Perimeter protection - Security beat
The excitement of ISC West 2019 continued until the very end – almost. Exhilarated by the first two busy days of the show, attendees and exhibitors seemed to welcome a slower third day. There were no complaints about booth traffic, and still plenty of thoughtful conversations taking place, everyone determined to maximize the value of face time with customers until the last second. Building An IoT Ecosystem In SAST At a show lacking in high-profile new technology announcements, the bigges...
From robots to drones to counter-drone solutions, a range of new technologies will be displayed at ISC West 2019. The Unmanned Security Expo will return, including a dedicated complimentary education theater for attendees offering sessions on a range of topics. UAVs, UGVs And Autonomous Systems Also included will be demos of the best UAVs (unmanned aerial vehicles), UGVs (unmanned ground robotics and vehicles) and autonomous systems on the market. The market growth for unmanned technologies be...
Constantly optimizing deep learning algorithms yields better video analytics performance, even in complex applications such as facial recognition or in scenarios with variable lighting, angles, postures, expressions, accessories, resolution, etc. Deep learning, a form of artificial intelligence (AI), holds the potential to enable video analytics to deliver on long-promised, but not often delivered performance. Our AI series continues here with part 2. Adapting Existing Hardware Today, low-co...
There is a new event on the calendar for the security industry in 2019: The Security Event 2019, 9-11 April, at NEC, Birmingham. For additional details and a preview of the new trade show and conference, we spoke with Tristan Norman, Founding Partner and Event Director, The Security Event. Q: It seems recently that some trade shows have been on the decline in terms of exhibit size and attendance. Why does the physical security industry need another trade show? Norman: I think there are numer...
ADT Inc.’s acquisition of Red Hawk Fire & Security, Boca Raton, Fla., is the latest move in ADT Commercial’s strategy to buy up security integrator firms around the country and grow their footprint. In addition to the Red Hawk acquisition, announced in mid-October, ADT has acquired more than a half-dozen security system integration firms in the last year or so. Here’s a quick rundown of integrator companies acquired by ADT: Protec, a Pacific Northwest commerc...
Several recent terrorist and mass violence attacks have been directed at soft targets, or relatively unprotected locations where people gather such as outside a music venue or in the unscreened passenger areas at airports. Attacks in public areas have led to the development of new security technologies aimed at protecting soft targets. One company addressing the challenges is Evolv Technology and its Edge automated high-speed personnel screening solution. The system integrates walkthrough fire...
A USB drive from Heathrow Airport, found on a London street in late October, contained confidential information about accessing restricted areas at the airport and security measures used to protect the Queen. The drive also contained a timetable for anti-terrorism patrols at the airport and documentation of the ultrasound system used by Heathrow security to check perimeter fences and runways for breaches. The data was not encrypted, and the London resident who found it turned it over to a newspa...
The massacre in Las Vegas is both sadly familiar and terrifyingly novel. Because of the recent series of violent attacks on innocent people gathered in public places, high body counts are no longer unheard-of, although the 59 dead after the Las Vegas tragedy sets a depressing new record. These news stories have become so grimly commonplace as to dull our collective sensitivity to their shock. However, the modus operandi of the latest attack, apparently by a “lone wolf” – caref...
The last two years have been pivotal for MOBOTIX, the German IP surveillance manufacturer. In 2016, the company entered into a share transfer agreement with Konica Minolta, a provider of advanced imaging and sensor solutions. More recently, the company has welcomed new CEO Thomas Lausten, who joins MOBOTIX with a wealth of experience from companies including Siemens, ADI Global Distribution and Milestone Systems. The changes have been accompanied by an updated look for the MOBOTIX brand, wi...
ISC West in Las Vegas kicked off Wednesday with an expanding focus on new technologies and new applications, including some that go beyond any narrow definition of “the security industry.” Qognify QBlock And Cloudscann “Technology is disrupting the market and executives are taking our solutions beyond security,” says Moti Shabtai, CEO and President of Qognify. “They are starting with security and quickly moving to other risk and business continuity issues in the...
