Banking & Finance security applications - Expert commentary
A variety of control and usage options are available for automated key management systems in data centers The protection of networks and data centers is a growing concern given the recent spate of high profile security breaches, and it is forcing organizations into taking serious steps to improve protection. For many businesses, this means implementing a combination of passive and active security measures designed to deter, detect and react against threats. Included in these m...
RFI Enterprises has a Central Station Alarm Association (CSAA) Five-Diamond Monitoring Center RFI Enterprises started in a small town and has over the years grown to a large regional business. The company has developed innovative security solutions to fulfill customer’s requirements for a secure environment. It has managed to stay ahead of growing competition within the systems integrator sector and design solutions for customers ranging from aerospace, banking and healt...
Successful video infrastructure management requires visibility into the network’s behaviour The importance of video in an organization has been growing over the past several years, almost exponentially. In retail, video images can help detect or deter theft by employees and patrons. Casinos use video partly due to state regulations, to ensure gaming activity is free of deceit or fraud. Branch offices use video to communicate with the head office. Schools use video for di...
Any wireless device can be a soft target for hackers Security network hacking is one of the hottest topics today. The ability to access security systems or devices anywhere, leaves them vulnerable and prone to hacking. Any wireless device can be a soft target for hackers. Let’s start with the concept that nothing on a network is really secure. Let’s admit this to ourselves and take the next steps to make our security networks more secure. Internet of Things Securi...
Small-timers with big ideas can always make their way into the industry In recent years, home automation technology has given birth to the “Smart Home” in which internet-enabled and controlled devices are bringing a new level of comfort to the standard house. From locking doors to setting the temperature to opening the blinds for a view of the sunset, technology is transforming the home into something reminiscent of the now-quaint 1960s sci-fi cartoon, The Jetsons....
Voice biometrics is fast becoming a security imperative due to increasing instances of fraud and identity theft. From identifying customers at banks and call centers to securing mobile devices in a “bring your own device” world, the use of a person’s unique “voiceprint” is fast gaining ground as an identifier. The global voice biometrics market is expected to reach $4.7 billion (U.S.) by 2020. Much of it is being driven by the increasing need to...
The key driver to growth in the IP market is the effectiveness and efficiency of the technology Technological advances in video surveillance are allowing end users the flexibility to do more with their systems than previously imagined. 2014 saw several new technological trends that shaped the future of the security market, with 4K and cyber security being the main drivers. The drift continues this year too with end users demanding HD video surveillance and wide-spread impl...
Widespread use of smartphones and the loT have fuelled explosive demand for connectivity, convenience and control The growing Internet of Things (loT) or intelligent, inter-connected devices are causing a paradigm shift in nearly every technology sector, including the security installing industry. The global IoT market, according to research firm IDC, Framingham, Mass., is predicted to increase from 10.3 million “endpoints” in 2014 to more than 29.5 million in 2020...
National Union Fire Insurance Company claims that Tyco failed to protect confidential details of the warehouse security systems A civil trial against Tyco Integrated Security was adjourned by a federal judge on July 14 and is now rescheduled for October 19. The lawsuit arose out of the burglary of a pharmaceutical warehouse in Enfield, Conn., owned by Eli Lilly. Eli Lilly’s insurance company, National Union Fire Insurance Company claims that Tyco failed to protect confid...
Intimate body search at airports also takes a psychological toll on the person conducting the search SourceSecurity.com's European Correspondent, Jeremy Malies gives an account of the Body Search 2015 security conference that was held at Hounslow, London. Along with emphasis on aviation security, the conference also covered an array of safety and commercial applications. Some of the topics outlined in this article include: New techniques in body scanning, the exasperation publ...
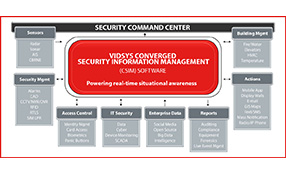
(see bigger image) The very nature of true enterprise PSIM software is that it has the capability to connect to other systems and subsystems In this article, James I. Chong, CEO & Founder of Vidsys, sheds light on true PSIM (Physical Security Information Management). He mentions how Vidsys is continually innovating and accelerating its roadmap for PSIM toward Converged Security and Information Management or CSIM. Citing various analysts’ projection, James s...
Private security professionals and law enforcement personnel are leveraging social media as a physical security tool to identify security threats and prevent crime. “Knowledge is power, and we’re all learning to cyber-sleuth to keep up with the bad guys,” says Wendy Patrick, JD, PhD, Deputy District Attorney, special operations division, San Diego District Attorney’s office and president of the Association of Threat Assessment Professionals San Diego...
Honeywell, Twitter integration brings security communication to its life safety products Honeywell, Northford, Conn., is leveraging the Twitter social media platform to bring higher levels of situational awareness and emergency communications to its life safety products. This move focuses to improve emergency response by monitoring various security, safety or building systems and providing information to identify potential threats. Gamewell-FCI’s Focal4 Now, Gamewe...
David Bleisch, ADT general counsel, addresses the media at a conference Door-to-door selling can be an effective tool to garner new security subscribers, and it’s been practiced for decades, according to Jay Hauhn, executive director of the Central Station Alarm Association (CSAA), Alexandria, Va. But it has to be done right, he says. A recent conference by ADT Security Services focused on deceptive alarm sales practices and the need to report such practices. In her late...
Monitronics’ ProShop offers sales and marketing materials to its dealer network as a valuable resource Monitronics Security, headquartered in Dallas, continues to stress the importance of professional monitoring services to its dealers and their customers as a critical component of recurring monthly revenue (RMR). “Traditional dealers need to emphasize the advantages of live, around-the-clock monitoring for anyone considering a non-traditional provider or do-it-yo...
