Visitor management systems
Verkada, a pioneer in AI-powered physical security technology, announced CapitalG is pioneering an investment at a $5.8 billion valuation - an increase of $1.3 billion since the announcement of its Series E in February. The investment will accelerate Verkada's AI capabilities and may also enable liquidity for employees, and comes as the company surpasses $1 billion in annualized bookings. AI-powered transformation "AI is fundamentally transforming how organizations protect people and places,...
Third Millennium, a provider of access control solutions and part of HID, announces the launch of new RXQR and RXQRK readers — multi-technology access-control devices that integrate high-security RFID card and QR code credentials into a single, elegant unit. Designed to simplify visitor and contractor management, and support both legacy and modern communication protocols, the RXQR range is part of Third Millennium’s RX Series, delivering an advanced yet cost-effective solution for t...
ZKTeco USA, a major provider of biometric verification and access control technology, announced the company will be highlighting its full portfolio of access control solutions ranging from its multi-tech standalone readers, metal detectors, optical turnstiles, Torus key cabinets, visitor management, and new scalable cloud-based access control software - Cielo365 at GSX 2025 (booth #3047) in New Orleans September 29th – October 1st. The company’s newly released cloud-base...
Property managers and residents face mounting challenges in multi-site security management, remote access control, communication gaps, and balancing modern convenience with budget constraints. Cloud-based solutions are revolutionizing how residential properties address these universal pain points. Sarah’s phone buzzed at 2 AM. As the property manager for three residential complexes across different cities, she’d grown accustomed to late-night emergencies. This time, it was a locked-...
Athena Security, a pioneer in AI-driven physical security solutions, has announced the launch of its new Hospital Visitor Management System (VMS) on the Apple iPad. Purpose-built to meet the critical needs of healthcare facilities. Athena’s Hospital VMS is the first Apple iPad solution in the industry to offer seamless offline capabilities—ensuring that hospitals stay operational and secure, even amidst internet interruptions due to down servers, power outages, or natural disasters....
Brivo, the pioneer in cloud-native unified physical security, announced a strategic partnership with Envoy. The integration brings Envoy’s workplace platform, designed to connect people, spaces, and data, into Brivo Security Suite. Together, Brivo Visitor Management powered by Envoy merges workplace experience with physical security, eliminating silos and enabling a modern, secure sign-in process that scales from single offices to Fortune 500 enterprises. Front-desk security Best-o...
News
Verkada, a pioneer in AI-powered physical security technology, announced it has achieved Federal Risk and Authorization Management Program (FedRAMP) ‘In Process’ designation for Verkada Command in AWS GovCloud. Together with Verkada’s federal agency sponsor, accredited Third-Party Assessment Organization (3PAO) Fortreum will conduct a detailed security assessment in the second half of 2025. As federal agencies and their partners look to replace outdated, siloed systems and address increasingly complex threats to public servants, government assets, and critical infrastructure, Verkada’s government-grade offering provides a cloud-based solution that leverages its latest advances in computer vision and AI while also adhering to regulatory standards and mandates. AI-powered solutions “Verkada has transformed the ways that more than 33,000 organizations today keep their people and places safe with our cloud-based platform and AI-powered solutions,” said Jon Andersen, Federal Chief Information Security Officer at Verkada. “We are eager to make this same impact in the federal government, and achieving FedRAMP ‘In Process’ is an important milestone in ensuring that Verkada’s secure, reliable, and compliant solutions are accessible to them.” Verkada’s FedRAMP In Process designation currently applies to the Command Platform hosted in AWS GovCloud, which includes: FIPS 140 Validated Cameras (Video Security) Verkada Guest (Visitor Management) FIPS 140 Validated Sensors (Air Quality) FIPS 140 Validated Command Connector Verkada Gateway (Cellular Networking) Verkada’s government-grade solutions are already listed on the FedRAMP marketplace and accessible through major government procurement channels, including GSA Schedule, NASA SEWP V, ITES-SW2, Carahsoft, and many existing partner vehicles.
The Partner Alliance for Safer Schools (PASS) has released the seventh edition of its Safety and Security Guidelines for K-12 Schools, which offers the most comprehensive information available on nationwide practices specifically for securing school facilities, from subject matter experts across the education, public safety, and industry sectors. The seventh-edition release – including updates to the Safety and Security Guidelines and the School Safety and Security Checklist – improves on previous versions of the PASS guidance to make it more comprehensive, easier to use, and more reflective of K-12 schools’ evolving security needs and challenges. PASS school security The PASS school security and safety guidelines provide school administrators, school boards, and public safety and security professionals with a road map for implementing a layered and tiered approach to enhancing the safety of school environments and a tool to prioritize needs. Provided free of charge, the guidelines have been downloaded by thousands of stakeholders and leveraged in many districts to evaluate and improve security infrastructure and procedures. New to the seventh-edition guidelines are the following features: Introduction of a new Digital Infrastructure Layer: This new layer recognizes the importance of cybersecurity and attentive management of digital systems and data. The addition of this layer takes a converged approach to security, dramatically expanding PASS beyond what was primarily a domain of physical security. Unification of the Property Perimeter and Parking Lot Layers into the new Campus Perimeter Layer: PASS’s many volunteer school security experts recognized that these layers are commonly approached from a unified safety standpoint. Detailed guidance on visitor entry: In addition to traffic-flow diagrams and example floor plans, this edition also extensively covers aspects like visitor management processes. Greater content on physical hardening: From topics like door construction to security film and window glazings to reinforcement of classroom walls, the seventh-edition guidelines add greater depth of content than before on aspects of physical hardening. Expanded information on panic alarm systems: As panic alarm systems have continued to prove valuable in school emergency situations, the newest edition increases guidance on this important solution. In-depth coverage of door locks and door devices: Properly locking doors is an essential component within a school, and this version covers the complexities of school-specific lock requirements with great nuance. And more! PASS Guidelines “I’m so proud of our technical committee and the effort that went into the seventh-edition PASS Guidelines – more than a year of discussion and seeking input from school officials went into this revision,” said Chuck Wilson, chair of the PASS Board of Directors. "Integrated security and life safety solutions, combined with cloud and power over Ethernet and wireless technologies, created the need for an entirely new layer titled digital infrastructure.” “Version 7 embraces the emerging technologies while maintaining our fundamental belief that the basic and foundational methods and solutions are necessary. This is our best work yet. The updated guideline and checklist can flow directly into the threat assessment and the school district’s comprehensive safety plan.” School safety topics Since 2020, the PASS guidelines have been included on SchoolSafety.gov Since 2020, the PASS guidelines have been included on SchoolSafety.gov, the federal government’s clearinghouse for best practice information across a range of school safety topics, and in 2019, PASS was recognized by the Federal Commission on School Safety as well as in other state commissions and reports. The guidelines describe approaches within five physical layers for school facilities: districtwide, digital infrastructure, the campus perimeter, the building perimeter and the classroom/interior. Within each layer, the resource outlines key safety and security components, such as policies and procedures, people (roles and training), architectural components, communication, access control, video surveillance and detection and alarms. Latest guidelines These guidelines are designed to provide stakeholders with specific actions that can effectively raise the baseline of security, vetted security practices specific to K-12 environments, objective and reliable information on available safety and security technology, multiple options for addressing security needs, and the ability to distinguish needed and effective solutions from sales pitches or unnecessary products. The latest guidelines are available at no cost on the PASS website along with a matching checklist tool, and PASS encourages education professionals, public safety personnel, and security solutions providers to take advantage of these free resources.
