Drones
Aetina Corporation, a pioneering provider of Edge AI solutions, has announced the launch of its next-generation MXM AI Accelerator Module series accelerated by NVIDIA RTX PRO Blackwell Embedded GPUs, which is part of its CoreEdge MXM AI Module family. This new series is accelerated by the NVIDIA Blackwell GPU platform to deliver up to 3X the AI performance uplift of its predecessor, establishing a new benchmark for advanced AI computing at the edge These modules are designed to be compact,...
Uvision Group, a global pioneer in smart integrated systems, has announced the complete acquisition of SpearUAV, an Israeli defense tech company, developer of encapsulated AI-based loitering systems. The acquisition marks another significant step in Uvision’s continued expansion, and in its strategy to deliver a comprehensive, multi-layered approach of loitering munitions across all domains to customers around the globe. This acquisition will accelerate SpearUAV’s ability to realiz...
Drones are poised to fill long-standing gaps in physical security. Fixed cameras leave blind spots, and human guards cannot quickly cover large or complex properties during high-risk moments. Drones fill the gaps, providing a missing mobile layer, offering unmatched speed, broad aerial visibility, and proactive coverage that elevates security from reactive to truly responsive and deterrent. As an added element in security systems, drones complement fixed cameras, access control, and license pla...
It is the time of year when city centers transform, as outdoor Christmas markets fill town squares and high streets. An estimated 6,000 markets will open across Europe during the festive season, with some of the largest — including Nuremberg’s Christkindlesmarkt, London’s Hyde Park Winter Wonderland and Craiova in Romania — welcoming millions of visitors. Sadly, these popular events have in recent years been the subject of attacks, most notably Berlin in 2016 and the tra...
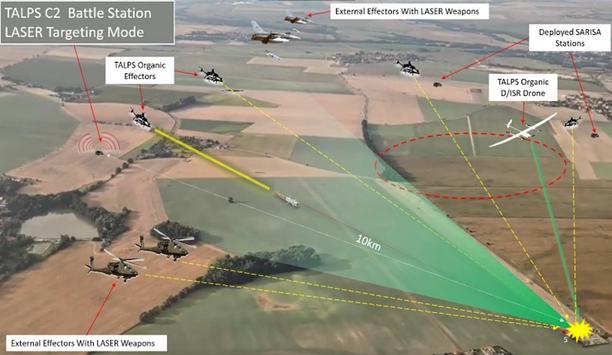
SAS Technology successfully participated in the Hellenic Armed Forces exercise “Aisios Oionos 2025”, held in the wider Alexandroupolis–Evros region. During the exercise, the company demonstrated for the first time the TALPS (Tactical Autonomous Laser Precision Strike) system — an advanced autonomous precision-strike capability developed as part of the ongoing operational employment of the UCAV SARISA II. The event was honored by the presence of the Minister of National...
Suprema, a pioneer in AI-powered access control and security solutions, announced the launch of BioStar X, its most advanced unified security platform. BioStar X unifies world-pioneering biometric access control and video surveillance, into a single, scalable platform, delivering total control, integrated monitoring, and enterprise-grade resilience. Advanced access control features The new BioStar X offers total control through a unified monitoring console. Administrators can view intera...
News
Secutech Thailand 2025 opened at the Queen Sirikit National Convention Center (QSNCC), placing the spotlight firmly on smart security and fire safety technologies. The show will take place alongside Fire & Safety Thailand, Thailand Smart City Expo, and EdTEX, featuring over 400 exhibitors from more than 10 countries and regions. This global cross-section offers visitors the opportunity to explore the latest industry-wide innovations across the 11,600 sqm fairground. A comprehensive fringe program includes seminars where industry experts will share valuable insights on cutting-edge smart technologies, fostering both collaboration and education. Supported by robust government and public sector backing, the show acts as a key nexus for advancing Thailand’s smart city vision. Future of security and fire safety Ms Regina Tsai, General Manager of Messe Frankfurt (HK) Ltd – Taiwan Branch, offered insights into the show’s smart product focus: “We recognize that the future of the security and fire safety industries lies in smarter, more integrated solutions." "Secutech Thailand has brought together the most innovative exhibitors, pioneering industry experts, and key government and public sector partners to create a dynamic hub where knowledge, technology, and collaboration intersect to shape the future of both industries.” Smart city transformation A new strategic partnership with N.C.C. Management and Development, organizers of the co-located Thailand Smart City Expo, significantly broadens visitors’ access to cross-sector business opportunities and reinforces Secutech Thailand’s position as the country’s pioneering platform for security and fire safety innovation. Ms Tsai explained: “Our partnership with N.C.C. Management and Development elevates the show’s strategic value by enabling deeper integration and unlocking substantial cross-sector business opportunities for both visitors and exhibitors.” This collaboration, especially when considered alongside the concurrent Fire & Safety Thailand and co-located EdTEX, will help accelerate Thailand’s smart city transformation while broadening the scope of opportunities for visitors. Latest smart security and fire safety applications To facilitate simpler sourcing, Secutech Thailand will feature five specialized solution categories that showcase the latest smart security and fire safety applications: Surveillance & Access Control, which includes AI cameras, biometric access, and visitor management platforms to enhance security and efficiency. Fire & Safety Systems, presenting detectors, alarms, and suppression technologies to protect lives and assets. Disaster Prevention & Critical Communication, offering seismic monitoring, gas detection, PA/evacuation systems, and anti-drone solutions crucial for urban resilience. Smart Technologies & Mobility, highlighting 5G, IoT, building automation, robotics, EV charging, and intelligent traffic management. Integrated Safety & Security Systems, demonstrating the integration of video analytics, cloud computing, and big data for comprehensive urban management. Fringe Program Seminar Highlights Complementing these solution categories is an extensive fringe program where industry experts will share key insights on the smart technologies shaping the future of security, fire safety, and smart cities. Designed to encourage knowledge exchange, insightful seminars will equip attendees with the tools and understanding needed to navigate and stay ahead of emerging trends in the rapidly evolving industry landscape. Highlights include: AI Disruption and the Future of Smart Factories: Opportunities, Challenges, and Adaptation for Smart Cities: Mr Thammarat Arsasuwan, a lecturer at Siam Technology College, will reveal how AI is transforming smart factories and the implications for smart city development. Digital Futures of Urban Living: Shaping Smart Cities with IoT and AI: Dr Suthat Krongchon of the Thai IoT Association will explain how IoT and AI technologies are driving the evolution of future urban living and smart city planning. Safe and Smart Use of Drones in Security and Smart City Applications: Mr Kasitbhat Intuyos, from the Civil Aviation Authority of Thailand (CAAT), will talk about the best practices and safety considerations for drone use in security and smart city contexts. Development of the Thai AI platform model Other seminar topics will cover innovation in disaster prevention and mitigation, sustainable CCTV solutions, cybersecurity for smart infrastructure, and the development of the Thai AI platform model for smart city applications – highlighting the technologies and strategies driving the future of urban resilience, security, and sustainable development. This year’s show benefits from strong support by key government and public organizations driving the nation’s adoption of smarter security and fire safety technologies. This wide-ranging cross-sector backing highlights the event’s extensive industry representation and demonstrates its role in preparing visitors to capitalize on major government and industry initiatives like Thailand 4.0 and the Eastern Economic Corridor (EEC). Some of the key supporting organizations participating at Secutech 2025 include: Association of Municipalities and Cities Bangkok Fire and Rescue Department Drone Association of Thailand Fire and Rescue Association National Cyber Security Agency National Municipal League of Thailand Thai Chamber of Commerce Thai Generator Association Thai IoT Association Thai Intelligent CCTV Association Thai Mechanical and Electrical Consulting Engineer Association Thai Security Association The Building Inspectors Association The Civil Aviation Authority of Thailand Thailand Convention Exhibition Bureau Thailand Information Security Association Thailand Productivity Institute Fire safety products There will be much for visitors to explore on the show floor, with highlights including pioneering security exhibitors such as HIP Global Co Ltd, Motorola Solutions, Vive Co Ltd, and many more, while featured fire safety products range from Dahua & Wisualarm’s smart fire detection systems to Sanlien Technology Corp’s expert structural and vibration monitoring solutions. The fair’s business matching program facilitates strategic connections between exhibitors and key industry stakeholders. Buyers from the Thai government, local hospitals, hotels, law enforcement agencies, industrial sectors, and provincial fire stations are actively invited to participate. With over 115 sessions already scheduled, the program seeks to maximize opportunities for exhibitors and buyers to forge successful partnerships within a rapidly evolving market increasingly focused on smarter, integrated solutions.
Teledyne FLIR OEM, a Teledyne Technologies Incorporated company (NYSE: TDY) and the global pioneer in enabling thermal imaging innovation, announced its latest Thermal by FLIR collaboration with SYPAQ Systems, one of Australia's pioneering sovereign drone manufacturers. The new CorvoX small unmanned aerial system (SUAS), featuring the NDAA-compliant and ITAR-free Boson® thermal infrared (IR) camera, is under contract to be delivered to the Australian Army in December 2025 under the Australian Defense Force DEF129 SUAS program for dismounted soldier operations. Delivery of advanced technologies “The Thermal by FLIR program represents a natural evolution of our commitment to delivering world-class sovereign defense capabilities globally," said Amanda Holt, CEO and Managing Director of SYPAQ Systems. "The Boson integration into our CorvoX platform exemplifies how strategic collaborations between Australia, the United Kingdom, and the United States (AUKUS) nations can accelerate the development and delivery of advanced technologies into the hands of the warfighters.” Modern reconnaissance and surveillance missions Developed specifically for dismounted soldier operations, CorvoX is configured with the Corvo Guarda 70-DN EO/IR payload, featuring a 640 x 512 resolution Boson, delivering world-pioneering thermal imaging performance, seeing through darkness, smoke, and most fog. The Boson is paired with an electro-optical (EO) sensor and resides within a two-axis mechanical system with advanced stabilization algorithms for geo-lock, object detection, and moving target tracking, essential for modern reconnaissance and surveillance missions. Thermal infrared technology “The CorvoX showcases the versatility and performance of our size, weight, and power (SWaP) optimized Boson thermal sensor in demanding uncrewed applications,” said Jared Faraudo, Vice President, Product Management, Teledyne FLIR OEM. “SYPAQ’s commitment to sovereign manufacturing and secure, high-volume supply chains aligns with our mission to enable innovative, market-pioneering thermal infrared technology worldwide.” Next-Generation CorvoX SUAS The CorvoX features an innovative thrust-vectored vertical takeoff and landing (VTOL) configuration that delivers class-leading endurance in extreme weather and up to 35 miles per hour (mph) (55 kilometers per hour (km/h)) of wind. Capable of speeds up to 62 mph (100 km/h), the lightweight, man-portable system weighs less than 4.4 pounds (2 kilograms), has a 32.3-inch (82-centimeter) wingspan, and can fly for up to 50 minutes. Designed for hand-thrown or ground VTOL takeoff, the CorvoX reduces the physical and cognitive load on operators. The system includes a novel memory structure that prevents sensitive intelligence from leaking during the mission, and the onboard artificial intelligence (AI) capabilities are updated constantly. See the CorvoX at Indo Pacific 2025 SYPAQ will showcase the CorvoX and Corvo Guarda 70-DN payload at Indo Pacific 2025 in Sydney, Australia, November 4-6, 2025. Visit SYPAQ at the Victorian Government Pavilion No. 3F92 to experience this next-generation capability firsthand.
