Industrial security systems
SharpEagle has been recognized as a key player in the global forklift 360-degree camera market, highlighted in the recent Forklift 360-Degree Camera Global Market Report by The Business Research Company. SharpEagle's advanced Bird's-Eye View Camera System leverages AI-powered stitching technology to deliver seamless 360-degree panoramic views around forklifts. This innovative solution enhances industrial safety by minimizing blind spots, improving situational awareness, and reducing accident ri...
The steute business division - Controltec has expanded its range of wireless foot switches to include a variant developed specifically for heavy-duty applications such as welding stations. In such applications, wireless foot switches really make sense because the lifetime of cabled foot switches can be limited due to weld spatter damaging the cables. And during normal work processes, the cables can also be a tripping hazard. Robust and extremely enlarged protective shield Conventional foot sw...
Corsha, the first and only Machine Identity Provider (mIDP) purpose-built to secure machine-to-machine (M2M) communication across operational systems and critical infrastructure, introduces a partnership and new platform integration with Dragos, Inc., a pioneer in operational technology (OT) cybersecurity. Together, Corsha and Dragos are transforming how organizations secure industrial systems by combining machine identity and threat detection to give security teams complete visibility, precis...
Hikvision hosted its 2025 HikTech Star Tour in Hangzhou, bringing together over 100 tech professionals to celebrate their outstanding video creations from this year's HikTech Star Show. Under the theme "Rising Stars, Reaching New Heights," participants discovered cutting-edge AIoT applications and strengthened connections within the global tech community. Real-world challenges Building on the strong momentum from last year, the HikTech Star Tour 2025 expanded its reach. "This isn't a one-time...
ADIPEC 2025, the upcoming global epicenter for oil and gas industry professionals seeking the latest technology advances, will see Teledyne Gas & Flame Detection present event visitors with a preview of its next-generation gas detector. Not set for official release until 2026, this exciting pre-launch will form one of six demonstration areas on the eye-catching stand, where the expert Teledyne Gas and Flame Detection team will be available to discuss optimal solutions to existing or new cha...
Mark Bridges, CEO of Ranger Fire and Security has been recognized as one of The LDC Top 50 Most Ambitious Business Leaders for 2025. The Top 50 was created by LDC, the private equity investor that is part of Lloyds Banking Group, in partnership with The Times. Now in its eighth year, the program continues to celebrate the drive and ambition of Britain’s best and brightest entrepreneurs. This year the program received almost 700 nominations, showcasing the exceptional individuals tha...
News
Hanwha Vision, a pioneer in security and surveillance solutions, introduces its bi-spectrum early fire detection cameras, combining dual thermal radiometry and visible imaging lenses for advanced fire detection, temperature monitoring, and reliable surveillance. Designed for critical environments such as industrial facilities, data centers, and electric vehicle charging stations, these cameras help identify potential fire hazards before they escalate, ensuring safety and operational efficiency. Advanced video analytics The TNM-C2712TDR and TNM-C2722TDR models utilize advanced video analytics to detect flames Fires can cause severe and costly property damage and life-threatening situations. The TNM-C2712TDR and TNM-C2722TDR models utilize advanced video analytics to detect flames through the visible channel, while the thermal sensor detects temperature changes. This dual-layered detection provides critical flame and temperature alerts, allowing users to take swift preventive actions before a fire spreads. Real-time temperature monitoring Beyond fire detection, real-time temperature monitoring enables proactive equipment maintenance. With support for up to two regions of interest, users can track minimum, maximum, and average temperature values, enabling precise event rule configurations. Furthermore, the cameras support a broad temperature detection range of −10°C to 450°C, making them suitable for diverse applications. Users can set predefined temperature thresholds, triggering alarms when variations exceed set limits. Visible and thermal images The ability to capture both visible and thermal images simultaneously ensures total situational awareness Equipped with a QVGA (160x120) thermal detector and wide-angle lenses, 95° for TNM-C2712TDR and 57° for TNM-C2722TDR, these cameras provide optimal coverage for short to medium-range monitoring, up to seven and 15 meters, respectively. The ability to capture both visible and thermal images simultaneously ensures comprehensive situational awareness, even in challenging conditions such as complete darkness, fog, or smoke. Hanwha Vision’s SUNAPI protocol Designed for seamless integration into security and industrial monitoring systems, these bi-spectrum cameras support the MQTT protocol for SCADA system compatibility, allowing efficient communication with industrial automation and control networks. Additionally, temperature data can be accessed with Hanwha Vision’s SUNAPI protocol, ensuring interoperability with various software platforms, including Wisenet SSM, Wisenet WAVE, and leading third-party VMS solutions. Bi-spectrum early fire detection cameras The models feature a durable, compact design suitable for both indoor and outdoor installations Built to withstand demanding conditions, the models feature a durable, compact design suitable for both indoor and outdoor installations. Their robust construction ensures long-term reliability in industrial environments. With cutting-edge fire detection, advanced temperature monitoring, and seamless integration, the bi-spectrum early fire detection cameras deliver enhanced safety and security for critical infrastructure. Key features of the bi-spectrum early fire detection cameras Bi-spectrum early fire detection with video analytics and thermal sensors. SCADA integration using the MQTT protocol for seamless data transmission. VMS compatibility with Milestone, Genetec, Wisenet SSM, and WAVE. Compact design for easy installation in tight spaces. 24/7 monitoring in complete darkness, fog, and harsh conditions. Discover how these intelligent thermal cameras can elevate the fire prevention and monitoring strategies now.
WAGNER Group GmbH has been awarded the GIT SECURITY AWARD 2026 in the "Fire protection" category. The award was given for the innovative OxyReduct F-Line oxygen reduction system, which actively prevents the outbreak of open fires under defined conditions. The system expands on the proven method of oxygen reduction with hydrogen-based fuel cell technology, which also enables an emission-free energy supply. The key advancement lies in the combination of a protective atmosphere and a self-sufficient energy supply. OxyReduct F-Line thus ensures continuous fire prevention with CO2-neutral operation – a milestone in preventive fire protection. Continuous oxygen reduction The solution is specially designed for applications with high availability and protection requirements. It really comes into its own in automated or deep-freeze warehouses, data centers, and archives, where conventional extinguishing systems reach their limits. Thanks to continuous oxygen reduction, fires cannot start, and damage from extinguishing agents or residues is avoided. With this award, the jury, the voting experts and industry insiders recognize both WAGNER's technical innovation, as well as its strategic commitment to consistently combining sustainability and safety. The OxyReduct F-Line is thus exemplary of a new generation of fire protection that takes on responsibility and actively drives change.
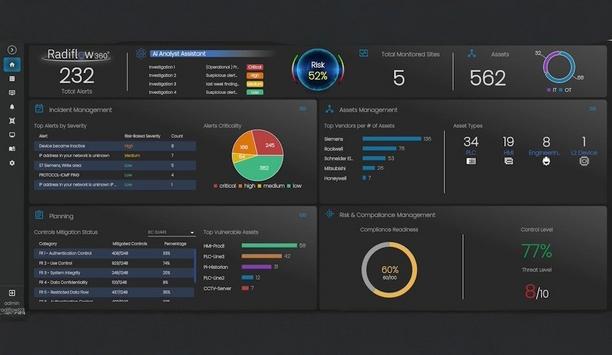
Radiflow, a pioneering provider of cybersecurity solutions for industrial automation networks, announced that the company has launched the new Radiflow360, a unified, AI-enhanced OT cybersecurity platform that delivers full visibility, risk management and streamlined incident response for mid-sized industrial enterprises. Radiflow360 now enables mid-sized industrial operators to gain full visibility and control over their OT networks and risks, and is supported by an AI analyst assistant that speeds up assessments and prioritizes threats. Unified approach to OT cybersecurity The built-in AI analyst assistant seamlessly interfaces with retail GenAI engines to bridge skill gaps This new platform streamlines compliance, accelerates incident response and integrates seamlessly with other Radiflow and third-party tools, delivering a scalable, unified approach to OT cybersecurity. The built-in AI analyst assistant seamlessly interfaces with commercial GenAI engines to bridge skill gaps and accelerate incident investigation. Initial phases of asset discovery Radiflow360 targets OT security teams at mid-sized industrial enterprises that need comprehensive, real-time control of their operational environments, but often struggle with manual processes and siloed tools. The platform frees these organizations from the need to juggle multiple systems by unifying intrusion and anomaly detection with the initial phases of asset discovery and risk assessment in a single pane of glass. New Radiflow360 platform For Radiflow’s partners, the new Radiflow360 platform offers a centralized solution to deliver scalable services This integrated platform enables precise asset mapping, automated risk and compliance scoring, streamlined security control planning and continuous anomaly monitoring, dramatically reducing complexity and accelerating response times. For Radiflow’s partners, the new Radiflow360 platform offers a centralized solution to deliver scalable, differentiated OT security services to their mid-range industrial enterprise and OT operator customers. OT Managed SOC service “Barrier has been working with Radiflow for many years and the company’s solutions add significant agility to our OT Managed SOC service we provide to industrial enterprises across the UK,” said Iain Slater, Sales Director at Barrier Networks. “The new Radiflow360 platform, in particular its unified approach to OT security, is exactly the kind of innovation our mid-market OT operator customers need at a time when UK industrial organizations are facing an increasing wave of targeted OT cyber-threats.” OT cybersecurity risks and threats “2025 marks a pivotal year for Radiflow — we have doubled our sales in the first half of the year and are stepping forward with a renewed focus on our mission to deliver solutions for our industrial enterprise and critical infrastructure customers and partners to efficiently manage the lifecycle of OT cybersecurity risks and threats,” said Ilan Barda, CEO at Radiflow. “The launch of our new Radiflow360 platform is an exciting milestone in our ongoing mission with a focus on providing mid-market industrial operators with a unified framework to manage their OT security lifecycle - from asset discovery to risk assessment and anomalies monitoring to AI-powered risk assessments and prioritizations." Radiflow will be presenting its new Radiflow360 platform at the IT-SA Expo Congress on October 7 to 9 in Nuremberg, Germany.