Emergency24, a pioneer in third-party central station alarm monitoring, is proud to announce a groundbreaking partnership with Intrado Life & Safety, Inc. (Intrado), a global pioneer in emergency communications. Emergency24 now integrates with Intrado’s Emergency Data Broker alarm solution, digitally connecting alarm events directly to more than 600 911 centers across the United States. Strategic collaboration This strategic collaboration marks a significant leap forward in emergency response efficiency This strategic collaboration marks a significant leap forward in emergency response efficiency. By leveraging Intrado’s Emergency Data Broker platform, Emergency24 can now transmit alarm data to public safety answering points (PSAPs) in as little as 15 to 30 seconds - a dramatic improvement over the industry’s average 2.5-minute dispatch time via traditional phone calls. This digital dispatch process not only expedites emergency response but also reduces the potential for errors caused by miscommunication during voice calls. Words from Emergency24 Vice President “Emergency24 has always led the way in dispatch response times, and our partnership with Intrado takes that commitment to the next level,” said Steve Mayer, Vice President at Emergency24. “This is a win for subscribers, alarm companies, 911 centers, and first responders. The faster we can verify and transmit critical alarm data, the faster first responders can act-and that’s better for everyone involved.” Rollout in Seminole County, Florida Emergency24 will continue to expand digital dispatch coverage throughout 2025 The rollout began in Seminole County, Florida, and is expanding this month to Waukesha County, Wisconsin, and the Cook County Sheriff's jurisdiction in Illinois. Emergency24 will continue to expand digital dispatch coverage throughout 2025, bringing the benefits of Intrado’s EDB solution to additional jurisdictions nationwide. Investment in advanced digital dispatch strategies This partnership underscores Emergency24’s ongoing investment in advanced digital dispatch strategies, further enhancing its reputation as an industry innovator. The integration with Intrado’s EDB platform builds on Emergency24’s tradition of technological leadership and positions the company- and its alarm dealer partners- at the forefront of next-generation emergency response.
Secutech 2025 is set to showcase a comprehensive array of cutting-edge solutions from 7 – 9 May at the Taipei Nangang Exhibition Center. This one-stop platform for smart technology and business will cover 15,120 sqm and feature approximately 400 exhibitors from eight countries and regions. Sourcing and business connections Edition is expected to attract visitors, including system integrators, manufacturers, and distributors With a fringe program of over 140 seminars and 14 trend-focused zones and pavilions, this edition is expected to attract visitors, including system integrators, manufacturers, distributors, and exporters, fostering collaboration across various industries. The show will be held concurrently with Fire & Safety and Smart Building, further facilitating cross-sector sourcing and business connections. Next generation of smart security solutions “This edition’s growth reflects rising demand for new products and services to solve unique security issues across industries,” said Ms Regina Tsai, General Manager of Messe Frankfurt (HK) Ltd – Taiwan Branch. “The next generation of smart security solutions must meet new requirements, evolving with societies’ advancements. Secutech serves as a premier platform for industry leaders worldwide to explore a wide range of innovations while connecting with key stakeholders. Our extensive global reach ensures that businesses can thrive by gaining valuable insights into market trends, product features, and competitive landscapes.” Integrated solutions The fair will offer advanced, integrated solutions tailored to the needs of various vertical sectors Exhibitors from Australia, China, Japan, Korea, Singapore, Spain, Taiwan, and the US will be present. The fair will offer advanced, integrated solutions tailored to the needs of various vertical sectors, specifically smart building, construction, fire safety, mobility, healthcare, environment, logistics, warehouse management, and more. This edition will highlight the participation of “MIT Plus” (Made in Taiwan) exhibitors, including products that comply with the National Defense Authorization Act (NATT). Latest advancements in smart security technologies Pioneering Taiwanese companies like Merit Li-Lin, Vivotek, FUHO TECHNOLOGY, and KCA will exhibit alongside notable global brands such as Panasonic, WD, NX, and BlazeCut. The diverse lineup will showcase the latest advancements in smart security technologies, including image recognition systems and smart monitoring solutions, which are essential across a range of environments, from commercial to healthcare settings. Opportunities for collaboration in the security sector Visitors can uncover opportunities for collaboration in the security sector and beyond, with the fair spanning 14 dedicated zones and pavilions: 5G Application Zone AI Application Zone AIoT Security Demo Center ESG Total Solution Pavilion Fire Protection/Disaster Prevention & Rescue Zone Healthy Building Pavilion Innovation Disaster Prevention Pavilion Safe Building Pavilion Security + AIoT Pavilion Smart Building and Living Application Zone Smart Factory & Industrial Safety Pavilion Taiwan Association of Disaster Prevention Industry Pavilion Taiwan Excellence Lock Gallery Taiwan Explosion-proof Electrical Association Pavilion Integration of smart technologies In addition to the product showcase, the highly anticipated 2025 Asia Disaster Prevention Forum will provide a platform for experts from Taiwan and the Philippines to discuss the integration of smart technologies in disaster response. Attendees can gain valuable insights into Taiwanese policies aimed at advancing firefighting response both domestically and internationally, while also examining case studies that showcase strategies to strengthen regional partnerships with the Philippines. Applications of AI The forum will look into the applications of AI and extended reality within the smart city sector In addition, collaborative efforts among the public, private, and civil sectors, intended to improve disaster resilience, remain an important focus. Moreover, the forum will look into the applications of AI and extended reality within the smart city sector, envisioning a future where multi-dimensional disaster plans can be easily visualized. Relevant topics on smart security Furthermore, the 140 seminars will spotlight a full spectrum of relevant topics on smart security, fire protection, industry safety, and more, offering attendees valuable knowledge. The Smart Security Trends and Applications Seminar Series will explore logistics and warehousing safety, intelligent sustainable operations, and smart security engineering technologies. An awards ceremony celebrating distributors and contractors will be held. The New Generation Architecture and Innovation Lifestyle Forum includes sustainable applications of HVAC systems in buildings, improving safety to modernize structures. Innovative Lifestyle Forum will focus on advanced access control technologies. Industrial Safety and Envrionmental Sanitation Seminar Series will touch on explosion-proof electrical technology and other disaster prevention practices. Fire and Disaster Prevention Seminar Series will expand on ways to scale storage safety strategies, with fire and safety designs in mind. AIoT Security Trends Forum will discuss regulations and product safety to protect against IoT environments. Synergy between security innovations Cross-industry sourcing remains integral to the fair, urging visitors to maximize options Cross-industry sourcing remains integral to the fair, encouraging visitors to maximize opportunities at the Smart Building and Fire & Safety events taking place at the same time. The synergy between security innovations, smart building, and fire safety solutions empowers buyers to discover essential products and form business connections with professionals in closely aligned fields. Secutech is organized by Messe Frankfurt (HK) Ltd – Taiwan Branch and is part of a global network of Safety Security and Fire trade fairs. Safety, Security & Fire business cluster Safety and security are increasingly important basic needs and, therefore, stand for a growing global market. With twelve trade fairs, congresses, and forums around the world, Messe Frankfurt brings together demand and supply worldwide with progressive, connected products, applications, and services focusing on commercial security and the protection of buildings, spaces, and people. The Safety, Security & Fire business cluster offers access to the dynamic markets of the Arabian Peninsula, Asia, Europe, and South America.
