Hotel security
The German Design Council has been shaping the design landscape in Germany since 1953. Every year, the organization presents the ICONIC AWARD to recognize visionary architecture and innovative solutions. At the 2025 awards ceremony, dormakaba's Quantum Pixel+ electronic hotel lock was honored with the ICONIC AWARD. Digital product solution The digital product solution increases convenience for hotel guests. Modern technologies, such as NFC, RFID, Bluetooth® Low Energy, and digital wallets...
At GSX 2025 –Ernest N. Morial Convention Center, New Orleans, September 29 to October 1, booth #3619 - Vismo will demonstrate its new “Checkpoints”, which uses QR codes at key points in a building or venue to create timestamped logs of presence. Not requiring a GPS location, Checkpoints’ QR code readings are automatically recorded in Vismo’s secure portal immediately the codes are scanned by phone. Vismo Protect App’s panic button “Checkpoints e...
Vismo has announced “Vismo Checkpoints”, a proof of presence tool that takes employee well-being a step further by using QR codes to let organizations know precisely where staff are in a building or event space. Designed for high location accuracy and ease of use, Checkpoints is used with the Vismo Locate & Protect App on smartphones, from where it integrates with Vismo’s secure portal and the employer organization’s security protocols. QR codes with a phone The ap...
Regula, a global developer of forensic devices and identity verification solutions, introduces a new embedded document reader—the Regula 7223E—designed to streamline ID card checks at self-service kiosks and e-gates. Built specifically for ID-1 format documents, such as driver’s licenses and national ID cards, the compact scanner helps borders and businesses speed up identity checks, reduce user errors, and deliver a better customer experience at scale. Self-service solutions...
dormakaba has opened its first Innovation Lab at its German headquarters in Ennepetal. The new innovation center provides a creative environment for employees, where new ideas are brought to life through real-world application scenarios, practical tests, and interdisciplinary collaboration. It is part of a strategic investment in innovation and the long-term development of the site. Concrete products and innovations "With the Innovation Lab, we are creating a lively, creative space where mark...
iDenfy, a US-based fraud prevention and identity verification company best known for its AI-powered RegTech automation solutions, partners with Reppublika Data Analytics & Technologies, a pioneer European software firm providing innovative SaaS solutions to the market research industry. iDenfy’s identity verification software will help the business verify all customers who are conducting surveys online while detecting fraudulent users with fake personal details or other renderings, of...
News
Not far from Kurfürstendamm, Berlin's number 1 shopping boulevard, a handful of people are working high up on the 13th floor to conquer the global market for smart door intercom systems with a compact and ultra-modern and above all high-quality and affordable product: DoorBird. The goal was to make it possible for residents all over the world to speak to their visitors at the door and even open the door for them, no matter where they may be at that moment. HD camera In autumn, 2014 the time had come: The very first models had an HD camera with a 180° ultra-wide angle and night vision mode, a motion sensor, Wi-Fi, and various connections. The comprehensive range of equipment was a decisive competitive advantage, and this was also immediately recognized: On December 23, 2014, a customer from Orlando, Florida, placed the very first DoorBird order on the company website. The first sale in Germany followed just two days later to a customer near Cologne. Smart door communication is taken to the next level Accessories such as the BirdGuard additional camera or an alarm siren were also taken into account But the first DoorBirds were far from the end of the story. While the so-called D10x series was still maturing into its final version in the company’s early days, another product range was already in the works. This range satisfied the high demand for models made of high-quality material (stainless steel) for flush or surface mounting, with the same technical functionality. Accessories such as the BirdGuard additional camera or an alarm siren were also taken into account. Door intercom market The small company then became an integral part of the door intercom market. Over the next few years, new or expanded door intercom models, indoor stations, upgrades, and access control systems as well as accessory products were consistently introduced. By 2024, just ten years after the company’s foundation, the total number of products would be 2,300 if you were to factor in the different color options available. Almost every one of these many products has been met with widespread approval from customers in 161 countries. And that’s no shock because from day one Door Bird has always precisely tailored its innovations to meet the needs of customers. Go West meets made in Germany Whether it was more products or more employees, The DoorBird family around the founders Bernd Müller and Sascha Keller continued to grow to create the best possible product experience. From the very first minute, DoorBird was based in Berlin. DoorBird still designs, tests, and manufactures in the German capital to this day. And for good reason. Degree of compatibility This in-house approach ensures the highest level of quality and reliability, and a high degree of compatibility “Made in Germany” is a promise that DoorBird makes to its customers: All products are developed internally, all design phases undergo strict controls, and each finished product is extensively tested in specially developed test environments. This in-house approach ensures the highest level of quality and reliability, and the high degree of compatibility of the DoorBirds further enhances user-friendliness. Well-documented interface Due to a well-documented interface (API), the products can be easily integrated into smart environments and can thus interact with a wide variety of garage doors or smart door locks, for example. This means the customer can combine smart home applications from different manufacturers according to their taste and do not have to commit to a single brand. In 2024, the DoorBird Connect network has over 80 integration partners. Home automation and security Although the know-how and production were located in Berlin, right from the outset the two founders saw the USA as one of the most important markets. The decision to present the DoorBird directly at a US trade fair was part of this thinking. The concepts of home automation and security were prevalent there much earlier than in Europe; the successful trade fair appearance in January 2015 confirmed the founders in their strategic direction and actions. Locations for IT and high-tech In 2021, the second location was opened in Jacksonville, Florida, to be even closer to partners and customers In the summer of 2015, the company moved into its first premises on American soil, in San Francisco, with its proximity to Silicon Valley, one of the most important locations for the IT and high-tech industry worldwide, San Francisco was the ideal starting point for conquering the US market. By quickly specializing in the upscale residential segment and the B2B business with electricians, DoorBird chose a path that turned out to be extremely successful. In 2021, the second location was opened in Jacksonville, Florida, to be even closer to partners and customers on the American East Coast. Part of a big family With their consistent product and sales strategy, the two founders set the course for success right from the start. DoorBird has grown continuously for many years through its efforts. In 2022, they took the opportunity to think even bigger with a strong partner at their side and secure a leading, globally relevant position for DoorBird in the market for IP door intercom systems in the long term. Large-scale projects such as hotels, commercial facilities, and entire residential complexes in particular are becoming increasingly important and offer enormous potential for DoorBird's future. Part of the ASSA ABLOY Group Since 2022, Bird Home Automation GmbH has therefore been part of the ASSA ABLOY Group. ASSA ABLOY is the world's pioneering manufacturer and supplier of locking and security systems for everything to do with doors. Following the acquisition of DoorBird, ASSA ABLOY has products that can be used worldwide in the area of door communication. After all, there will be other innovative products in the future, of course always geared towards the needs of the customers. Meeting these needs with top-quality products, no matter what the application and no matter where in the world, is what the company wants to do, always made with love in Berlin. Made in Germany.
Matrix SARVAM UCS is an enterprise-grade (SME and ENT) Unified Communication solution that offers collaboration, communication, messaging, and mobility. It brings diverse users from multiple locations to a common platform for real-time collaboration and communication. Customer responsiveness It unifies all the communication networks and devices to provide users the flexibility of accessing the calls, messaging, and voicemails from any of the devices irrespective of their location. This thus improves an organization's agility and productivity. These attributes make it a must-have solution for businesses, hotels, hospitals, manufacturing units, retail chains, and banks. By leveraging the power of unified communications, different categories of enterprises can boost collaboration and improve customer responsiveness. Key features: Unified communication server for 10 to 2000 users. Connect analog, digital, VoIP, and smartphones on a common platform. Offers scalable solutions for organizations of different sizes. Manage and monitor network elements, audit network usage, and detect network faults with the support of SNMPv1/v2c/v3. Attend up to 64 calls simultaneously.
Matrix SARVAM UCS is an enterprise-grade (SME and ENT) unified communication solution that offers collaboration, communication, messaging, and mobility. It brings diverse users from multiple locations to a common platform for real-time collaboration and communication. Improving agility and productivity It unifies all the communication networks and devices to provide users the flexibility of accessing the calls, messaging, and voicemails from any of the devices irrespective of their location. This thus improves an organization's agility and productivity. These attributes make it a must-have solution for businesses, hotels, hospitals, manufacturing units, retail chains, and banks. By leveraging the power of unified communications, different categories of enterprises can boost collaboration and improve customer responsiveness. Key features Unified communication server for 10 to 2000 users. Connect analog, digital, VoIP, and smartphones on a common platform. Offers scalable solutions for organizations of different sizes. Manage and monitor network elements, audit network usage, and detect network faults with the support of SNMPv1/v2c/v3. Attend up to 64 calls simultaneously.
