United Kingdom (UK) News
Brivo, global innovator and designer of cloud-based physical security solutions for commercial buildings, announced its expansion into Europe with the opening of its Amsterdam office and the creation of a new subsidiary, Brivo Systems BV. The move highlights the increasing adoption of cloud-based physical security systems and the company’s growing partner and customer base in Europe. With sales, technical, and logistics operations located in Amsterdam, Brivo will now provide a full range o...
PerpetuityARC Training, part of Linx International Group, is proud to announce that associate trainer Paul Barker has been made a life member of ASIS International and life CPP. The accolade acknowledges Paul’s significant contribution to the international success of its Certified Protection Professional (CPP) qualification. In 1993 Paul became the third security professional in the UK to be awarded the CPP qualification, and two years later he was instrumental in expanding the course in...
Recife’s urban trains system carries around 400 thousand passengers a day – it is the third largest railway operator in number of users in Brazil. To ensure a safe journey for passengers, it is imperative to increase the subway security with modern technologies and monitoring equipment. The main challenge was to adapt the technology to the specific conditions such as lighting, people flow and speed of a subway station while not interrupting the transportation service. Therefore, eas...
I have been thinking a lot about the U.S. government’s ban on video surveillance technologies by Hikvision and Dahua. In general, I question the wisdom and logic of the ban and am frankly puzzled as to how it came to be. Allow me to elaborate. Chinese Camera Manufacturers Reality check: The government ban is based on concerns about the potential misuse of cameras, not actual misuse. Before the government ban, you occasionally heard about some government entities deciding not to use camer...
Governments and corporations face crisis events every day. An active shooter terrorizes a campus. A cyber extortionist holds a city for ransom. A hurricane washes away a key manufacturing facility. Not all critical events rise to the level of these catastrophic emergencies, but a late or inadequate response to even a minor incident can put people, operations and reputations at risk. Effective Response Plan In 2015, for example, the City of Boston experienced several record-breaking snowstorms...
Using a smart phone as an access control credential is an idea whose time has come – or has it? The flexible uses of smart phones are transforming our lives in multiple ways, and the devices are replacing everything from our alarm clocks to our wallets to our televisions. However, the transformation from using a card to using a mobile credential for access control is far from a no-brainer for many organizations, which obstacles to a fast or easy transition. We asked this week’s Exper...
In 1973, a brilliant economist named E.F. Schumacher wrote a seminal book titled ‘Small Is Beautiful:’ taking an opposing stance to the emergence of globalization and “bigger is better” industrialism. He described the advantages of smaller companies and smaller scales of production, highlighting the benefits of building our economies around the needs of communities, not corporations. In almost every industry or market that exists in the world today, you're like...
Repercussions are rippling through the physical security industry since President Trump signed into law the ban on government uses of surveillance equipment by Chinese manufacturers Hikvision and Dahua. In addition to the direct and indirect consequences of the new law, there have also been other developments likely to impact the future of Chinese companies in the video surveillance market. The ban has raised awareness of Chinese companies’ role in video surveillance, and other developme...
Iris ID, a provider of iris recognition technology, announces its iCAM 7S series enrolment process is now fully integrated with the latest version of the Symmetry Enterprise access control software from AMAG Technology. Symmetry Enterprise is designed for large organizations with complex security requirements. It supports unlimited card readers, cardholders and clients and allows users to control security from one location. The native integration of the iCAM enrolment process allows users to se...
ACRE, a global provider of integrated technology solutions and services, announced that ACRE, Vanderbilt and its subsidiaries, has entered into a strategic alliance with AlertEnterprise to expand and diversify technology options for customers. The AlertEnterprise suite of security convergence software, including its Physical Identity and Access Management (PIAM) solution, combined with the Vanderbilt Security Management Solution (SMS), will offer predictive analytics, compliance and advanced in...
Plasco ID, an integrator of identification solutions, announced it has been chosen as a trusted provider of HID FARGO Connect, the cloud-based card personalization and issuance solution by HID Global that untethers printers from dedicated computers and eliminates the need for locally installed ID management software or ID card printer drivers. Now, previously ‘isolated’ card printers are transformed into smart edge devices, bringing enhanced flexibility and productivity to end-user c...
There’s a lot of excitement around artificial intelligence (AI) today – and rightly so. AI is shifting the modern landscape of security and surveillance and dramatically changing the way users interact with their security systems. But with all the talk of AI’s potential, you might be wondering: what problems does AI help solve today? The Need For AI The fact is, today there are too many cameras and too much recorded video for security operators to keep pace with. On top of...
Newly modernized halls with lots of daylight will house hundreds of exhibitions and conference events at the upcoming Security Essen 2018 at Messe Essen, Germany. A new layout and hall numbering system will be unfamiliar to past attendees but promises to simplify the experience as it brings together attendees and exhibitors. European Physical Security Market Security Essen is an international trade fair, but the emphasis is more on German, Austrian and Swiss companies. In all, Security Essen w...