Teledyne FLIR OEM, a Teledyne Technologies Incorporated company and the pioneer in enabling thermal imaging innovation, announced its latest Thermal by FLIR collaboration with Gremsy, a pioneer in professional unmanned aerial vehicle (UAV) payload and gimbal solutions. Through the collaboration, Gremsy is introduced its NDAA-compliant ORUS-L and Lynx payload lines, equipping drones with best-in-class aerial thermal intelligence. NDAA-compliant thermal camera module “Thermal by FLIR helps position Gremsy at the forefront of drone payloads with reliable NDAA-compliant thermal camera module availability,” said Jared Faraudo, vice president, product management, Teledyne FLIR OEM. “By integrating the size-weight-and-power (SWaP)-optimized long-wave infrared (LWIR) Boson+ camera module within the Gremsy spherical payload designs, the collaboration empowers demanding professional applications that require situational awareness day or night.” Teledyne FLIR OEM's thermal imaging technology The International Traffic in Arms Regulations (ITAR)-free and National Defense Authorization Act (NDAA)-compliant Boson+ thermal imaging camera module has recently been integrated into two new groundbreaking Gremsy products: Lynx, an ultra-compact ISR payload, and ORUS-L, a pioneering, sphere-shaped payload. These represent the introduction of an innovative product series. "Boosting innovation in uncrewed intelligence, our Lynx and Orus L payloads represent monumental achievements for our team while pushing new frontiers for our expanding spherical ecosystem," said Huy Pham, CTO of Gremsy. “The sphere form factor enables exceptional protection, aerodynamic efficiency, and a flexible platform for a wide range of critical applications. Our new payloads, enhanced by Teledyne FLIR OEM's thermal imaging technology, help users better achieve their mission objectives with unprecedented insight." LYNX NDAA: Ultra-compact ISR payload The ultra-lightweight and compact Lynx NDAA model is engineered for ultimate aerial efficiency, drastically reducing SWaP challenges on UAV platforms and translating directly into significantly longer operational times and enhanced platform versatility. Its dual thermal and visible imaging capabilities provide a critical advantage for time-sensitive public safety, drone-as-first-responder (DFR), and defense missions. Orus-L NDAA: Pioneering spherical payload with AI integration As the vanguard of Gremsy's spherical payload vision, the IP55-rated ORUS-L NDAA model supports flight speeds up to 100 km/h across vertical-takeoff-and-landing (VTOL) and fixed-wing platforms. Powered by the NVIDIA Jetson Orin NX, ORUS-L performs complex AI tasks including object detection, target lock, and autonomous tracking in real-time. Leveraging its built-in high-performance processor and Gremsy’s advanced image processing algorithm, this high-performance gimbaled solution includes an electro-optical (EO) camera, the radiometric Boson+ thermal camera module, and a laser range finder (LRF) ideal for critical inspection and public safety applications. Teledyne FLIR thermal camera modules Thermal by FLIR is a cooperative product development and marketing program that supports original equipment manufacturers (OEMs) and product innovators who use Teledyne FLIR thermal camera modules in their products. It allows integrators to get to market faster, enabling lower development costs and accelerating business growth via the world's largest volume manufacturer of ITAR-free IR sensors and modules: Teledyne FLIR OEM.
Sentrycs, a global pioneer in Protocol Manipulation-based counter-drone technology—commonly known as Cyber over RF, and Omnisys, a global expert in mission optimization for defense and homeland security, have announced a strategic collaboration that combines their technologies to improve the planning and deployment of sensor systems in multi-domain operations. The joint solution merges Sentrycs’ field-proven C-UAS systems with Omnisys’ BRO-AD (Battle Resource Optimization for Air Defense) platform, creating a powerful synergy that addresses the growing need for precision in sensor deployment. Maximum effectiveness Together, the technologies enable defense and security forces to account for operational constraints—such as terrain topography and electromagnetic interference—when determining optimal sensor layouts. By modeling various operational scenarios, BRO-AD helps decision-makers anticipate blind spots and optimize coverage. When integrated with Sentrycs’ counter-drone capabilities, this approach ensures that sensors are positioned where they will deliver maximum effectiveness, enhancing protection while reducing unnecessary deployment. For users in the field, the result is increased operational readiness, improved system performance, and better resource allocation. Shared commitment “This collaboration reflects a shared commitment to delivering operationally relevant solutions that meet today’s evolving security challenges,” said Meir Avidan, VP Business Development and Strategic Partnerships at Sentrycs. “Together with Omnisys, we are offering a smarter, more adaptive approach to systems’ deployments in real-world conditions.” Dov Pearl, Chief Business Officer at Omnisys, added: “By integrating BRO-AD’s powerful modeling capabilities with Sentrycs’ counter-drone systems, we’re helping customers plan and execute sensor deployments with greater accuracy, efficiency, and mission success.”
ZE Government Solutions (ZEGS), a wholly owned subsidiary of AI-based gun detection pioneer ZeroEyes, launched ZeroEyes Aerial Detection Kit (ZAD), a portable, drone-based AI threat detection and intelligent situational awareness solution designed for public safety agencies. The kit provides operators with a stand-alone drone solution that can be deployed in minutes from agencies' existing drone platforms to detect firearms, people, vehicles, drones, and maritime vessels. Rapid integration with drones Outdoor spaces are among the most challenging environments to protect due to their size and open nature, leaving them vulnerable to unauthorized access and potential gun-related violence. ZeroEyes Aerial Detection addresses this critical need with layered advanced AI analytics that detect threats in real time through a drone's live camera feed. To provide confidence and situational awareness, detections can be viewed instantly by law enforcement or security personnel and dispatched immediately to on-site staff when detections are made. Rapid integration with drones ensures that first responders or federal agencies are quickly informed of on-scene security threats, allowing for appropriate response posture to the current situation. ZeroEyes Aerial Detection Kit The kit enhances drone operations for a variety of scenarios, including drone response, event and perimeter security, armed assailants, suspect and article searches, barricaded gunmen, hostage situations, and domestic disputes. Providing immediate detections and alerting improves law enforcement situational awareness and personnel safety. ZeroEyes Aerial Detection Kit integrates seamlessly with existing drones and drone programs, and comes equipped with a carry-on case and a ZeroEyes laptop to stream video and deliver automated alerts to dispatch or operations centers via LTE, Wi-Fi, or mesh radio. It connects to drone feeds or controllers through HDMI, IP address, RTSP or Headsets, and is compliant with the National Defense Authorization Act and protected by DHS SAFETY Act designation. New drone solution “Protecting outdoor spaces is one of the greatest challenges in security today,” said Dustin Kisling, Executive Vice President of ZE Government Solutions. “With our new drone solution, we can detect potential threats in real time and provide verified alerts, giving organizations and the public the confidence that help is on the way when it matters most.”
Allient Inc., a designer and manufacturer of specialty Motion, Controls and Power products and solutions for targeted industries and applications, has announced it will present its electrification, precision motion and lightweighting technologies that are defining the next-generation of tactical systems at the Association of the United States Army (AUSA) Annual Meeting & Exposition on October 13-15 at the Walter E. Washington Convention Center in Washington, D.C. If they are attending, please visit the Booth #4243 or get in touch to arrange a meeting during the event. Allient's latest defense solutions At AUSA 2025, Allient will feature its latest defense solutions, including: UAS Propulsion Made in the USA You Can Count On - Allient’s frameless and slotless motors offer industry-pioneering torque density with zero cogging, ideal for agile and reliable UAV/UAS systems. Experience compact designs that enable smooth, precise flight control. Electrified Ground Mobility - Allient’s electrification expertise powers next-gen vehicles with silent electric drive systems that cut weight without sacrificing performance. Integrated Controller & Actuation Systems - From rugged motion control to sophisticated actuation, our Allient based systems deliver real-time, multi-axis coordination with high-bandwidth communication, built for mission-critical environments. Lightweighting Without Compromise - Allient delivers advanced ground vehicle solutions with lightweight composites and electrified drive systems, boosting performance and battlefield endurance. Gimbal & Camera Stabilization - Allient’s high-precision motors and drives deliver cogless, high-resolution motion for targeting, ISR platforms, and autonomous systems. How Allient is shaping the future of defense "Allient’s track record in defense applications continues to set us apart in the industry," said Steve Warzala, President of Allient Defense, Chief Growth Officer, and Corporate Vice President. “We look forward to showcasing our latest advancements and unique blend of technologies at AUSA, highlighting how Allient is shaping the future of defense for the Warfighter and beyond.” Latest advancements in defense technologies AUSA is North America’s premier land power exposition and professional development forum, bringing together military pioneers, government officials, and industry innovators from around the world. Organized by the Association of the United States Army (AUSA), the event highlights the latest advancements in defense technologies, military systems, robotics, ground vehicles, and mission-critical solutions supporting the U.S. Army and allied forces.