3DX-Ray who will be exhibiting once again at the important Milipol Exhibition 2023 in Paris, has announced the successful sale of four AS1 Portable X-Ray Systems and four more AXIS-A33 walk-through metal detectors. AS1 Portable X-Ray Systems The AS1 Portable X-Ray Systems are a repeat sale of four systems to an established EOD Unit customer in SE Asia. These systems represent an upgrade in capability from their existing LS1 and LS3 systems which they have used successfully for years. These new systems give them higher image resolution and sophisticated image processing software from the very latest product in the 3DX-Ray product line. 3DX-RAY ThreatScan®-AS1 The 3DX-RAY ThreatScan®-AS1(ISC) is a robust amorphous silicon portable X-ray inspection system The 3DX-RAY ThreatScan®-AS1(ISC) is a robust amorphous silicon portable X-ray inspection system. It comprises, as standard, a detector panel with an imaging area of 43 x 35cm, a new high penetration 150kV generator, and a laptop along with batteries, chargers, the user-friendly 3DX-RAY ThreatSpect software, wireless communication, and transport case. AXIS-A33 The sales of AXIS-A33 walk-through metal detectors are to two different customers based in the north of England. The first two systems have been delivered to an educational establishment and the other two systems to a distributor of high-tech electronic components. Applications in different sectors 3DX-RAY LTD, CEO, Vincent Deery said, “Once again these systems have proved their utility, with these customers using the systems for very different purposes." "In education, these systems are essential tools in keeping our young people safe, and in the commercial sector they are ideal for preventing and deterring petty theft.” Digital walk-through metal detector The coil design and LEDs show the horizontal position of metal objects, allowing the operator to analyze quickly The AXIS-A33 is a highly sensitive digital walk-through metal detector with 33 independent detection zones and outstanding electromagnetic and digital processing technology. The coil design and high-brightness LEDs show the horizontal position of metal objects, allowing the operator to analyze quickly and accurately. These systems are ideal for use in multiple applications including public and commercial building lobbies, airports, prisons, hotels, factories, banks, event venues, and of course educational establishments. Demonstration at Milipol Paris 2023 Come and meet the 3DX-Ray team at Milipol Paris 2023 from the 14 to 17 November 2023, Stands No.4 E075 On show will be the ThreatScan®-AS1(ISC), ThreatScan®-LS1, and the ThreatScan®-LS3 Portable X-Ray Systems, currently in service with EOD units worldwide. In addition, their AXIS™-CXi, the only cabinet-based x-ray system for screening mail that has a materials discrimination function, suitable for parcels and small baggage, will also be on show.
From 10 to 13 October, the global airport community will gather for the 24th edition of inter airport Europe at the Munich Trade Fair Centre in Germany. The event returns with an impressive line-up of well over 400 airport suppliers from 37 countries, including seven national pavilions and more than 100 new exhibitors. Live exhibits Visitors can look forward to plenty of live exhibits in the halls and Outdoor Area and a new 600 square meter GSE Experience Area. An exciting event program including Technical Seminars, Innovation Awards, and the co-located inter airport FOCUS, The Sustainability Summit provides interesting opportunities to further engage with new technologies and suppliers, all dedicated to improving airport performance while delivering a return on investment. New economic importance inter airport Europe has developed into the most senior gathering of global airport operators, airlines, CAAs, service suppliers The Munich Trade Fair Centre will once again turn into the world’s biggest hub for exploring and sourcing new technology, equipment, and services for better airports. Over nearly 50 years, inter airport Europe has developed into the most senior gathering of global airport operators, airlines, CAAs, service suppliers, investors, and other experts in this sector. The upcoming event marks another milestone for the airport industry which is currently rising to new economic importance with a multitude of opportunities and challenges. Airport professionals Airport professionals from more than 100 countries have already registered as visitors, including key representatives from AENA, Air France, Deutsche Lufthansa, Fraport AG, Heathrow Airport, İGA Istanbul Airport, Oman Airports, Shell Aviation, WISAG, and many more. Over four exhibition days, they can explore an excellent cross-section of technologies and services for the entire airport supply chain, including airside operations, terminal management, passenger services, baggage handling, safety and security, airport IT, air traffic control, airport maintenance, and environmental management. Insights into technology innovations Networking and knowledge platform on how to develop, embed, and integrate sustainability strategies An impressive program of accompanying events offers additional insights into technology innovations about wider market trends. These include Technical Seminars, Innovation Insight Sessions, the prestigious Innovation Awards, and the co-located inter airport FOCUS Sustainability Summit, a two-day, high-profile networking and knowledge platform on how to develop, embed, and integrate sustainability strategies into every aspect of airport life. Roadmap to airport operations “Co-locating exhibition and summit is an exciting opportunity for us to provide more value to the global airport community. Both events naturally complement each other, providing attendees with a great roadmap to future-proof their airport operations,” says Olaf Freier, Portfolio Director Transport of inter airport Europe, on behalf of show organizer RX. “The co-location offers new and encouraging perspectives that will help pave the way for innovation, resilience, and sustainability at future airports.” inter airport Europe at a glance: Indoor and outdoor stands with live equipment Over 30% of exhibitors are newcomers on the inter airport show floor, forming an impressive line-up A large show floor in halls B5, and B6, and the adjacent outdoor area invite visitors to discover more than 400 suppliers who deliver advanced airport equipment, technology, and services across the globe. The top five exhibitor countries are Germany, Italy, the United Kingdom, France, and the Netherlands, with 37 countries represented in total. Over 30% of exhibitors are newcomers on the inter airport show floor, forming an impressive line-up of well-known international brands alongside promising startups and scaleups. A new 600 square meter GSE Experience Area, sponsored by Weihai Guangtai Airport Equipment, will offer visitors the opportunity to see the latest equipment for aprons and runways live and in action. National Pavilions and First-time Exhibitors Several National Pavilions will feature this year – Italy, France, the UK, the Netherlands, Finland, and newcomer Spain, all showcasing some of their countries’ finest tech companies and products. Long-term show partner GATE (The Airport Technology Network) will be hosting a number of its members at their dedicated GATE Pavilion again. In addition, there will be two First-time Exhibitor pavilions specifically dedicated to companies new to inter airport Europe. Opening and Innovations Awards Ceremony The spotlight on best practices, technologies, and partnerships that drive innovation and excellence The inter airport Europe Innovation Awards celebrate the achievements of the many inventors and technical pioneers within the exhibitor community, putting the spotlight on best practices, technologies, and partnerships that drive innovation and excellence for better airports. The winners will be announced at the Opening and Innovation Awards Ceremony on Tuesday, 10th October, 11:00 - 12:00, at the Seminar Theatre in Hall B5. Welcoming presentations include speeches from Nicola Hamann, Managing Director at RX, Kay Bärenfänger, President at GATE Alliance, and Jost Lammers, CEO at Munich Airport. Seminar Programme: Three days of expert talks The free-to-attend inter airport Europe Seminar features a selection of technical talks on pioneering solutions and approaches to pressing airport issues, including the Innovation Insight Sessions featuring participants of the Innovation Awards. The 15-to-30-minute sessions will touch on key aspects of the passenger experience and passenger journey, baggage handling, security systems, as well as ramp and terminal management. The technical seminars will run between 10 - 12 October at the Seminar Theatre in Hall B5, stand B5-1580. Visit the show website for the full seminar agenda. inter airport FOCUS – The Sustainability Summit The Sustainability Summit offers two days of top-tier education, networking, and collaboration opportunities The co-located inter airport FOCUS – The Sustainability Summit offers two days of top-tier education, networking, and collaboration opportunities for aviation stakeholders looking to develop, discuss, or initiate sustainability measures required to reach their net zero commitments, including sustainable airport operations, net-zero infrastructure, and new mobility concepts. inter airport FOCUS takes place on 11 and 12 October at the Press Centre East Entrance (Rooms 1A, 1B, 2). The Summit tickets can be purchased online or on-site and also include free entry to the inter airport Europe exhibition and seminars. For the full summit program, please visit inter airport FOCUS. Visitor tools, Matchmaking Visitors are invited to use the Exhibitor List Tool and Online Show Preview to search for products and companies that are of particular interest to them. Once registered, visitors have access to the inter airport Europe Matchmaking Platform, allowing them to send or receive meeting invitations based on their business requirements. Meetings can be arranged at the exhibitor’s stand or in the dedicated meeting lounge in Hall B6, stand B6-590. Hosted Buyer Programme The Hosted Buyer Programme offers a tailored networking experience with industry pioneers The Hosted Buyer Programme offers a tailored networking experience with industry pioneers from airfield construction, ground handling, ground support equipment, interior design, hardware and software solutions, terminal infrastructure, and operations in the 2023 group. It focuses on growing markets and emerging regions, with buyers from UAE, India, Kenya, South Africa, Saudi Arabia, and Ghana, and it is an excellent opportunity to open up new markets for exhibitors. Venue, tickets, and opening times inter airport Europe 2023, the 24th International Exhibition for Airport Equipment, Technology, Design, and Services, takes place in halls B5, B6, and the adjacent outdoor area at the Munich Trade Fair Centre in Germany. Access to the exhibition halls is via Entrance East. Please visit the Online Travel Hub for further information on transport, accommodation, and visa. Show opening hours are from 9:00 AM to 5:00 PM on Tuesday, Wednesday, and Thursday (10 to 12 October), and from 9:00 AM to 3:00 PM on Friday (13 October). Visitors can register via the Online Ticket Shop and benefit from a reduced price when purchasing their ticket in advance. Day tickets cost €42 online or €52 on-site; season tickets cost €62 online or €72 on-site.