Omny has selected Thomas Fetten to lead its next phase of growth, as the company helps organizations around the world make sense of complex operational data, identify hidden security risks, and better protect critical infrastructure. Fetten will officially assume the role on 1 October 2025. Fetten brings more than 25 years of global leadership experience in technology, cybersecurity, and managed services, including senior executive roles at Deutsche Telekom Security, Secure Link/Orange Cyber Defense, and IBM. He also advised private equity funds on technology and cybersecurity investments, driving international expansion and transformation. With Fetten stepping into the CEO role, Omny is reinforcing its ambition to broaden its footprint and strengthen relationships with customers and partners in Europe and internationally. New stage of growth In his new role, Fetten will focus on strengthening Omny’s role as a trusted provider of operational technology “Omny is entering a new stage of growth, beyond Norway,” says Chairman of the Board, John Markus Lervik. “After an extensive search, we found that Fetten’s experience working with major European security providers, along with his deep understanding of both clients and partners, make him the right leader to position Omny as the go-to security partner for operational resilience.” In his new role, Fetten will focus on strengthening Omny’s role as a trusted provider of operational technology (OT) security solutions. His vision emphasizes customer impact, technological innovation, and global growth. Protecting critical infrastructure “We have a unique opportunity to help organizations protect critical infrastructure at a time when cyber and physical risks are converging,” says Thomas Fetten. He continues, “I see Omny as one of Norway’s best-kept secrets, with the potential to become a global leader in OT security. Together with the team, I look forward to sharpening our long-term vision, working closely with our clients to address their urgent OT security challenges, and partnering with managed security service providers, OEMs, and others to bring our solutions to more organizations.” Fetten, a German national who grew up in the United States, will be based in Europe and spends significant time with Omny’s teams, clients, and technology partners across regions. Fetten’s arrival marks the beginning of a new chapter for Omny, centered on the alignment of Omny’s product and goals, and closer collaboration with customers and partners, extending the reach of its OT security solutions.
Flexxon, a pioneer in industrial NAND flash storage, announced the launch of X-Mask Pro – the next evolution of the company's best-selling X-Mask. Designed to secure and conceal sensitive data in mission-critical operations, X-Mask Pro delivers plug-and-play functionality, paired with unmatched durability, built-in encryption, and regulator-ready compliance, ensuring that vital information remains secure, intact, and invisible to unauthorized individuals. Infrastructure monitoring and autonomous systems Flexxon provides firms with a rugged, secure, and regulator-compliant key that conceals vital data As industries worldwide generate growing volumes of sensitive operational data - from aerospace and defense to infrastructure monitoring and autonomous systems - protecting this data at the source has become a pressing priority. With X-Mask Pro, Flexxon provides enterprises with a rugged, secure, and regulator-compliant solution that conceals confidential and vital data in field operations. Digital economy Camellia Chan, CEO and Co-founder of Flexxon, said: "Data is the most valuable asset in today's digital economy, and it must be protected at the source. Especially in industrial applications, data captured must remain secure and inaccessible to unauthorized individuals at all times." "With X-Mask Pro, we are strengthening our leadership in secure storage to deliver a solution that is not only physically resilient but also digitally impenetrable – all while prioritizing usability with plug-and-play functionality. Our goal is to make it easy to use for authorized parties, and impossible for prying eyes to reach their target." Industrial-grade security and reliability X-Mask Pro delivers a powerful combination of durability, encryption, and endurance Building on Flexxon's long-standing prowess in developing secure industrial memory solutions, X-Mask Pro delivers a powerful combination of durability, encryption, and endurance. Rigorously tested to withstand extreme temperatures from −40°C to 85°C, high humidity, shock forces up to 1500G, vibrations, and drops from 1.5 meters, X-Mask Pro delivers consistent performance under the most demanding conditions. It is also tested against bending stress, torque, and electrostatic discharge (ESD) up to ±8kV, ensuring resilience during real-world deployment. X-Mask Pro's hardware-based encryption At the same time, X-Mask Pro's hardware-based encryption and data concealment capabilities ensure that sensitive data remains invisible and unreadable to unauthorized users. Together with these functions, proprietary software authentication controls through the X-Mask Pro Tool, allow for seamless setup and configuration by users to conceal or unlock the data stored. Beyond resilience and security, X-Mask Pro is fully regulator-ready, meeting the strictest global compliance requirements - from General Data Protection Regulation (GDPR) to national security and legal standards - and is built to support nonstop, high-volume recording across advanced applications such as HD video, LiDAR, and multispectral sensors. How X-Mask Pro works X-Mask Pro is resistant to extreme environmental stress, ensuring that data not only remains secure At its core, X-Mask Pro integrates hardware-based encryption with proprietary authentication controls to safeguard sensitive data from interception or tampering. Unlike standard memory cards that can be easily removed, stolen, and read, X-Mask Pro ensures that all stored information remains concealed and encrypted without authorized access. Combined with Flexxon's industrial-grade engineering, X-Mask Pro is resistant to extreme environmental stress, ensuring that data not only remains secure but also intact. This makes X-Mask Pro uniquely capable of addressing both security threats and environmental risks, offering end-to-end assurance for industries and professionals who require uncompromised data integrity. Prioritising ease of use Users first activate card security on their PC, creating a protected environment for all future use X-Mask Pro is designed to make security seamless. Users first activate card security on their PC, creating a protected environment for all future use. Once activated, the card can be inserted into any device with a microSD slot, and used normally, with contents remaining fully readable during operation. The difference comes when the card is removed or the device is powered off. At this point, all data is automatically encrypted and hidden, making it unreadable to anyone without authorization. To access the content again, users simply authenticate and unlock the card on a PC using a secure PIN. X-Mask Pro delivers automated protection This process ensures that data is always available to authorized users, while remaining completely inaccessible to anyone without proper access or authorization. From professional photographers managing high-value shoots to surveillance operators safeguarding sensitive footage, X-Mask Pro delivers peace of mind through end-to-end, automated protection. Available now in capacities from 64GB to 128GB, X-Mask Pro can be purchased online through Flexxon's eStore or any of the global authorized retailers.
ABB has been recognized as a pioneer in the 2025 Gartner® Magic Quadrant™ for Global Industrial IoT Platforms. ABB views the recognition as a reflection of the company’s continued commitment to delivering innovative industrial AI and IoT solutions that empower industries to operate leaner and cleaner. Data-driven business outcomes “Being recognized by Gartner® four consecutive times and now positioned as a Leader is a proud moment for ABB and we see it is a testament to our focus on innovation and delivering data-driven business outcomes for customers,” said Rajesh Ramachandran, Global Chief Digital Officer, Process Automation, ABB. He adds, “We believe this recognition highlights not only our robust strategy on Industrial IoT, but also our proven capability to deliver on it. We are providing scalable, AI-powered solutions that help customers address real operational challenges and outperform, while future-proofing their journey towards autonomous operations.” Integration and contextualization of real-time data ABB Genix Industrial IoT and AI Suite is an enterprise-grade platform that provides seamless integration The Gartner® Magic Quadrant™ provides a graphical competitive positioning of four types of technology providers, in markets where growth is high and provider differentiation is distinct: Leaders, Visionaries, Niche Players and Challengers. Leaders execute well against their current vision and are well-positioned for tomorrow. ABB Genix Industrial IoT and AI Suite is an enterprise-grade platform that provides seamless integration and contextualization of real-time data from operational technology (OT), information technology (IT) and engineering technology (ET) systems. It enables advanced analytics and AI-driven decisions, empowering industrial customers to transition to intelligent operations through smart manufacturing. Genix comprehensive capabilities Genix helps industries by offering comprehensive capabilities, such as data integration, application enablement and management, applied AI, security, and implementation ease and scalability. It also supports key use cases, including industrial automation, predictive maintenance, digital twins, industrial data management and sustainability. Data management and self-service analytics Genix helps industries from energy to manufacturing and maritime to accelerate time‑to‑value excellence Genix features a modular architecture, enterprise system integration, industry-specific models and flexible deployment options across cloud, edge and hybrid environments. The platform’s Industrial DataOps layer enables contextual data management and self-service analytics. Its application management provides tools for developing and handling both native and third-party applications via APIs – standardized interfaces that allow different software systems to exchange data seamlessly. With pre‑built applications for asset performance, sustainability, digital twins and autonomous operations, Genix helps industries from energy to manufacturing and maritime to accelerate time‑to‑value and achieve operational excellence. GenAI with real-time actionable insights Advanced capabilities, such as Genix Copilot and Metrics Hub, unlock the power of GenAI with real-time actionable insights across the field and shop floor engineers, functional specialists, and industry executives, driving collaborative decision-making and boosting productivity. ABB has developed a strong partner ecosystem for Genix, including strategic collaborations with Microsoft and RedHat, which help expand market reach and deliver greater value to customers.