Expert commentary
The global maritime surveillance market is projected to grow from $21.9 billion in 2023 to $ 42.7 billion by 2033. This growth is being driven by increasing global trade, maritime security concerns, and the adoption of advanced surveillance technologies such as radars, drones, and satellite monitoring systems. Moreover, the global shipping industry is now on the frontlines of a new kind of conflict — one defined by economic coercion, shadow fleets, and contested logistics – a durable competition where adversaries seek control and influence over global supply chains. As tariff regimes expand and national security policies increasingly target commercial vessels, maritime operators are being forced to navigate a risk environment shaped more by geopolitics than wind and weather. Infrastructure of global trade Trade disruptions are no longer accidental by products of diplomacy — they are deliberate policy levers. Tariff escalation between the U.S. and China, sanctions on Russian oil, and Houthi attacks in the Red Sea are not isolated threats; they signal a new normal in which governments treat the shipping industry as a tactical asset. From China's military-civil fusion shipbuilding policies to LOGINK, its state-run maritime surveillance network, the very infrastructure of global trade is becoming entangled in nation-state agendas. Contested logistics: Struggle for global economic stability The current maritime threat landscape involving contested logistics contains strategic positioning The current maritime threat landscape involving contested logistics encompasses strategic positioning across critical chokepoints and infrastructure. The statistics are sobering: major shipping companies reported traffic through the Suez Canal dropped by 66% as of September 2024 due to Houthi attacks, with J.P. Morgan estimating shipping costs have surged significantly, particularly from Asia to Europe, nearly five-fold. Regional maritime security issues These developments illustrate how foundational industries, such as shipbuilding, semiconductors, and rare earth minerals, have become battlegrounds in a broader geopolitical struggle where a cascade of effects have the potential to destroy economies. For example, a military blockade of Taiwan — where Taiwan Semiconductor Manufacturing Corporation operates — would impact every company dependent on advanced semiconductors. This interconnectedness means that what may, on the surface, appear to be regional maritime security issues, can be much more — the potential for global economic disruption across multiple industries. Monitoring of Arctic fleet movements Shadow fleets operated by sanctioned states rely on tactics such as false flagging, frequent ownership changes New threat vectors are coming into focus as the seas expand. As the polar ice caps melt, new Arctic shipping lanes are opening, with a large portion of traffic driven by Russian vessels. These routes present unique surveillance challenges due to their remote nature and the limited presence of traditional maritime enforcement bodies. Monitoring of Arctic fleet movements and infrastructure developments is essential for maintaining security in this emerging corridor. Concerns about dual-use capabilities and strategic readiness Shadow fleets, illicit networks, and military-grade commercial vessels represent real risks, posing challenges in the areas of regulatory compliance, insurance viability, and operational safety. Shadow fleets operated by sanctioned states rely on tactics such as false flagging, frequent ownership changes, and manipulations of the Automatic Identification System (AIS). By turning off transponders, spoofing locations, or falsifying data, these vessels can effectively vanish from traditional tracking systems. This disappearance makes ships harder for authorities to trace and easier for adversaries to exploit for sanctions evasions and/or covert logistics. China's commercial fleets increasingly mirror military standards, raising concerns about dual-use capabilities and strategic readiness under the guise of trade. The need for a new risk framework To navigate this new threat landscape on the high seas, organizations must adopt a new kind of visibility For logistics and shipping pioneers, these implications are profound. This is no longer about simply avoiding sanctioned cargo — it's about forecasting how governments will act and how quickly those actions can alter operations. Vessels may be commandeered, sanctioned, or rerouted without warning. Insurance may evaporate. Contracts may become liabilities. To navigate this new threat landscape on the high seas, organizations must adopt a new kind of visibility — one that models the cascading effects of tariffs, military requisition policies, and enforcement shifts. This is where Open-Source Intelligence (OSINT) becomes indispensable. Real-time context on geopolitical risks OSINT draws from publicly available data -- including satellite imagery, port registries, and social media — to provide real-time context on geopolitical risks. It can be used to track vessel flagging and ownership changes, monitor transshipment hubs, and surface anomalies in crew rosters and employment histories — indicators often tied to sanctions evasion or illicit activity. AIS anomaly detection reveals when ships "go dark." Satellite imagery exposes vessels operating without transponders. Tracking shifts in vessels' flagging or changes in crew manifests can signal risk before it hits operations. Early indicators of disruption OSINT supports risk modeling by revealing trends like flag-of-convenience usage, secondary insurance For insurers and regulators, OSINT supports risk modeling by revealing trends such as flag-of-convenience usage, secondary insurance underwriting in high-risk zones, and affiliations with known bad actors. OSINT doesn't just enhance compliance — it enables foresight, empowering industry players to anticipate when and where governments will act. Now, tariff announcements, sanction designations, and strategic military exercises are not isolated datapoints — they're potentially early indicators of disruption. Maritime situational awareness is a business imperative The age of separating business risk from political risk is over. Global shipping is now a domain of contested logistics where the rules can change as fast as a sanctions update or new enforcement directive. Companies that integrate OSINT into their operational planning gain the ability to model and mitigate threats proactively. Those that don't may find themselves caught in the wake of potential financial, operational, and reputational harm. The shipping industry needs access to the same kind of threat modeling governments use to act. In an era of growing complexity, the role of OSINT in securing global shipping networks cannot be overstated.
As city managers, law enforcement agencies, and first responders face mounting pressure to combat crime and respond to emergencies with limited resources, real-time crime centers empowered by a new generation of data-driven technologies are emerging as an effective force multiplier. Real-time crime centers Real-time crime centers (RTCCs) serve as centralized hubs where dedicated personnel leverage pioneering-edge technologies to analyze diverse data streams and provide critical support to law enforcement and emergency operations. These 24/7 facilities are transforming how agencies gather, process, and act upon information, enabling more proactive and efficient policing strategies. The core functions of RTCCs These centers provide officers with unprecedented situational awareness and real-time intelligence At their core, RTCCs are tasked with three primary objectives: enhancing safety, facilitating identification, and supporting apprehension. By integrating data from a wide range of data sources, these centers provide officers with unprecedented situational awareness and real-time intelligence. Integrated data approach This integrated data approach allows RTCCs to alert officers to potential threats, quickly identify suspects, and guide responders during critical incidents. For instance, in the event of a robbery, RTCC operators can rapidly search camera and license plate data to track suspect vehicles, significantly improving the chances of a swift arrest. According to the Bureau of Justice Assistance at the U.S. Department of Justice, the mission of an RTCC is to centralize a broad range of current and evolving technologies, coordinate sworn and non-sworn human resources, and direct the attention to high-crime areas, active crimes in progress, high-profile or highly recidivistic offenders, and large-scale public events that may require law enforcement presence or response. The technology powering RTCCs The effectiveness of an RTCC hinges on its ability to seamlessly integrate a wide array of technologies: Open Platform Video Technology: At the heart of many crime centers is an open platform video management software (VMS) that serves as the central nervous system, unifying diverse data streams into a cohesive operational picture. By leveraging open APIs and SDKs, the VMS can incorporate a wide range of cameras, sensors, and analytics tools. This data-driven approach to video technology enables seamless alert distribution to both the RTCC and field officers via mobile applications. IP Camera Networks: The eyes of an RTCC, these systems combine fixed, PTZ, multi-sensor, thermal, and other specialty cameras to provide continuous city monitoring. Strategically placed throughout urban areas, cameras offer comprehensive coverage of critical locations such as transportation hubs, commercial districts, and high-crime zones. This network forms the foundation for real-time monitoring and incident response. Sensor Arrays: Beyond visual data, RTCCs employ various sensor technologies. Acoustic sensors can detect sounds such as gunshots, shouts for help, breaking glass, and other sounds instantly alerting officers and cueing nearby cameras. Environmental sensors monitor air quality for gasses, smoke, and other non-visible hazards. License Plate Recognition (LPR): LPR systems act as a force multiplier, continuously scanning for vehicles of interest. By generating real-time alerts for stolen or wanted vehicles, these systems significantly enhance the ability to track suspects and recover stolen property, contributing to reduced auto theft rates. Aerial Surveillance: Many RTCCs incorporate drone technology, providing on-demand aerial perspectives of developing situations. This capability is particularly valuable for monitoring large-scale events, assessing natural disasters, supporting operations in hard-to-reach areas, and serving as a powerful first response for crime scene situational awareness. AI-Powered Analytics: At the heart of many RTCC operations are sophisticated AI algorithms that analyze video data in real-time. These systems can identify a range of suspicious activities, from unattended packages to unauthorized intrusions. By rapidly processing vast amounts of video data, they help operators focus on potential threats and anomalies. Geospatial Mapping: To make sense of the influx of data, RTCCs rely on advanced mapping software. These tools visualize events, alerts, and data streams geographically, allowing operators to quickly identify patterns, clusters of activity, and relationships between incidents. Database Integration: RTCCs maintain direct connections to various law enforcement databases, including local, state, and federal resources like the National Crime Information Center (NCIC). This integration allows for rapid background checks and threat assessments, providing crucial context for ongoing operations. Cloud Infrastructure: The scalability and flexibility of cloud computing are revolutionizing RTCC capabilities. Cloud and hybrid solutions offer secure, off-site storage and facilitate easy data sharing between agencies. This approach not only reduces initial costs but also allows for incremental upgrades, making advanced RTCC functionality accessible even to agencies with limited budgets. Real-world impact RTCC operators tracked shooting suspects via camera feeds, guiding officers to their locationThe proliferation of RTCCs across the United States with over 80 centers in operation speaks to their proven effectiveness. Cities that have implemented these high-tech command centers are reporting significant improvements in response times, clearance rates, and overall public safety. Real-time surveillance In Winston-Salem, North Carolina, the local RTCC leverages over 1,300 live video feeds to provide real-time surveillance across the city. This extensive network, combined with gunshot detection technology and license plate readers, has already demonstrated its value. In a recent incident, RTCC operators were able to track shooting suspects via camera feeds, guiding officers to their location for a quick apprehension. Video analysis by RTCC Similarly, Newport News, Virginia, saw an immediate impact after launching its RTCC in 2021. The center has played a crucial role in solving homicides caught on video and rapidly closing a series of carjacking cases. These success stories underscore the game-changing potential of RTCCs when it comes to solving crimes and gathering evidence. In Memphis, Tennessee, video analysis by RTCC detectives helped identify a shooter in custody following an incident at a community basketball court even when no witnesses had come forward. Identifying suspects with RTCC Officers and analysts can view street and body camera footage to monitor crowds at parades The Jackson Police Department in Mississippi has seen similar benefits since building an RTCC in 2019, part of a broader effort that included deploying 100 cameras and 271 body cams. Officers and analysts can view street and body camera footage to monitor crowds at parades and other events. During pursuits, the cameras provide extra surveillance, allowing officers to identify suspects or witnesses to help solve crimes. Enhancing crime mitigation and emergency response While RTCCs have proven their worth in responding to active incidents, their true potential lies in proactive crime prevention and enhanced emergency preparedness. By leveraging advanced analytics and integrated data sources, RTCCs are evolving into powerful predictive tools for law enforcement. Pattern recognition algorithms For instance, pattern recognition algorithms can analyze historical crime data alongside real-time video feeds to identify potential hotspots for criminal activity. This allows law enforcement to strategically deploy resources, increasing visible presence in high-risk areas before crimes occur. Similarly, anomaly detection systems can alert RTCC operators to unusual behaviors or suspicious activities, enabling early intervention in potentially dangerous situations. Asset and property protection, automated alerts RTCCs can monitor critical infrastructure, government buildings, and other high-value assets 24/7 Asset and property protection is another area where RTCCs excel. By integrating with access control systems and using AI-powered video analytics, RTCCs can monitor critical infrastructure, government buildings, and other high-value assets 24/7. Automated alerts for perimeter breaches, unauthorized access attempts, or suspicious objects left in restricted areas allow for an immediate response, significantly enhancing security postures. Emergency response and preparedness In terms of emergency response and preparedness, RTCCs serve as vital command and coordination centers during crises. Whether facing natural disasters, major accidents, or other large-scale emergencies, RTCCs provide a centralized hub for information gathering and dissemination. Real-time video streams from affected areas, combined with data from environmental sensors and emergency service communications, allow for rapid situational assessment and coordinated response efforts. Post-incident investigation and analysis RTCCs can also play an active role in post-incident investigation and analysis. The ability to quickly compile and analyze vast amounts of data from multiple sources can significantly accelerate case resolution and help identify patterns to prevent future incidents. As RTCCs continue to evolve, their capacity for integrating diverse data streams and leveraging advanced analytics positions them as indispensable tools in modern law enforcement strategy. The future of technology-driven policing The integration of artificial intelligence and machine learning promises to enhance video analytics As RTCCs continue to evolve, they are likely to incorporate even more advanced technologies. The integration of artificial intelligence and machine learning promises to enhance video analytics capabilities, enabling faster and more accurate threat detection. Additionally, the expanding use of drones, subject to FAA regulations, could provide RTCCs with cost-effective aerial surveillance options. Effective and ethical operations However, the implementation of RTCCs is not without challenges. Agencies must navigate issues of privacy, data security, and community trust. Ongoing training for personnel and careful planning are essential to ensure these centers operate effectively and ethically. Data-driven approach Despite these hurdles, the trend toward technology-driven policing shows no signs of slowing. RTCCs represent a shift from reactive to proactive law enforcement strategies, offering a data-driven approach to crime prevention and response. As these centers become more prevalent, they will play an increasingly vital role in helping agencies maximize their resources and make informed decisions, ultimately contributing to safer communities for all.