Managing visitor access efficiently has become a critical component of business operations across industries. With increasing security concerns, regulatory compliance, and the need for seamless visitor experiences, organizations must adopt robust visitor management solutions. Traditional methods such as logbooks and manual tracking are no longer sufficient to meet the security and operational demands of 2025. Digital solutions Modern businesses require digital solutions that not only enhance security but also improve efficiency Modern businesses require digital solutions that not only enhance security but also improve efficiency, ensure regulatory compliance, and create a frictionless visitor experience. From healthcare and corporate enterprises to manufacturing and critical infrastructure, every sector faces unique challenges that can be addressed with a strategic approach. Introduction Organizations need to consider multiple factors while implementing visitor management strategies. The reception area serves as the first line of security for any organization, making it imperative to deploy a structured and efficient system. Introducing a robust solution helps streamline visitor processes, enhance security, and improve operational efficiency. Key challenges An efficient visitor management system extends security with additional measures at visitor sign-in, ensuring safety and compliance with modern regulations. Here are some key reasons why organizations should prioritise it: 1. Strengthening Security Measures Security threats such as unauthorized access, workplace violence, and data breaches are on the rise. Implementing stringent authorization protocols, real-time visitor tracking, and automated alerts helps mitigate these risks effectively. 2. Enhancing Surveillance Across Premises A comprehensive visitor management system helps organizations maintain a digital record of visitor information, making it easier to identify unauthorized individuals and potential security threats. 3. Optimizing Investment While traditional logbooks may seem effective, they lack efficiency and security. A digital system eliminates the need for manual record-keeping, reducing costs related to security incidents and administrative overhead. 4. Ensuring Compliance and Transparency Transparent communication between security personnel and staff is critical. A modern system ensures accurate record-keeping, helping organizations comply with regulatory requirements like GDPR. 5. Managing Visitor Flow Efficiently A software-enabled system maintains an auditable trail of activity, making it easier to analyze visitor trends and track frequent visitors. Additionally, pre-registration options enable a seamless check-in experience. The way forward Organizations must transition from outdated visitor management methods to intelligent, automated solutions tailored to modern security demands. 1. Digitalization of Visitor Entry Cloud-based solutions enhance security by eliminating manual errors, ensuring efficient visitor check-ins, and maintaining accurate records. 2. Touchless and AI-Powered Authentication Touchless check-ins for Visitors using QR codes, facial recognition, and biometric authentication improve security while ensuring a seamless visitor experience. 3. Automated Pre-Registration and Screening Pre-registered visitors receive digital passes, allowing quick check-ins while reducing congestion at entry points. Automated screening processes help maintain health and security protocols. 4. Real-time Monitoring and Alerts AI-driven platforms provide real-time monitoring and instant alerts for unauthorized access, ensuring swift security responses. 5. Integration with Access Control Systems Integrating the systems with existing access control solutions enables controlled entry to restricted areas and enhances overall security. 6. Data Compliance and Privacy Protection Secure data storage, encryption, and access control mechanisms help organizations comply with global data protection regulations while safeguarding visitor information. Conclusion Outdated visitor management methods pose significant security and compliance risks. Organizations must adopt modern solutions to enhance security, streamline visitor experiences, and ensure regulatory compliance. A robust visitor management system enables seamless communication between security personnel and front-desk staff, offering a secure and efficient visitor experience. Does this sound like a great fit for the organization? Or are they looking for a tailored solution to enhance security and visitor management? If they’re looking to take the next step in upgrading their visitor management strategy, explore solutions that offer a balance of security, compliance, and ease of use. The right system will help them create a safer and more efficient workplace while ensuring that visitor interactions are streamlined and secure.
Pioneering Yorkshire security firm Gough & Kelly has extended its 25-year partnership with the University of Sheffield with a six-figure electronic security contract. The five-year contract will see the installation and ongoing maintenance of over 1,300 advanced CCTV cameras integrated with Avada Connect AI technology in 150 university buildings across the city. The team at Gough & Kelly says this will create a ‘smarter, safer, and more secure’ campus for 100,000 daily users, including students, staff, and visitors. Avada Connect software The Avada Connect software allows for advanced identification of people of interest Gough & Kelly’s AI-powered surveillance system will significantly improve security monitoring across Sheffield University sites and help to deter crime, monitor suspicious activities, and provide visual evidence in the event of incidents such as theft, vandalism, loitering, unusual activity, and unauthorized access. The Avada Connect software allows for advanced identification of people of interest. It has a spotlight search function that saves time and resources while providing accurate results. Gough & Kelly security services The system also provides real-time threat detection, automated alerts, and advanced object searching, allowing the control team to search specific objects, including faces, clothing, bags, and license plates. Gough & Kelly has been a trusted partner of Sheffield University for more than 25 years, providing CCTV, access control, and manned security services across the university campus. In recent months, the company has also provided stewarding services at the university-owned Octagon Performance venue following the temporary closure of Sheffield O2 Academy. Integrating Avada Connect Gough & Kelly has been a trusted partner of Sheffield University for more than 25 years Andy Stokes, Sales Director at Gough & Kelly says: “We are thrilled to be expanding our work with the university with the installation of new, digital CCTV systems." “By integrating Avada Connect, we are upgrading the university to the same cutting-edge cloud-based CCTV monitoring, currently in use across Doncaster, Sheffield, and (where else). With its advanced timeline searching and identification capabilities, Avada Connect is compatible with most CCTV systems and makes security more efficient while resulting in significant cost-saving benefits.” Installation of new digital CCTV cameras Elsewhere in the city, Gough & Kelly partnered with Sheffield City Council and Sheffield Police last year for the Safer Streets initiative, in which saw the installation of 15 new digital CCTV cameras on London Road and Ecclesall Road. Gough & Kelly was established in 1988. Headquartered in Leeds, the company now employs more than 270 people and provides security and safety solutions for councils, sporting events, venues, schools, colleges, and universities across the UK.


Expert commentary
As the backbone of community welfare, healthcare facilities cater to crucial public needs from emergency care to specialized medical treatments, and due to its position as a significant facet of the world's critical infrastructure, the healthcare sector faces a multitude of challenges in ensuring patient and visitor security, managing high traffic, and safeguarding sensitive data. Medical sites, such as large hospitals and urgent care clinics, see a wide variety of patients, medical staff, administrative teams, and visitors throughout the day. In addition to protecting patients, visitors, and staff, healthcare environments must protect medical and patient data, ensure immediate response to urgent medical events, and maintain 24/7 operations. Security challenges Cloud-based solutions have made their mark on healthcare security, offering unparalleled scalability Addressing the security challenges presented by 24/7 availability and high patient and visitor traffic calls for a merging of technology, processes, and security strategies that go beyond what a typical security infrastructure would look like. Cloud-based solutions have made their mark on healthcare security, offering unparalleled scalability, accessibility, and integration capabilities. These advancements address the multifaceted demands of healthcare organizations, ensuring seamless around-the-clock operations while prioritizing patient care and safety. Enhancing Operational Efficiency to Save Lives Cloud-based access control solutions have revolutionized how healthcare security professionals approach collaboration within medical facilities. These solutions offer unparalleled accessibility and insight into patient and visitor security information and access logs, improving coordination among security teams and leading to more accurate monitoring and response to developing medical events. By managing and operating access control solutions via the cloud, healthcare facilities can implement effective physical security measures while ensuring seamless collaboration among staff to deliver the highest medical care possible to patients across facilities. Physical access controls Cloud-based access control systems allow users to securely access and manage physical access controls Cloud-based access control systems allow multiple users to securely access and manage physical access controls and visitor management data simultaneously, enabling them to keep track of patient movements as they are transferred throughout the facility or between different facilities. For larger hospitals or medical campuses with multiple facilities hosting access controls via the cloud empowers users with the ability to find patients and patient data in an instant, as well as opening the door to collaborate with teams separated by long distances, ensuring all team members have access to the information they need to continue saving lives. Scaling the way to top-notch care Healthcare institutions are constantly growing and changing in response to evolving industry regulations and standards, and the access control solutions these organizations rely on should be able to scale to meet their changing needs. To ensure their access control systems can keep up with these growing demands, healthcare security professionals can invest in access control solutions hosted in the cloud to avoid the tedious hardware constraints that come with traditional on-premises solutions. Cloud solutions offer significant levels of scalability, enabling healthcare organizations to adjust their storage requirements and computing resources based on changing requirements on the fly. This capability for flexibility ensures users can manage large amounts of data without significant upfront investments in hardware. Cloud-based access control solutions Cloud-based access control solutions provide healthcare organizations with the flexibility they need to expand their access In addition to compliance with changing regulations, cloud-based access control solutions provide healthcare organizations with the flexibility they need to expand their access control platform across a growing campus or multiple buildings. Larger healthcare facilities typically consist of multiple sites of varying sizes across diverse landscapes, each with distinctive security needs. Systems hosted in the cloud provide scalability and flexibility for user organizations, allowing security teams to modify or expand upon their security infrastructure as needed without spending on costly new hardware. This adaptability is crucial for helping address varying risks over multiple sites, providing security personnel the flexibility they need to ensure patient safety over long distances. Ease of use for security teams To truly understand the value of a cloud-based access control system, healthcare security professionals must consider the long-term savings and ROI these solutions provide by bolstering operational efficiencies and enabling unprecedented scalability. These systems ensure compliance with changing standards and deliver a simplified user experience across platforms, prioritizing security and ease of use for security teams across the healthcare sector.