Expert commentary
Amidst the challenges of a prevailing economic downturn, the retail sector finds itself grappling with an unparalleled rise in incidents of shoplifting, theft, and burglaries. The disconcerting scenes witnessed on London’s Oxford Street in August 2023, where crowds gathered, looting as many stores as possible, sent shockwaves across the nation’s retailers. This alarming surge in retail crime has put retailers on high alert, as they contend with a rising tide of security concerns. Shoplifting concerns Recent data from the Union of Shop Distributive and Allied Workers (USDAW), has raised alarming concerns: shoplifting rates have surged by an unprecedented 24%. In the first half of 2023 alone, there were approximately 8 million reported shoplifting incidents. With the ongoing burden of the cost of living crisis and the approaching festive season, it is expected that these figures will keep surging. Implementing robust security measures Theft and prevention strategies cost retailers approximately £2 billion in 2021/2022 While more help from the Government to support retail workers and the businesses shoplifters target is certainly needed, the implementation of robust security measures will significantly contribute to deterring these crimes from occurring in the first place. British retailers spend millions on tools to deter and catch shoplifters inside stores, from CCTV and security guards to electronic tagging and alarms. The Grocer reported that theft and prevention strategies cost retailers approximately £2 billion in 2021/2022. Despite these initial costs, other threats are at play beyond the shop floor. Break-ins by criminal gangs For many large town center stores and supermarkets, and units in retail parks, the rear doors and delivery areas are commonly targeted by criminal gangs. It’s not uncommon for thefts to occur from pallets or cages that have been unloaded from lorries and sit waiting to be moved into the building. After-hours break-ins are a risk for all store owners too, particularly over the festive season when a lot of high-value stock has been delivered to shops and supermarkets. Addressing anti-social behaviour The additional fencing was deemed an essential measure to safeguard the community Anti-social behavior also poses a challenge for retailers. In 2022, an Aldi based in Derby invested in security fencing to protect staff and deter loitering groups. The additional fencing was deemed an essential measure to safeguard the community, as dangerous items were frequently found outside the store, including weapons and hypodermic needles. So how do physical security solutions such as fencing and gates help better protect retail establishments such as supermarkets and edge-of-town retail park shops? Fencing and gates: a critical component of retail security 1. Risk assessment and target hardening A thorough risk assessment will identify potential weak spots that require protection. ‘Target hardening’ involves implementing physical security measures that become more robust as they approach the target. This helps deter intruders while ensuring ease of access for customers and staff. 2. Effective perimeter security Opt for difficult-to-climb security fencing that provides a robust obstacle against thieves, vandals, and intruders Selecting fencing solutions according to the potential threats, site characteristics, and topography is crucial. It is important to specify fencing that strikes a balance and maintains a welcoming appearance while safeguarding external areas of the store or warehouse from potential harm and unauthorized access. Solid fencing which provides concealment can help to conceal expensive goods and remove them as a target for opportunistic theft. Opt for difficult-to-climb security fencing that provides a robust obstacle against thieves, vandals, and intruders. I recommend selecting a sufficiently tall and robust fence such as an acoustic barrier. Its noise-reducing properties are often beneficial for these types of sites too. 3. Controlling vehicular speeds and access To enhance security, consider controlling vehicular speeds and access. One effective approach is the installation of bollards at the ends of traditional high streets. This practice is already commonplace as a means of safeguarding against hostile vehicle attacks, but it can also play a pivotal role in preventing quick getaways of vehicles involved in potential heists. Additionally, employing road blockers and sliding gates at the rear entrances of delivery areas would serve to fortify security further. These measures can help in delaying vehicles, allowing for necessary checks to be conducted. 4. Balancing security with aesthetics The presence of high-security fencing can also make a site more of a target for vandals and burglars Another challenge is avoiding creating an imposing presence, especially important for areas situated near residential communities. The presence of high-security fencing can also make a site more of a target for vandals and burglars. To minimize this risk consider specifying timber fencing and traffic barriers to secure car parks, providing both security and a welcoming atmosphere for shoppers. Taking an integrated approach Combine secure perimeter fencing with effective lighting in places with shaded areas and at doors, gates, and shop windows, alongside Perimeter Intrusion Detection Systems (PIDS), and strategically placed CCTV. These measures will hinder unauthorized entry and escape, increasing the likelihood of detection and apprehension. Prioritising employee wellbeing Installing robust security fencing, complemented by CCTV, good lighting, and guarding, creates a safe environment Installing robust security fencing, complemented by CCTV, good lighting, and guarding, creates a safe environment for employees. This not only safeguards their well-being but also provides peace of mind that they are protected effectively in the case of a burglary or crime. When selecting security products for retail sites, it is advisable to opt for items that have undergone rigorous testing and carry relevant certifications for their security level. Each component should meet industry-specific standards for its intended purpose and originate from manufacturers accredited under ISO 9001:2015. This ensures a high standard of quality and reliability in safeguarding the premises. High-quality security fencing As the cost-of-living crisis continues, crime rates increase, and the festive season approaches, the time to act and implement on-site security is now. By investing in comprehensive security measures, retailers can protect their assets, employees, and customers, ensuring a safer and more secure shopping environment for all. High-quality security fencing is also a sound investment, that requires little or no maintenance once installed. The best fencing solutions are extremely weather-resistant, and won’t suffer from rust or corrosion. With all sectors preparing to ride the rapids of recession in the coming year, improving on-site security while selecting cost-effective measures, is one surefire way to protect your people, your property, and your profits from harm.
The average business owner or investor has some kind of security precaution in place, especially in the after-hours when there are fewer deterrents to inhibit criminal activity. Security guards, video surveillance systems, motion sensor lights, or even just fake cameras placed around the property are some of the common options people choose. Future of overnight security Smart business owners are starting to realize, however, that some of these traditional security measures are becoming antiquated and no longer cutting. The now and future of overnight security is in remote guarding. Pioneered by companies like Los Angeles-based Elite Interactive Solutions, which was founded back in 2007, remote guarding is revolutionizing the overnight security business. Minimizing criminal activity Remote guarding is fast becoming the most popular choice among commercial end-user property owners Remote guarding utilizes a combination of cutting-edge technology, “digital guards,” highly trained security agents, and local law enforcement if and when necessary to minimize the potential of criminal activity. For those adequately enlightened to its overwhelmingly impressive crime prevention capabilities, remote guarding is fast becoming the most popular choice among commercial end-user property owners to secure and protect their investments. What Is Remote Guarding? Remote guarding is a revolutionary concept and increasing trend in security systems that utilize a combination of methods to effectively analyze potential threats to property. Cameras and/or other monitoring devices running highly advanced algorithmic software are installed in strategic areas or vulnerable places onsite and remotely located security agents are immediately notified of any activity within a designated perimeter of the property. A blend of AI, cybersecurity, and video analytics When properly deployed by an expert provider, the technology stack includes a proprietary blend of video analytics, artificial intelligence, cybersecurity, and more. Done right, “noise” is effectively filtered out, allowing agents to act on legitimate alerts and achieve zero false alarms communicated to first responders. Today, there are a lot of terms and descriptions tossed around about remote guarding, remote video, virtual guarding, etc., but those attributes must be present to represent the true definition of the offering and its many virtues. Realtime situational awareness Many systems have a two-way speaker that allows the security agent to give a verbal warning When specially trained security agents are alerted to trespassers, possible intruders, or other suspicious activity, they analyze the situation in real time and determine the necessary level of action. Many systems have a two-way speaker that allows the security agent to give a verbal warning, known as a voice-down, to the individual(s) that they are being watched. Most perpetrators, often believing the response is emanating directly from security personnel on the property itself rather than from a remote command center, flee immediately. However, if the threat persists, the security agent enlists local law enforcement to get on the scene. Customized remote guarding When properly deployed, remote guarding systems are also customized to specific properties. A team of consultants visits the client’s property to evaluate its vulnerabilities and where to best place cameras and/or other monitoring devices for system efficacy. Traditional Security Shortfalls According to Keith Bushey, a retired commander for the Los Angeles Police Department, there is much frustration between law enforcement officers and potential victims of crime due to the historically unreliable performance of traditional burglar alarm systems and central monitoring stations. He states about 90% of security-related calls are false alarms, a problem that has been well-documented through the years. Onsite challenges When a legitimate emergency does occur, the perpetrators have often already done their damage When a legitimate emergency does occur, the perpetrators have often already done their damage and/or escaped by the time law enforcement arrives. Onsite security guards are not the remedy either as they bring their own set of issues and challenges. Unexpected costs Traditional security systems can also have unexpected costs. The cost is not only in the security guards’ paycheck or the cost of the equipment itself. The cost comes when an actual incident occurs. In worst-case scenarios, the security guard(s) are injured, the business suffers inventory loss, and/or damage is sustained to the property. The medical and other costs for the security guard(s), the loss of inventory, property damage, deployment of law enforcement resources, and possible fallout of legal expenses all add up. Even in the best-case scenario, false alarm expenses incur if law enforcement is dispatched. These, among many others, are some of the primary issues that remote guarding resoundingly answers as a superior alternative. A Bounty of Benefits Remote guarding systems have been proven to cut costs and be more effective than traditional security systems. Even though the monthly monitoring costs of remote guarding are significantly higher than traditional intrusion detection system monitoring, the much higher effectiveness in crime reduction, elimination of false alarms, and augmenting or replacement of manned guards result in a substantially higher return on investment (ROI) to the end user. Easy tracking of threats The security cameras already have their image captured on record, making them easier to track down For example, case studies have demonstrated reduced security costs for clients by 60%, on average. These reductions have come from the costs of security staff, inventory, or property loss, plus saving money on insurance premiums and deductibles. The nature of remote guarding reduces the risk and costs of false alarms, with professional security agents able to determine an actual threat before law enforcement is called. In a rare instance when a perpetrator escapes before law enforcement arrives or can detain the individual(s), the security cameras already have their image captured on record, making them easier to track down and identify. Reduction of false alarms The significant reduction in false alarms is greatly appreciated by law enforcement, as it allows them to focus on real emergencies or crises. Better relationships are also developed between clients and law enforcement, as remote guarding systems are highly reliable in providing accurate and real-time information to officers as they approach the scene. In short, it assists law enforcement in doing their job more effectively, as well as more safely thanks to having eyewitness information before engaging in an active crime scene. Partnership When you combine the decreased cost with the increased efficiency and success rate, it is easy to see why many commercial end-user property owners across the country are making the shift to remote guarding. It’s also an outstanding opportunity for professional security dealers and integrators to partner with a remote guarding services provider to bring a superior solution to their end customers and pick up a recurring monthly revenue stream in the process.
The autumn equinox, which marks the start of autumn, occurs this weekend on Saturday, September 23. With darker evenings ahead, the experts at ADT have shared five ways to maximize your home's security. Author's quote Michele Bennett, General Manager at ADT UK&I comments: “Opportunistic thieves use darkness to their advantage, so it’s no surprise that the number of burglaries committed increases when the darker nights draw in." He adds, "Our 2022 burglary report found that burglaries are most common at night, with 58% of burglaries occurring between 6 p.m. and 6 a.m. Taking steps to optimize your home’s security before the clocks go back this year will provide reassurance that your property is as secure as possible.” Five ways to secure your property: Get a monitored alarm installed: A visible alarm system is a strong deterrent to potential burglars, as criminals are less likely to target a home that is protected. In the event of a break-in, a monitored alarm will alert you, your keyholders and depending on the package you take out, the police, ensuring a swift response to an alarm activation. Light up the dark: Well-lit exteriors make your home less appealing to potential intruders. Install motion-activated lights around any entry points, particularly porches and gardens, which alert you to movement on your property. This will also prevent burglars from operating under the cloak of darkness and increase the chance of a passerby spotting suspicious activity. Trim your garden landscape: Thieves look for escape routes and hiding spots when deciding which homes to break into, making gardens with high, overgrown hedges more likely to be targeted. This is especially true in the darker evenings, so be sure to give your garden a thorough tidy-up to make your property less likely to be targeted. It’s also advisable to ensure any tools are locked away in sheds and garages that could assist a burglar such as ladders, or a garden spade to force entry. Be smart with your lights: Using smart plugs allows you to turn on a few well-appointed lights and radios or televisions from any location from your phone. Used in conjunction with an outdoor camera or video doorbell, you can have lamps plugged into smart plugs come on when motion is detected. Programming lights to come on at different times throughout the night will help to deter burglars by making your property look occupied. Purchase a smart doorbell or outdoor camera: Smart doorbells are an effective way to deter burglars as they provide evidence in the event of a break-in, package theft, or other suspicious activity around your home. They also notify you when someone is at your door reducing the chance of you being caught out by a late evening or early morning robbery. Further encroachment Smart doorbells also act as a deterrent to unscrupulous door-to-door sellers and con artists, as video footage is recorded. In the event of a late-night door knock, you can see and speak to whoever is at your front door, without having to open the door. ADT’s new outdoor camera also has two-way audio and a high-pitch deterrent siren so you can warn off anyone from your property to deter any further encroachment.