There’s a new security paradigm emerging across malls, server farms, smart office buildings, and warehouses, and its advantage over the status quo are so broad they are impossible to ignore. Instead of a lecture, let’s start with a short narrative scenario to illustrate my point. Darryl's work Darryl works as a security guard at the Eastwood Mall. Like any typical evening, tonight’s shift begins at 9:30 PM, as the stores close and the crowds thin. His first task: Ensure that by 10 pm, all mall visitors have actually left and that all doors, windows, and docks are locked securely. As he walks through most major areas throughout the mall, he checks them off his list. All’s quiet, so after a 45-minute patrol, he stops for a quick coffee break before heading out again. He repeats the process throughout the night, happy to finish each round’s checklist and rest his feet for a few minutes. Challenge: Vandalism during the shift A few cameras located sporadically throughout the mall recorded two dark figures moving in and out of the shadows As usual, there’s nothing notable to report, he clocks out and heads home. The next morning, however, he's greeted by an angry mall manager. He learns that sometime during his shift, three stores were robbed and a back hallway vandalized. A few closed-circuit cameras located sporadically throughout the mall recorded two dark figures moving in and out of the shadows at about 4 am. The mall manager demands an explanation, and Daryl has none, “They must have been hiding during closing time and then waited for me to pass before acting,” he says. “I can only be in one place at one time. And if they were hiding in a dark hallway, I would never have seen them.” Theft explanation “Actually,” explains the manager, “we found a loading door ajar near the furniture store. We’re guessing that’s how they got in, but we can’t be sure. Do you check all the docks? We need to know if we need to replace a lock. Look at your logs - tell me exactly what you saw and when.” Daryl tries to recall. “I'm pretty sure I checked that one a couple of times. I checked it off my list.” Darrell decides not to mention that at 4:00 AM, he was feeling the night's fatigue and might have skipped that area a couple of times. That's the end of our tale. Poor Daryl is not a bad security guard, but he’s only human. His job is repetitive and unstimulating. Darryl's work log He checks off each location for the record, but there's no way for him to record the thousands of details Let’s discuss his hourly log. He checks off each location for the record, but there's no way for him to record the thousands of details he sees to later zoom in on the few observations that might be helpful for an investigation. He has walked by that loading dock door hundreds of times, and it's all a blur. This isn’t an unusual story; Darryl is doing the same job that humans have been doing in almost precisely the same way for millennia. And, like last night, the criminals have always found a way to avoid them. But there is a better way. Solution: Fully-automated indoor drone Replacing a human guard with a fully-automated indoor drone eliminates virtually all the problems we've identified in this story as it flies through the facility: Drone teams can work 24/7: While each drone needs to dock to recharge its battery periodically, a fleet working in concert can patrol around the clock in multiple areas simultaneously. This makes it much more difficult for an intruder to move freely, without risk of discovery. A drone can even keep an eye out and keep recording while docked. Drones see and log everything: Everything is recorded and stored in full detail as they compare what they see with what they expect to see High-resolution onboard cameras and ultrasensitive sensors can detect heat, movement, and moisture, and see into dark areas much more effectively than the human eye. As they aren't limited to the floor, they can also fly high in the air to look above obstacles and at high windows or warehouse shelves. And they don’t lose focus or get bored as the night drags on: Everything is recorded and stored in full detail as they compare what they see with what they expect to see based on a previous flight. Anything unusual triggers an alert. Drones don’t need vacations, snack/bathroom breaks, or new-recruit training: Without the need to deal with biological requirements, you aren't paying for non-work hours, and there’s no overtime for extra hours or holiday shifts. In a high-turnover business like security, there's no time spent training new employees; adding drones to your fleet simply means installing your existing procedures onto each. There is certainly room for judgment calls that require human intervention, but these can often be handled remotely using a control panel that provides all relevant data and alerts from the drones on duty. That means no scrambling to the office in the middle of the night for a false alarm. Drones outshine stationary cameras and the people staring at those screens: A guard in the security office staring at dozens of these screens usually loses their attention span throughout the shift Close-circuit cameras are expensive to install, maintain, and periodically replace. In addition, they are limited in their scope and, almost by definition, leave large blind spots. A guard in the security office staring at dozens of these screens (that generally show nothing notable) usually loses their attention span throughout the shift. Conclusion In short, there is a good reason that our industry is following close on the heels of the manufacturing industry, which has been eagerly adopting robotics as a more cost-effective and precise solution for years. It is simply becoming harder and harder to justify the expense of the traditionally error-prone and monotonous work that we ask of our security guards.
Security beat
With the year 2025 stretched out before us, there are many techniques one could use to predict what will happen in the new year. You might analyze historical data and analyze future trends. Or you could try statistical or economic modeling. Or you could develop multiple scenarios based on various assumptions to explore potential outcomes. Or you could just check your email. At this time of year, my email is full of industry folks looking to predict what the future holds in 2025. Ranging from artificial intelligence (AI) to privacy, the retail market to drones, here is a sampling of forecasts for 2025 provided by various players in the security market, courtesy of my email messages. What’s Ahead for AI? From Faisal Pandit, VP & GM, Global Security Products, Johnson Controls (JCI): “The future of security operations includes customizable, scalable solutions where users can control if, when, and how they use AI to improve efficiency depending on the size and function of their organization.” Says Kevin Woodworth, Vice President, Global Product Management, Intrusion, JCI: “Next year will see a growing focus from product developers on designing systems that streamline setup and configuration through increased AI integration. This reflects a broader trend of leveraging AI to simplify use and enhance adaptability as solutions evolve, rather simply employing it because it’s popular.” From Peter Evans, CEO of Xtract One Technologies: “AI algorithms will significantly advance in distinguishing between harmless, everyday items and potential threats. With this, we will see false alerts become even more rare.” Says JP Castellanos, Director of Threat Intelligence, Binary Defense: “Machine learning (ML)-powered anomaly detection will move beyond proof-of-concept to become mission-critical, enabling teams to uncover unknown threats and behavioral anomalies in real time – well before they escalate.” Evans of Xtract: “As AI becomes more advanced in threat detection, it will lead to more sophisticated protection of individual privacy. We can expect to see more AI techniques utilized for threat identification that do not capture personal data and are privacy-first.” Predictions on interoperability and compliance Woodworth of JCI: “New products added to singular systems must be interoperable. In 2025, organizations will need to embrace interoperability. AI will progress past reactive measures to achieve predictive capabilities.” Pandit of JCI: “With organizations increasing their focus on the regulatory environment, there will be an uptick in specialized certification programs to meet these needs. New security roles will emerge that will be focused on tracking and applying relevant regulatory changes.” Expanding capabilities for video cameras Woodworth of JCI: “Beyond capturing images, cameras will be able to detect potential threats and also mitigate them instantly, issuing vocal warnings, controlling access, or escalating issues without human intervention.” Looking ahead to retail developments Hansel Oh, Director of Product Marketing at Brivo: “Centralized, cloud-based security platforms will enhance credential management and monitor logistical operations to enable retailers to battle cargo theft.” Stephen Burd, Vice President, Essence Security: “With an increase in police response times, sophisticated crime, and smash and grabs, 2025 will see a huge demand for security solutions that go beyond simply notifying the police and will look to actively intervene and prevent damage or loss from occurring.” The role of drones and training Mary-Lou Smulders, CMO, Dedrone by Axon: “Drones will transition from being viewed as supplementary tools to becoming essential components of public safety operations. As departments recognize their effectiveness in various scenarios, the perception of drones will shift, and they will be integrated into core operational frameworks alongside traditional assets like patrol cars while replacing helicopters as a cost-effective and versatile alternative.” Erik Hohengasser, Electrical Technical Lead at NFPA: “As the skilled trades evolve, there will be an increasing demand for specialized and technical training. Predictive analytics, virtual simulations and hands-on experiential learning will become especially valuable due to allowing employees to gain real-world expertise in safe and controlled environments.”