There are many aspects to consider when developing a retail security strategy, including loss prevention, physical security, asset protection, risk management, and IT. All these areas could be the responsibility of just a few people working to secure a handful of stores or each of these areas could be entirely separate departments, as is often the case for major retailers with locations throughout the country. Regardless of the size of the retailer, there are many different technologies that ca...
GSX 2018 is both a new event for the security industry and the continuation of a 63-year tradition. Global Security Exchange (GSX) is the new branding for ASIS International’s annual seminar and exhibits, which have been held since 1955. In recent years, the ASIS event has joined forces with other organizations to expand its scope and to appeal to a broader audience. Partners include ISSA (Information Systems Security Association) and Infragard, a public-private partnership between U.S. b...
Fidano, a software and business solutions provider for the payment processing industry, has successfully completed a rigorous fifth annual examination of its policies and procedures, under the System and Organization Controls (SOC) 1 Type 2 standards, demonstrating its ongoing commitment to data security at all levels of its operations. SOC 1 Type 2 standards examination The demanding third-party examinations that led to the achievement were administered by the professional IT assurance and co...
KnowBe4, a provider of security awareness training and simulated phishing, has completed a rigorous third-party audit of its data security procedures and processes under the System and Organization Controls 2 (SOC 2) Type 2 standards. KnowBe4 completed the SOC 2 Type 1 examination in April, and immediately initiated action to achieve a SOC 2 Type 2 status. The examination that led to compliance with the demanding SOC 2 Type 2 data security standards was administered by the professional IT compl...
Optex are preparing for a busy Security Essen show, where the sensor technologies company will demonstrate how the different detection technologies can improve security systems. Optex are showcasing new firmware for 2D Lidar scanners, with models now ranging from less than 20m to a 100m pre-warning zone, along with a new PIR to add to our outdoor intrusion range. For residential applications, they will be exhibiting the newly launched Shield PIR series that feature a volumetric 12m 90-degree m...
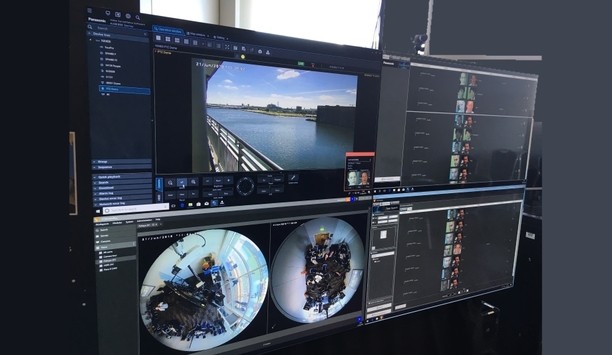
Panasonic, global provider of facial recognition solutions, will showcase its technology features in the Genetec stand (Hall 5, Booth #G30) at Security ESSEN 2018, the world’s most important trade fair for security in Germany. As a technology partner in the Genetec ecosystem, Panasonic will demonstrate the benefits of facial recognition with Genetec Security Center, engineered to benefit end-users with innovative solutions for security camera analytics. FacePRO Facial Recognition System F...
By now your organization should know the drill. To keep your enterprise safe from unauthorized access you take the basic precautions: create strong passwords that are not re-used and are updated frequently, use updated anti-virus software, employ host and network-based intrusion detection and prevention, data encryption, etc. etc. However, complacency has no place in cybersecurity. Hackers are working round-the-clock to outwit your most ardent security professionals. Here are a few specific vu...
Paxton, the global brand of electronic access control and video intercom solutions has appointed Jeff Pou as Training Engineer for the Southeast. Based in Georgia, Jeff will be responsible for training dealers in North Carolina, South Carolina, Tennessee, Georgia, Florida, Alabama, Mississippi, and Louisiana, ensuring they are aware of Paxton’s product offerings to support their current and future projects. Prior Experience At Apple & Microsoft Jeff joins Paxton with over 20 years o...
The physical security industry is embracing the cloud in a big way. Cloud-based systems – which involve accessing a shared pool of information technology resources via the Internet – are much higher-profile in the video and access control markets, and large and small companies are getting on the cloud bandwagon. We asked this week's Expert Panel Roundtable: What factors are contributing to growth in cloud systems in the security market?
Honeywell, a pioneer in Connected Buildings, announced its advanced smoke detection technology – capable of detecting and reporting smoke at its inception, before a fire develops – can now integrate with some of the most widely used fire panels in commercial buildings without the need for additional hardware or wiring. Combining Intelligent VESDA-E detection technology with NOTIFIER and Gamewell-FCI fire systems allows owners and operators to easily upgrade Connected Buildings to imp...