Security beat
Companies at GSX 2023 emphasized new ways that technologies such as artificial intelligence (AI) and the cloud can address long-standing issues in the security market. Among the exhibitors at the event in Dallas were companies seeking creative ways to apply technology, lower costs, and make the world a safer place. Reflecting on the exhibition, here are some additional takeaways. Expanding AI at the edge i-PRO is a company reflecting the continued expansion of edge AI capability in the security market. Today, more than half of the company’s lineup supports AI at the edge so the customer has a wide choice of form factors when seeking to leverage the feature set. AI processing relay, extended warranty i-PRO is increasing their warranty period from 5 to 7 years, which could be a lifetime warranty in some cases I-PRO also has an “AI processing relay” device that accepts non-AI video streams and applies edge analytics. AI has progressed from a high-end technology to a feature available in a variety of cameras at different price points. i-PRO is also increasing its warranty period from 5 to 7 years, which could be a lifetime warranty in some cases depending on a customer’s refresh schedule and lifecycle management. Active Guard, MonitorCast The company’s video management system (Video Insight) is continuing to build new features including “Active Guard,” an integrated metadata sorter. Their access control platform, MonitorCast, is a Mercury-based solution that is tightly integrated with Video Insight. Their embedded recorders now have PoE built in. “We can move at a faster pace to fill out our product line since leaving Panasonic,” says Adam Lowenstein, Director of Product Management. “We can focus our business on adapting to the market.” Emphasis on retail and other verticals Shoplifting is a timely issue, and retail is a vertical market that got a lot of attention at GSX 2023. “We see a lot of retailers who are primarily interested in protecting employee safety, but also assets,” says Brandon Davito, Verkada’s SVP of Product and Operations. “Shrinkage is a CEO-level priority.” “Retailers are getting more engaged with security posture, instead of letting perpetrators walk,” Davito adds. Intrusion detection Verkada has an intrusion product that will notify a central station if there is an alarm On the alarm side, Verkada has an intrusion product that will notify a central station if there is an alarm, and operators can review videos to confirm the alarm. Other capabilities seeking to discourage trespassers include sirens, strobes, and “talkdown” capabilities. International expansion Verkada continues to expand internationally with 16 offices in all, including Sydney, Tokyo, and London. The core value proposition is to enable customers to manage their onsite infrastructure more simply, including new elements such as PTZ cameras, intercoms, and visitor management. Verkada emphasizes ease of use, including a mobile application to allow access to be managed across the user base. Forging partnerships “We are committed to the channel and industry, and we continue to build relationships and expand our reach,” says Davito. Among the industry relationships is a new partnership with Convergint, which was hinted at during the show and announced later the same day. They are also expanding their partnerships with Schlage, Allegion, and ASSA ABLOY. Working with other verticals They offer new features for K -12 schools, and a new alarm platform is easier to deploy and manage Verkada has also found success across multiple other verticals, notably healthcare, where they integrate with an electronic medical records system. They offer new features for K-12 schools, and a new alarm platform is easier to deploy and manage. They are integrating wireless locks to secure interior doors in schools, looking to secure the perimeter, and installing guest management systems. Transitioning the Mid-Market to the Cloud Salient is squarely focused on the “mid-market,” a large swath of systems somewhere between small businesses and enterprise-level systems. Pure cloud systems are not as attractive to this market, which has a built-out infrastructure of on-premise systems. Adding a camera to an existing system is easier and less expensive than tying it to the cloud. Benefits of cloud It’s a market that may not be ready for pure cloud, but there are benefits to be realized from adding a cloud element to existing systems. “We are continuing to augment our premise-based solutions with added cloud capabilities and flexibility,” says Sanjay Challa, Salient’s Chief Product Officer. The feedback Salient hears from their customers is “I want to own my data.” The hybrid cloud approach offers the right mix of control, flexibility, and unit economics. Cloud add-on capabilities We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive" Cloud add-on capabilities include bringing more intelligence about system operation to the user via the cloud. Over time, Salient expects to sell more cloud-centric offerings based on feedback from integrators and customers. “We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive over time,” says Challa. Vaidio AI technology Salient seeks to be a transition pioneer to help customers realize the path to the cloud. Their approach is “crawl, walk, run,” and helping customers make the transition at each stage. Salient has added AI to its product offering, incorporating Vaidio AI technology from IronYun into a powerful suite and broad array of on-premise analytics, which are gaining traction. The seamless approach makes it easy for customers to embrace AI analytics, although Salient remains broadly committed to open systems. Addressing ‘Soft’ Features for Integrators AMAG is in the process of enhancing its product line with the next generation of access control panels. However, “product” is just part of the new developments at AMAG. In addition to “hard” features (such as products), the company is looking to improve its “soft” features, too; that is, how they work with the integrator channel. Integrator channel Rebuilding a process to make your organization more efficient, is relatively easy; it just takes a lot of persistence" “We have the depth of our legacy customer base we can learn from, we just need to close the feedback loop quicker,” says Kyle Gordon, AMAG’s Executive Vice President of Global Sales, Marketing, and commercial Excellence, who acknowledges the value of reinstating face-to-face meetings after COVID. “We are laser-focused on nurturing our integrator channel,” he says. “Developing new features takes time, but rebuilding a process to make your organization more efficient, that’s relatively easy; it just takes a lot of persistence,” says Gordon. More cohesive internal communication is another useful tool, he says. Disrupting the cloud based on price Wasabi is working to make cloud applications less expensive by offering a “disruptive” price on cloud storage, $6.99 per terabyte per month (80% less than hyperscalers). Contending “hyperscalers” like AWS are charging too much for cloud storage, Wasabi is using its own intellectual property and server equipment co-located in data centers around the world. Wasabi sells “hot cloud storage,” which refers to the fact that they only have one tier of storage and data is always accessible. In contrast, a company such as AWS might charge an “egress fee” for access to data stored in a “colder” tier. Cloud storage “We saw that several video surveillance companies had not yet adopted cloud storage, and we saw an opportunity to make it easy to use,” said Drew Schlussel, Wasabi’s Senior Director of Product Marketing. “We just install a little bit of software that allows them to store data in the cloud and bring it back from the cloud.” Performance, protection (cybersecurity), and price Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies such as Genetec and Milestone. Emphasizing performance, protection (cybersecurity), and price, their data centers are certified to SOC 2 and ISO 27001 standards. Faster throughput for weapons detection Xtract One is a young company focusing on weapons detection in a time of accelerated concern about gun issues post-COVID. Founded in Canada and based on technology developed at McMaster University, Xtract One has found a niche in providing weapons detection at stadiums and arenas. These customers already have budgets, and it is easy to shift the money to a newer, faster technology. Madison Square Garden in New York City is among its customers. Cost savings solution Xtract One can increase throughput to 30 to 50 people per entrance per minute (compared to 5 to 6 people per minute when using metal detectors). The solution doesn’t require anyone to empty their pockets and the system alarms on items beyond guns and knives. Using Xtract One allows customers to reduce the number of screening lanes and security staff, providing additional cost savings, all while getting fans through the screening process in half the time. Purpose-built sensors The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties In addition to stadiums and arenas, Xtract One, formerly Patriot One, is also getting “inbound” interest from schools, hospitals, manufacturers, and other verticals that makeup 50% of their business. “We’re on a rocket ride, mainly because the weapons issues are not going away,” says Peter Evans, CEO and Director at Xtract One. The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties, all correlated by an AI engine. Providing early warning of violence ZeroEyes is another company focused on weapons detection. Their AI gun detection system works with video images to identify if someone is “brandishing” (carrying) a weapon. In other words, the system does not detect concealed weapons. Identifying someone carrying a weapon provides early warning of a possible violent act. Increased response with AI-enables images Images are identified by AI and sent to a monitoring center where a human confirms the image before contacting first responders. Knowing the location of a shooter enables staff to lock entry points, move people to safety, and direct first responders. The company was founded to leverage existing camera views to stop mass shootings and gun violence by reducing response times.