Security applications for drones have evolved to provide benefits such as bird's-eye views of large areas, easy access to remote locations, and rapid deployment. However, to date, most drone applications have been outdoors. Not for long. Today, indoor drones are also finding unique opportunities for enhanced surveillance, security, and operational efficiency in indoor environments such as offices, warehouses, self-storage facilities, and malls. Indoor drones can navigate complex indoor spaces, providing real-time data and monitoring without the limitations of fixed cameras. New era of autonomous robotics A significant advantage of using drones indoors, as opposed to outdoors, is their ability to operate fully autonomously, circumventing U.S. Federal Aviation Administration (FAA) regulations that restrict such autonomy in outdoor environments. A new era of autonomous robotics enables drones to work seamlessly for users without the need for specialized flight training. A single security manager can oversee multiple indoor drones simultaneously with simple map clicks or prompts. A new era of autonomous robotics enables drones to work seamlessly for users Indoor monitoring and inspection Indoor Robotics is a company seeking to revolutionize indoor monitoring and inspection through its Control Bridge platform guiding indoor drones. Since its founding in 2018, Indoor Robotics has evolved through years of market engagement and product development. After initially recognizing a demand for autonomous indoor monitoring, the company found that existing hardware fell short. “However, we understood the challenges of full autonomy and knew we would solve it using drones,” says Bar Biton, Marketing Manager of Indoor Robotics. Indoor Robotics has evolved through years of market engagement and product development Hardware challenges Seven years later, with the hardware challenges addressed, the company is shifting focus to continually increasing value for security managers, especially with generative AI (artificial intelligence). In 2018, the problem was charging methods, which has been solved with ceiling docking stations and five patents. “Today it’s about making indoor environments safer and even saving lives by identifying blocked emergency exits, missing safety gear, leaks, fire hazards, and more,” says Biton. While indoor navigation presents challenges—such as the unreliability of GPS and the need for precision — Indoor Robotics has dedicated significant resources to achieve centimeter-level accuracy and ensure the utmost safety, maintaining a record of zero safety incidents to date, says Biton. Indoor navigation presents challenges—such as the unreliability of GPS and the need for precision Advanced AI-driven navigation systems Navigation challenges for indoor drones include maneuvering through confined spaces, avoiding obstacles, and maintaining stable flight in varied lighting conditions. To address these, Indoor Robotics employs advanced AI-driven navigation systems, real-time 3D mapping, and robust obstacle avoidance technologies. These solutions enable drones to adapt to dynamic environments, ensuring precise and safe navigation. Additionally, the Control Bridge platform provides real-time data and monitoring, allowing drones to adjust their routes and respond to changing conditions effectively, thus enhancing their operational reliability. Highly versatile indoor drones find applications across numerous vertical markets such as retail, logistics, healthcare, and corporate settings. Key use cases encompass security surveillance, where drones monitor premises continuously; maintenance checks, especially in hard-to-reach areas; safety inspections to comply with regulations and company policies; and emergency response to provide real-time data during incidents. In warehouses, drones efficiently inspect high shelves. Healthcare facilities and data centers use them to oversee restricted zones. Additionally, corporate offices employ drones to automate after-hours security, safety, and maintenance routines. Indoor Robotics employs advanced AI-driven navigation systems, real-time 3D mapping, and robust obstacle-avoidance technologies Alerts to the remote management team One Indoor Robotics client, a global tech company, deploys drones to enhance site surveillance and operational efficiency across six offices in three countries. The drones conduct regular security patrols after-hours, monitor facility activities, and ensure compliance with safety standards. This deployment has significantly improved the overall safety and security of their offices. The drones provide real-time alerts to the remote management team, enabling prompt responses to any anomalies, such as maintenance issues or unauthorized access. “The key advantage is the unified security standard provided by our Control Bridge operating system, allowing them to oversee all their sites from one centralized platform, ensuring consistent security management across all locations,” says Biton. When indoor drones co-exist with human workers, primary challenges include ensuring safety and preventing disruptions. Drones are equipped with advanced sensors and AI-driven obstacle avoidance systems to detect and navigate effectively around people. Strict operational protocols and designated flight paths are implemented to minimize interactions. Additionally, many drone operations are scheduled for after-hours to further reduce potential disruptions. “Safety is our top priority, and we invest significant resources to ensure it,” says Biton. “We are proud to report zero safety issues to date, reflecting our commitment to maintaining a secure environment for both drones and human workers.” Deploys drones to enhance site surveillance and operational efficiency across six offices in three countries Implementation of indoor drones Indoor drones are significantly more cost-effective and affordable when compared to traditional security methods like additional cameras, sensors, manpower, and even ground robots, says Biton. They cover larger areas and provide dynamic surveillance in less time, offering real-time data collection and enhanced flexibility. Unlike cameras or ground robots, drones eliminate blind spots and adapt to environmental changes autonomously. They also offer substantial indirect savings by optimizing maintenance routines, according to Indoor Robotics. For instance, a drone can instantly identify issues in hard-to-reach areas, allowing for immediate, targeted responses, instead of requiring an inspector first and then a technician, thus streamlining maintenance processes. “The biggest obstacle to greater implementation of indoor drones is education and awareness,” says Biton. “Many people are not yet exposed to the concept of autonomous indoor drones and may find it hard to believe they really work.” To overcome this, Indoor Robotics focuses on creating awareness and educating customers about the reliability and benefits of the technology. Demonstrations, case studies, and clear communication about the capabilities and safety of drones are key. By showcasing successful implementations and providing hands-on experiences, Indoor Robotics seeks to build trust and drive wider adoption of indoor drone technology in security applications. Control Bridge operating system Drones are designed with strict privacy controls and advanced AI to ensure they respect privacy norms A common misconception is that indoor drones are intrusive and pose significant privacy risks. However, drones are designed with strict privacy controls and advanced AI to ensure they respect privacy norms. They operate primarily during off-hours and are programmed to avoid sensitive areas, focusing solely on enhancing security and operational efficiency. The solution also includes rigorous data protection measures to safeguard any collected information, ensuring compliance with privacy regulations and addressing concerns effectively. Soon, automation will become integral to tasks across all facility types, from manufacturing and logistics to retail and office spaces. Using Indoor Robotics’ Control Bridge operating system, facility managers will deploy fleets of robots to identify issues, collect data, and gain insights to enhance operations, maintenance, and safety. Facilities will benefit from 24/7 AI-driven monitoring, eliminating the need for occasional surveys. Managers will receive immediate alerts for any anomalies, with preventive maintenance tasks seamlessly integrated into building management platforms, ensuring optimal performance and safety. New standards in the industry The Indoor Robotics platform-agnostic approach provides flexibility and scalability. “As we continue to evolve, we support more and more platforms, enabling our clients to tailor their indoor monitoring solutions to their specific needs,” says Biton. “We believe that the future of security lies in intelligent, automated systems that can adapt to dynamic environments and provide real-time insights,” says Biton. Indoor Robotics seeks to be at the forefront of this transformation, setting new standards in the industry and paving the way for a safer, more efficient future.
New buzzwords were abundant in the articles that generated the most clicks on our website in 2022. From the metaverse to the Internet of Things, from frictionless access control to artificial intelligence (AI), the topics most popular among our site’s visitors were at the cutting edge of change and innovation in the physical security marketplace. Here is a review of the Top 10 Articles of 2022, based on reader clicks, including links to the original content: Metaverse will promote collaboration and enable more efficiencies for security Metaverse is a familiar buzzword currently, but few people grasp what it means. In the simplest terms, the metaverse is an online “place” where physical, virtual, and augmented realities are shared. The term, Metaverse, suggests a more immersive online environment that combines elements of augmented reality (AR) and virtual reality (VR). For the physical security industry, the looming creation of a complex online environment offers possibilities and challenges. Establishing identity will be a central principle of the metaverse, and various biometrics are at the core of ensuring the identity of someone interacting in the virtual world. Cybersecurity elements are also key. On the benefits side, the security market is already taking advantage of technologies related to the eventual evolution of the metaverse. For example, the industry has deployed AR to provide information about a door lock’s status on a screen, headset, or smart glasses as a patrolling guard walks by. What are the security challenges of the transportation industry? Because transit agencies rely on several IoT devices, they get exposed to higher cybersecurity risks Rapid technological advancement, increasing urbanization, and the growing expectations of commuters and governments are pressuring transit industry players to modernize. Commuters, urban planners, first responders, and other stakeholders want to use transit data to support their decision-making. Transit agencies’ security and operations teams need closer collaboration to stay ahead. However, for many years, most transit agencies have relied on siloed, proprietary systems. Because transit agencies rely on an ever-growing number of Internet of Things (IoT) devices, they also get exposed to higher cybersecurity risks as there are more network access points to manage. The future is here: ADT’s innovation lab evaluating robots and indoor drones New robots and indoor drones for security applications are on the horizon, based on the work of ADT Commercials’ Innovation Lab, which is evaluating the latest technologies’ value to customers and some typical use cases. The ideal use of humanoid robots is to perform jobs that are considered repetitive, dirty, dangerous, and/or mundane. In security, that describes most security guard positions. As the name implies, autonomous indoor drones are focused on flying indoors versus the outdoor environment, which is heavily regulated by the U.S. Federal Aviation Administration (FAA). Flying autonomously indoors not only eliminates FAA oversight but also will enable ADT Commercial to offer another choice to customers to further reduce their dependencies on and costs of human guards. Innovative security: the key to business efficiency, cost savings, and more Organizations have shifted business focus countless times since the onset of the pandemic. While many leaders have been primarily concerned with the immediate health and safety of their customers and employees, 2022 has given rise to a new trend. More than ever, business leaders are seeking security solutions that increase operational efficiency and cost savings as well as improve logistics and business insight. As working environments become more complex, organizations looking to drive higher productivity and profitability margins should consider security upgrades that prioritize integrated analytics and automation. Shoplifting today is more sophisticated, and so are the tools to fight it One tool to fight shoplifting is analytics, which can be used to determine where shrink is occurring Shoplifting is often viewed as petty theft by individuals, but that is not always the case. Overall, shoplifting is becoming more sophisticated and coordinated. Traditional “shoplifting” has two major differences when compared to organized retail crime (ORC). The differences are numbers and motivation. ORC consists of groups working together to monetize theft, very different than an individual taking an item they need. One tool to fight to shoplift is analytics, which can be used to determine where shrink is occurring. Understanding where crimes take place helps retailers make strategic decisions about where to place their loss prevention efforts. Oosto offers 10 reasons to switch to frictionless access control in commercial buildings Access control for buildings is nothing new. It’s only in recent years that the urgency to implement smarter, more efficient, and more convenient forms of access control has increased, in the context of public and private sector digital transformation. Upheavals from the COVID-19 pandemic have forced organizations to re-think, pivot, and invest in new technology solutions that will incorporate Artificial Intelligence (AI) and Machine Learning, to gain speed in their operations, glean actionable insights from their video analytics, and enhance productivity with their teams. Which security trend is here to stay? Technologies and trends in the security marketplace come and go with some regularity. But how can you tell which trends are gaining traction and which amount to “the flavor of the month.” For example, while many physical security departments were hesitant to consider cloud-connected solutions in the past, they now better understand the benefits these solutions bring and how they can help them utilize their resources to achieve business goals while minimizing overall operational complexity. Other technologies mentioned in the article include mobile credentials, AI-based analytics, video management systems, cybersecurity, and a new emphasis on data. What do these technology trends have in common? They are opening new possibilities for greater system efficiency and functionality. In short, they are playing a role in transforming our industry. GSX 2022 reflects changing technologies and evolving role of security The role of the security director increasingly will encompass facets of cybersecurity and physical security GSX 2022 in Atlanta highlighted the changing role of security in the enterprise. The role of the security director increasingly will encompass facets of cybersecurity as well as physical security. Transitioning to an operation that incorporates both disciplines requires a workforce that embraces education and building new skills. Education and the opportunity to build new skills are evident everywhere at GSX, including in the hundreds of education sessions and also in the knowledge shared on the show floor in the exhibit hall. Consolidation changing the face of the security market Consolidation is a dominant trend in the security marketplace. Large companies typically swallow up smaller companies as a means of expanding both their technology portfolios and their geographic reach. Sometimes a big fish is swallowed up by an even bigger fish. Despite the pandemic and resulting economic challenges, the security market has continued to be a desirable environment for both big players and startups, which then provide abundant acquisition targets for larger companies. This article highlighted recent mergers and acquisition news. Six trends at the intersection of video and AI Video has evolved beyond the capabilities of advanced imaging and performance to include another level: Artificial Intelligence. Video imaging technology combines with AI, delivers a wealth of new data, not just for traditional physical security applications, but for a much deeper analysis of past, present, and even future events across the enterprise. This is more than a big development for the physical security industry; it is a monumental paradigm shift that is changing how security system models are envisioned, designed, and deployed. Much of the heightened demand for advanced video analytics is being driven by six prevalent industry trends.