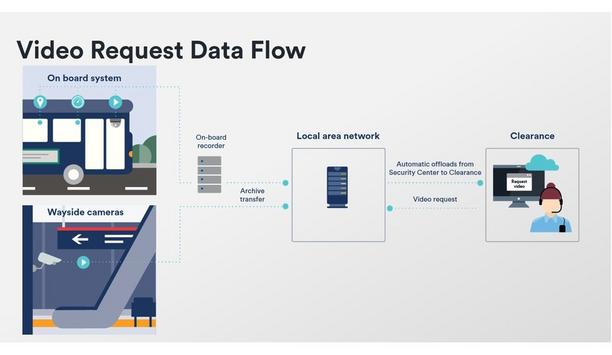
Genetec Inc., a pioneering technology provider of unified security, public safety, operations, and business intelligence solutions, announced that its Genetec Clearance™ digital evidence management system now enables the remote retrieval of video recordings from physical security systems across transit agency sites and fleets to help speed up investigations. The capability is enabled by the integration of Clearance with the Genetec Security Center Fleet Monitoring™ module. Using a browser-based system, agencies can now link all their on-board and landside data into a unified solution to manage evidence and streamline the sharing of recordings with internal departments and external partners. Genetec Clearance These requests are still often delivered on physical media, adding to the cost and delay of the process Transit security teams devote considerable time and resources to assist with requests from their legal and claims departments, law enforcement agencies, and parties that require access to video recordings captured by their camera systems. These requests are still often delivered on physical media, adding to the cost and delay of the process. Genetec Clearance eliminates the time-consuming, costly process of dispatching transit personnel to vehicles and stations, transferring video to external drives, and delivering it to requesting parties. All requests are centrally and securely tracked within Clearance and go through the agency’s approval process to ensure they are aligned with governance policies before the video is shared. On-board systems Internal departments and external parties order recordings from station cameras From a web browser, internal departments and external parties can now request recordings from station cameras and on-board systems, and review video from the same application. Exports from on-board systems include vehicle telematic data, which can be reviewed alongside video uploads. This data, such as vehicle speed, brake, and turn signal activation, can be shared with attorneys and other authorized parties, helping to assess a scene and provide further analysis of events. “Transit security teams have the complex duty of managing highly distributed operations to ensure the safety of commuters and transit employees day in and day out,” said Erick Ceresato Product Group Director, Genetec Inc. Genetec Clearance integration Erick Ceresato added, “By automating the steps involved to fulfill video requests, and reducing the time it takes to deliver video evidence to reviewers, Genetec solutions free up security teams to focus on mission-critical activities. Having a unified security environment across stations and vehicle fleets opens the door to this kind of efficiency and removes bottlenecks that have traditionally impeded access to this data.” The Genetec Clearance integration with the Fleet Monitoring module will be available in October 2023 and is being showcased at the APTA Expo at the Genetec booth #3510.


Expert commentary
The average business owner or investor has some kind of security precaution in place, especially in the after-hours when there are fewer deterrents to inhibit criminal activity. Security guards, video surveillance systems, motion sensor lights, or even just fake cameras placed around the property are some of the common options people choose. Future of overnight security Smart business owners are starting to realize, however, that some of these traditional security measures are becoming antiquated and no longer cutting. The now and future of overnight security is in remote guarding. Pioneered by companies like Los Angeles-based Elite Interactive Solutions, which was founded back in 2007, remote guarding is revolutionizing the overnight security business. Minimizing criminal activity Remote guarding is fast becoming the most popular choice among commercial end-user property owners Remote guarding utilizes a combination of cutting-edge technology, “digital guards,” highly trained security agents, and local law enforcement if and when necessary to minimize the potential of criminal activity. For those adequately enlightened to its overwhelmingly impressive crime prevention capabilities, remote guarding is fast becoming the most popular choice among commercial end-user property owners to secure and protect their investments. What Is Remote Guarding? Remote guarding is a revolutionary concept and increasing trend in security systems that utilize a combination of methods to effectively analyze potential threats to property. Cameras and/or other monitoring devices running highly advanced algorithmic software are installed in strategic areas or vulnerable places onsite and remotely located security agents are immediately notified of any activity within a designated perimeter of the property. A blend of AI, cybersecurity, and video analytics When properly deployed by an expert provider, the technology stack includes a proprietary blend of video analytics, artificial intelligence, cybersecurity, and more. Done right, “noise” is effectively filtered out, allowing agents to act on legitimate alerts and achieve zero false alarms communicated to first responders. Today, there are a lot of terms and descriptions tossed around about remote guarding, remote video, virtual guarding, etc., but those attributes must be present to represent the true definition of the offering and its many virtues. Realtime situational awareness Many systems have a two-way speaker that allows the security agent to give a verbal warning When specially trained security agents are alerted to trespassers, possible intruders, or other suspicious activity, they analyze the situation in real time and determine the necessary level of action. Many systems have a two-way speaker that allows the security agent to give a verbal warning, known as a voice-down, to the individual(s) that they are being watched. Most perpetrators, often believing the response is emanating directly from security personnel on the property itself rather than from a remote command center, flee immediately. However, if the threat persists, the security agent enlists local law enforcement to get on the scene. Customized remote guarding When properly deployed, remote guarding systems are also customized to specific properties. A team of consultants visits the client’s property to evaluate its vulnerabilities and where to best place cameras and/or other monitoring devices for system efficacy. Traditional Security Shortfalls According to Keith Bushey, a retired commander for the Los Angeles Police Department, there is much frustration between law enforcement officers and potential victims of crime due to the historically unreliable performance of traditional burglar alarm systems and central monitoring stations. He states about 90% of security-related calls are false alarms, a problem that has been well-documented through the years. Onsite challenges When a legitimate emergency does occur, the perpetrators have often already done their damage When a legitimate emergency does occur, the perpetrators have often already done their damage and/or escaped by the time law enforcement arrives. Onsite security guards are not the remedy either as they bring their own set of issues and challenges. Unexpected costs Traditional security systems can also have unexpected costs. The cost is not only in the security guards’ paycheck or the cost of the equipment itself. The cost comes when an actual incident occurs. In worst-case scenarios, the security guard(s) are injured, the business suffers inventory loss, and/or damage is sustained to the property. The medical and other costs for the security guard(s), the loss of inventory, property damage, deployment of law enforcement resources, and possible fallout of legal expenses all add up. Even in the best-case scenario, false alarm expenses incur if law enforcement is dispatched. These, among many others, are some of the primary issues that remote guarding resoundingly answers as a superior alternative. A Bounty of Benefits Remote guarding systems have been proven to cut costs and be more effective than traditional security systems. Even though the monthly monitoring costs of remote guarding are significantly higher than traditional intrusion detection system monitoring, the much higher effectiveness in crime reduction, elimination of false alarms, and augmenting or replacement of manned guards result in a substantially higher return on investment (ROI) to the end user. Easy tracking of threats The security cameras already have their image captured on record, making them easier to track down For example, case studies have demonstrated reduced security costs for clients by 60%, on average. These reductions have come from the costs of security staff, inventory, or property loss, plus saving money on insurance premiums and deductibles. The nature of remote guarding reduces the risk and costs of false alarms, with professional security agents able to determine an actual threat before law enforcement is called. In a rare instance when a perpetrator escapes before law enforcement arrives or can detain the individual(s), the security cameras already have their image captured on record, making them easier to track down and identify. Reduction of false alarms The significant reduction in false alarms is greatly appreciated by law enforcement, as it allows them to focus on real emergencies or crises. Better relationships are also developed between clients and law enforcement, as remote guarding systems are highly reliable in providing accurate and real-time information to officers as they approach the scene. In short, it assists law enforcement in doing their job more effectively, as well as more safely thanks to having eyewitness information before engaging in an active crime scene. Partnership When you combine the decreased cost with the increased efficiency and success rate, it is easy to see why many commercial end-user property owners across the country are making the shift to remote guarding. It’s also an outstanding opportunity for professional security dealers and integrators to partner with a remote guarding services provider to bring a superior solution to their end customers and pick up a recurring monthly revenue stream in the process.
