Sylvain Gil

Sylvain Gil
Co-Founder and Vice President of Products, ExabeamSylvain Gil is the Co-Founder and VP of Products at Exabeam. Prior to this he worked at Imperva and Solsoft.
News mentions
Exabeam, the next-gen SIEM company, announced a new product that uses machine learning to spot compromised IoT and other devices. Exabeam Entity Analytics discovers the normal behavior of medical, ind...
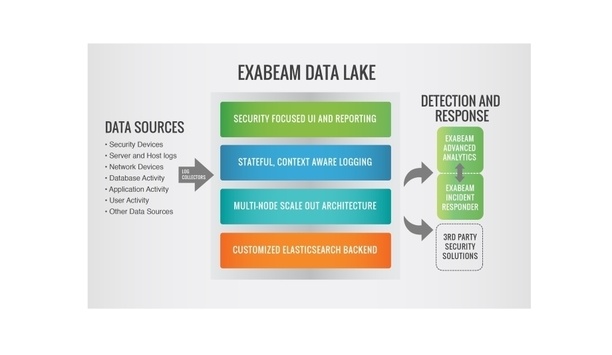
Exabeam, a developer of security intelligence solutions, has announced Exabeam Data Lake, a security data lake that enables organizations to easily store and access critical log data in the enterprise...