Case studies
Located in the heart of California’s Central Valley, the Clovis Police Department serves the rapidly growing community of Clovis, California—a vibrant city situated just northeast of Fresno in Fresno County. Home to over 129,000 residents, Clovis is known for its strong community values, family-friendly neighborhoods, and forward-thinking city leadership. Once a historic railroad town, Clovis has transformed into a modern, thriving municipality, consistently ranked among California’s best places to live. Real-time public safety technology Clovis maintains a lean public safety model, with about 130 sworn officers and a total department staff Despite its growth, Clovis maintains a lean public safety model, with approximately 130 sworn officers and a total department staff of about 230 employees. The department takes pride in its reputation for innovation, responsiveness, and community trust, often operating with fewer resources than larger metropolitan areas—yet delivering highly efficient and effective policing services. As the city continues to expand—adding new residential developments, commercial centers, and educational infrastructure—the need for advanced, real-time public safety technology has never been greater. Commitment to innovation and collaboration Recognizing this, Clovis PD launched a bold initiative to build a Real Time Information Center (RTIC)—a centralized hub designed to unify data from hundreds of surveillance cameras, license plate readers, dispatch systems, drone feeds, and body-worn cameras. The department’s goal: enhance officer safety, accelerate response times, and support smarter decision-making across the entire public safety ecosystem. With a deep commitment to innovation and collaboration, the Clovis Police Department is setting the standard for what’s possible in modern law enforcement. The challenge For Clovis PD, the answer began with re-imagining how real-time data is gathered, visualized, and acted upon As technology rapidly reshapes the public safety landscape, Clovis PD faced a key question: How could a lean, high-performing department continue to meet the demands of a growing city while maintaining visibility, speed, and responsiveness across a diverse set of threats and situations? For Clovis PD, the answer began with re-imagining how real-time data is gathered, visualized, and acted upon. The department managed streams of mission-critical information from hundreds of surveillance cameras, LPRs, drones, dispatch systems, and body-worn cameras—but these assets were siloed and difficult to manage from a single point of control. Officers and dispatchers needed faster access to the right information at the right time, and leadership needed a way to centralize command operations without overwhelming staff or adding layers of complexity. Future of real-time collaboration What Clovis required was a unified platform that could make sense of multiple inputs, prioritize action, and scale as the city’s needs evolved. It had to be powerful, but also intuitive and accessible to analysts, officers, and supervisors alike. Most importantly, it needed to be built in a way that would support not just the workflows—but the future of real-time collaboration between departments, field units, city pioneers, and neighboring agencies. That vision became the foundation for Clovis PD’s Real Time Information Center (RTIC)—and set the stage for a successful deployment with RGB Spectrum and Wildfire Technology. The RGB Spectrum solution: Zio and XtendPoint in action At the heart of Clovis PD’s RTIC is RGB Spectrum’s Zio® AV-over-IP platform and XtendPoint™ KVM-over-IP system, providing the centralized control, flexible visualization, and easy expandability the department needed. Powering the visual backbone The Zio 4000 video wall processor seamlessly drives a 14’ × 5.6’ Barco TruePix 0.9 mm pixel pitch LED video wall, displaying live video from across the city, interactive maps, drone feeds, dispatch data, and analytic tools. With 16 HDMI inputs and 12 outputs, Zio acts as the visual brain of the RTIC—integrating diverse content streams into a single pane of glass for maximum awareness. Operators can quickly shift between presets for specific scenarios (e.g., drone deployment, vehicle pursuit, or major traffic events). Video streams are not only viewable in the RTIC but are routed to other locations, including Dispatch, the Emergency Operations Center (EOC), supervisor offices, and field units. Zio also supports future integration with remote web access portals—allowing city officials and council members to view situational data during major incidents. Control with confidence Clovis PD operators use RGB Spectrum’s XtendPoint KVM-over-IP to control and interact with up to eight systems Clovis PD operators use RGB Spectrum’s XtendPoint KVM-over-IP to control and interact with up to eight independent systems simultaneously using a single keyboard and mouse. Each operator station features two 43″ curved 4K displays, creating a panoramic, ergonomic environment that consolidates workflows and boosts productivity. “What sold me on RGB was how effortless it was for everyone to manipulate the screen and display what they needed—everyone had access, and it just worked,” Chief Fleming, Chief of Police, Clovis Police Department. This intuitive plug-and-play interface significantly reduces training time and enables officers, dispatchers, and analysts to work fluidly between tasks—whether monitoring cameras, controlling drones, running license plates, or launching live body cam feeds. Future-ready architecture: Built to expand RGB Spectrum’s IP-based architecture offers the flexibility Clovis PD needs to grow and adapt over time: Drone Expansion: As Clovis expands its DFR (Drone as First Responder) program with multiple Brink drone launch sites, the system will support direct drone video integration into the video wall and remote routing to field teams and fire personnel. Body-Worn Cameras: Using Axon’s new Respond technology, live body cam video is now accessible in real time—giving analysts and dispatchers critical visual data, especially when officers can’t communicate via radio. Mobile Command & Trailers: RGB Spectrum’s architecture enables future integration with mobile assets like camera trailers and portable operations centers, giving Clovis PD the tools to bring their RTIC capabilities to festivals, parades, emergencies, and other offsite events. “We’re not just solving for today’s challenges—we’re setting the foundation for tomorrow’s public safety technology,” said Chief Fleming. The human factor: Designed for everyday use From video wall presets to XtendPoint switching, every component was designed with the operator in mind Despite the complexity of the system’s backend, Clovis PD has found it remarkably easy to use. From video wall presets to XtendPoint switching, every component was designed with the operator in mind. Chief Fleming notes that even with staff rotating through dispatch or new to the RTIC, most users are up and running with minimal training. As the department continues to grow its analytics and drone teams, they’re confident in scaling the system further—without retraining or major technical overhauls. Inter-agency collaboration & City Council engagement The new RTIC isn’t just benefiting Clovis PD—it’s elevating collaboration with fire, EMS, and neighboring jurisdictions. Fire & EMS: Fire department command staff are integrated into the drone viewing platform, allowing them to view aerial video in real time from their phones or tablets. County-wide Visibility: Drone video and surveillance feeds are shareable with county partners via secure portals, enabling unified situational awareness across jurisdictions. City Council Access: The Zio platform can generate remote viewing links that allow City Council and department heads to access selected live data and camera feeds during major incidents or EOC activations—keeping decision-makers informed without disrupting operations. This capability has not only improved response times and safety but has also proven to be a valuable selling point for gaining city support. Community pioneers now have full visibility into how investments in public safety technology translate to real-world benefits. The role of Wildfire Technology: Seamless execution As the system integrator, Wildfire Technology delivered end-to-end project success. From vendor selection and budgeting to installation, training, and post-deployment support, Wildfire guided Clovis PD every step of the way. Created detailed project plans and electrical requirements Helped secure sole-source documentation to streamline approval Completed installation and commissioning in under 30 days Provided responsive support and firmware updates post-launch “Everything was clean, professional, and ahead of schedule. Their team cared about the space like it was their own. That kind of integrity is rare,” Chief Fleming. Forward-thinking technology deployment From integrated drone surveillance and mobile command capabilities to remote city leadership access Clovis PD’s RTIC is built not just for now—but for the evolving needs of tomorrow. From integrated drone surveillance and mobile command capabilities to remote city leadership access and future third-party analytics platforms, the department is thinking beyond traditional law enforcement. They’ve already begun planning to host open houses and agency tours, sharing their story to help others nationwide modernize their own public safety operations. “If something doesn’t work, we’ll say so. But RGB Spectrum’s real-time visualization system is absolutely working for us—and we rely on it every day,” Chief Fleming. Final thoughts The partnership between RGB Spectrum and Wildfire Technology helped Clovis PD bring its vision of a fully connected, mission-critical Real Time Information Center to life. The result is a scalable, ergonomic, and operator-friendly environment that strengthens officer safety, improves situational awareness, and increases the department’s ability to respond and adapt in real time. “This isn’t just about the tech—it’s about what the tech enables. And with RGB and Wildfire behind us, we’ve built something that’s going to serve Clovis for years to come,” Chief Fleming.