It’s no secret that the data security sector is constantly changing. It has an annual CGR of about 12.3%. Future trends in data security Much of this has to do with the rise of cybercrime in recent years, with reports showing that cyberattacks happen as often as every 39 seconds. To combat the growing rate of cybercrime, data security has been on the rise. As we journey further into this era, it becomes evident that a spectrum of significant trends is molding the future of data security. This exploration delves into a selection of these trends, unraveling their importance and the potential implications they carry 1. AI security tools will increase Artificial Intelligence is also being used in the development of smart attacks and malware The introduction of Artificial Intelligence in the data security industry brought significant changes, especially in cybersecurity. AI has been the golden standard for face detection, natural language processing, automated threat detection, and automated security systems. Additionally, Artificial Intelligence is also being used in the development of smart attacks and malware, bypassing even the latest security protocols in data control. And as time progresses, AI security tools will flourish and dominate the scene. Let’s take a more in-depth look at three of the top AI security tools. Targeted attack analysis tool Manufacturers utilize targeted attack analysis tools to uncover targeted and stealthy attacks. Artificial Intelligence can be applied to the program’s capabilities, processes, and knowledge. For instance, Symantec launched this tool to combat the Dragon 2.0 attack in 2022. The phishing attack reprimanded multiple energy companies while trying to gain access to their operational networks. Targeted Attack Analysis Tools can analyze incidents and look for similarities from previous situations. They also help detect suspicious activities and collect all the necessary data to determine whether a specific action is malicious. Intercept X tool Results from the Intercept X Tool feature high accuracy and a low false positive rate Sophos, a British security hardware and software company, launched the Intercept X Tool. It engages a neural network that records and analyses data like a human brain. Sophos’ Intercept X Tool can extract features from a single file and perform a deep analysis. It detects malicious activities within 20 milliseconds. Plus, it’s also trained to work on bi-directional sharing and real-world feedback of threat intelligence. Results from the Intercept X Tool feature high accuracy and a low false positive rate. IBM Watson Technology IBM’s QRadar Advisor uses IBM Watson Technology, a unique AI tool for fighting cyber attacks. Artificial Intelligence can auto-investigate activities and indicators for potential exploitation or compromise. With cognitive reasoning, IBM Watson Technology can present critical insights to accelerate the response cycle. Security analysts can utilize this technology to search for threat incidents, reducing the risk of letting them fly under the radar. 2. Blockchain as a security solution It guarantees no points of failure or hackable entrances that can expose datasets inside the system Blockchain is a type of distributed ledger technology (DLT) that aims to establish trust within an untrusting ecosystem. Today it’s one of the most robust cybersecurity technologies in the industry. Blockchain utilizes a decentralized ledger system, but your team members can still gain access to transparent information in the cloud. Members can also record, pass along, and view necessary transactional data in the blockchain. The entire blockchain process maintains data integrity within the system while establishing trust among team members. It guarantees no points of failure or hackable entrances that can expose datasets inside the system. Cybersecurity, biometrics Cybersecurity primarily benefits from these features because blockchain can create a secure and robust wall between data and hackers. On top of that, blockchain ledgers can include biometrics like fingerprints and retina scans. These prevent hackers from accessing any private data. Because blockchain is decentralized, it also limits hackable data. Together with the technology’s record-keeping system, each node is provided insight into data manipulation exposing real-time cybercrime attempts. 3. Increased and widened access control Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data Access control is critical in data security. More than a valuable security tool, business leaders can use access control to regulate people accessing any given resource. A company with an IT security setting can control who has the liberty to edit certain files. One of the primary goals of access control is to minimize threats or attacks to organizations and businesses to keep people and data secure. Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data protection laws. Benefits The benefits of increased and widened access control include: Identifying who can access and control your data at specific time intervals. Protecting data from overwriting, accidental deletion, and malicious intent. User permissions that can be readily changed. Compliance and regulation with data privacy laws. Central management of access to data through a reporting portal or a dashboard. Multi-factor authentication Access control comes in various types and systems, so it’s critical to know the features of what you’re looking for. The most common type is multi-factor authentication or MFA. It involves multiple steps before logging in, requiring the user to enter other relevant information besides the password. Some other examples of information include biometrics, answering a security question, or entering a code sent to the user’s email address. Two-factor authentication, role-based access control Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession. Another type of access control is role-based access control. In this setup, only one individual can set up access guidelines and grant permissions to specific team members within an organization. 4. Greater use of the zero-trust security model The zero-trust security model is a framework that requires every user within and outside the organization to undergo authentication, authorization, and validation. These are all essential to ensure proper security configuration before access is granted to the company’s applications and data. A zero-trust model assumes that anyone can cause data breaches and that a traditional network edge is not taken into effect. Moreover, it addresses the following modern-day challenges: Hybrid cloud environments. Security of remote workers. Ransomware threats. This framework utilizes the combination of multiple advanced technologies, including: A risk-based multi-factor authentication. Endpoint security. Identity protection. Cloud workload technology. The zero-trust model uses all these innovative tools for system identification, user verification, access consideration, and system security maintenance. Constant validation and monitoring Enforcing strict policies and compliance with data privacy laws are also essential Additionally, it also considers data encryption, email security, and asset verification before establishing connections with applications. The architecture of a zero-trust framework requires constant validation and monitoring of the users and the devices they are using. Enforcing strict policies and compliance with data privacy laws are also essential. More importantly, the zero trust architecture requires all organizations to be aware of all their available services and accounts to gain complete control of data handling and manipulation. 5. Increased privacy regulations Privacy regulations and policies guide organizations in proper data control, handling, and security. These policies guide organizations in proper data control, handling, and security. As a responsible business owner, you must comply with these regulations to avoid legal issues. With cybersecurity attacks becoming common, expect increased and stricter privacy regulations to be released in the next few years. While current policies are still taken into effect, various modifications and adjustments will occur to compete with the rising numbers of data breaches, thefts, data loss, and more. California Privacy Rights Act (CPRA) Currently, the California Privacy Rights Act (CPRA) is the most comprehensive legislation on state data privacy. It only started to take effect on January 1, 2023. The CPRA introduces the following principles: Broad individual consumer rights. Significant duties of people who need to collect sensitive and personal information. Additional definitions of data privacy and security. An individual’s duties include releasing information about data collection to concerned data subjects and proper access, correction, and deletion of information. Final thoughts 2023 is a big year for data security. Trends such as increased adoption of zero-trust policies, a greater reliance on AI security tools, and the implementation of blockchain as a security solution are all things we expect to see shortly. Staying up-to-date with these trends is important for keeping your business current and ensuring that you’re adhering to new and changing regulations. Doing so can give you an edge over the competition and keep you out of legal hot water.
Daniel May of Consort reviews the integration of access control systems in healthcare settings, outlining the benefits and key considerations decision-makers must make throughout product specifications. From patient safety and traversal to the protection of sensitive data and pharmaceuticals, healthcare environments are faced with several operational challenges. And where security remains at the forefront of decision-making, modern access control systems may often hold the answers. Physical security systems Hospitals in particular have developed into multi-faceted spaces that house hundreds to thousands of patients, staff, and visitors at any one time. In England for example, research has found in the three months leading to June 2023, an average of 44,626 people visited major hospital A&E departments each day, with over 16 million attendances typically recorded over the course of a year-not to mention an additional nine million logged at other minor units. For any building, this level of sustained footfall can request severe security difficulties For any building, this level of sustained footfall can invite severe security tests. With that, the need to deploy effective physical security systems in healthcare is clear. And so, as access control continues to become more readily adopted and new products enter the market, decision-makers are reminded to consider the requirements of their building, ensuring they select the solutions most suited to their settings and budget. Security controlled Patient safety will always remain the top priority in healthcare settings, and where matters of health and social care come into question, a diverse set of professional regulatory bodies are tasked with setting and maintaining high standards. When it comes to healthcare premises specifically, patient security and perimeter security often come hand in hand and are amongst the most pressing of challenges that decision-makers must face. To help address operational planning and potential design concerns in the NHS, the Health Building Note (HBN), provides general design guidance for healthcare buildings under HBN 00-01-citing the use of access control measures as a way of maintaining security and protecting the safety of patients, staff, and visitors. Use of access control Hospital buildings control varied levels of access for a number of security purposes Hospital buildings, for example, must control varied levels of access for a number of operational and security purposes. Routine scenarios exist where vulnerable patients are under monitoring and thus refrained from exiting the premises for their own safety, while at the same time, permitted staff must be able to reach their patients and medicines when required. For this, the use of access control is key. Equally, access credentials can also help management teams keep track of those who may be entering or exiting rooms with equipment and pharmaceutical supplies, deterring any unwanted visitors and opportunists in the process. Incorporation of access control systems On a similar note, regulations have set a minimum standard for how personal data should be stored and managed in healthcare environments, giving decision-makers an added responsibility to regulate staff-controlled areas with patient medical records. While instances of personal data breaches are rare, healthcare facilities and professionals are at legal risk should confidential data be found misused or missing. As such, the incorporation of access control systems has become essential in keeping data storage areas secure, with intuitive online systems capable of permitting access to staff with the correct credentials while simultaneously tracking who has requested clearance at digital entry points. HBN guidance Healthcare experts are better fitted to control the sheer volume of people entering and exiting To function effectively, healthcare facilities must always be perceived as safe places by the people who reside within them, and as HBN guidance implies, a unified physical security system can help address key safety and security concerns while enhancing patient and staff experience. Opportunely, access control systems are more accessible and adaptable than ever and combine several technologies such as mechanical locks and automatic doors with electronic access credentials in the form of smartphone apps, badge readers, and biometric scanners. By integrating these systems into the building’s existing infrastructure, healthcare professionals are better equipped to control the sheer volume of people entering and exiting the premises without impairing the general flow of movement and coordination around the facility. Better by design Despite the clear benefits offered to healthcare facilities, there are a number of considerations to be mindful of when choosing an access control solution. Poorly implemented systems can have an adverse effect on security and functionality - quickly costing healthcare organizations time and budget to rectify and replace the inadequate products that don’t meet the building’s requirements. For that reason, decision-makers and design teams are reminded that there is no single solution that fits all healthcare buildings. As such, it’s crucial for decision-makers to understand the systems that are being put in place throughout each of the touchpoints in their facility. Clear collaboration is required during periods of specification, where together, teams can ensure the selected product works on all angles, from meeting fire safety and sustainability standards to aesthetics and scalability. Modern access control products Scalability is a key area that decision-makers must review when selecting access control systemsFrequently overlooked, scalability is a key area that decision-makers must review when selecting access control systems. Such is their diverse nature; healthcare facilities can often change and develop as years go by, and by selecting a system that facilitates growth, such as a cloud-based solution-security and efficiency is long-established. While modern access control products are known for seamless integration, there are some systems that may restrict the ability to use different vendors throughout the remainder of the building’s infrastructure. This, in effect, causes a monopolization of products throughout the estate, which can have an adverse effect on growth by increasing costs and reducing the levels of service associated with the security system already in place. Improve security and safety A scalable and reliable access control system will continue to improve security and safety by adapting to a building’s new requirements-and all while having minimal impact on its operational network. And so, while technology will no doubt continue to influence and transform the access control market, healthcare facilities and their professionals must continue to remain educated on their own systems, ensuring they have the best options in place to keep their patients, staff, and visitors safe and secure for years to come.