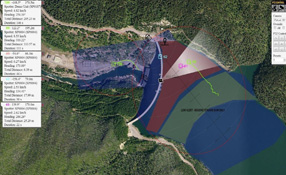
Using an asymmetric approach to perimeter security is more efficient and cost-effective. The approach, advocated by Applied Research Associates (ARA), involves strategic deployment of the company’s Pathfinder seismic-acoustic sensors. Asymmetric placement of the sensors is in contrast to typical perimeter security systems, which are linear: Sensors are distributed at specific intervals along a perimeter and require infrastructure to communicate back to a control center. Instead, asymmetr...
What happens to a company’s data in the case of a disaster such as 9/11 or Hurricane Sandy? How can a company recover from a disaster and continue their business uninterrupted? It’s a complicated challenge – and one many security professionals and risk management professionals must consider. Companies like Recovery Point provide resources to help a company survive a catastrophic event and keep its computer programs and business processes running. Their customers include large,...
The future of drones in the security and safety industry is sooner than you think. Tyco Integrated Security and Percepto offered a glimpse of that future at ASIS 2016: Autonomous drones that can patrol a perimeter 24 hours a day, seven days a week, managed remotely and able to perform multiple tasks on-site. The technology was developed by Israeli-based Percepto, based on innovation with roots in the Israeli military. Percepto has sharpened its focus on computer vision and applied it to allow d...
Perimeter security has evolved in recent years from an emphasis on fences and low-cost sensors to a broader systems approach that incorporates a variety of technologies. Protech is among the companies leading the transition and positioning itself as a one-stop systems provider at the perimeter. Mergers And Acquisitions In 2014, U.S.-based Protech merged with Sorhea, a French manufacturer of perimeter security systems. The combination expanded Protech’s business from one product to the a...
I have been unpacking from last week’s ASIS show in Orlando. It was a good show, except if you compare it to last spring’s ISC West in Las Vegas, which was especially well attended and generated a lot of excitement in the market. ASIS was definitely smaller, lower key and less crowded. And there were no big product announcements. But there was still plenty of technology on display. In particular, I saw the show reflecting several ongoing trends in the market. Impact Of M&As Me...
A long and hard-fought primary season in the United States will culminate this month when the major political parties nominate their candidates officially at their national conventions in Cleveland and Philadelphia. The rancorous campaign has raised concerns about possible civil unrest associated with both conventions, but security planners say they have considered every eventuality. Beyond possible civil disturbances, there have been no credible threats made against either convention, authoriti...
In a layered approach to security, the outermost layer increasingly might refer to an area outside a fence line. The sooner a facility is alerted to a possible threat, the better, and when a threat reaches inside a facility’s fence, it may be too late to mitigate it. Security directors need situational awareness that extends outside the facility and provides the ability to intercept intruders before they become a threat. Zones of interest, or buffer zones, outside a facility’s fence...
Video cameras were big news at the ASIS International Seminar and Exhibits in Atlanta, but the eagerly anticipated new 4K Ultra-HD cameras took a back seat to other camera innovations, including a rash of new panoramic view cameras in various flavors and types (including faster frame rates) and a renewed emphasis on cameras as intelligent system components. Samsung announced its new Open Platform program that leverages the added computing capacity of Samsung’s WiseNetIII computer chip ins...
If you had a super power, would you use it for good or evil? The question might typically be the subject of vigorous debate among third graders, but it’s also a question that comes up when you consider technology. Sometimes the benefits of technology are almost like super powers. As much as we seek to apply the powers of technology to security, there is also a criminal element that stands ready to use them with evil intent. Such is the case with drones. We have previously mentioned t...
Could Drones Be Used for Civilian/Commercial Surveillance Within Five Years? Drone strikes in war zones are reported routinely now in the news, but unmanned aerial vehicles (UAVs) or drones are still not common in commercial and civilian applications. Commercial uses may still be several years away, but is it too soon to start thinking about the possible security applications? Currently in the United States, Congress has directed the Federal Aviation Administration to come up with a plan by Se...