ZE Government Solutions (ZEGS), a wholly owned subsidiary of AI-based gun detection pioneer - ZeroEyes, announced that its new ZeroEyes Awareness Kit (ZAK), a drone featuring advanced built-in video analytics capabilities, which allows for real-time threat detection and early warning, was used to enhance security at Joint Base Charleston (JB-CHS)’s August 16 Summer Fest Concert. ZEGS rapidly deployed its computer vision software onboard an Easy Aerial tethered drone to augment security forces with overwatch capabilities, alerting the teams to any potential firearms or unauthorized personnel on the active flight line. Deployment of ZAK for real-time security Set-up took less than 30 minutes and provided JB-CHS and its defenders with an AI-enabled security platform Joint Base Charleston is a U.S. military installation in South Carolina that serves as a hub for various military operations, including airlift and airdrop operations, naval nuclear training, and logistics support. Its annual Summer Fest concert is sponsored by Air Force Entertainment. This announcement marks the first deployment of ZAK for real-time security in a real-world environment since its development as part of the Air Force Research Laboratory’s Small Business Innovation Research (SBIR) Program. Set-up took less than 30 minutes and provided JB-CHS and its defenders with an AI-enabled security platform to enhance operations for the on-base event. Extra layer of aircrew security ZAK provided overwatch for six continuous hours of flight time, protecting more than 1,000 base personnel and their families. While the operational test was for an in-garrison Morale, Welfare, and Recreational (MWR)-sponsored event, the capability is intended to provide roll-on/roll-off security for C-17 crews based out of JB-CHS. The capability easily transfers to downrange operations providing an extra layer of aircrew security in emergency situations and austere environments and incorporates Tactical Awareness Kit (TAK) plug-in capability. Drone threat detection system “This significant achievement was made possible through our collaboration with the Palmetto Spark Cell at JB-CHS, which played a crucial role in enabling the real-time use of ZAK during this live event, when security was paramount,” said Dustin Kisling, Executive Vice President for ZeroEyes Government Solutions. He adds, “Their support allowed us to tailor our tethered drone threat detection system to meet the most demanding security use cases for Air Mobility Command. By providing a platform for rigorous testing and iterative development, the Palmetto Spark Cell has been instrumental in advancing ZAK’s capabilities and ensuring its readiness for deployment in real-world scenarios.” The future of the Air Force Drone Program and AI July SECDEF memo specifically stated that 'small UAS are such critical force enablers that they must be prioritized' The July SECDEF memo specifically stated that 'small UAS are such critical force enablers that they must be prioritized at the same level as major weapons systems.' 'No later than September 1, 2025, the U.S. Army, the U.S. Navy, the U.S. Marine Corps and the U.S. Air Force will establish deliberately screened, active-duty experimental formations purpose-built to enable rapid scaling of small UAS across the Joint Force by 2026.' Use of small UAS platforms This expedited timeline laid out by the current administration has raised the urgency levels of the force looking to pursue and sustain drone programs. In anticipation of directives like this following the use of small UAS platforms in Ukraine, ZEGS recognized the need for enhanced operations using Artificial Intelligence to combat threats in combat zones and for use in home-station operations where safety of force is crucial. With the help of the SBIR program and the Palmetto Spark, ZEGS was able to add this capability to its portfolio of public safety and DoD solutions. Growing industry need for AI While necessary, the SECDEF drone directive only addresses one component of the issue While necessary, the SECDEF drone directive only addresses one component of the issue – the deployment of a large number of sensors does not necessarily correspond to an improvement in situational awareness, as it often results in a deluge of information being delivered to operators or analysts. This information overload can place a significant cognitive burden, distracting them from the mission at hand. JB-CHS recognized this and has partnered with ZEGS to deliver a unique force multiplier for their drone program through the use of AI and computer vision. ZEGS’ capabilities with drone operations ZEGS enables a streamlined approach to surveillance of threats, whether downrange with adversaries or protecting citizens against insider threats in-garrison during public events. The pre-emptive efforts to combine ZEGS’ capabilities with drone operations has put Joint Base Charleston, Air Mobility Command, and the US Air Force ahead of the curve and leading the pack for future operations.
Summer is here, and with it comes the height of music concerts and festival season. As thousands of music fans gather at venues worldwide, security professionals face increasing challenges in protecting these large-scale events. Milestone Systems, a globally renowned provider of open platform video management software (VMS), is helping security teams leverage integrated technology solutions to enhance safety and create seamless experiences for the thousands of fans attending these events. Comprehensive security via unified technology Securing large-scale public events like music festivals and concerts has become increasingly complex Securing large-scale public events such as music festivals and concerts has become increasingly complex amid evolving threats ranging from severe weather and crowd surges to targeted attacks. To meet these challenges, security professionals are adopting open-platform video management technologies that unify data from fixed cameras, drones, mobile devices, thermal sensors, and AI-driven analytics into a single, real-time operational interface. Flexible VMS platforms These advanced systems support coordinated decision-making between venue security, law enforcement, and emergency services, streamlining both response and prevention. Flexible VMS platforms are particularly valuable for overlaying event-specific venue maps, an essential feature when layouts change frequently for different events throughout festival season. Key technologies for event security Event security professionals are increasingly deploying integrated technology solutions to enhance safety at large gatherings: Video Management Software (VMS): Central platforms that integrate and manage multiple security technologies Thermal Cameras: Detect unauthorized fires, overheating equipment, and monitor crowd density Drone Surveillance: Provides aerial overwatch for large areas with real-time video feeds AI-Powered Analytics: Identifies unusual patterns, counts crowds, and detects potential threats Access Control Systems: Manages entry points with credential verification Mobile Command Centers: Specially equipped vehicles that serve as on-site security headquarters Real-world applications demonstrate value The Jelling Music Festival in Denmark exemplifies how effective video security enhances event safety. This year's festival, hosting nearly 40,000 attendees over four days, features 60 cameras throughout stages, entrances, and the campsite. All video feeds are monitored via Milestone's video management software on 65-inch smart screens in a specially equipped emergency command truck. Thermal cameras at the campsite offer advanced detection capabilities, enabling quick identification of unauthorized fires or barbecues. Open VMS technology Security teams are testing new abilities, including software that accurately counts attendees in specific areas The festival has grown from 1,000 spectators and 16 performances in 1989 to its current scale, thanks to open VMS technology that helps prevent overcrowding around the stages. Security teams are testing new capabilities, including software that accurately counts attendees in specific areas, providing critical data for crowd management and emergency response. Response times and overall crowd safety The synchronization of video, audio, and geospatial data across agencies creates a shared operating view that improves response times and overall crowd safety. Security professionals can implement thermal imaging, IR-enabled cameras, and drone surveillance to create more adaptive and resilient event security strategies.
Thames Valley Police worked with local authorities to improve CCTV coverage, cut costs, and boost efficiency. It’s made public spaces safer and ensured long-term, reliable monitoring across the region. Thames Valley Police is the largest non-metropolitan police force in England and Wales, covering 2,218 square miles and a population of 2.42 million people. Its jurisdiction includes multiple towns, city centers and council areas across the three counties of Berkshire, Buckinghamshire and Oxfordshire. Setting a long-term vision for public space CCTV Public space CCTV is vital in deterring and detecting crime across the Thames Valley Public space CCTV is vital in deterring and detecting crime across the Thames Valley. However, significant pressure on local authority budgets has made it increasingly difficult for councils to provide public space CCTV. There was real jeopardy that financial constraints would result in unmaintained systems, with limited or no real-time monitoring. A fresh approach was needed, so the Thames Valley CCTV partnership between Genetec™ and Hanwha Vision was formed. The first major challenge was securing funding to overhaul several local authorities’ aging systems, which were proving increasingly expensive to upgrade and maintain. The second was to manage the ongoing costs of staffing control rooms to ensure the long-term sustainability of monitored CCTV across the Thames Valley. Ownership and monitoring of public space CCTV Ambitious plans were devised to pool resources and replace many disparate systems with one police-owned system that could extend across multiple authorities. In effect, the aim was to transfer the ownership and monitoring of public space CCTV from local authorities to dedicated Thames Valley Police control rooms. It would be led by the Thames Valley Police & Crime Commissioner (PCC) Matthew Barber, collaborating with any local authority who chose to participate. It was a feat that had never been attempted in the UK on this scale that held the potential to drive efficiencies and enhance CCTV provision in areas it might otherwise have deteriorated. Ongoing commitment and investment “CCTV is an important part of community safety; benefitting police and local communities in helping to deter crime and antisocial behavior, identify offenders and support prosecutions." "Ongoing commitment and investment enables high quality, consistent and sustainable CCTV provision now and into the future”, explains Matthew Barber, PCC, Thames Valley. Centralization creates area-wide visibility and control Several control rooms in the Thames Valley, like Windsor & Maidenhead, had implemented Genetec Security Center Several control rooms in the Thames Valley, such as Windsor & Maidenhead, had already implemented Genetec Security Center and were very happy with its operation. Furthermore, as an open platform video management system, it could minimize costs by supporting a phased unification or “takeover” of existing systems across the Thames Valley. Finally, its hybrid cloud architecture provided Thames Valley with maximal flexibility to leverage any combination of cloud or on-premises infrastructure according to Name Thames Valley Police Industries Public Safety Location Thames Valley, United Kingdom Products Genetec Security Center; Genetec Cloud Services; Federation Technology Partners Hanwha Vision Channel Partners CDS Systems what made sense for each application and location. This made it the obvious choice on which to standardize. Range of multidirectional AI-enabled cameras Following a competitive tender, Thames Valley chose CDS Systems to implement its proposed solution. This would be built on Genetec Security Center and incorporate a range of multidirectional AI-enabled cameras from Hanwha Vision. A key driver in the decision was the high levels of commitment shown by all three parties to cybersecurity. Another was the recognition that the system design and technology selection could ensure a cost-effective implementation that could continue to evolve in line with the needs of its users. Integration between Genetec and Hanwha Vision technology Legacy cameras were retained and reused to maximize the return on existing investment wherever possible “We urgently needed to improve the quality of CCTV, enhance collaboration, and drive efficiencies for all partners. The respective capabilities and seamless integration between Genetec and Hanwha Vision technology was the optimal way of meeting Thames Valley’s requirements,” says Sam Thomas, CDS Systems. Phase one of the deployment involved CDS taking over an existing control room in Milton Keynes, replacing the legacy analog infrastructure with a modern IP backbone. It then installed Genetec Security Center to establish one platform through which officers could smartly interact with all incoming video feeds. Legacy cameras were retained and reused to maximize the return on existing investment wherever possible. A second Genetec workstation was also set up inside Slough Police Station, allowing officers to rapidly review footage for improved community response. Hanwha Vision’s AI-enabled multidirectional cameras CDS then introduced Hanwha Vision’s AI-enabled multidirectional 4k cameras to improve CCTV coverage and quality in public spaces. Each of these cameras incorporates up to five cameras in one device for wide-area surveillance, which would previously have required several separate devices, simplifying installation and resulting in significantly less associated cabling and infrastructure. They also provide powerful AI analytics, including accurate object detection and classification, to enable forensic search and save operators' time when responding to incidents. For example, identifying and establishing the movement of specific people or vehicles based on attributes such as vehicle type. Thames Valley CCTV partnership Phase two will see four additional control rooms in Oxfordshire merged into a single hub Phase two will see four additional control rooms in Oxfordshire merged into a single hub inside Abingdon Police station, also built on the Genetec Security Center. This and the control room in Milton Keynes will be interlinked, adding further resilience as each site will be able to act as a fallback for the other. At this point, there will be a dedicated team of eighteen staff responsible for monitoring CCTV and enhancing CCTV for all participating communities in the Thames Valley CCTV Partnership. Innovative and cost-effective solutions “The CCTV Command Suite enabled by CDS, Genetec, and Hanwha Vision has improved our workflows beyond recognition, enabling staff to quickly review and package evidence for frontline officers or more complex investigations. It has received several plaudits from officers for its ease of use,” says Jason Owen, CCTV Operations Manager, Thames Valley Police. “This collaboration between Thames Valley Police, Genetec, CDS Systems, and Hanwha Vision showcases the power of partnership in driving innovative, cost-effective solutions that improve public safety,” says John Boorman, Head of Product and Marketing at Hanwha Vision Europe. “Our AI-enabled cameras are designed to reduce false alarms and streamline operations, ensuring teams can focus on real incidents and drive efficiency across their monitoring.” Efficiency, at a lower cost All CCTV operators are civilian police staff vetted to the same clearance levels as sworn-in officers Pooling resources and transferring ownership to the police has brought about significant cost efficiencies for participating authorities, while also enhancing the quality and reliability of public spaces CCTV. Just as importantly, it has dramatically improved the police’s direct access to quality video evidence. Unlike in a traditional council-run control room, all CCTV operators are civilian police staff vetted to the same clearance levels as sworn-in officers. This means they have full access to Thames Valley’s suite of police databases and reporting software packages. They are better equipped to rapidly report incidents, support front-line officers, and communicate effectively with investigators as a result. On average, it handles between 300 – 500 incidents a month and has substantially increased the number of successful requests for supporting footage. “We’ve immediately seen the benefit of our investment in equipment and CCTV operators, with the police now much better equipped to deter and detect crime across the Thames Valley,” adds Barber. A solid platform for further improvements Control room operators’ intuition will always be the driving force that brings results Looking forward, Thames Valley has plans to use the Genetec platform to connect its people and mobile surveillance assets back to its control rooms for better cross-force interaction. Genetec Federation as a Service is already allowing live and recorded video to be shared with officers in the field. Soon it will also be extended to ensure video from police CCTV vans and drones is immediately available in the control room. In both cases, this is achieved without complex network configuration, requiring only an internet connection. It is also at the beginning of its journey of fully realizing the value of the AI-equipped Hanwha Vision cameras specified by CDS. Control room operators’ intuition will always be the driving force that brings results, but AI is freeing them up to do what they do best by saving time on routine monitoring and searches. Cost savings, resilience, and efficiencies Finally, talks continue that would see the addition of further control rooms across the Thames Valley to the Thames Valley CCTV Partnership. Having proven the model, would allow it to scale operations further to deliver even greater cost savings, resilience, and efficiencies. “We’re proud of what we’ve achieved to date but have no intention of resting on our laurels. The foundations we’ve established will ensure continued high-quality, consistent, and sustainable CCTV provision for our communities,” concludes Owen.