Security beat
When it comes to security cameras, the end user always wants more—more resolution, more artificial intelligence (AI), and more sensors. However, the cameras themselves do not change much from generation to generation; that is, they have the same power budgets, form factors and price. To achieve “more,” the systems-on-chips (SoCs) inside the video cameras must pack more features and integrate systems that would have been separate components in the past. For an update on the latest capabilities of SoCs inside video cameras, we turned to Jérôme Gigot, Senior Director of Marketing for AIoT at Ambarella, a manufacturer of SOCs. AIoT refers to the artificial intelligence of things, the combination of AI and IoT. Author's quote “The AI performance on today’s cameras matches what was typically done on a server just a generation ago,” says Gigot. “And, doing AI on-camera provides the threefold benefits of being able to run algorithms on a higher-resolution input before the video is encoded and transferred to a server, with a faster response time, and with complete privacy.” Added features of the new SOC Ambarella expects the first cameras with the SoC to emerge on the market during early part of 2024 Ambarella’s latest System on Chip (SOC) is the CV72S, which provides 6× the AI performance of the previous generation and supports the newer transformer neural networks. Even with its extra features, the CV72S maintains the same power envelope as the previous-generation SoCs. The CV72S is now available, sampling is underway by camera manufacturers, and Ambarella expects the first cameras with the SoC to emerge on the market during the early part of 2024. Examples of the added features of the new SOC include image processing, video encoders, AI engines, de-warpers for fisheye lenses, general compute cores, along with functions such as processing multiple imagers on a single SoC, fusion among different types of sensors, and the list goes on. This article will summarize new AI capabilities based on information provided by Ambarella. AI inside the cameras Gigot says AI is by far the most in-demand feature of new security camera SoCs. Customers want to run the latest neural network architectures; run more of them in parallel to achieve more functions (e.g., identifying pedestrians while simultaneously flagging suspicious behavior); run them at higher resolutions in order to pick out objects that are farther away from the camera. And they want to do it all faster. Most AI tasks can be split between object detection, object recognition, segmentation and higher-level “scene understanding” types of functions, he says. The latest AI engines support transformer network architectures (versus currently used convolutional neural networks). With enough AI horsepower, all objects in a scene can be uniquely identified and classified with a set of attributes, tracked across time and space, and fed into higher-level AI algorithms that can detect and flag anomalies. However, everything depends on which scene is within the camera’s field of view. “It might be an easy task for a camera in an office corridor to track a person passing by every couple of minutes; while a ceiling camera in an airport might be looking at thousands of people, all constantly moving in different directions and carrying a wide variety of bags,” Gigot says. Changing the configuration of video systems Low-level AI number crunching would typically be done on camera (at the source of the data) Even with more computing capability inside the camera, central video servers still have their place in the overall AI deployment, as they can more easily aggregate and understand information across multiple cameras. Additionally, low-level AI number crunching would typically be done on camera (at the source of the data). However, the increasing performance capabilities of transformer neural network AI inside the camera will reduce the need for a central video server over time. Even so, a server could still be used for higher-level decisions and to provide a representation of the world; along with a user interface for the user to make sense of all the data. Overall, AI-enabled security cameras with transformer network-based functionality will greatly reduce the use of central servers in security systems. This trend will contribute to a reduction in the greenhouse gases produced by data centers. These server farms consume a lot of energy, due to their power-hungry GPU and CPU chips, and those server processors also need to be cooled using air conditioning that emits additional greenhouse gases. New capabilities of transformer neural networks New kinds of AI architectures are being deployed inside cameras. Newer SoCs can accommodate the latest transformer neural networks (NNs), which now outperform currently used convolutional NNs for many vision tasks. Transformer neural networks require more AI processing power to run, compared to most convolutional NNs. Transformers are great for natural language processing (NLP) as they have mechanisms to “make sense” of a seemingly random arrangement of words. Those same properties, when applied to video, make transformers very efficient at understanding the world in 3D. Transformer NNs require more AI processing power to run, compared to most convolutional NNs For example, imagine a multi-imager camera where an object needs to be tracked from one camera to the next. Transformer networks are also great at focusing their attention on specific parts of the scene—just as some words are more important than others in a sentence, some parts of a scene might be more significant from a security perspective. “I believe that we are currently just scratching the surface of what can be done with transformer networks in video security applications,” says Gigot. The first use cases are mainly for object detection and recognition. However, research in neural networks is focusing on these new transformer architectures and their applications. Expanded use cases for multi-image and fisheye cameras For multi-image cameras, again, the strategy is “less is more.” For example, if you need to build a multi-imager with four 4K sensors, then, in essence, you need to have four cameras in one. That means you need four imaging pipelines, four encoders, four AI engines, and four sets of CPUs to run the higher-level software and streaming. Of course, for cost, size, and power reasons, it would be extremely inefficient to have four SoCs to do all this processing. Therefore, the latest SoCs for security need to integrate four times the performance of the last generation’s single-imager 4K cameras, in order to process four sensors on a single SoC with all the associated AI algorithms. And they need to do this within a reasonable size and power budget. The challenge is very similar for fisheye cameras, where the SoC needs to be able to accept very high-resolution sensors (i.e., 12MP, 16MP, and higher), in order to be able to maintain high resolution after de-warping. Additionally, that same SoC must create all the virtual views needed to make one fisheye camera look like multiple physical cameras, and it has to do all of this while running the AI algorithms on every one of those virtual streams at high resolution. The power of ‘sensor fusion’ Sensor fusion is the ability to process multiple sensor types at the same time and correlate all that information Sensor fusion is the ability to process multiple sensor types at the same time (e.g., visual, radar, thermal, and time of flight) and correlate all that information. Performing sensor fusion provides an understanding of the world that is greater than the information that could be obtained from any one sensor type in isolation. In terms of chip design, this means that SoCs must be able to interface with, and natively process, inputs from multiple sensor types. Additionally, they must have the AI and CPU performance required to do either object-level fusion (i.e., matching the different objects identified through the different sensors), or even deep-level fusion. This deep fusion takes the raw data from each sensor and runs AI on that unprocessed data. The result is machine-level insights that are richer than those provided by systems that must first go through an intermediate object representation. In other words, deep fusion eliminates the information loss that comes from preprocessing each individual sensor’s data before fusing it with the data from other sensors, which is what happens in object-level fusion. Better image quality AI can be trained to dramatically improve the quality of images captured by camera sensors in low-light conditions, as well as high dynamic range (HDR) scenes with widely contrasting dark and light areas. Typical image sensors are very noisy at night, and AI algorithms can be trained to perform excellently at removing this noise to provide a clear color picture—even down to 0.1 lux or below. This is called neural network-based image signal processing, or AISP for short. AI can be trained to perform all these functions with much better results than traditional video methods Achieving high image quality under difficult lighting conditions is always a balance among removing noise, not introducing excessive motion blur, and recovering colors. AI can be trained to perform all these functions with much better results than traditional video processing methods can achieve. A key point for video security is that these types of AI algorithms do not “create” data, they just remove noise and clean up the signal. This process allows AI to provide clearer video, even in challenging lighting conditions. The results are better footage for the humans monitoring video security systems, as well as better input for the AI algorithms analyzing those systems, particularly at night and under high dynamic range conditions. A typical example would be a camera that needs to switch to night mode (black and white) when the environmental light falls below a certain lux level. By applying these specially trained AI algorithms, that same camera would be able to stay in color mode and at full frame rate--even at night. This has many advantages, including the ability to see much farther than a typical external illuminator would normally allow, and reduced power consumption. ‘Straight to cloud’ architecture For the cameras themselves, going to the cloud or to a video management system (VMS) might seem like it doesn’t matter, as this is all just streaming video. However, the reality is more complex; especially for cameras going directly to the cloud. When cameras stream to the cloud, there is usually a mix of local, on-camera storage and streaming, in order to save on bandwidth and cloud storage costs. To accomplish this hybrid approach, multiple video-encoding qualities/resolutions are being produced and sent to different places at the same time; and the camera’s AI algorithms are constantly running to optimize bitrates and orchestrate those different video streams. The ability to support all these different streams, in parallel, and to encode them at the lowest bitrate possible, is usually guided by AI algorithms that are constantly analyzing the video feeds. These are just some of the key components needed to accommodate this “straight to cloud” architecture. Keeping cybersecurity top-of-mind Ambarella’s SoCs always implement the latest security mechanisms, both hardware and software Ambarella’s SoCs always implement the latest security mechanisms, both in hardware and software. They accomplish this through a mix of well-known security features, such as ARM trust zones and encryption algorithms, and also by adding another layer of proprietary mechanisms with things like dynamic random access memory (DRAM) scrambling and key management policies. “We take these measures because cybersecurity is of utmost importance when you design an SoC targeted to go into millions of security cameras across the globe,” says Gigot. ‘Eyes of the world’ – and more brains Cameras are “the eyes of the world,” and visual sensors provide the largest portion of that information, by far, compared to other types of sensors. With AI, most security cameras now have a brain behind those eyes. As such, security cameras have the ability to morph from just a reactive and security-focused apparatus to a global sensing infrastructure that can do everything from regulating the AC in offices based on occupancy, to detecting forest fires before anyone sees them, to following weather and world events. AI is the essential ingredient for the innovation that is bringing all those new applications to life, and hopefully leading to a safer and better world.