It’s no secret that the data security sector is constantly changing. It has an annual CGR of about 12.3%. Future trends in data security Much of this has to do with the rise of cybercrime in recent years, with reports showing that cyberattacks happen as often as every 39 seconds. To combat the growing rate of cybercrime, data security has been on the rise. As we journey further into this era, it becomes evident that a spectrum of significant trends is molding the future of data security. This exploration delves into a selection of these trends, unraveling their importance and the potential implications they carry 1. AI security tools will increase Artificial Intelligence is also being used in the development of smart attacks and malware The introduction of Artificial Intelligence in the data security industry brought significant changes, especially in cybersecurity. AI has been the golden standard for face detection, natural language processing, automated threat detection, and automated security systems. Additionally, Artificial Intelligence is also being used in the development of smart attacks and malware, bypassing even the latest security protocols in data control. And as time progresses, AI security tools will flourish and dominate the scene. Let’s take a more in-depth look at three of the top AI security tools. Targeted attack analysis tool Manufacturers utilize targeted attack analysis tools to uncover targeted and stealthy attacks. Artificial Intelligence can be applied to the program’s capabilities, processes, and knowledge. For instance, Symantec launched this tool to combat the Dragon 2.0 attack in 2022. The phishing attack reprimanded multiple energy companies while trying to gain access to their operational networks. Targeted Attack Analysis Tools can analyze incidents and look for similarities from previous situations. They also help detect suspicious activities and collect all the necessary data to determine whether a specific action is malicious. Intercept X tool Results from the Intercept X Tool feature high accuracy and a low false positive rate Sophos, a British security hardware and software company, launched the Intercept X Tool. It engages a neural network that records and analyses data like a human brain. Sophos’ Intercept X Tool can extract features from a single file and perform a deep analysis. It detects malicious activities within 20 milliseconds. Plus, it’s also trained to work on bi-directional sharing and real-world feedback of threat intelligence. Results from the Intercept X Tool feature high accuracy and a low false positive rate. IBM Watson Technology IBM’s QRadar Advisor uses IBM Watson Technology, a unique AI tool for fighting cyber attacks. Artificial Intelligence can auto-investigate activities and indicators for potential exploitation or compromise. With cognitive reasoning, IBM Watson Technology can present critical insights to accelerate the response cycle. Security analysts can utilize this technology to search for threat incidents, reducing the risk of letting them fly under the radar. 2. Blockchain as a security solution It guarantees no points of failure or hackable entrances that can expose datasets inside the system Blockchain is a type of distributed ledger technology (DLT) that aims to establish trust within an untrusting ecosystem. Today it’s one of the most robust cybersecurity technologies in the industry. Blockchain utilizes a decentralized ledger system, but your team members can still gain access to transparent information in the cloud. Members can also record, pass along, and view necessary transactional data in the blockchain. The entire blockchain process maintains data integrity within the system while establishing trust among team members. It guarantees no points of failure or hackable entrances that can expose datasets inside the system. Cybersecurity, biometrics Cybersecurity primarily benefits from these features because blockchain can create a secure and robust wall between data and hackers. On top of that, blockchain ledgers can include biometrics like fingerprints and retina scans. These prevent hackers from accessing any private data. Because blockchain is decentralized, it also limits hackable data. Together with the technology’s record-keeping system, each node is provided insight into data manipulation exposing real-time cybercrime attempts. 3. Increased and widened access control Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data Access control is critical in data security. More than a valuable security tool, business leaders can use access control to regulate people accessing any given resource. A company with an IT security setting can control who has the liberty to edit certain files. One of the primary goals of access control is to minimize threats or attacks to organizations and businesses to keep people and data secure. Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data protection laws. Benefits The benefits of increased and widened access control include: Identifying who can access and control your data at specific time intervals. Protecting data from overwriting, accidental deletion, and malicious intent. User permissions that can be readily changed. Compliance and regulation with data privacy laws. Central management of access to data through a reporting portal or a dashboard. Multi-factor authentication Access control comes in various types and systems, so it’s critical to know the features of what you’re looking for. The most common type is multi-factor authentication or MFA. It involves multiple steps before logging in, requiring the user to enter other relevant information besides the password. Some other examples of information include biometrics, answering a security question, or entering a code sent to the user’s email address. Two-factor authentication, role-based access control Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession. Another type of access control is role-based access control. In this setup, only one individual can set up access guidelines and grant permissions to specific team members within an organization. 4. Greater use of the zero-trust security model The zero-trust security model is a framework that requires every user within and outside the organization to undergo authentication, authorization, and validation. These are all essential to ensure proper security configuration before access is granted to the company’s applications and data. A zero-trust model assumes that anyone can cause data breaches and that a traditional network edge is not taken into effect. Moreover, it addresses the following modern-day challenges: Hybrid cloud environments. Security of remote workers. Ransomware threats. This framework utilizes the combination of multiple advanced technologies, including: A risk-based multi-factor authentication. Endpoint security. Identity protection. Cloud workload technology. The zero-trust model uses all these innovative tools for system identification, user verification, access consideration, and system security maintenance. Constant validation and monitoring Enforcing strict policies and compliance with data privacy laws are also essential Additionally, it also considers data encryption, email security, and asset verification before establishing connections with applications. The architecture of a zero-trust framework requires constant validation and monitoring of the users and the devices they are using. Enforcing strict policies and compliance with data privacy laws are also essential. More importantly, the zero trust architecture requires all organizations to be aware of all their available services and accounts to gain complete control of data handling and manipulation. 5. Increased privacy regulations Privacy regulations and policies guide organizations in proper data control, handling, and security. These policies guide organizations in proper data control, handling, and security. As a responsible business owner, you must comply with these regulations to avoid legal issues. With cybersecurity attacks becoming common, expect increased and stricter privacy regulations to be released in the next few years. While current policies are still taken into effect, various modifications and adjustments will occur to compete with the rising numbers of data breaches, thefts, data loss, and more. California Privacy Rights Act (CPRA) Currently, the California Privacy Rights Act (CPRA) is the most comprehensive legislation on state data privacy. It only started to take effect on January 1, 2023. The CPRA introduces the following principles: Broad individual consumer rights. Significant duties of people who need to collect sensitive and personal information. Additional definitions of data privacy and security. An individual’s duties include releasing information about data collection to concerned data subjects and proper access, correction, and deletion of information. Final thoughts 2023 is a big year for data security. Trends such as increased adoption of zero-trust policies, a greater reliance on AI security tools, and the implementation of blockchain as a security solution are all things we expect to see shortly. Staying up-to-date with these trends is important for keeping your business current and ensuring that you’re adhering to new and changing regulations. Doing so can give you an edge over the competition and keep you out of legal hot water.