A pioneer in the access control sector since 1971, AMAG Technology is looking to the future and the next generation of products that will expand its services to customers. “In our vision, we have advanced approaches that will not only provide our partners with advanced technologies but also ones that are easier to install with tools to expand their services,” says David Sullivan, who was appointed President of the venerable access control company in September 2022. New challenges at AMAG Sullivan brings a new outlook to the AMAG business, a part of Allied Universal, and a new vision to lead the company into the future. We caught up with David Sullivan to discuss his new challenges at AMAG and the journey ahead as the company looks to the future. Q: How does your background inform your approach to leading AMAG? I believe that it helps me to define a vision for AMAG that will be unique and on the leading edge of our industry David Sullivan: With the exception of only a few short years, my career has been in access control. I have experience with several systems and have had the privilege to manage several successful access control companies. As a result, I bring a great deal of experience into my role at AMAG. I believe that it helps me to define a vision for AMAG that will be unique and on the leading edge of our industry. Q: How would you describe AMAG’s journey over the last several years and how do you see the future? Sullivan: Prior presidents of AMAG always shared their leadership vision and direction with senior leaders located in the United Kingdom. This had an impact on the full direction of the business, sometimes limiting its ultimate success. Before I became a part of AMAG, these senior leaders that were located in the UK retired, placing for the first time the full management responsibilities of the president. This has allowed me to integrate the business into a single team, with single objectives, and a single vision. We expect to begin to reveal this new vision in the coming weeks. We are excited about the future of AMAG and believe we will surprise the industry with our new products and approach in the coming months and years. Q: How important is it that a manufacturer provides both hardware and software solutions? How does AMAG’s approach (in general) differentiate it in the market? We can design the complete solution, providing functionality that others may find more difficult to accomplish Sullivan: Regardless of the manufacturer, we all provide hardware and software. An access control solution is not complete without both. Some of us choose to make our panels, and others do not. Those who are dependent on third-party suppliers are restricted to the developments and direction of that company, and while it might be perceived to be an open technology, it still is proprietary to the hardware manufacturer. AMAG has controlled its manufacturing of panels from day one. The result means that we can design the complete solution, providing functionality that others may find more difficult to accomplish. Q: How does the breadth of AMAG’s product suite provide advantages to customers and/or integrators? Sullivan: AMAG’s product portfolio is unique and provides the end user with an end-to-end identity management solution from one company. Our Control Room PSIM, Symmetry CONNECT Identity Management Solution, Symmetry Access Control, and Symmetry GUEST solutions all integrate to provide the user with a broad set of features and capabilities from a single provider. There is no finger-pointing when we come to support your system. We hold full responsibility for making it work and can quickly provide a resolution to any application difficulties the user may be experiencing. Q: How does AMAG address the divide between on-prem and cloud systems? How do you help customers make the transition and/or plan for the future? We are in the early stages of developing our next generation of access control in which we intend to provide on-prem Sullivan: In our current product portfolio, we have three products that are cloud-based. Our mobile credential platform (Symmetry Mobile), our visitor management solution (Symmetry GUEST), and our physical identity and access management solution (Symmetry CONNECT) are all offerings that operate in the cloud. We are in the early stages of developing our next generation of access control in which we intend to provide on-prem, web client, and cloud-based offerings. One of the primary objectives is to ensure that the large installed base of systems that are out there today will be able to migrate not only to our next generation but as well to the cloud if the client so desires. Q: What is AMAG’s approach to mobile credentialing? Sullivan: As an access control provider, adding Symmetry Mobile credentialing to our portfolio just made sense. We want our customers to have a forward-thinking solution with the opportunity to save money not only on the physical badges but the cost of printing and distributing badges. Mobile credentials can be easily issued and revoked remotely, reducing administrative overhead, and eliminating the need for physical inventory management. Organizations can centrally configure what devices are used and the read range for each type of device and operating system, thus providing flexibility. Symmetry Mobile offers a customized questionnaire that controls access and reduces liabilities. Q: What has surprised you the most in your first year or so leading AMAG? Not many companies are blessed with such a broad portfolio that is supported by a resource-rich company Sullivan: I wouldn’t say I was surprised by this as much as happy to see, but I would say that the quality of our people was a pleasant surprise. As well, the AMAG product offering is broad and has some unique elements. When coupled with the depth of the resources that we have in AMAG, I know that we are second to none. Not many companies are blessed with such a broad portfolio that is supported by a resource-rich company that has so many talented people. Q: Please describe your dealer channel, and how you are seeking to expand it. Sullivan: The AMAG products are sophisticated and typically are installed for higher-end applications. With this sophistication comes a need to be well able to install such a solution. We have a strong group of certified and loyal partners who help us to deliver these enterprise solutions. We desire to provide our existing partners with updated and competitive systems to offer to their end users. Q: What is the security industry’s (and/or AMAG’s) biggest challenge in the next five years? We need to find ways to provide both our channel partners and the customers with solutions that are easily integrated Sullivan: I believe that the advancements that we are seeing in technology provide our industry with the opportunity to truly change how security is provided to our collective customers. As we advance these solutions, we will need to do so responsibly and in a way that helps the channel’s abilities. We need to find ways to train our partners to both install and support these more complex solutions. At the same time, we need to find ways to provide both our channel partners and the customers with solutions that are easily integrated, moving away from proprietary closed systems to open and cohesive solutions. This will ensure that the users get the best, and most complete solutions. Q: What does the industry as a whole misunderstand about AMAG -- time to set the record straight! Sullivan: Well, I am not ready to openly share where we are heading. We are in the process of putting together some advanced approaches to how we will do business with our partners. We are focused on providing tools that will enhance their services to their customers, and with products that are leading edge. I can only state that all should keep their eyes on AMAG, because over the next few years, we are going to surprise some people, and more importantly make our loyal partners quite powerful.
Acre is a company built on mergers and acquisitions (M&A). Since its founding in 2012, Acre acquired several familiar access control companies, from Vanderbilt to RS2 Technologies, Open Options to Feenics, and several others. Acre itself was acquired in 2021 by UK-based private equity firm Triton, thus launching a new chapter in the company's history. Don Joos was named the new CEO in 2022 and set about transforming Acre from a collection of acquired companies into a coherent whole (representing various brands). A year later, we recently caught up with Don Joos to discuss the "new Acre" and what's ahead. Q: How does your background inform your approach to leading Acre Security? In physical security, there is a shift to more of a software-centric versus hardware approach Joos: This is my fourth company as CEO. What I’ve found along the way is that no matter the size or type of business, there’s a common theme, the business is going through some form of evolution or transformation because the industry they're in is going through an evolution. And today, in physical security, there is a shift to more of a software-centric versus hardware approach, and there’s a shift occurring that’s pulling us to the cloud. I think a key thing here is that while the industry is evolving, we must keep a careful eye on the evolution of the customer because the customer is the one who will dictate the pace of change, and I think that is what a lot of people sometimes lose sight of. Q: It seems Acre is on the path from being a “collection of small companies” to “a collection of brands within a single company.” Joos: I think most people think of Acre as a federation of companies. Acre Security was seen more as a holding company. For me, I think the biggest misconception is just that: “This is just a federation of companies” versus “This is a business.” Acre Security is a business that has a range of portfolios to address key verticals and pivotal business problems for customers. Because of what’s happening now and the market dynamics that are occurring, it ties back to “Who is Acre Security?” We have a clear answer as to where we want to be from cloud access control versus on-premise access control. We have clear answers regarding market segments, visitor management, and intrusion. When you think about it, those are the core areas of our business. Q: What has surprised you the most in your first year or so at Acre? Joos: I think the thing that surprised me the most was how similar the problems are because I was coming into a new industry. It’s surprising how strong a correlation [security has] to other industry transformations that I’ve been a part of. Q: What are the points of differentiation among the various Acre Security brands? Joos: I think if you go back to the history of the company, it was designed to compete. That is, that's how it was set up under the logic of, “If we have three bids in a deal, it increases the odds that we're going to win one of them.” As we evolve, to have sustained scalable growth, it is not just about going shallow and casting a wide net. It’s about creating a concentrated focus. Some of the technology is just inherently older technology. And so for me, it’s about creating migration paths for the customers to move to more modern technology, such as the cloud. I love our installed base. When you think about the cost of acquisition to get a new cloud customer, it costs a lot less when you have an installed base that you can migrate to the more modern solution versus having to spend the money and the sales energy to hunt for that next opportunity. Q: Where has Acre positioned itself in the marketplace? We can take care of your current needs, but we also have a clear migration path to take care of your future needs Joos: If you're ready to go to the cloud, we have an answer for you. If you're not ready to go to the cloud, but you're ready to take more cloud-based applications to continue to evolve, we have an answer for you. If you're not quite ready yet and you're still looking for a market-leading premises solution, we have an answer for you, and we have a migration path when you're ready down the road. So, you have a safe bet with Acre because we can take care of your current needs, but we also have a clear migration path to take care of your future needs. Q: How are you building up your team? Joos: In 2023, we’re getting a lot of core building blocks in place and making investments in people who have experience in this space or aligned industries. It is a balance. I think we need a group that understands the industry and a group that's going to come into it and challenge why we do things the way we do. I think that makes us unique: we have fresh eyes looking at things from a different perspective. With that, you’re naturally going to end up with a better answer to problems because people are comfortable challenging the status quo. Q: How are you seeking to expand your dealer channel and/or transition it from the various dealers “inherited” in previous acquisitions? Joos: The channel invests in Acre Security. Our success is their success, and so what we're proposing to them is a range of solutions that supports their longevity and their financial success. But we also continue to build out our portfolio through organic technology innovation or M&A. We're continuing to make investments in our channel strategy and how our partners interact with us We're continuing to expand their addressable market if they want to make investments with us. We're continuing to make investments in our channel strategy and how our partners interact with us. The design of our upcoming technology right now is built with the channel in mind. We want to ensure that we are not creating any channel conflict or any perceived channel conflict. I think that's usually the worst kind: when it's perceived but not real. You need to be very upfront and clear with communications. Q: What is the biggest challenge in the industry right now? Joos: Companies and customers are looking to embed security into their workflows. What I mean is these are not just standalone solutions anymore. They’re integrating with enterprise resource planning (ERP) and human resource (HR) software systems. In property management, they want it integrated into the fitness center, they want it integrated into the cafeteria areas and the dry cleaners, and so forth. So, this is about an ecosystem, and there are times when we are going to be the core, and there is going to be a lot of technology that is adjacent to us. There are times when we are the adjacency to someone else's core in a smart city or a smart building. This gets to why having an open application programming interface (API) is going to be an important part of the technology evolution. It cannot be a closed environment anymore; that is part of the past. Q: What’s next for Acre? We're constantly evolving our cloud access control as well as our on-premise access control Joos: There is a lot of work going on with integrating the business into a single Acre Security company. This is an investment year for us, we are adding people to our team. We are making a lot of investments from a systems and technology perspective. We have a lot of work right now going into integrating the business from an IT infrastructure perspective and all the tools that we use from an employee perspective. We are making a lot of investment as it relates to the commercial side. You're going to see some next-gen technology coming out from an intrusion perspective. We're constantly evolving our cloud access control as well as our on-premise access control. We're also bringing software applications, too. Q: What is Acre’s “message” going forward? Joos: One of the takeaways for me is this is not the Acre of the past. We are making some bold changes. New things are happening here; you better pay attention because clearly, something is different. I think that's one. I think the second is that as they spend time within us, they're going to realize the wide range of solutions and use cases that we can address, whether you're in access control or cloud, whether you're in intrusion, whether you are in visitor management, or whether you're looking at some network connectivity solutions. The third thing that I think people are going to see is a whole lot of energy as they talk to our people and the passion that you see from the team. If I wrap those three points up in one kind of statement there, I think my goal is that people walk away saying “Something is going on at Acre Security. We better pay attention.”