Casinos offer several attractive applications for LiDAR, including security and business intelligence. Using laser sensors, the technology can replace the use of surveillance cameras. For casino security, LiDAR can track player movement and provides complete coverage and accuracy that have not been achievable by surveillance cameras. Massive coverage areas can save on costs of sensor deployment versus other technologies. LiDAR and its applications LiDAR is a method for determining ranges by targeting an object with a laser and measuring the time for the reflected light to return to the receiver. LiDAR sensors emit pulsed light waves into a surrounding environment, and the pulses bounce off surrounding objects and return to the sensor. The sensor uses the time it took for each pulse to return to the sensor to calculate the distance it traveled. LiDAR is commonly used in markets such as robotics, terrestrial mapping, autonomous vehicles, and Industrial IoT (Internet of Things). Today, casinos offer a lucrative emerging market for technology. LiDAR tracking enables casino operators to understand the guest path, journey, queue time, count Crowd management LiDAR can contribute to a casino’s guest experience by counting people at doors or in sections of the gaming floor to provide intelligence about crowd size to track occupancy. LiDAR tracking enables casino operators to understand the guest path, journey, queue time, count, and other statistical information by comparing previous time frames to current occupancy levels. This approach allows them to understand digital media advertisement and experience placement. Aid in advertisement “Inside a casino, sensors are deployed like surveillance cameras,” says Gerald Becker, VP of Market Development & Alliances, Quanergy. “But instead of security, they are used to provide anonymous tracking of all people walking through the gaming floor. We can get centimeter-level accuracy of location, direction, and speed of the guests. With this data, we can access the guest journey from the path, dwell count, and several other analytics that provides intelligence to operations and marketing to make better decisions on product placement or advertisement.” Quanergy Quanergy is a U.S.-based company that manufactures its hardware in the USA and develops its 3D perception software in-house. Quanergy has various integrations to third-party technology platforms such as video management systems (VMSs) in security and analytics for operational and business intelligence. Perimeter security Sensors can be mounted to a hotel to monitor for potential objects being thrown off the hotel LiDAR is deployed in both exterior and interior applications. For the exterior of a casino or resort, sensors can be mounted to a hotel to monitor for potential objects being thrown off the hotel, or people in areas where they should not be. For example, they can sense and prevent entrance to rooftops or private areas that are not open to the public. Some clients install sensors throughout the perimeter of private property to safeguard executives and/or a VIP’s place of residence. Flow tracking and queuing capabilities Tracking crowd size can initiate digital signage or other digital experiences throughout the property to route guests to other destinations at the property. It can also help with queue analysis at the reservation/check-in desk or other areas where guests line up to tell operations to open another line to maintain the flow of guests passing. Flow tracking and queuing capabilities help casino operators to understand which games groups of customers frequent and allow for the optimization of customer routing for increased interaction and playtime on the casino floor, quickly impacting the financial performance and return of the casino. No privacy concerns LiDAR provides a point cloud; its millions of little points in a 3D space create the silhouettes of moving or fixed objects The main hurdle right now is market adoption. LiDAR is an emerging technology that is not so widely known for these new use cases, says Becker. “It will take a little bit of time to educate the market on the vast capabilities that can now be realized in 3D beyond traditional IoT sensors that are available now,” he comments. One benefit of LiDAR is that it poses no risk of personally identifiable information (PII) and therefore no privacy concerns. No PII is captured with the technology. Cameras can capture images and transmit them over the network to other applications. However, LiDAR provides a point cloud; its millions of little points in a 3D space create the silhouettes of moving or fixed objects. IoT security strategy There is a lot of interest from surveillance and security to include marketing and operations, says Becker. “LiDAR will become a part of the IoT security strategy for countless casinos soon. It will be common practice to see LiDAR sensors deployed to augment existing security systems and provide more coverage.” Also, the intelligence gained with the accuracy of tracking guests anonymously provides peace of mind to the visitors that they are not being singled out or uniquely tracked but provides valuable data to the casinos that they have not been able to capture before. “This will help them maximize their operations and strategy for years to come,” says Becker.
The cloud is here to stay. Its resilience and ability to connect the world during the COVID-19 pandemic has proved its worth, even to the uninitiated who have now witnessed first-hand the value of connected systems. Video and access control as a service provides a flexible and fluid security and business solution to meet the demands of a rapidly evolving industry, where the changing threat landscape means investing in the cloud is an investment towards success. This article will look back at our articles in 2020 about the growing popularity of cloud solutions for physical security, with links to the original content. Product offering While most people agree on the definition of “cloud,” there are several points about the terminology that may require clarification. Private cloud or public cloud? VSaaS or unlimited storage for video? Beyond the basics, the terms become foggy, reflecting a variety of notions about how cloud services fit into the broader physical security marketplace. As cloud usage becomes more popular, it’s important that marketers be precise in their terminology, and that integrators and end users be diligent in understanding the specifics of available product offerings. Different meanings “The cloud has many different possible connotations, depending on the context,” says Yu Hao Lin of Rasilient Systems, one of our Expert Roundtable panelists. For example, corporate CIOs will more likely understand the cloud to be a private cloud platform. As such, the public cloud is a ubiquitous term while the private cloud is more specified. Cloud system security Security of cloud systems is an ongoing discussion in the industry, especially how cloud system cybersecurity compares to that of on-premise systems. Our Expert Panel Roundtable weighed in on this question. “While both kinds of security systems serve their purpose, it can be argued that the streamlined updates that are commonplace with cloud-based solutions may put them at more of an advantage when it comes to data security,” says panelist Eric Widlitz of Vanderbilt Industries. “Also, most reputable cloud-based solutions are running in secured data centers by companies such as Google, Microsoft, or Amazon, so you also get to take advantage of all the security layers they have protecting your data.” Hybrid cloud video security solution A growing list of cloud players reinforces the importance of the cloud in the future of physical security There are several relatively new companies pushing cloud in a big way. Verkada is fast-growing company currently currently focusing to deliver an all-in-one hybrid cloud video security solution powered by edge processing inside the camera. The growing list of cloud players reinforces the importance of the cloud in the future of physical security. Combining AI and cloud video One company investing in the cloud is Eagle Eye Networks, which has raised $40 million of Series E funding from venture capital firm Accel to finance the realization of their vision to combine AI and cloud video. The money will allow Eagle Eye to continue its steep growth curve and leverage AI on its true cloud platform to reshape video surveillance. “The investment will make video surveillance smarter and safer for end-users,” says Ken Francis, President. Eagle Eye offers an application programming interface (API) to enable the integration of best-in-breed third-party AI and analytics systems to leverage the video. Eagle Eye is also investing in its own AI development and hiring additional development and customer service personnel. Hirsch Velocity Cirrus and MobilisID Identiv introduced the Hirsch Velocity Cirrus cloud-based Access Control as a Service (ACaaS) solution and MobilisID smart mobile physical access control solution. Hirsch Velocity Cirrus is an optimal solution for both end-users and integrators, with lower upfront costs, reduced maintenance, enhanced portability, and the future-proof assurance of automatic security updates and feature sets. MobilisID is a smart mobile physical access control solution that uses Bluetooth and capacitive technologies to allow frictionless access to a controlled environment without the need to present a credential. Advantages and disadvantages Advantages of cloud-based physical security technologies are many, when supporting staffThe advantages of cloud-based physical security technologies are many, and have wide-ranging applications for all areas of the transport sector; across stations, transport hubs, and vehicles. When used to support staff and complement existing processes, such systems can prove invaluable for transport professionals in helping to create a safer working environment, promoting confidence among personnel and passengers, and assuring passengers who are fearful about the current pandemic that all possible precautions are being taken during their journey. 5G supporting cloud-based applications 5G is the first communication environment that is cloud-native. As such, 5G networks will support cloud-based applications in a way that 4G, 3G and 2G can’t support. For instance, sensors (e.g. in a manufacturing plant) often have small internal storage and rely on synced devices (e.g. gateways) to interact with the cloud. Soon, these sensors will be able to work more efficiently, interacting with the cloud via the ultra-low latency and the edge computing capabilities supported by 5G networks. Increasing use of IoT Unlike current IoT services that make performance trade-offs to get the best from these existing wireless technologies, 5G networks will be designed to bring the high levels of performance needed for the increasing use of IoT. It will enable a perceived fully ubiquitous connected world, with the boosted capacity offered by 5G networks transferring exponentially more data at a much quicker rate.