Daniel May of Consort reviews the integration of access control systems in healthcare settings, outlining the benefits and key considerations decision-makers must make throughout product specifications. From patient safety and traversal to the protection of sensitive data and pharmaceuticals, healthcare environments are faced with several operational challenges. And where security remains at the forefront of decision-making, modern access control systems may often hold the answers. Physical security systems Hospitals in particular have developed into multi-faceted spaces that house hundreds to thousands of patients, staff, and visitors at any one time. In England for example, research has found in the three months leading to June 2023, an average of 44,626 people visited major hospital A&E departments each day, with over 16 million attendances typically recorded over the course of a year-not to mention an additional nine million logged at other minor units. For any building, this level of sustained footfall can request severe security difficulties For any building, this level of sustained footfall can invite severe security tests. With that, the need to deploy effective physical security systems in healthcare is clear. And so, as access control continues to become more readily adopted and new products enter the market, decision-makers are reminded to consider the requirements of their building, ensuring they select the solutions most suited to their settings and budget. Security controlled Patient safety will always remain the top priority in healthcare settings, and where matters of health and social care come into question, a diverse set of professional regulatory bodies are tasked with setting and maintaining high standards. When it comes to healthcare premises specifically, patient security and perimeter security often come hand in hand and are amongst the most pressing of challenges that decision-makers must face. To help address operational planning and potential design concerns in the NHS, the Health Building Note (HBN), provides general design guidance for healthcare buildings under HBN 00-01-citing the use of access control measures as a way of maintaining security and protecting the safety of patients, staff, and visitors. Use of access control Hospital buildings control varied levels of access for a number of security purposes Hospital buildings, for example, must control varied levels of access for a number of operational and security purposes. Routine scenarios exist where vulnerable patients are under monitoring and thus refrained from exiting the premises for their own safety, while at the same time, permitted staff must be able to reach their patients and medicines when required. For this, the use of access control is key. Equally, access credentials can also help management teams keep track of those who may be entering or exiting rooms with equipment and pharmaceutical supplies, deterring any unwanted visitors and opportunists in the process. Incorporation of access control systems On a similar note, regulations have set a minimum standard for how personal data should be stored and managed in healthcare environments, giving decision-makers an added responsibility to regulate staff-controlled areas with patient medical records. While instances of personal data breaches are rare, healthcare facilities and professionals are at legal risk should confidential data be found misused or missing. As such, the incorporation of access control systems has become essential in keeping data storage areas secure, with intuitive online systems capable of permitting access to staff with the correct credentials while simultaneously tracking who has requested clearance at digital entry points. HBN guidance Healthcare experts are better fitted to control the sheer volume of people entering and exiting To function effectively, healthcare facilities must always be perceived as safe places by the people who reside within them, and as HBN guidance implies, a unified physical security system can help address key safety and security concerns while enhancing patient and staff experience. Opportunely, access control systems are more accessible and adaptable than ever and combine several technologies such as mechanical locks and automatic doors with electronic access credentials in the form of smartphone apps, badge readers, and biometric scanners. By integrating these systems into the building’s existing infrastructure, healthcare professionals are better equipped to control the sheer volume of people entering and exiting the premises without impairing the general flow of movement and coordination around the facility. Better by design Despite the clear benefits offered to healthcare facilities, there are a number of considerations to be mindful of when choosing an access control solution. Poorly implemented systems can have an adverse effect on security and functionality - quickly costing healthcare organizations time and budget to rectify and replace the inadequate products that don’t meet the building’s requirements. For that reason, decision-makers and design teams are reminded that there is no single solution that fits all healthcare buildings. As such, it’s crucial for decision-makers to understand the systems that are being put in place throughout each of the touchpoints in their facility. Clear collaboration is required during periods of specification, where together, teams can ensure the selected product works on all angles, from meeting fire safety and sustainability standards to aesthetics and scalability. Modern access control products Scalability is a key area that decision-makers must review when selecting access control systemsFrequently overlooked, scalability is a key area that decision-makers must review when selecting access control systems. Such is their diverse nature; healthcare facilities can often change and develop as years go by, and by selecting a system that facilitates growth, such as a cloud-based solution-security and efficiency is long-established. While modern access control products are known for seamless integration, there are some systems that may restrict the ability to use different vendors throughout the remainder of the building’s infrastructure. This, in effect, causes a monopolization of products throughout the estate, which can have an adverse effect on growth by increasing costs and reducing the levels of service associated with the security system already in place. Improve security and safety A scalable and reliable access control system will continue to improve security and safety by adapting to a building’s new requirements-and all while having minimal impact on its operational network. And so, while technology will no doubt continue to influence and transform the access control market, healthcare facilities and their professionals must continue to remain educated on their own systems, ensuring they have the best options in place to keep their patients, staff, and visitors safe and secure for years to come.
Security beat
Companies at GSX 2023 emphasized new ways that technologies such as artificial intelligence (AI) and the cloud can address long-standing issues in the security market. Among the exhibitors at the event in Dallas were companies seeking creative ways to apply technology, lower costs, and make the world a safer place. Reflecting on the exhibition, here are some additional takeaways. Expanding AI at the edge i-PRO is a company reflecting the continued expansion of edge AI capability in the security market. Today, more than half of the company’s lineup supports AI at the edge so the customer has a wide choice of form factors when seeking to leverage the feature set. AI processing relay, extended warranty i-PRO is increasing their warranty period from 5 to 7 years, which could be a lifetime warranty in some cases I-PRO also has an “AI processing relay” device that accepts non-AI video streams and applies edge analytics. AI has progressed from a high-end technology to a feature available in a variety of cameras at different price points. i-PRO is also increasing its warranty period from 5 to 7 years, which could be a lifetime warranty in some cases depending on a customer’s refresh schedule and lifecycle management. Active Guard, MonitorCast The company’s video management system (Video Insight) is continuing to build new features including “Active Guard,” an integrated metadata sorter. Their access control platform, MonitorCast, is a Mercury-based solution that is tightly integrated with Video Insight. Their embedded recorders now have PoE built in. “We can move at a faster pace to fill out our product line since leaving Panasonic,” says Adam Lowenstein, Director of Product Management. “We can focus our business on adapting to the market.” Emphasis on retail and other verticals Shoplifting is a timely issue, and retail is a vertical market that got a lot of attention at GSX 2023. “We see a lot of retailers who are primarily interested in protecting employee safety, but also assets,” says Brandon Davito, Verkada’s SVP of Product and Operations. “Shrinkage is a CEO-level priority.” “Retailers are getting more engaged with security posture, instead of letting perpetrators walk,” Davito adds. Intrusion detection Verkada has an intrusion product that will notify a central station if there is an alarm On the alarm side, Verkada has an intrusion product that will notify a central station if there is an alarm, and operators can review videos to confirm the alarm. Other capabilities seeking to discourage trespassers include sirens, strobes, and “talkdown” capabilities. International expansion Verkada continues to expand internationally with 16 offices in all, including Sydney, Tokyo, and London. The core value proposition is to enable customers to manage their onsite infrastructure more simply, including new elements such as PTZ cameras, intercoms, and visitor management. Verkada emphasizes ease of use, including a mobile application to allow access to be managed across the user base. Forging partnerships “We are committed to the channel and industry, and we continue to build relationships and expand our reach,” says Davito. Among the industry relationships is a new partnership with Convergint, which was hinted at during the show and announced later the same day. They are also expanding their partnerships with Schlage, Allegion, and ASSA ABLOY. Working with other verticals They offer new features for K -12 schools, and a new alarm platform is easier to deploy and manage Verkada has also found success across multiple other verticals, notably healthcare, where they integrate with an electronic medical records system. They offer new features for K-12 schools, and a new alarm platform is easier to deploy and manage. They are integrating wireless locks to secure interior doors in schools, looking to secure the perimeter, and installing guest management systems. Transitioning the Mid-Market to the Cloud Salient is squarely focused on the “mid-market,” a large swath of systems somewhere between small businesses and enterprise-level systems. Pure cloud systems are not as attractive to this market, which has a built-out infrastructure of on-premise systems. Adding a camera to an existing system is easier and less expensive than tying it to the cloud. Benefits of cloud It’s a market that may not be ready for pure cloud, but there are benefits to be realized from adding a cloud element to existing systems. “We are continuing to augment our premise-based solutions with added cloud capabilities and flexibility,” says Sanjay Challa, Salient’s Chief Product Officer. The feedback Salient hears from their customers is “I want to own my data.” The hybrid cloud approach offers the right mix of control, flexibility, and unit economics. Cloud add-on capabilities We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive" Cloud add-on capabilities include bringing more intelligence about system operation to the user via the cloud. Over time, Salient expects to sell more cloud-centric offerings based on feedback from integrators and customers. “We want to provide the flexibility for customers to go full-cloud as it becomes more economically attractive over time,” says Challa. Vaidio AI technology Salient seeks to be a transition pioneer to help customers realize the path to the cloud. Their approach is “crawl, walk, run,” and helping customers make the transition at each stage. Salient has added AI to its product offering, incorporating Vaidio AI technology from IronYun into a powerful suite and broad array of on-premise analytics, which are gaining traction. The seamless approach makes it easy for customers to embrace AI analytics, although Salient remains broadly committed to open systems. Addressing ‘Soft’ Features for Integrators AMAG is in the process of enhancing its product line with the next generation of access control panels. However, “product” is just part of the new developments at AMAG. In addition to “hard” features (such as products), the company is looking to improve its “soft” features, too; that is, how they work with the integrator channel. Integrator channel Rebuilding a process to make your organization more efficient, is relatively easy; it just takes a lot of persistence" “We have the depth of our legacy customer base we can learn from, we just need to close the feedback loop quicker,” says Kyle Gordon, AMAG’s Executive Vice President of Global Sales, Marketing, and commercial Excellence, who acknowledges the value of reinstating face-to-face meetings after COVID. “We are laser-focused on nurturing our integrator channel,” he says. “Developing new features takes time, but rebuilding a process to make your organization more efficient, that’s relatively easy; it just takes a lot of persistence,” says Gordon. More cohesive internal communication is another useful tool, he says. Disrupting the cloud based on price Wasabi is working to make cloud applications less expensive by offering a “disruptive” price on cloud storage, $6.99 per terabyte per month (80% less than hyperscalers). Contending “hyperscalers” like AWS are charging too much for cloud storage, Wasabi is using its own intellectual property and server equipment co-located in data centers around the world. Wasabi sells “hot cloud storage,” which refers to the fact that they only have one tier of storage and data is always accessible. In contrast, a company such as AWS might charge an “egress fee” for access to data stored in a “colder” tier. Cloud storage “We saw that several video surveillance companies had not yet adopted cloud storage, and we saw an opportunity to make it easy to use,” said Drew Schlussel, Wasabi’s Senior Director of Product Marketing. “We just install a little bit of software that allows them to store data in the cloud and bring it back from the cloud.” Performance, protection (cybersecurity), and price Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies Wasabi works with integrators, resellers, and distributors and also integrates with VMS companies such as Genetec and Milestone. Emphasizing performance, protection (cybersecurity), and price, their data centers are certified to SOC 2 and ISO 27001 standards. Faster throughput for weapons detection Xtract One is a young company focusing on weapons detection in a time of accelerated concern about gun issues post-COVID. Founded in Canada and based on technology developed at McMaster University, Xtract One has found a niche in providing weapons detection at stadiums and arenas. These customers already have budgets, and it is easy to shift the money to a newer, faster technology. Madison Square Garden in New York City is among its customers. Cost savings solution Xtract One can increase throughput to 30 to 50 people per entrance per minute (compared to 5 to 6 people per minute when using metal detectors). The solution doesn’t require anyone to empty their pockets and the system alarms on items beyond guns and knives. Using Xtract One allows customers to reduce the number of screening lanes and security staff, providing additional cost savings, all while getting fans through the screening process in half the time. Purpose-built sensors The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties In addition to stadiums and arenas, Xtract One, formerly Patriot One, is also getting “inbound” interest from schools, hospitals, manufacturers, and other verticals that makeup 50% of their business. “We’re on a rocket ride, mainly because the weapons issues are not going away,” says Peter Evans, CEO and Director at Xtract One. The system uses purpose-built sensors looking for specific characteristics, such as reflective and density properties, all correlated by an AI engine. Providing early warning of violence ZeroEyes is another company focused on weapons detection. Their AI gun detection system works with video images to identify if someone is “brandishing” (carrying) a weapon. In other words, the system does not detect concealed weapons. Identifying someone carrying a weapon provides early warning of a possible violent act. Increased response with AI-enables images Images are identified by AI and sent to a monitoring center where a human confirms the image before contacting first responders. Knowing the location of a shooter enables staff to lock entry points, move people to safety, and direct first responders. The company was founded to leverage existing camera views to stop mass shootings and gun violence by reducing response times.