Case studies
Powder bed-based laser melting of metals (PBF-LB/M) is a key technology in additive manufacturing that makes it possible to produce highly complex and high-performance metal components with customized material and functional properties. This technology is used in numerous industries - from aerospace and medical technology to the automotive industry - and is considered groundbreaking for the manufacturing of the future. Advances in process monitoring and control are crucial to further increasing the quality, reproducibility and efficiency of this manufacturing process. Imaging components of the research project A key challenge is the precise analysis of the layer-by-layer laser melting process, as this has a decisive influence on component quality. As part of research into increasing process stability and efficiency, students and scientific staff at the Laser Application Center (LAZ) at Aalen University are conducting global, dynamic observation of the PBF-LB/M process. The imaging components of the research project are two high-performance USB3 industrial cameras from IDS In the context of high-speed process control with temperature feedback, phenomena such as spatter and smoke formation, solidification behavior, and the safe movement of mechanical components during additive manufacturing are investigated. This is supplemented by a high-resolution, static analysis of the remelted component layer geometries and precise detection of potential defects in the powder layers in order to be able to draw well-founded conclusions about the resulting component quality. The imaging components of the research project are two high-performance USB3 industrial cameras from IDS Imaging Development Systems. Two IDS industrial cameras provide the necessary image information The two different tasks require different camera models. "We use a model from the USB3 uEye CP camera family for the global, dynamic observation of the PBF-LB/M process, such as splashes or the formation of smoke." "A USB3 uEye camera from the SE series is used for the static, high-resolution identification of anomalies within the powder layers and in the remelted component layer geometries," explains David Kolb, research associate at the LAZ. Requirements for the camera systems The requirements for the two IDS camera systems are different due to their areas of application in the PBF-LB/M The requirements for the two IDS camera systems are different due to their areas of application in the PBF-LB/M. "Since powder bed-based laser beam melting of metals is a highly dynamic additive manufacturing process in which the component is generated layer by layer, the following features were particularly important for global, dynamic monitoring: The camera must offer a resolution of more than 1000 x 1000 pixels and a frame rate of more than 100 fps, cover an image field of at least 100 mm x 100 mm and have a trigger port for video recordings," says David Kolb, explaining the choice of camera model. The selected U3-3040CP-C-HQ Rev.2.2 enables excellent image quality even in low light or when the camera should take pictures of fast-moving objects. The integrated IMX273 global shutter CMOS sensor from Sony's Pregius range scores particularly well for its image quality, high sensitivity and wide dynamic range. With a resolution of 1.58 megapixels (1456 x 1088 px), it achieves a frame rate of 251 frames per second - ideal for detailed video and image analyses of dynamic processes. Layer-by-layer PBF-LB/M process The video sequence/image shows the layer-by-layer PBF-LB/M process with different laser parameters, recorded with the U3-3040CP-C-HQ Rev.2.2 from IDS using the IDS peak software. "Depending on the setting of the industrial camera, various process properties such as material evaporation or the quantity and direction of splashes during the PBF-LB/M can be observed and quantified," says David Kolb, describing the application. "The knowledge gained from this provides us with important information to understand the laser-material interactions of the additive manufacturing process in greater depth and to be able to customize the manufacturing parameters depending on the material or, for example, the component geometry." New types of soft magnetic components The stator half-shell made of FeSi6.5, based on this, enables ideal adaption to the needs of transverse flux machines To determine the process parameters, cube-shaped components were additively manufactured and the global manufacturing process was analyzed using the USB3 uEye CP camera. This made it possible to identify optimum laser parameters with which new types of soft magnetic components for more efficient electric motors of the future can be produced from the difficult-to-process iron-silicon alloy with 6.5 wt.% silicon (FeSi6.5). The stator half-shell made of FeSi6.5 based on this enables ideal adaptation to the special requirements of transverse flux machines thanks to its optimized, three-dimensional magnetic flux guidance. Use of additive manufacturing technologies The high electrical resistance of the material and the design freedom of the PBF-LB/M allow a reduction in eddy current losses, increased power density and the integration of additional functions such as cooling structures. Both the complex geometry and the brittle, soft magnetic material FeSi6.5 are almost impossible to produce or process using conventional manufacturing processes and require the use of additive manufacturing technologies. BSI technology The sensor must be able to detect geometric features below 40 µm in order to identify defects in the layers For static, high-resolution observation of powder layers or component layer geometries, on the other hand, the following camera properties are required in particular - in addition to a trigger port for single image recording: The sensor must be able to detect geometric features below 40 µm in order to identify defects in the layers and offer an image field of at least 100 mm × 100 mm and an image ratio that is as square as possible (1:1). This is exactly what the 20.36 megapixel (4512 x 4512 px) industrial camera U3-3990SE Rev.1.2 delivers. With the IMX541, it has a high-performance, extremely high-resolution, large-format 1.1" CMOS sensor from Sony's Pregius S series. The BSI technology ("Back Side Illuminated") used enables smaller pixels (2.74 µm) and a higher resolution, as well as improved quantum efficiency and sensitivity. User-friendly and flexibly integrable IDS cameras "Thanks to the particularly user-friendly and flexibly integrable IDS cameras, the necessary adjustments to the test setup could be implemented quickly and easily so that the USB3 uEye SE can be positioned specifically at a defined angle," explains David Kolb. The near-vertical observation of the individual powder component geometry layers will provide valuable insights The near-vertical observation of the individual powder component geometry layers will provide valuable insights into component quality and potential manufacturing defects once the final adjustments have been completed. In this way, crucial information about the properties of additively manufactured components can be obtained and used specifically to optimize the manufacturing processes. Outlook Research in the field of PBF-LB/M is essential for the development and processing of new material alloys and the production of performance-enhancing, sometimes multi-material component geometries. An in-depth understanding of the process helps to minimize defects and realize innovative designs that would not be possible using conventional production methods. The IDS cameras provide in-depth insights into the PBF-LB/M and thus make a valuable contribution to research, development and transfer (R&D&T) - for example, in the processing of new material alloys or the production of complex, application-optimized (multi-material) components. In future, artificial intelligence will be used to automatically analyze the dynamic and static observation of the PBF-LB/M. The aim is to gain an even better understanding of the highly dynamic laser-material interaction - such as the number and trajectory of spatter and the formation of process errors - and to further improve the additive manufacturing process in terms of resource efficiency and sustainability.
i-PRO Co., Ltd. (formerly Panasonic Security), a pioneering manufacturer of edge computing cameras for security and public safety, announced the successful deployment of its advanced, AI-powered camera technology at a major UK aerospace manufacturing facility. The project, delivered in partnership with long-time integrator Richards CCTV, modernized the site’s aging security infrastructure, addressing stringent aviation industry compliance needs while enhancing safety, operational efficiency, and future scalability. Advanced functionality and analytics The customer, a prominent supplier within the global aerospace supply chain, operates in a high-risk environment The customer, a prominent supplier within the global aerospace supply chain, operates in a high-risk environment where precision engineering and rigorous safety standards are essential. Its legacy security system had grown increasingly unreliable, lacking the advanced functionality and analytics required for the complex security landscape. With high-value assets, civil aviation regulations, and extensive health-and-safety oversight requirements at play, the company sought a more intelligent, robust, and resilient security platform. i-PRO’s edge-AI camera technology To meet these demands, Richards CCTV designed and implemented a comprehensive upgrade based on i-PRO’s edge-AI camera technology. The installation included 169 high-performance cameras deployed across production lines, common areas, external perimeters, and critical zones. Key components Advanced camera technology i-PRO’s AI-powered search application that turns camera metadata into actionable intelligence i-PRO’s portfolio includes AI-enabled S-Series cameras that can distinguish people from objects in real time to reduce false alarms, high-speed PTZ cameras that extend perimeter awareness, and fixed domes that deliver clear evidence in shared spaces to help resolve incidents quickly. The cameras are integrated with Active Guard, i-PRO’s AI-powered search application that turns camera metadata into actionable intelligence, enabling operators to run real-time alerts and proactively manage incidents before they escalate. Remote monitoring and analytics enhance operational efficiency Real-time alerts and mobile integration allow managers to receive live notifications and make decisions remotely, reducing the need for constant on-site supervision. Meanwhile, embedded AI analytics enable quality-control teams to detect manufacturing anomalies earlier, increasing production integrity and minimizing downtime. “Our client was happy to lean on our long-standing experience working with i-PRO cameras and the local i-PRO team,” said Phil Luckman, Sales Account Manager at Richards CCTV. “Knowing that i-PRO is willing to properly engage with a customer, come on-site if required, and help demonstrate a proof-of-concept is invaluable.” System reliability and ease of integration Post-deployment, the aerospace plant has seen measurable improvements across several fronts From the outset, system reliability and ease of integration were key. Richards CCTV reported that all 169 devices were “quick to configure and install,” with minimal disruption to day-to-day operations. i-PRO’s durable design, five-year hardware warranties for certified partners, and responsive UK-based support team ensured a smooth, future-proof, deployment and instilled confidence in the long-term viability of the platform. Post-deployment, the aerospace manufacturer has seen measurable improvements across several fronts. The ability to analyze footage from multiple angles has helped refute false personal injury claims, while also identifying root causes of legitimate incidents, leading to meaningful updates in health-and-safety policies. The new system’s high-fidelity audit trails also support quality assurance and compliance documentation, delivering transparency for internal stakeholders and regulators alike. New use cases for i-PRO’s evolving AI capabilities Looking ahead, the installation offers scalability and future-proofing, enabling the end user to adapt the system to continuously evolving needs and industry standards. Planned expansions include securing additional tree-lined zones and increasing coverage in logistics corridors. The facility is also exploring new use cases for i-PRO’s evolving AI capabilities, including automated detection of PPE compliance and unsafe behaviors around heavy machinery. “The cameras provide excellent images in all lighting conditions—every single one performed out of the box,” added Luckman. “With their build quality and long warranties, we know the i-PRO system will deliver long-term value.”