Case studies
Hotel Montresor Tower, a stylish four-star destination just outside Verona, Italy, has successfully upgraded its fire detection infrastructure with Hochiki's advanced Latitude life safety platform. As part of a comprehensive refurbishment, the hotel partnered with installer TOLA & C. SRL to install a new Latitude 8‑loop control panel, complemented by voice alarm devices (VADs), call points, and ESP sensors. Black‑finished ESP detectors Legacy sensors were updated to the ESP range to comply with the Italian standard UNI11224 The Latitude system was chosen for its intuitive programming and powerful Hotel Mode, which offers controlled alarm delays, minimizing unnecessary disruption while maintaining strict safety compliance in guest rooms. To preserve the venue’s contemporary aesthetic, sleek black‑finished ESP detectors were installed in the newly renovated conference center. Elsewhere, legacy sensors were updated to the ESP range to comply with Italian standard UNI11224, which mandates system upgrades every 12 years to ensure reliability and performance. Integrating the Latitude panel and ESP devices Director Luca Montresor commented on the upgrade: “We’ve been extremely satisfied with Hochiki’s technology over the years—it’s reliable, easy to maintain, and straightforward for our staff to operate. When it was time to expand and refurbish, there was no question we’d stay with Hochiki for the new system too.” By integrating the Latitude panel and ESP devices, Hotel Montresor Tower has not only elevated its life safety infrastructure but ensured seamless visual integration and enhanced operational efficiency, future‑proofing the guest experience without compromise.
Interface Systems, a managed service provider of security, actionable insights, and purpose-built networks for multi-location businesses, announced that Nicker Management, a fast-food franchise operator in the Los Angeles area, has successfully implemented Interface’s Virtual Security Guard solution. By deploying Interface’s advanced security technology, Nicker Management has enhanced safety, reduced operational costs, and provided a secure environment for employees and customers. Nicker Management Nicker Management, led by sisters Nicole Harper Rawlins (CEO) and Kerri Harper-Howie (Co-owner), operates 24 fast-food restaurants across South LA, Compton, Lynwood, and Carson. Faced with persistent security challenges, including loitering, panhandling, and criminal activity, the company sought a modern, cost-effective solution to protect its employees and guests. Addressing critical security concerns Nicker Management chose Interface Systems to implement the Virtual Guard solution at one of its restaurants “We’re faced with lots of challenges with crime, unhoused people, and individuals suffering from mental and/or substance abuse issues,” said Harper Rawlins. “It creates significant risk at our restaurants. Over the years, we experimented with a range of security solutions, and hiring on-site guards quickly became costly and unsustainable.” After evaluating various options, Nicker Management chose Interface Systems to implement the Virtual Guard solution at one of its restaurants, ensuring a proactive and scalable approach to security. How can Virtual Guard Solution help? 24/7 Monitoring & Rapid Response – Trained intervention specialists continuously monitor restaurant locations to deter loitering, panhandling, and aggressive behavior in real time. Automated Voice-Downs – Proactive announcements throughout the day signal active monitoring and reinforce security presence. Virtual Tours – Scheduled and unscheduled remote video assessments help identify threats, suspicious activities, and compliance issues. Employee Security Escorts – Live monitoring ensures employees' safe passage to and from their vehicles during vulnerable times such as shift changes, and opening, and closing hours. Secure working environment “Knowing there’s a professionally trained security team on standby gives us confidence that we can maintain a secure working environment at all hours,” said Harper Rawlins. The deployment of Virtual Guard has streamlined security operations at Nicker Management’s restaurant, allowing staff to focus on providing excellent customer service without the burden of handling security incidents. 24/7 monitoring With 24/7 monitoring by Virtual Guard, employees and customers feel safer, and staff no longer have to handle security threats alone. In addition, automated alerts also remind employees of key procedures during shift changes. The system's effectiveness was demonstrated during a recent incident when a loiterer refused to leave the restaurant lobby. The staff triggered a silent alarm, and the Virtual Guard team immediately responded with a voice-down, prompting the individual to leave without further incident. Optimizes costs “Interface’s Virtual Guard solution empowers franchise businesses like Nicker Management to address security risks effectively while optimizing operational costs,” said Sean Foley, Chief Revenue Officer at Interface Systems. “Our innovative approach allows employees to focus on delivering excellent service, knowing their safety is in trusted hands.”
Nestled in the scenic countryside near Umberleigh, Northcote Manor Country House Hotel & Spa combines award-winning accommodation, fine dining, and a tranquil spa. This 18th-century country house is devoted to providing elegance and security for its guests. Partnering with local locksmith experts, Keyhole Surgery upgraded its security management by installing a Mul-T-Lock MTL™300 master key suite. MTL™300 master key system Mul-T-Lock’s MTL™300 master key system offers ideal security for Northcote Manor’s 16 guest rooms. The suite enhances safety across the hotel, giving management precise control over key access while ensuring guests' peace of mind. Richie Herkes, General Manager of Northcote Manor Country House Hotel & Spa, commented, “At our beautiful Georgian manor, dating back to Tudor times, we’re committed to providing our guests with a serene and secure environment. We trusted David to deliver an upgrade to our room security’s existing system that could accommodate." Additional security layer With the Mul-T-Lock MTL™300 master key suite, management can establish a hierarchical access structure "He recommended the Mul-T-Lock MTL™300 master key suite as a secure yet discreet access management across all rooms and common areas, improving our operations without compromising style.” With the Mul-T-Lock MTL™300 master key suite, management can establish a hierarchical access structure, ensuring only those with the appropriate permissions can enter restricted room areas at any given time. The capability to manage multiple permission levels adds a critical layer of security, minimizing unauthorized access and enhancing operational efficiency. Easy installation improves overall management David Pearcy of Keyhole Surgery explained why the MTL™300 was the ideal choice for the upgrade, “For a distinguished property like Northcote Manor, it was essential to implement a high-security solution that wouldn’t interfere with the building’s stunning historic appeal." "The Mul-T-Lock MTL™300 suite provides the right balance with a cylinder design that is easy to install on existing doors. The master key system allows staff to access essential areas quickly and efficiently, reducing the need for multiple keys and improving overall management.” Secure and flexible access management system The Mul-T-Lock MTL™300 master key suite minimizes keys in operation for Northcote Manor The Mul-T-Lock MTL™300 master key suite minimizes keys in operation for Northcote Manor, while maintaining a secure, flexible, and efficient access management system specifically designed to give authorized personnel-controlled access to the hotel’s rooms and facilities. Ian Thresher, Mul-T-Lock regional sales manager for the South-West, shared his thoughts on the partnership, “Northcote Manor’s decision to work with Keyhole Surgery as an established Mul-T-Lock authorized dealer and to implement the MTL™300 master key suite reflects a forward-thinking approach to hospitality security." Precise security management "MTL™300 offers an elegant, streamlined solution that aligns perfectly with the hotel’s dedication to both guest comfort and operational excellence." "By reducing key clutter and enabling precise security management, this system helps Northcote Manor retain its renowned beauty and charm safely for many, many years to come.”
Geutebrück video security provides comprehensive protection for professional users, from perimeter security to process documentation. The open platform for video management G-Core offers a variety of interfaces to third-party systems and is the basis for integrated security systems. The latest integration with Commend's communication solutions supports efficient communication and security for users from various verticals such as banking, industrial production, police and corrections authorities, health care, education, road and air traffic, parking facilities, and hotels. Direct voice contact By linking Geutebrück's G-Core Video Management System and Commend's communication servers, information, and commands can be exchanged effortlessly between the systems. For example, users of a Commend intercom station can call up video images from specific cameras at the click of a mouse, assess the situation, and then make direct voice contact with the other party, e.g. to respond immediately to emergency calls. Advanced analysis The integration creates a safer working environment and minimizes training times and operating errors This integration not only offers greater transparency but also simplifies the users' daily as they do not have to switch between different platforms. This creates a safer working environment and minimizes training times and operating errors. The integration also offers advanced analysis options, such as the automatic detection of suspicious activities using AI algorithms and the creation of detailed security reports. Flexibility and scalability The flexibility and scalability of the combined solution allow the security system to be adapted to changing requirements and simplify the integration of additional components. Overall, the integration provides an improved security infrastructure that significantly increases the efficiency, security, and user-friendliness of monitoring and communication systems.