Casinos offer several attractive applications for LiDAR, including security and business intelligence. Using laser sensors, the technology can replace the use of surveillance cameras. For casino security, LiDAR can track player movement and provides complete coverage and accuracy that have not been achievable by surveillance cameras. Massive coverage areas can save on costs of sensor deployment versus other technologies. LiDAR and its applications LiDAR is a method for determining ranges by targeting an object with a laser and measuring the time for the reflected light to return to the receiver. LiDAR sensors emit pulsed light waves into a surrounding environment, and the pulses bounce off surrounding objects and return to the sensor. The sensor uses the time it took for each pulse to return to the sensor to calculate the distance it traveled. LiDAR is commonly used in markets such as robotics, terrestrial mapping, autonomous vehicles, and Industrial IoT (Internet of Things). Today, casinos offer a lucrative emerging market for technology. LiDAR tracking enables casino operators to understand the guest path, journey, queue time, count Crowd management LiDAR can contribute to a casino’s guest experience by counting people at doors or in sections of the gaming floor to provide intelligence about crowd size to track occupancy. LiDAR tracking enables casino operators to understand the guest path, journey, queue time, count, and other statistical information by comparing previous time frames to current occupancy levels. This approach allows them to understand digital media advertisement and experience placement. Aid in advertisement “Inside a casino, sensors are deployed like surveillance cameras,” says Gerald Becker, VP of Market Development & Alliances, Quanergy. “But instead of security, they are used to provide anonymous tracking of all people walking through the gaming floor. We can get centimeter-level accuracy of location, direction, and speed of the guests. With this data, we can access the guest journey from the path, dwell count, and several other analytics that provides intelligence to operations and marketing to make better decisions on product placement or advertisement.” Quanergy Quanergy is a U.S.-based company that manufactures its hardware in the USA and develops its 3D perception software in-house. Quanergy has various integrations to third-party technology platforms such as video management systems (VMSs) in security and analytics for operational and business intelligence. Perimeter security Sensors can be mounted to a hotel to monitor for potential objects being thrown off the hotel LiDAR is deployed in both exterior and interior applications. For the exterior of a casino or resort, sensors can be mounted to a hotel to monitor for potential objects being thrown off the hotel, or people in areas where they should not be. For example, they can sense and prevent entrance to rooftops or private areas that are not open to the public. Some clients install sensors throughout the perimeter of private property to safeguard executives and/or a VIP’s place of residence. Flow tracking and queuing capabilities Tracking crowd size can initiate digital signage or other digital experiences throughout the property to route guests to other destinations at the property. It can also help with queue analysis at the reservation/check-in desk or other areas where guests line up to tell operations to open another line to maintain the flow of guests passing. Flow tracking and queuing capabilities help casino operators to understand which games groups of customers frequent and allow for the optimization of customer routing for increased interaction and playtime on the casino floor, quickly impacting the financial performance and return of the casino. No privacy concerns LiDAR provides a point cloud; its millions of little points in a 3D space create the silhouettes of moving or fixed objects The main hurdle right now is market adoption. LiDAR is an emerging technology that is not so widely known for these new use cases, says Becker. “It will take a little bit of time to educate the market on the vast capabilities that can now be realized in 3D beyond traditional IoT sensors that are available now,” he comments. One benefit of LiDAR is that it poses no risk of personally identifiable information (PII) and therefore no privacy concerns. No PII is captured with the technology. Cameras can capture images and transmit them over the network to other applications. However, LiDAR provides a point cloud; its millions of little points in a 3D space create the silhouettes of moving or fixed objects. IoT security strategy There is a lot of interest from surveillance and security to include marketing and operations, says Becker. “LiDAR will become a part of the IoT security strategy for countless casinos soon. It will be common practice to see LiDAR sensors deployed to augment existing security systems and provide more coverage.” Also, the intelligence gained with the accuracy of tracking guests anonymously provides peace of mind to the visitors that they are not being singled out or uniquely tracked but provides valuable data to the casinos that they have not been able to capture before. “This will help them maximize their operations and strategy for years to come,” says Becker.