A damning new report shows theft from construction sites is surging nationwide, detrimentally affecting projects, firms and employees. Key findings Spike in cases: Two-thirds of respondents say the rate of theft increased in 2023, as the resale value of goods reached record levels. Criminals are getting smarter: one in three believe crime, including theft, physical violence, harassment and vandalism, is becoming more sophisticated. It comes as reports of criminals using drones to target sites become more frequent. A hidden productivity drain: A third of projects have been delayed due to crime, with copper and cable topping the tables as the most frequently targeted goods–delaying the development of critical infrastructure, such as railways. Workers bear the brunt of poor security: one in four workers have been left out of pocket, after having to replace stolen tools, and say being robbed is their “biggest fear.” However, security is seen as a “low priority” on sites they work on (30%). Underestimation of the risks BauWatch, examines the senses of building workers, to understand their incidents of theft at work The “Unseen Threats: 2024 Construction Crime Index,” from pioneering site-security provider, BauWatch, examines insights from construction workers, to understand their experience of theft at work. It suggests a “perfect storm” of factors, including goods inflation, increasingly sophisticated criminal tactics, and a general underestimation of the risks, are making sites vulnerable to crime, in turn causing major delays to projects, as well as denting staff morale. It also identifies the types of perpetrators that might pose a threat, including opportunists, professional gangs, and “insiders” (criminals posing as legitimate personnel), and outlines a list of best practice measures that can be immediately employed to minimize the risk of a robbery. BauWatch’s crime index We’ve observed that, since the Government removed the construction industry’s access to red diesel Rico Wojtulewicz, Head of Policy and Market Insight at the National Federation of Builders said: “We’ve observed that, since the Government removed the construction industry’s access to red diesel, fuel theft has risen, as indicated by responses in BauWatch’s crime index. CCTV has therefore become an even more important tool to help tackle site crime, not only because it acts as a deterrent and helps collect video evidence but as it also offers an insight into how and where a site might be better protected.” With criminals seemingly becoming more brazen, BauWatch, which supplies CCTV security to over 5000 active Construction sites across the UK and Europe, and the National Federation of Builders, are calling for firms to take extra preventative action against thieves, rather than taking a “wait and see” approach. Author's quote “Construction sites have always attracted thieves, but with the resale value of goods going through the roof, they’re now prime targets. So, it’s worrying to see that some workers don’t feel confident about on-site security,” said Alexis Potter, BauWatch’s Managing Director. Potter added: “Repeated incidents, even small ones, have huge repercussions if left unchecked as we can see in this report. The best way to minimize the impact of theft is to deter criminals from entering at all, so we are advocating for the adoption of preventative security measures to protect staff, safeguard investments and maintain project schedules.”
Artificial Intelligence Technology Solutions, Inc., a global pioneer in AI-driven security and productivity solutions along with its wholly owned subsidiary, Robotic Assistance Devices, Inc. (RAD), announced that it is in preparation to ship an order of 10 ROSA™ security devices to a major urban East Coast University. This multiple ROSA deployment will also see the implementation of RAD Light My Way™, providing the students and university staff with an additional layer of safety and security as they move about the campus. ROSA's cutting-edge AI ROSA units will also allow students and staff to instantly summon powerful deterrence This major deal marks a game-changer for campus safety, as the tech-savvy school aims to replace outdated call boxes with ROSA's cutting-edge AI and security capabilities. Equipped with RAD's innovative RAD Light My Way system, the ROSA units will also allow students and staff to instantly summon powerful deterrence and emergency assistance. Enhanced safety measures The CEO of AITX and RAD, Steve Reinharz, expressed that the deployment of RAD's security devices and solutions is an essential step in updating obsolete security measures. The robots will be positioned in busy areas on the campus, replacing old call boxes and enhancing the safety measures currently in place. AI-driven security solutions The university's decision to implement these AI-driven security solutions reflects the ongoing trend of using advanced technology to combat campus crime. According to findings published in June 2022 from the School Survey on Crime and Safety, postsecondary education campuses experienced a total of 27,300 crimes during the 2019-2020 period. Crimes reported Forcible sex offenses accounted for 43%, burglaries for 33%, and motor vehicle thefts for 11% The reported crimes amounted to approximately 19 incidents per 10,000 full-time students. Among these reported offenses, forcible sex offenses accounted for 43%, burglaries for 33%, and motor vehicle thefts for 11%. The Company confirmed that one of RAD’s largest dealers has received the purchase order from the university. The names of the university and dealers are expected to be announced in the future. RAD Light My Way “This marks another highly visible deployment of RAD Light My Way,” said Steve Reinharz, adding “The ROSA devices will be positioned in busy locations throughout the campus replacing obsolete and ineffective call boxes." He continues, "Like so many other colleges and universities, this school has experienced an increase in crime and a sharp decline of student confidence in the safety measures that are in place.” Easy-to-use devices “We welcomed a large contingent of the university’s administrative and security staff to the REX a few months ago,” said Mark Folmer, CPP, PSP, FSyI, President of RAD. He adds, “They were so impressed with RAD Light My Way and how easy it is to use. We are looking forward to having much of the school enrolled in RAD Light My Way soon. Collectively, we expect this and the deployment of the ROSAs to be welcomed throughout the campus.” Ship and deploy units The Company stated that all units are expected to be shipped and deployed within the next 2 weeks The Company stated that all units are expected to be shipped and deployed within the next 2 weeks. The Company anticipates receiving permission from its largest RAD Light My Way user, an East Coast regional hospital group, to be named and provide testimonials on its application and use shortly. ROSA AI-driven security analytics ROSA is a multiple award-winning, compact, self-contained, portable, security and communication solution that can be installed and activated in about 15 minutes. Like other RAD solutions, it only requires power as it includes all necessary communications hardware. ROSA’s AI-driven security analytics include human, firearm, and vehicle detection, license plate recognition, responsive digital signage and audio messaging, and complete integration with RAD’s software suite notification and autonomous response library. Two-way communication Two-way communication is optimized for cellular, including live video from ROSA’s dual high-resolution, full-color, always-on cameras. RAD has published three case studies detailing how ROSA has helped eliminate instances of theft, trespassing, and loitering at car rental locations and construction sites across the country. RAD Light My Way has been the recipient of two Secure Campus 2022 Awards from Campus Security & Life Safety Magazine. In October 2021 RAD Light My Way along with RAD's ROSA won CBRE’s 2021 Best Workplace Experience Solution Award. AI-driven Solutions-as-a-Service business model RAD solutions are specifically designed to provide cost savings to businesses of between 35%-80% AITX, through its subsidiary, Robotic Assistance Devices, Inc. (RAD), is redefining the $25 billion (US) security and guarding services industry through its broad lineup of innovative, AI-driven Solutions-as-a-Service business model. RAD solutions are specifically designed to provide cost savings to businesses of between 35%-80%, when compared to the industry’s existing and costly manned security guarding and monitoring model. Cost savings RAD delivers this tremendous cost savings via a suite of stationary and mobile robotic solutions that complement, and at times, directly replace the need for human personnel in environments better suited for machines. All RAD technologies, AI-based analytics, and software platforms are developed in-house. Sales opportunities RAD has a prospective sales pipeline of over 35 Fortune 500 companies and numerous other client opportunities. RAD expects to continue to attract new business as it converts its existing sales opportunities into deployed clients generating a recurring revenue stream. Each Fortune 500 client has the potential of making numerous reorders over time.


Round table discussion
The Metaverse sounds like the plot of the latest summer action movie. In reality, it’s a technology - or, more accurately, a group of technologies - that will likely have a transformational impact on a host of markets. For security, the Metaverse has an extensive list of needs. It also presents some opportunities. We asked this week’s Expert Panel Roundtable: What does the Metaverse mean for security?
Perimeter security is the first line of defense against intruders entering a business or premises. Traditionally associated with low-tech options such as fencing, the field of perimeter security has expanded in recent years and now encompasses a range of high-tech options. We asked this week’s Expert Panel Roundtable: What are the latest trends in perimeter security technology?
What is a business, or an industry, but a collection of people and the results of their work? People make all the difference in the destiny of a business or industry. And the people involved in a business reflect the impact of demographic changes – and the passage of time. The security industry has been largely built by Baby Boomers, who are getting older and increasingly stepping aside to make way for younger folks. We asked this week’s Expert Panel Roundtable: Is there a “new generation” of employees and managers entering the physical security marketplace, and what will be the impact?