As Micro-LED displays and advanced semiconductor components push the limits of miniaturization and efficiency, precision and scalability in manufacturing become critical. The technology‑pioneering company Micraft Systems Plus has developed two cutting-edge systems that meet these demands: the uLED Laser Soldering Machine and the HBM High-Accuracy Die Bonder. Both rely on industrial cameras from the USB3 uEye CP series from IDS Imaging Development Systems to deliver maximum accuracy, speed, and process control. These systems are already in high-volume use across the Asian electronics market. 20MP USB3 uEye CP cameras Application 1: Micro-LED Transfer & Laser Soldering with 20MP USB3 uEye CP cameras uLED Laser Soldering Machine is designed for high-speed, even of Micro-LEDs onto large-area substrates The uLED Laser Soldering Machine is designed for high-speed, precise of Micro-LEDs onto large-area substrates, including G4.5 and G6 glass panels. Laser soldering minimizes thermal and mechanical stress, which is essential when handling thousands of miniature components simultaneously. Firstly, the cameras are used to capture global reference marks for the preliminary alignment or to determine the rough position of the substrate in the machine coordinate system. This position data is then transmitted to the motion control system, which enables high-precision motion control on this basis - with a repeat accuracy of the coordinates of around ±1 µm. Dynamic rotation correction Once qualified, the chips are aligned and transferred with extreme precision. For fine adjustment, the cameras now capture fiducial marks, enabling real-time sub-micrometer alignment of the substrate and, if necessary, dynamic rotation correction. The alignment results are then transmitted to the motion control system, which adjusts the stage position and angle to ensure each Micro-LED is perfectly matched to the target location. Initial inline visual inspection The camera automatically moves to the relevant area, enabling operators to perform an initial inline visual inspection With a throughput rate of up to 10 million chips per hour, the system delivers both exceptional accuracy and high-volume efficiency, a key performance indicator (KPI) for scalable mass production. After bonding, the camera automatically moves to the relevant area, enabling operators to perform an initial inline visual inspection - such as verifying chip alignment, detecting potential tilt, and checking for physical damage or placement errors. This step is critical in mass transfer operations where yield optimization is essential. Advanced camera tasks in the micro LED process USB3 uEye CP cameras from IDS are the eyes of the uLED Laser Soldering Machine. Throughout the Micro LED workflow, the two integrated U3-3800CP-M-GL Rev.2.2 cameras from IDS support several key process steps: Donor wafer inspection (prior to transfer): Cameras detect defects such as cracks or missing units, ensuring only functional Micro LED chips are selected. Alignment and placement (during mass transfer): Cameras identify alignment marks and fiducials on substrates and dies. The results are transmitted to the motion control system for sub-micron placement accuracy. Post-transfer inspection: The cameras verify that each Micro LED has been precisely positioned and is free of tilt, damage, or misplacement. Rework and repair: When necessary, cameras guide pick-and-place systems to replace individual chips with precision. IMX183 Rolling Shutter CMOS Sensor Camera is therefore ideally suited for complex image analysis in applications such as surface “Exceptionally high-resolution images with low noise levels ensure the capture of even the smallest details,” emphasizes Damien Wang, Area Sales Manager APAC South East at IDS. The light-sensitive IMX183 Rolling Shutter CMOS Sensor from Sony's STARVIS series in the USB3 Vision industrial camera U3-3800CP Rev.2.2.provides outstanding image quality with a resolution of 20.44 MP (5536 x 3692) at 2.4 µm pixels and it delivers up to 19.8 fps. The camera is therefore ideally suited for complex image analysis in applications such as surface and display inspections. 12 MP USB3 uEye CP cameras Application 2: Die Bonding for High Bandwidth Memory (HBM) with 12MP USB3 uEye CP cameras The second system, the HBM High-Accuracy Die Bonder, is designed for advanced semiconductor packaging, especially HBM (High Bandwidth Memory) applications, where vertical stacking of dies requires micron-level precision. Here, two U3-3890CP-M-GL Rev.2.2 cameras from IDS locate the dies and bonding pads, provide precise coordinates to the placement unit, and enable accurate placement of each component. Inline inspection checks Inline checks every bond for placement accuracy, alignment integrity, and possible damage “The IDS camera is also mainly used for the alignment system in our HBM equipment. It identifies the positions of the chip and the target substrate and converts this information into coordinates for the motion control system to achieve precise positioning and alignment,” explains the manufacturer. The control unit uses these coordinates to guide placement with sub-micron accuracy, ensuring consistent results in high-density packaging. Inline inspection checks every bond for placement accuracy, alignment integrity, and possible damage. In high-density memory stacks, even minor misalignments can lead to electrical or thermal issues, making precise vision a must. Sensor performance for precise bonding The U3-3890CP Rev.2.2 is equipped with the rolling shutter CMOS sensor IMX226. The 12.00 MP sensor (4000 x 3000 px, pixel size 1.85 µm) from the Sony STARVIS series excels with exceptional light sensitivity and low noise levels. At full resolution, it delivers a frame rate of 33.2 fps. - perfect for fast, precise processes. Thanks to IDS camera integration, the system achieves repeatable accuracy and long-term process stability - ideal for complex 2.5D or 3D semiconductor packages. Vision technology at the core: IDS uEye CP Cameras To achieve the required speed and precision, both systems count on IDS’s uEye CP camera series To achieve the required speed and precision, both systems count on IDS’s uEye CP camera series. These compact (29 × 29 × 29 mm) cameras are built for industrial environments, featuring durable magnesium housing, Global Shutter CMOS sensors, and USB3 Vision connectivity. Thanks to the STARVIS series BSI ("back-side-illumination") technology, both sensors are ideally suited for tasks that require a perfect result even in low light conditions. Their high-resolution, low-noise imaging allows reliable detection of alignment marks, micro chip positions, solder bumps, and post-bonding joint quality, even at sub-micron scale. Crucially, their fast frame rate and minimal latency ensure seamless interaction with motion-control systems, providing real-time image data for rapid adjustments. These cameras also demonstrate strong thermal reliability, supporting continuous 24/7 operation essential in semiconductor factories. Integration and on-site calibration The standby mode reduces the power consumption in idle mode to a minimum and thus contributes to energy efficiency, making the industrial camera an environmentally friendly solution for long-term use. With the comprehensive software SDK from IDS, integration and on-site calibration become simple, making the uEye CP a foundational enabler for precision and throughput in packaging processes. Customer benefit: Scalable precision and increased efficiency The machine builder significantly enhanced process accuracy, repeatability, and reliability By integrating IDS vision technology into both platforms, the machine builder significantly enhanced process accuracy, repeatability, and reliability. Error rates fell, setup times shortened, and overall manufacturing efficiency improved - driving strong competitive advantage in both Micro‑LED displays and advanced semiconductor packaging. Both systems are already in use with pioneering manufacturers in Taiwan and Asia, showcasing how German-engineered vision technology seamlessly integrates with state-of-the-art automation to meet modern production demands. Outlook The market for semiconductor manufacturing – particularly in precision automation – is developing rapidly, and with it, the requirements for modern industrial cameras are also evolving. “Our customers are demanding high-resolution, compact, and absolutely reliable solutions more than ever before,” says Damien Wang. The trend toward higher resolution is a key driver of innovation: sharp, detailed images are essential for complex automation tasks. At the same time, stable performance under challenging operating conditions has become a fundamental requirement. “Many applications require continuous, uninterrupted operation. That’s why our focus is increasingly on cameras that perform reliably even in demanding environments,” emphasizes the responsible project manager from Micraft Systems Plus. Another trend is ongoing miniaturization. Industrial cameras with compact form factors are gaining importance, as space in modern systems is often limited – without any compromise in performance. To address these developments, the product portfolio is being strategically expanded and adapted to meet the growing technical demands.
In the fast-evolving landscape of intelligent manufacturing, Dahua Technology is shaping a new benchmark with its advanced innovation capabilities and efficient production models, creating a fully digitalized and automated smart manufacturing system. Dahua AIoT Industrial Park From being recognized with China’s “National Worker Pioneer” award last year to being named one of the country’s first “Excellence-level Smart Factories” this year, the Dahua AIoT Industrial Park has made great strides in transforming its production. The factory features key innovations, such as automated assembly, unmanned testing, visualized supervision, and autonomous logistics. It fully integrates people, machines, materials, methods, and environment to deliver an exceptional user experience to customers worldwide. A model of human-machine collaboration Dahua has created a highly adaptive and collaborative smart manufacturing model By combining intelligent material management, automated assembly and testing, flexible production lines, an AIoT digital system, and digital twin technology, Dahua has created a highly adaptive and collaborative smart manufacturing model. The factory’s flexible production lines are designed for agility — capable of seamlessly switching between tasks at the push of a button, handling precision electronic components and complex structural parts alike. This flexibility is made possible by the deep integration of advanced automation and intelligent equipment in key production processes: Automated Screw Fastening: Equipped with visual positioning and real-time inspection modules for precise fastening and risk prevention. Airtightness Testing: AI-powered testing in collaboration with robotic arms for fully automated operation. Precision Dispensing: Visually guided dispensing combined with real-time quality inspection. Real-time digital twin operations The factory operates 24/7, continuously capturing data from all equipment and production processes With digital twin technology, the factory operates 24/7, continuously capturing data from all equipment and production processes. It creates accurate 1:1 digital models of production lines, robots, and machinery, using real-time data to simulate production flows, monitor line status, and predict potential issues. Even during non-operating hours, smart inspections for environment, perimeter, and fire safety run automatically, with instant alerts for any anomalies. Through the operations center, managers can access live data and make informed decisions to drive efficiency and reduce costs. Unmanned Testing & Quality Management Dahua enhances product quality through granular market insights, modular R&D design, and intelligent testing systems. Leveraging PLM (Product Lifecycle Management), testing parameters are auto-calibrated, while a big-data-driven “Smart Test Brain” continuously fine-tunes test strategies in real time. Dahua enhances product quality via granular market insights and design. Testing processes for mature products are streamlined, while defect predictions automatically trigger stricter testing standards, ensuring fast, high-quality output. For end-to-end quality control, every product is tracked using a unique QR code, enabling instant traceability across its entire lifecycle. This system builds a comprehensive quality data pool that supports production optimization and quality strategy adjustments. Autonomous Logistics for High-Efficiency Operations Dahua's smart warehouse combines vertical storage systems with a network of AGVs Dahua’s smart warehouse combines vertical storage systems with a network of AGVs, intelligent conveyor lines, robotic arms, vision systems, and automated labeling equipment, all managed via a digital platform to enable fully unmanned “lights-out” factory operations. During the inbound processes, products are automatically scanned, measured, packaged, and assigned by the Warehouse Control System (WCS), with robotic arms and AGVs handling storage placement. Outbound processes are fully automated as well — whether for full pallets, single-SKU shipments, or mixed-SKU orders — and completed within 10 minutes through coordinated efforts of AGVs, robotic arms, and conveyor lines. Looking Ahead From “Pioneer” to “Excellence,” the Dahua AIoT Industrial Park is achieving new levels of production efficiency, product quality, and operational synergy through the deep integration of IT and OT technologies. Moving forward, Dahua will continue driving innovation and contributing to new-generation productivity, helping industries worldwide benefit from intelligent manufacturing and creating a smarter future for all.