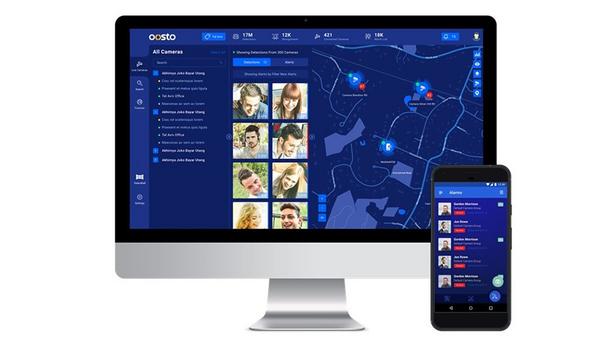
Newer facial recognition systems are scalable and provide more accurate results, and the end-user selects the parameters of system performance to suit their own application needs. “We have developed algorithms that can be optimized in various compute environments, whether in a small chip inside an edge device or on a large server device,” says Ido Amidi, Oosto’s Vice President of Products and Business Development. “It all depends on client needs. We can do it all without giving up performance. There is no significant loss in performance across various platforms.” The system’s “containerized environment” operates efficiently in a customer’s IT architecture. Facial recognition implementation Oosto, formerly AnyVision, was founded in 2016 based on deep learning research into facial recognition. The focus has been on how to use face recognition to identify people in real-world scenarios. Products began coming to market in 2017, targeting verticals that involve a need to identify “bad actors” or very important people (VIPs). The implementation of the technology involves the software operating in an on-premise appliance or server The most common implementation of the technology currently involves the software operating in an on-premise appliance or server, with inputs coming from cameras at the edge and outputs going to a network video recorder or access control system. As concepts of the Internet of Things (IoT) trickle down into the security marketplace, edge-based deployments will become more common, supplying real-time actionable information, and avoiding a flood of unstructured video data. Ethical recognition Oosto helps users deploy, set up, and calibrate the system; then, it is managed by the customer based on their needs. Privacy features are built into the system, part of the company’s commitment to “ethical” facial recognition. The technology, in general, has changed a lot since early implementations a decade or so ago failed to perform as promised. Expanded capabilities are fueled by developments in deep learning. Privacy features Facial recognition can help end-users identify people of interest but is specifically designed not to violate anyone’s privacy. There are no databases or watch lists involved; the user typically compiles their selection of “bad actors” against which facial recognition algorithms can be compared. While Oosto provides a valuable tool, the end-user customer decides how to deploy that tool in their business, says Amidi. Oosto's “liveness detection” deploys algorithms to analyze images from video and/or 3-D cameras Liveness detection Recently, Oosto has adapted the approach to provide access control; too, including “liveness detection” that deploys algorithms to analyze images from video and/or 3-D cameras to ensure a presented face is not a printed image or mask. Their latest software release is a single platform aimed at recognizing and providing insights into how people behave in physical spaces. New functionality includes the ability to detect unknown individuals entering restricted areas. Neural net algorithm Improved facial recognition functions well even for those wearing masks. A new neural net algorithm improves accuracy when identifying those wearing masks and the system can alert if a person is not wearing a mask (to aid compliance). Expanded video forensics features, designed to expedite investigations, include an ability to do in-depth searches on captured video related to body attributes, the color of clothing, etc. Recognition algorithms How well can Oosto recognize a face among 20 different people on a casino floor? It all depends on variables, such as the number of people, lighting, and angle of view, image quality, and even networking issues. Recognition algorithms are “trained” using data collected from real-world use cases; training takes place in the lab environment. The system can adapt to various lighting conditions, such as in a glass-enclosed lobby in the morning versus in the afternoon. As people enter an area, they may be looking down at their smartphones, for instance, which would mean some of their faces would not be in view. Such variables impact accuracy. Test requirements of a system apply to each specific customer and can be adjusted and tweaked as needed Customizable system Each customer must decide their parameters regarding how to best use the system, with the fewest acceptable number of false alerts, in real-time, and using existing infrastructure. Test requirements of a system apply to each specific customer and the system’s sensitivity and other operational factors can be adjusted and tweaked as needed, including at any time after a system has been installed. Meeting specified application “No customer is alike, so the needs of each customer’s system are unique,” says Amidi. For example, some situations might have a higher tolerance for false alarms, such as when there is an operator available who can make the final decision on whether a face matches. In other situations, such as when there is a missing child, false alerts are a bigger problem, and rapid response is especially of the essence. “What we give customers out of the box applies to any scenario, and customers can tweak the system with the click of a button to meet a specific application,” says Amidi. “We empower our customers to understand the pros and cons so they can react in real-time.” Identity management Oosto can help to enhance the customer experience by identifying important customers Oosto sells through systems integrators and has a partnership program with more than 150 integrators worldwide certified to manage and install systems. Oosto targets Fortune 500-size companies in financial services, gaming, and retail. The system helps to create a safe environment that is devoid of any “bad actors.” Alternatively, Oosto can help to enhance the customer experience by identifying important customers that warrant special treatment. The system also can provide an alert if any unauthorized person enters a restricted zone; that is, anyone who is not an employee, a registered visitor, or a contractor. Understanding technology In many parts of the world, facial recognition is widely accepted and used for applications such as payment and access control. Anxiety about technology, especially in the United States, is based on a lack of understanding. The public needs to “be better educated” on the subject, and Amidi expects the technology to become more socially accepted over time. “It’s a tool, and it needs to be supervised,” says Amidi. “From a technology perspective, we trust the accuracy. It just needs to be better explained.”
Case studies
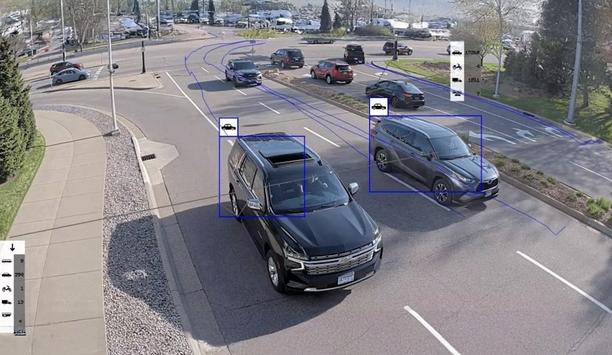
Mall of America®, the largest shopping and entertainment complex in North America, announced an expansion of its ongoing partnership with Axis Communications to deploy cutting-edge car-counting video analytics across more than a dozen locations. With this expansion, Mall of America (MOA) has boosted operational efficiency, improved safety and security, and enabled more informed decision-making around employee scheduling and streamlining transportation for large events. AI-enabled video analytics Mall was able to meet its needs for a reliable, accurate, and scalable key to support its security Standing at 5.6 million square feet and home to more than 500 retailers, restaurants, and more, MOA hosts more than 300 events each year, and has more than 32 million visitors annually from around the globe. Scheduling those events, ranging from a concert to a massive outdoor food festival, requires careful planning to ensure the Mall can support parking operations and provide safety and security to those in attendance. By expanding its surveillance system and investing in AI-enabled video analytics with Axis Communications, the Mall was able to meet its requirements for a reliable, accurate, and scalable solution to support its 24/7 security and safety operations. Accuracy and reliability "We needed technology that could keep pace with our evolving needs and make sure our security team could focus on the highest-priority tasks,” said Aaron Nielsen, Vice President of Information Technology at MOA. “Our previous solution struggled with the unpredictable Midwestern weather, including snow, rain, and cold, all impacting accuracy and reliability. Car counting is one of the most important operational metrics we have." Micro-level scheduling for vendors The success of the initial test led MOA to rapidly expand the implementation to more than a dozen locations Nielsen added: "Implementing a system that delivers accurate data allows us to quickly scale from one location to more than a dozen additional locations throughout the Mall, providing efficiency and invaluable information for our team.” The success of the initial test led MOA to rapidly expand the implementation to more than a dozen locations. The car-counting data now drives macro-level decisions about Mall hours and event planning, as well as micro-level scheduling for vendors and staff, empowering operational agility across the organization. State-of-the-art expansion With this state-of-the-art expansion, MOA can: Deploy Solutions Anywhere: A trial began with an Axis camera deployed in a particularly challenging location—on a light pole isolated from the building. Despite difficult access to power and data, the trial system proved over 99% accurate. After minor adjustments, the performance improved even further. Drive Decisions with Analytics: By deploying AI-enabled line-crossing analytics at the edge, MOA benefits from a more rugged, scalable, and cost-effective approach to decision-making, powered by the business intelligence these devices gather. This is especially useful in locations where the Mall entrance meets busy intersections, as the line-crossing technology can precisely draw the distinction between a car entering the Mall versus one that is merely passing by. Create a Smarter Security Strategy: Beyond parking intelligence, Axis’ technology supports the Mall’s broader security strategy. Cameras and Axis network speakers installed in restricted areas detect and deter unauthorized access in real-time, and alerts are immediately sent to the Mall’s central dispatch center. Prioritize Employee Safety: With unpredictable Minnesota winters, keeping employees and customers safe was key to this technology deployment. With this new system, adjustments to the devices are intuitive, and what used to require ladders, lifts, and multiple people can now be done from a desktop. Non-technical team members can review audits, make changes, and immediately analyze results from a safe location. Experiential retail and entertainment MOA is exploring additional possibilities as it continues aligning resources for future phases of the project “Mall of America presented us with a challenge that required not just technology, but collaboration, trust, and innovation,” said James Stark, Segment Development Manager, Retail at Axis Communications. “We’re honored to be part of their forward-looking approach to safety and operational intelligence. As Mall of America continues to lead the way in experiential retail and entertainment, we remain committed to delivering the reliability, flexibility, and insight-driven technology that their dynamic environment demands.” Advanced capabilities Looking ahead, MOA is exploring additional possibilities as it continues aligning resources for future phases of the project. From advanced capabilities like people counting and license plate recognition to leveraging line analytics to better understand visitor trends—such as distinguishing hotel guests from shopping center visitors—the potential for smarter, more efficient operations is there.