This article by Keith Jernigan Sr., General Manager - MOBOTIX Corporation states the enormous impact of smart surveillance on various sectors. Highlighting the changing trends of video surveillance, Keith talks about the several benefits of IoT. He mentions that the new era will see video surveillance companies as more than just video security cameras sellers. To summarize, IoT is forecasted to conjure up businesses offerings, reduce costs and hazards, create jobs and opportunities, thus leading...
All seven decision factors contribute to an effective physical security solution Installation of an effective physical security solution can enable end users to avoid serious mistakes. This article presents a comprehensive and consultative decision methodology to help end users make the best decisions about security entrance products for the long term. The decision-making process is based on Boon Edam’s more than 100 years of experience in installing thousands of entry s...
Security-Net has grown significantly in stature as a global national accounts organization Back in the day, security companies kept their business close to the vest, didn’t collaborate and worked locally, without expanding beyond limited geographic boundaries. Security-Net™, Exton, Pa., came about in an effort to find a better way. So some 22 years ago, in 1993, the organization began a journey – one that would eventually establish it as a highly respected n...
Biometrics is most useful as an additional level of authentication — determining that you are who you say you are Over the years, the growth of biometric security technology has faced challenges of cost and pushback from users. Prices have been higher than more traditional technologies. In addition, users did not advocate storage of their personal biometric data by employers or the government. “I believe this is changing,” says Rueben Orr, CPP, vice preside...
Today, the once crime-ridden area of Los Angeles is a flourishing shopping and tourist mecca Los Angeles struggled with a rising crime rate. Constant crime plagued the historic area with its well-known tourist attractions, which include TCL Chinese Theater and the Walk of Fame. Criminal activity ranged from major to minor, from felonies to prostitution, public drunkenness, trespassing, vandalism, theft and on and on. Time and budget constraints had forced local police officer...
New notification appliances from Silent Knight provide code-required low-frequency output Just before the National Fire Protection Association’s (NFPA) World Safety Conference and Expo, June 22-25 in Chicago, Honeywell unveiled new solutions and features designed to boost life safety and provide more intuitive installations. S3 Series Control/Communicator A “virtual press conference” unveiling the announcements was kicked off by Beth Welch, manager of publi...
Suffering a breach is probably something that companies won’t admit to unless they must As the world has grown more and more interconnected through the Internet and company networks, cybercrime has grown at an alarming rate. According to the Federal Trade Commission, 783 businesses reported IT breaches in 2014, up 27.5 percent from 2013. “There were probably many more, but most go unreported,” says Kim Phan, of council with the Washington, D.C., law offices o...
Wi-Fi, real-time location tracking and security sensors are important elements of IoT solutions The tracking of people, processes and things continues to grow, and that’s good news for systems integrators, who can add these services to their arsenal of offerings and boost their levels of recurring monthly revenue (RMR). Real-Time Location Tracking Global Positioning Systems (GPS) and Radio Frequency Identification (RFID) are great ways to not only add security, but ope...
ESA opens the 2015 exhibit show floor with a ribbon cutting ceremony The Electronic Security Association (ESA) wrapped up ESX 2015, June 24 to 26 in Baltimore, Md., drawing integrators, manufacturers and association members from across the country to attend the annual educational, exhibits and networking event. Security Integration Companies Celebrating its eighth year, the show is jointly owned and sponsored by ESA and the Central Station Alarm Association (CSAA). ESX inclu...
Security beyond its traditional boundaries is a big theme at IFSEC 2015 The security landscape is changing. Touring exhibitors on the first day of IFSEC International in London, it seems an increasing number of vendors are offering products that go beyond what may be termed "security," offering solutions for applications such as health and safety and data collection. They are also offering more smart technology with mobile phones and tablets, and are selling smarter by tailori...
A retail banking tipping point is fast approaching with the state-side adoption of EMV technology Banking faces a challenge: to reconcile major security concerns with improving technology in order to reflect modern, mobile technology and the self-service solutions that customers have come to expect from their non-banking retail experiences. This is probably the number one issue I discuss with my bank clients. Banks need to make the technology in their branches more automated,...
The future will produce cost-effective solutions that can provide meaningful coverage of wide expansive areas The greatest trend in history will continue to change the world, and the physical security market. It’s called Moore’s Law. In accordance with Moore’s Law, our electronics have consistently doubled in speed, halved in size, or halved in price every two years for decades already. This trend means that our electronics, communications networks, data ne...
According IHS Technology, more than 11 million consumer and DIY network cameras will be shipped worldwide this year Perhaps we should start looking at do-it-yourself (DIY) systems such Google’s Nest and other devices as an opportunity for existing security contractors – those that are open-minded anyway – to bring in additional customers and new streams of recurring monthly revenue (RMR). DIY systems continue to proliferate in the marketplace and are availab...
Maricopa County installed a fully integrated security controls system, featuring a VMS Larger IP video systems require plenty of storage, and several high-profile applications help to demonstrate the value of storage in today’s networked video environment. Maricopa County Security Project One example is the Maricopa County (Ariz.) Sheriff’s Office, which is nationally recognized for its zero tolerance toward crime and unwavering focus on innovation in law enforce...
Daniel Budinoff, president of Security Specialists, Stamford, Conn., is almost a fixture at trade shows, especially ISC West. He attends some six to seven trade shows per year, but finds ISC West most applicable to his company, his product research needs and his networking endeavors. In fact, he has attended ISC West for more than 25 years, only missing perhaps one or two shows during that time period. With this year’s show just around the corner, April 10-12 in Las Vegas, it’s a gre...