HID, the worldwide pioneer in trusted identity solutions, announces that Royal Jersey Laundry has introduced a new tracking feature of HID’s linen management platform at each of its 5-star hotel customer sites to guarantee that drivers drop off and collect precise linen stock and that costly errors are avoided. Linen tracking This new feature replaces a paper-based system used by drivers for the management of cages filled with clean/soiled linen delivered/collected at customer sites. It provides detailed end-to-end tracking of linen cages across multiple customer locations throughout the whole cycle of washing, packing, delivery, and collection, a complex process given that 550,000 pieces are laundered each week for numerous clients. Royal Jersey Laundry Royal Jersey Laundry works with most five-star hotels in London including The Dorchester, The Carlton Tower Jumerah Founded in 1915, Royal Jersey Laundry is one of the few cleaners servicing the luxury hotel sector. Based in a 25,000 square-foot purpose-built facility in Dagenham, rebuilt in 2021 for £15 million after a fire, it works with most five-star hotels in London including The Dorchester, The Carlton Tower Jumerah, The Peninsula London, and The Ritz. Need for constant communication Supporting the five-star segment is demanding given the constant communication required between the hotel and laundry, exacting standards, and the quantity and range of items to be laundered. This includes duvets, sheets, towels, and bath robes along with smaller items such as foot mats, drink coasters, shaving towels, and dry cleaning for guests themselves. Royal Jersey Laundry operates 24/7, employs 150 staff members, and washes 40 tons of linen per day. Maintaining laundering schedule Five-star hotels prefer to use linen they own with five sets kept of everything, allowing them to maintain a schedule In contrast with budget and mid-level hotels, five-star hotels prefer to use linen they own with five sets kept of everything, allowing them to maintain a rigorous laundering schedule and ensure guests always receive fresh, cleaned linens. “An average 300-bed hotel will have around 30,000 items of linen which will cost around £250,000,” says James Lincoln, Royal Jersey Laundry’s managing director. “The volume of linen is so high and it’s always moving such that accurate inventory control was a major challenge verging on the impossible.” HID cloud-based RFID linen management system Before the HID cloud-based RFID linen management system, everything was done manually. Laundry staff would check items off ironing/folding machines, a wholly error-prone process, and log the quantities on pieces of paper. The operational overhead for the laundry was exacerbated as the various linen items from the different hotels had to be kept separate, too. “Linen is everywhere: on beds, in cupboards, in transit, and at the laundry, yet no one had full insight into stock levels and, when things went missing which often happened, typically we’d get blamed,” says Lincoln. Real-time linen inventory management LinTRAK tags are sewn into linen items by laundry staff or linen manufacturers during the production process To address these problems, Royal Jersey Laundry installed a real-time linen inventory management system from HID combining LinTRAK® RFID tags, a full set of RFID equipment including table-top and conveyor-belt scanners, one RFID portal and one cabin scanning unit, and cloud-based Acuity software. The discrete LinTRAK tags are sewn into linen items by laundry staff or linen manufacturers during the production process. Some hotels also use LinTRAK tags to manage staff uniforms and restaurant linens such as napkins and tablecloths. HID LinTRAK textile tags Around 40% of Royal Jersey Laundry hotel customers have transitioned to the HID linen management solution and connect via Acuity’s web portal. Once cleaned, the linen is packed into cages, and scanned in seconds through HID’s RFID cabin station. Items are automatically counted, with delivery notes generated including billing information. HID’s Acuity software integrates with the laundry’s Sage accounting software to generate invoices. Benefits of textile tags The implementation of HID LinTRAK textile tags, RFID stations, and the Acuity software platform has radically changed how Royal Jersey Laundry operates, delivering a range of benefits: Fast Return on Investment: Since the installation of the HID equipment in 2019, the system has already paid for itself given the efficiency and productivity gains. Better use of people resources: Laundry and housekeeping staff no longer waste time on dull and resource-intensive activities like manually counting linen. They have been redeployed to more productive work, generating 10-20% savings in labor costs. Better visibility of stock levels: As hotels know exactly the location and quantity of linen, they are better able to cater to peak demand, reducing linen expenditures by up to 30%. Improved responsiveness and customer satisfaction: Access to in-depth data generated by the Acuity platform means the laundry can quickly answer customer queries. “We give hotels complete transparency about where their linen is in the cleaning and delivery cycle. There are just no grey areas anymore,” says Lincoln. Increased security of expensive linen assets: While theft of linen at five-star hotels is rare, it does happen. RFID tagging enables better monitoring of expensive bedding and towel investments. Enhanced reliability and productivity: Operations are more efficient as RFID-enabled items can never be lost or misplaced. Furthermore, digital scanning results in faster processing of items. “We’re effectively two businesses: the laundry itself and a logistics operation. We run a mixed fleet of lorries and electric vans which nip in and out of London three times a day picking up and delivering garments for hotel customers using us for guest work,” adds Lincoln.
The wellness resort situated in the Pune district offers restorative treatments including revitalizing yoga therapies, naturopathy, and Ayurveda. Embracing a holistic approach, they seamlessly blend traditional methods such as acupressure, acupuncture, and physiotherapy with alternative therapies like bird watching, star gazing, and animal-assisted therapy. This unique fusion of rejuvenating treatments harnesses the power of nature to facilitate a radical transformation towards a beautiful life and optimal health. Challenges The resort encompasses various facilities like a hotel, administrative office, school, factory, and security office across a sprawling 68-acre site. Their existing consultant recommended PBX systems of the different brands along with digital handsets, that challenged the possibility of investment optimization. Also, they were hesitant to abandon their current fiber network. To elaborate on their challenges: Adoption of modern communication with existing Infrastructure: Their investment in existing infrastructure needed protection, and a provision had to be made to modernize the communication using existing infrastructure. Managing different protocols: Interface with existing and different telecom networks requires managing different protocols, which can be cumbersome, time, and energy-consuming. Requirement of modern phone features: They required advanced features like Abbreviated Dialing, Call Pick Up, and Internal Call Restriction, to become efficient in day-to-day operations. Stipulated Time-frame: The inauguration date of the establishment was already made public and thus the task had to be completed within a stipulated time frame. Solution This included the Matrix range of IP-PBX, VoIP - FXO - FXS, and VoIP - PRI Gateways Matrix Comsec in partnership with SMB Automation analyzed the challenges of communications and crafted a solution that was the best fit. The solution offered was based on the prelude of utilizing existing infrastructure and amalgamation of Matrix Telecom Solutions within a stipulated time frame. This included the Matrix range of IP-PBX, VoIP - FXO - FXS, and VoIP - PRI Gateways that optimized the feasibility of communication and helped the firm become more efficient. The solution includes: The IP-PBX included ETERNITY GENX12SAC. This enabled them up to 240 Analog users with 64 CO Ports. Additionally, third-party PMS Integration with ETERNITY GENX12SAC was made possible. The VoIP - FXO - FXS Gateway included SETU VFX808, which enabled them a smooth transition to modern communication while maintaining existing infrastructure through features like 9 SIP accounts, peer-to-peer and proxy calling between distant locations, etc. The VOIP-PRI gateways included SETU VTEP, which comes with features of 125 SIP Trunks and up to 60 simultaneous calls. A third-party PBX was integrated with the gateway. The IP phones included SPARSH VP510E and SPARSH VP210. This came with features like an LCD Graphical display, Context-sensitive keys, Built-in 16 DSS Keys, Polyphonic ring tune, and much more. Results All the properties were brought to work on a single communication platform and proved to be beneficial The solution so implemented enabled them to reap the benefits of modern communication while also enabling them to make the best out of the existing infrastructure. Additionally, all the properties were brought to work on a single communication platform and proved to be beneficial in more than one way. The Hybrid IP-PBX enabled them to universal Network Connectivity through PSTN, GSM, and VoIP connectivity, LDAP Client Support to centralize and ease phonebook management, Logical Partitioning that prevents the conduct of any legal offenses related to Telecom regulations, and much more. The VoIP - FXO - FXS Gateway enabled them, VoIP access to traditional PBX, Multi-site connectivity with centralized telecom management, Next-generation conveyance facilities like call detail records of up to 2000 calls, Secure communication bridging with VoIP security over SRTP/TLS encryption, etc. The VOIP-PRI gateway, SETU VTEP, provided much-needed Least-cost routing ensuring that the call is always placed on the most appropriate network resulting in the optimization of the feasibility of calls. The IP desk phones helped provide advanced features like Call Pick up, Call Forward, Call Waiting, and Call Transfer along with an Intuitive interface, that enabled employees to become efficient while simultaneously, enhancing user experience.


Round table discussion
Headlines of violence in our schools are a reminder of the need to keep educational institutions safe. In fact, if there is a positive aspect to the constant bombardment of headlines, it is that it keeps our attention perpetually focused on how to improve school security. But what is the role of physical security systems? As the new school year begins, we asked this week’s Expert Panel Roundtable: Are schools safer because of physical security systems? Why or why not?
As physical security technologies become more complex, it is incumbent on the dealer/integrator to have the skills and expertise needed to ensure that a system operates smoothly. The value of integrators increasingly rests on the skill sets they bring to bear when installing a system. If the skills are missing, there is a problem. We asked this week’s Expert Panel Roundtable: What missing skills among security integrators can cause problems for customers?
Driving the smart homes market is the convenience of simple technology solutions. Almost every home now has a “smart speaker” that makes it easier than ever for homeowners to interface and control their technology. But where does security fit into the new landscape of smart home systems? We asked this week’s Expert Panel Roundtable: What’s new in smart homes and residential security systems?
Products