The global energy landscape is evolving at an unprecedented pace. With the increased adoption of renewable energy sources and the drive for a more sustainable future, the demand for efficient energy storage has never been greater. Enter Battery Energy Storage Systems (BESS)—the backbone of modern energy infrastructure, ensuring stability, resilience, and efficiency in power distribution. Record-breaking growth in storage In 2024, the US battery storage market saw record-breaking growth, with nearly 9.2 gigawatts (GW) of new capacity installed in late November alone, according to figures from S&P Global. But how is this supercharged leap into more stable power distribution fairing on a fundamental level? Despite an estimated capacity increase in the United States of a staggering 89% in 2024, according to U.S. Energy Information Administration (EIA), there is still more to be done to ensure this rapid rollout of these mainly Lithium-ion battery systems don’t pose a threat to workers, communities and the energy infrastructure. US battery storage market saw record-breaking growth, with nearly 9.2 GW of new capacity The global importance of battery energy storage systems BESS helps to bridge the gap by storing excess energy when supply is high BESS plays a critical role in balancing power supply and demand, especially as more countries transition to renewable energy sources like solar and wind. Typically, renewable energy sources are inherently intermittent—meaning they don’t produce electricity consistently throughout the day, due to a variety of uncontrollable environmental factors. BESS helps to bridge the gap by storing excess energy when supply is high and distributing it when demand peaks. While the idea of shoring up the energy infrastructure to greater withstand periods of intense strain is a laudable (and indeed, logical) one, they must ensure that in the haste to erect new BESS sites, they don’t overlook vital safety concerns. How BESS underpins growing support for the electrification In addition to grid stabilization, BESS is instrumental in enhancing energy reliability. By storing surplus electricity, BESS ensures that power remains available even during blackouts or grid failures. It’s also an important element of reducing carbon emissions, as with stored renewable energy, reliance on fossil fuel-powered plants decreases, leading to a more sustainable energy mix. Let’s not forget how BESS underpins growing support for the electrification of transportation. As electric vehicles (EVs) gain traction, BESS can facilitate fast-charging infrastructure without overloading the grid. Prominence of BESS installations can mean greater risks Renewable energy producers added 10.5 GWh power to the energy network, according to market intelligence In February 2025 alone, renewable energy producers added 10.5 GWh capacity to the global energy network, according to market intelligence firm Rho Motion’s Battery Energy Stationary Storage Monthly Database. But while BESS sites are a useful way to prevent overloading the world’s power supplies—releasing stored energy at peak times when power generators come under greater strain—they come with challenges. One of the greatest concerns is thermal runaway, a dangerous chain reaction in which rising temperatures spread from one battery cell to another. Why advanced thermal imaging solutions are essential Without proper monitoring and early detection of potential failures, thermal runaway incidents can easily snowball into devastating fires. These fires spread rapidly, passing from unit to unit, causing sizable financial losses, environmental damage, and, of course, safety hazards—including releasing toxic substances such as hydrogen fluoride gas. Advanced thermal imaging solutions are becoming essential to keep BESS sites safe That’s why advanced thermal imaging solutions are becoming essential to keep BESS sites safe and operational. Fixed thermal cameras with advanced analytics are the go-to solution, as they can trigger alarms and suppression systems when temperatures pass a set threshold.
Modern measurement technologies enable high-precision detection of the movement of liquids and gases - and thus provide valuable data for numerous applications. How does the air flow around an airplane? How does the blood move through our veins? And how can pollutant emissions in combustion processes be minimised? For this purpose, speed, direction, pressure, and turbulence within a flow are analyzed in order to increase efficiency, ensure safety, and drive innovation in a wide variety of areas. Innovative sensor technology High-resolution cameras are used to track marked particles within a flow and analyze their movement A range of methods are available to measure these flows, including visual ones such as particle image velocimetry (PIV). High-resolution cameras are used to track marked particles within a flow and analyze their movement. iLA_5150 GmbH from Aachen (Germany) now also relies on EBIV. The abbreviation stands for Event-Based Particle Image Velocimetry and is a new optical method for the qualitative and quantitative visualization of flows and flow velocities. It combines PIV with event-based cameras, here with a uEye EVS from IDS Imaging Development Systems GmbH. The innovative sensor technology of the industrial camera enables highly dynamic and energy-efficient detection, especially of fast and turbulent movements. Application In the EBIV method, tiny particles are added to a flowing fluid and illuminated in a plane, the so-called light section plane. They generate individual light pulses as they enter and exit the LED light section. This change in local brightness is recorded independently by the camera pixels and transmitted to the PC as a data stream of "change events". In contrast to conventional cameras, event-based models therefore only react to the changes in brightness registered in the image field. Stationary scattered light, such as background or a non-changing illuminated surface, does not generate a measurement signal. This reduces the amount of data considerably. Frame rates of up to 10,000 frames per second The data stream essentially contains information about what happens, when and where The data stream essentially contains information about what happens, when and where. In detail, these are the pixel coordinates on the sensor, microsecond time stamps of the pixel events and the information about the events: ON or OFF. This allows a distinction to be made between increasing intensity (ON event) and decreasing intensity (OFF event). Using suitable software, the stream can be converted into an image matrix in which both the spatial information and the linear time base of the stream are available. The result is comparable to the extremely high frame rate of a high-speed camera. EBIV measurement method "The EBIV measurement method differs fundamentally from conventional imaging methods. They usually generate very large amounts of data and require powerful peripherals that can process them. For exceptional frame rates of 1000 Hertz and more, the image-based cameras required are themselves very complex and expensive." "With the help of event-based camera technology, comparable frame rates of 10,000 frames per second are possible, whereby only standard PC interfaces such as USB with a few gigabits per second are required. The price of the event-based models themselves is significantly lower than that of corresponding high-speed cameras and is therefore also very interesting for smaller teaching and research institutions," explains Dr André Brunn - Head of Development at iLA_5150 GmbH. Further processing The user can optimize the display of the move paths and adapt them to unique study objectives The data stream is converted into image data and displayed in a front end - the so-called EBIV viewer - for direct online flow visualization. The user can also select the integration time, which corresponds to the exposure time of an image camera, as well as the time increments of the sequence, i.e., the period between two consecutive shots. Classic image filters can also be used. With the help of these settings, the user can optimize the display of the movement paths and adapt them to individual examination objectives. Both fine flow details and large-scale patterns can be made more clearly recognizable. This ability to readjust the measurement results is another advantage of the event-based approach. Numerical analysis of the flow properties In the qualitative visualization of the flow in the EBIV-View, particles are continuously illuminated so that they are visible as luminous traces. The method is therefore very well suited to visualizing the flow. However, it does not provide exact measurements of its speed or direction. For a precise, numerical analysis of the flow properties, individual particles are illuminated for a moment using short, time-defined light pulses. Image sequences of the event-based camera As with classic PIV, the image sequences of the event-based camera can also be statistically analyzed This allows their exact position to be recorded and their movement quantified. By comparing the particle positions in successive images, the speed and direction of the flow can be precisely calculated using PIV, for example. The result is a transient 2D vector field that changes over time - in other words, the vectors do not remain constant. As with classic PIV, the image sequences of the event-based camera can also be statistically analyzed, for example, to determine mean values and fluctuations in the flow velocity. Camera and software On the camera side, iLA relies on a uEye XCP-E from IDS. The small, lightweight industrial camera offers event-based sensor technology in a robust die-cast zinc housing (29 × 29 × 17 mm) with screw-on USB Micro-B connection. It is compatible with all standard C-mount lens sizes. This makes it ideal for both industrial and non-industrial areas. The integrated event-based vision sensor (EVS) was developed by Sony and Prophesee. It is supported by the Metavision SDK, a seamlessly integrated suite of software tools and models, APIs, and other training and development resources from Prophesee for efficient analysis, visualization, and customization. Building on this, the EBIV viewer from iLA_5150/PIVTec is specially tailored to flow visualization applications. Outlook The optimization of fluidic systems and processes requires detailed knowledge of the flow conditions The optimization of fluidic systems and processes requires detailed knowledge of the flow conditions. A qualitative flow visualization is often sufficient to understand effects and develop suitable control mechanisms. Until now, however, imaging fast flows with high temporal resolution was usually only possible with expensive high-speed cameras. Event-based camera technology offers a cost-effective alternative that requires significantly less technical effort. These “simple” methods have been lacking in teaching and research in particular. Thanks to the extreme data reduction, this technology also allows the use of several cameras or large camera arrays without the periphery becoming a limitation for data transfer. The compact design of the uEye EVS models also makes them ideal for mobile applications. This means that real application environments can be analyzed directly for the first time - without having to rely on artificial flow models or channels. Established flow measurement methods Event-based cameras enable efficient, cost-effective and high-resolution visualization and quantification of flows. Due to the small amounts of data generated, many processes can be analyzed almost in real time, which also makes them interesting for use in fully automated systems. Established flow measurement methods such as Particle Image Velocimetry (PIV) can be seamlessly integrated and expanded. The technology can be used wherever flow information is captured by changes in scattered light intensity - be it from moving particles or vibrating surfaces.


Round table discussion
Future-proofing your skillset is about embracing continuous learning and developing a versatile set of competencies that remain valuable regardless of technological shifts or industry changes. In the security marketplace, it is not about predicting the exact jobs of the future, but rather equipping yourself to adapt and thrive in the uncertain security landscape. But where to begin? The emerging technology shifts in the security industry provide clues, such as the growing importance of cybersecurity and artificial intelligence (AI). We asked our Expert Panel Roundtable: How can physical security professionals “future-proof” their skillsets to prepare for emerging technologies?
Retaining top talent is a route to bring innovative ideas and creative solutions to a company. Talent drives product development, improves processes, and helps businesses stay ahead of the competition. In essence, retaining top talent is essential for businesses to remain competitive, innovative, and successful. Unfortunately, staffing shortages are a reality for many corporate players in the security industry, as well as throughout the business community. We asked this week's Expert Panelists: How can physical security organizations attract and retain top talent?
There is safety in numbers, or so the expression goes. Generally speaking, several employees working together tend to be safer than a single employee working alone. Even so, some environments require that workers complete their jobs alone, thus presenting a unique combination of security vulnerabilities. The U.S. Occupational Safety and Health Administration (OSHA) defines a lone worker as “an employee working alone, such as in a confined space or isolated location.” We asked this week’s Expert Panel Roundtable: How can security technologies help to protect "lone workers?"
Products