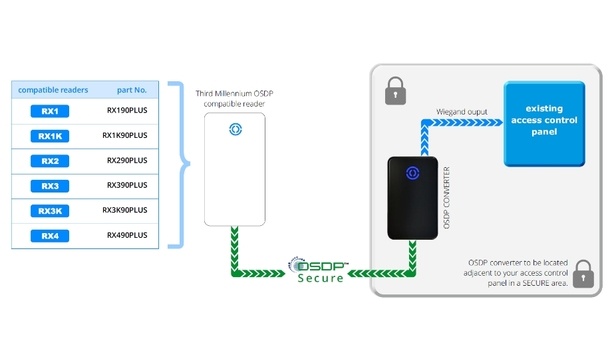
“AMAG welcomes Third Millennium to the Symmetry Preferred Partner Program and looks forward to a long, productive relationship," said Jason Schimpf, Vice President Product/Partner Programs, AMAG Technology. Third Millennium’s OSDP reader with OC1 converter can now be used with the Symmetry Access Control system. Cost-Effective Solution Legacy controllers can be upgraded to OSDP by just changing the reader and fitting an OC1. The OC1 takes the OSDP output from the Third Mill...
We are living in the age of Big Data, and businesses are inundated with large volumes of data every day. Success depends on capturing, analyzing and ultimately transforming that data into information and intelligence that can be used to improve the business. So, it is with today's physical access control and video systems, too, which also generate unprecedented levels of data. But how can we make the data useful to end users and how can they realize its full value? We asked this week's Expert Pa...
A video surveillance solution manufactured by Tyco, the security products division of Johnson Controls and installed by Kings Secure Technologies, is helping deter and detect hate crime directed at worshippers who attend the Gurdwara Singh Sabha in Bradford. HD Illustra IP Network Cameras 32 high definition Illustra IP network cameras from Tyco have been installed to monitor activity around the site of the Sikh place of worship, to identify anyone showing hostility towards the congregation. T...
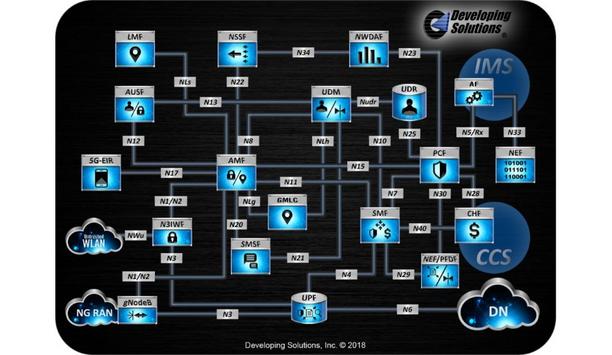
Developing Solutions, Inc. dsTest v5.1 is available to all current customers with active support agreements. It is available for downloading from the Developing Solutions secure support website. All features available in v5.0 are carried forward into v5.1. In addition to the continued support and development for 3G and 4G core network testing, dsTest v5.1 will include the initial releases of 5G core services for the N2, N8, N10, N13, N12, N11, and N4 reference points. Implementing automated te...
It has been an eventful few months for Arecont Vision, which has gone through Chapter 11 bankruptcy and, ultimately, was acquired by Costar Technologies Inc. What emerged is a new company, Arecont Vision Costar, poised for future growth unfettered by previous debt. For insights into what’s next for the newly minted company, we posed several questions to Jim Pritchett, CEO, Costar Technologies Inc., and Raul Calderon, President, Arecont Vision Costar. Q. Please relate how Costar came to...
When an active assailant strikes, it’s over fast, and most of the damage happens before help arrives. Responding appropriately can save lives, and it takes training and practice to know what to do as a tragedy unfolds: Where can I hide? Can I get out? Where do I run? If you hear shots or see someone with a knife, your training empowers the best response, and thorough and repetitive training avoids being paralyzed by panic. Standards On Workplace Violence ASIS International is a member of...
Facial recognition has a long history dating back to the 1800s. To track down criminals, such as infamous bandits Jesse Woodson James and Billy the Kid, law enforcement would place “Wanted Alive or Dead” posters advertising bounties and soliciting public cooperation to help locate and even apprehend the alleged criminals. In addition to the bounty, these posters would include a photo and brief description of the crime, which would then be circulated to law enforcement agencies arou...
Browse security news
Featured products
Related videos
Find Lost Wallet with Dahua WizSeek
Dahua Traffic Signal Controller Highlight
CLIQ Connect
The Key To Unlocking K12 School Safety Grants
DownloadHoneywell GARD USB Threat Report 2024
DownloadPhysical Access Control
DownloadThe 2024 State Of Physical Access Trend Report
DownloadThe Security Challenges Of Data Centers
Download- UK Security companies
- UK Manufacturers
- UK Distributors
- UK Resellers / Dealers / Reps
- UK Installers
- UK Consultants
- UK Systems integrators
- UK Events / Training / Services
- UK Manned guarding
- UK Training organisations
- UK Associations / regulatory bodies
- UK Event organisers
- UK Media
- UK Recruitment / personnel
- UK Services