from around the world. GLASS Technology™ Powered by GLASS Technology™, Ground Labs’ Enterprise Recon significantly reduces the time req...
Aritech, a provider of security and life-safety solutions, is pleased to introduce a new immersive customer experience concept for visitors of the 360° Virtual Tour website. Aritech is a part of Carrier Global Corporation, the global provider of healthy, safe, sustainable, and intelligent building and cold chain solutions. 360° Virtual Tour Experience A 360° Virtual Tour experience, showcasing Aritech’s latest security technology for flexible office environments, is availabl...
OriginGPS, the pioneer in miniature GNSS modules and cellular IoT systems, will present its high-performance solutions, along with several prototypes addressing challenges and trends, such as sports performance monitoring, environmental health, and real-time tracking of practically everything that moves. Exhibited solutions Products exhibited at the show include a smart baseball providing and transferring raw data on pitches to the cloud, where it may be monitored and analyzed to rate ba...
ExtraHop, the pioneer in cloud-native network intelligence, announces that security and solutions provider Axians is using ExtraHop for its core security offering, the Circle of Visibility. This cybersecurity offering marries three solutions—NDR, EDR, and SIEM—to help organizations detect, investigate, and ultimately stop advanced attacks before they can do significant damage. Many organizations have a strong preventative posture, yet have fallen victim to a cyberattack. Significan...
Johnson Controls, the pioneer for smart, healthy, and sustainable buildings, is proud to announce that it has been named to the 2022 Fortune Change the World list, for its OpenBlue solutions and OpenBlue Net Zero Buildings as a Service offering. Fortune's Change the World list recognizes companies that use creative tools to address society's unmet needs and is evaluated based on measurable social impact, business results, and degree of innovation. First-of-its-kind digital solution OpenBlue i...
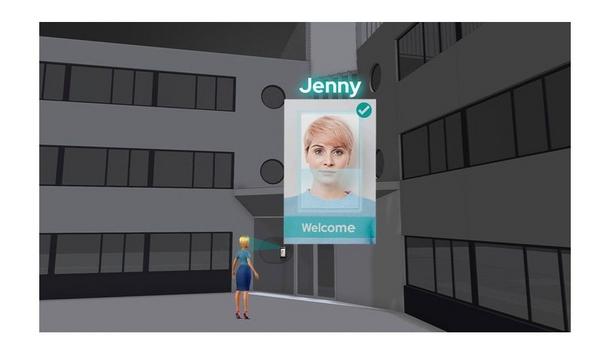
Adopting facial recognition in access control systems is widespread among businesses and organizations looking to improve building security. There are several important factors to consider when selecting a facial recognition access control system, such as the size of a building and the number of people who will use it. This article will provide an overview of how to choose the most suitable facial recognition access control system for a building security system. This will enable users to m...
This week, the UK Government announces that organizations can now apply for up to £200,000 of funding to support research into the cyber security of office devices which connect to the internet, to ensure they are properly protected against hackers. With UK businesses relying on enterprise IoT devices to increase productivity and enable hybrid working, these smart devices collect sensitive data, which can be accessed by other users, making them an attractive target for cyber criminals to...