Check Out Our Special Report On Casino Security
HID ActivID Credential Management System For Remote Monitoring
Technical Specification
- Make: HID
- Model code: ActivID Credential Management System
- Reader Types: Smart Card
- Central / Remote Monitoring: Yes
- Web-enabled software: Yes
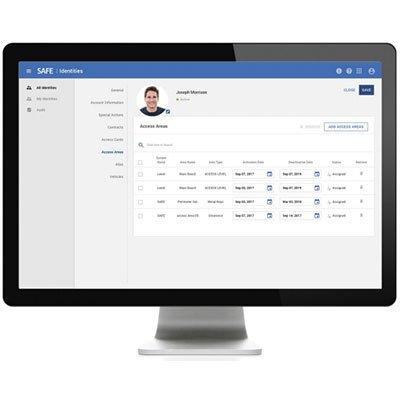
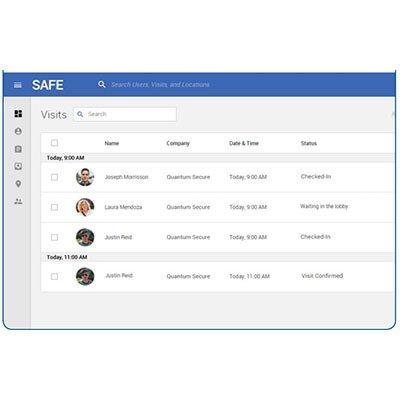
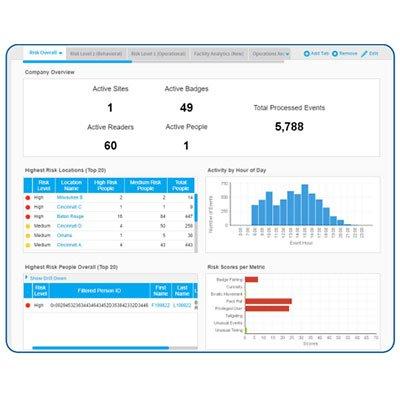
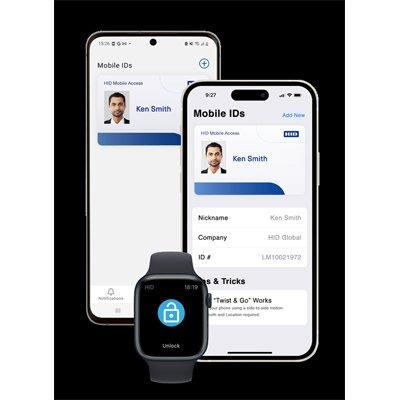
The HID ActivID Credential Management System enables organisations to issue an authentication credential that goes beyond perimeter security. A smart card or smart token can be used to secure access to individual workstations and servers within the firewall, as well as securing VPN and other remote access use cases. The smart card or token can also be used to encrypt data, hard drives, documents and emails, and for digital signatures. It gives organizations a way to simply and securely manage their smart card and smart USB token deployments. The credential management solution makes it easy to define and apply policies to manage data, applets, digital certificates and OTP credentials across the entire product lifecycle.
Read more| Make | HID |
|---|---|
| Manufacturer | HID |
| Category | Access Control>Access control software |
| Model code | ActivID Credential Management System |
| Reader Types | Smart Card |
| Central / Remote Monitoring | Yes |
| Web-enabled software | Yes |
| Additional info | The HID ActivID Credential Management System enables organisations to issue an authentication credential that goes beyond perimeter security. A smart card or smart token can be used to secure access to individual workstations and servers within the firewall, as well as securing VPN and other remote access use cases. The smart card or token can also be used to encrypt data, hard drives, documents and emails, and for digital signatures. It gives organizations a way to simply and securely manage their smart card and smart USB token deployments. The credential management solution makes it easy to define and apply policies to manage data, applets, digital certificates and OTP credentials across the entire product lifecycle. |
More HID Access control software
You might be interested in these products
- See other HID products
- HID Access control readers
- HID Access control cards/ tags/ fobs
- HID Access control controllers
Related Whitepapers
The Truth Behind 9 Mobile Access Myths
6 Good Reasons To Embrace Mobile Credentialing
Three Essential Reasons To Upgrade Your Access Control Technology In 2022