Jeff Nigriny

Jeff Nigriny
President and Founder, CertiPathJeff Nigriny is the President and Founder of CertiPath. Prior to joining CertiPath, he was the VP and CSO at Exostar. Jeff holds a BS degree in Information Systems from Virginia Tech and has also done MS in the same discipline from American University.
Articles by Jeff Nigriny
In the wake of 9/11, the Federal Government’s secure-the-fort, big idea was to create an identity credential for all federal employees and contractors. Homeland Security Presidential Directive (...
News mentions
IDEMIA Public Security North America, a pioneer in identity security and authentication services, and CertiPath, an innovator and pioneer in high-assurance identity, credential, and access management...
The Security Industry Association (SIA) has announced the agenda, speaker line-up and program for Part 3 of the 2021 SIA GovSummit, its annual public policy and government security technology con...
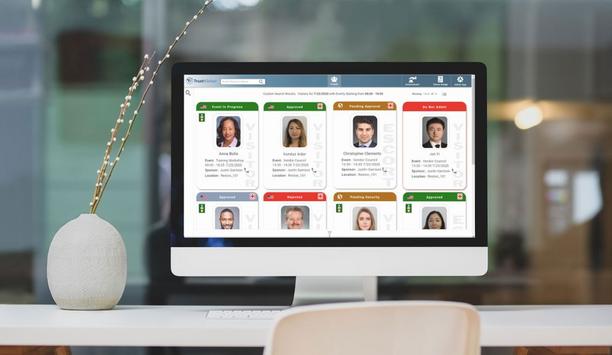
CertiPath, an innovator in high-assurance identity, credential and access management services for highly regulated environments, launches an advanced visitor management solution within its TrustVisito...
CertiPath, an innovator and renowned company in high-assurance identity, credential and access management services for highly regulated environments, has announced the appointment of industry veteran,...
NextgenID announces the immediate availability of products and solutions that meet the OMB Policy specified within the latest Executive release memorandum. “NextgenID continues to be a leader i...