Seamless ASSA ABLOY digital access is now part of the Sharry workplace experience. By connecting Sharry with ASSA ABLOY’s ARX access control solution, businesses can administer secure employee access via mobile credentials as well as visitor management, all from a single unified platform, helping to save time and costs. This new integration combines ASSA ABLOY’s digital access expertise with the convenient functionality of a Sharry workplace platform. It allows administrators to control access permissions, streamline credential management and simplify guest registration directly within Sharry's ecosystem. With Sharry and ARX, customers now have a choice of mobile credentials, supporting Wallet, NFC and BLE unlocking. Integration with Sharry workplace platform “It is exciting that we can expand our ARX solution via integration with Sharry workplace experience platform to make day-to-day life easier for our customers,” says Matti Kuismin, VP & Head of Product Unit EAC at ASSA ABLOY Opening Solutions EMEIA. “The ARX security solution is an open platform and easy to integrate. Through integration with Sharry as a mobile-first technology, we enable easy-to-use mobile keys within Wallet – and do that with the highest security standards.” “We have already deployed the integrated solution with a customer in Scandinavia. Their employees now access their offices with the tap of a phone or smartwatch, thanks to the use of HID mobile credentials, both app- and Wallet-based.” Enhance security with integrated access management Integration with Sharry now enables skills and security chiefs to combine access and visitor management Developed from decades of access expertise and experience, ASSA ABLOY ARX combines digital access with alarm functionality, and is available for both Offline and Online (real-time) management. ARX is built on an open platform model, to connect seamlessly with a broad range of complementary business systems and software. The integration with Sharry now enables facilities and security managers to combine access and visitor management within a single solution. Sharry streamlines the process of employee onboarding (and offboarding), which is now integrated with access permission management, including the easy distribution of mobile credentials. It simplifies visitor management, saving staff time, and provides workplace analytics with a genuine ROI. ARX’s robust security infrastructure “We’re excited to expand our access control ecosystem with ASSA ABLOY ARX, a proven and trusted security solution,” says Karel Hudínek, Head of Technology Partnerships at Sharry. “This integration brings seamless credential management, automated access assignments, and an enhanced user experience to enterprises and property managers." "By combining ARX’s robust security infrastructure with Sharry’s mobile-first technology, we enable a smarter, more efficient approach to access management – one that simplifies operations while maintaining the highest security standards.” The Sharry/ARX integration is now available to all ASSA ABLOY customers in the Scandinavia region.
Centro Ilarco is a state-of-the-art commercial office building in the heart of Bogotá, Colombia. Designed to accommodate three corporate towers with a total of 90 offices, this landmark structure focuses on providing innovative, secure, and seamless access experiences for its tenants. The solution As a multi-building office complex, Centro Ilarco required a robust access control system to ensure security, manage tenant entry, and streamline visitor access at every entry point. To meet these needs, the DNAKE S617 8” Facial Recognition Door Station was installed across the building. Since its implementation, Centro Ilarco has experienced a significant boost in both security and operational efficiency. Tenants now enjoy hassle-free, touchless access to their offices, while building management benefits from real-time monitoring, detailed access logs, and centralized control of all entry points. DNAKE smart intercom solution has not only enhanced security but also improved the overall tenant experience. Installed products S617 8” Facial Recognition Android Door Station Smart Pro APP
HORIZON is a premium residential development located east of Pattaya, Thailand. With a focus on modern living, the development features 114 luxurious detached homes designed with sophisticated security and seamless communication in mind. In line with the project's commitment to providing top-tier amenities, the developer partnered with DNAKE to enhance the security and connectivity of the property. DNAKE smart intercom solutions With DNAKE smart intercom solutions in place, the development stands out not only for its luxurious homes but also for the seamless integration of modern technology that ensures both security and convenience for all residents. Coverage 114 Luxurious Detached Homes Installed Products C112 One-button SIP Door Station E216 7" Linux-based Indoor Monitor Solution benefits Streamlined Security C112 One-button SIP Video Door Station, allows residents to screen visitors and see who is at the door before granting access. Remote Access With DNAKE Smart Pro App, residents can remotely manage visitor entry and communicate with building staff or guests from anywhere, at any time. Ease of Use The user-friendly interface of the E216 makes it easy for residents of all ages to operate, while the C112 offers simple yet effective visitor management. Comprehensive Integration The system integrates seamlessly with other security and management solutions, such as, CCTV, ensuring full coverage across the property.
KOLEJ NA 19, a modern residential development in the heart of Warsaw, Poland, aimed to provide enhanced security, seamless communication, and cutting-edge technology for its 148 apartments. Prior to the installation of the smart intercom system, the building lacked integrated, modern solutions that could ensure secure and reliable access control for residents and enable effective communication between visitors and residents. The solution Residents can now enjoy an intuitive and seamless way to communicate with visitors DNAKE smart intercom solution, specifically tailored for the KOLEJ NA 19 complex, integrates advanced facial recognition technology, SIP video door stations, high-quality indoor monitors, and the Smart Pro app for remote access. Residents can now enjoy an intuitive and seamless way to communicate with visitors and neighbors in a modern, high-tech environment. In addition to the contactless access provided by facial recognition, which eliminates the need for traditional keys or cards, the Smart Pro app offers even more flexible access options, including QR codes, Bluetooth, and more. Installed products: S615 4.3” Facial Recognition Android Door Station C112 One-button SIP Door Station 902C-A Master Station S213K SIP Door Station with Keypad E216 7" Linux-based Indoor Monitor Smart Pro Cloud-based Intercom App
Located in Petrópolis, RJ, the Imperial Museum houses one of the most important collections from Brazil’s imperial period, including the iconic crown of Dom Pedro II. As the nation's pioneering repository of artifacts from the Second Reign, the museum showcases over 300,000 historical items—from museological and archival pieces to rare books—making it a vital resource for researchers and history enthusiasts. With more than 300,000 visitors annually, the museum plays a vital role in preserving the nation’s cultural heritage. To further enhance security and optimize visitor management, the museum turned to its long-term partner, VIVOTEK, for a cutting-edge surveillance upgrade. Challenge As visitor numbers grew and security demands evolved, the museum required a smarter surveillance system to address key concerns: High-value Artifact Protection: The Crown Room, where Dom Pedro II’s Imperial Crown is displayed, required continuous high-level monitoring. Visitor Flow Management: Real-time tracking was needed to prevent congestion and improve the visitor experience. Intelligent Security Features: Upgrading to AI-powered analytics would provide enhanced intrusion detection, more precise monitoring, and reduced false alarms. Solutions VIVOTEK, the pioneering security solution provider, partnered with ALCA NETWORK to implement an AI-driven surveillance system tailored to the museum’s needs: VSS PRO Video Management System: Centralized control with seamless AI integration enabled precise monitoring and real-time surveillance management. AI-powered Cameras: Installed in key areas, including the Crown Room, these cameras offer 24/7 surveillance with advanced intrusion detection capabilities. 3D People Counting Cameras: Deployed in high traffic zones, these cameras provide real-time visitor flow tracking, offering valuable insights for effective crowd management. Integrated Security Upgrade: The new deployment seamlessly integrated with the existing 88-camera system, enhancing the museum’s security and ensuring comprehensive monitoring of critical areas. Result and customer feedback With VIVOTEK’s advanced AI security solution in place, the Imperial Museum now benefits from robust protection for its most prized artifacts and gained powerful tools for managing visitor flow. The unified VMS and AI-driven analytics provided more accurate monitoring, significantly reducing the risk of false alarms and improving operational efficiency. Claudio Leal, Head of Electronic Security at the Imperial Museum, commented: “Thanks to the partnership with VIVOTEK and ALCA NETWORK, we now have a modern, intelligent security system that not only protects our collections but also helps us better manage the flow of visitors. The real-time data and reports have been incredibly useful for operational planning, and we are more confident than ever in the safety of our artifacts”.


Products


Round table discussion
Video surveillance has been a dominant factor in the casino market since the 1950s when video replaced the use of elevated walkways that allowed casino security personnel to monitor the gaming floor from above. As technology continues to evolve, we can expect to see more innovative uses of video in the casino market. Beyond video, other technologies are also transforming the casino experience. We asked this week’s Expert Panel Roundtable: How are new technologies impacting the casino surveillance and security market?
An organization’s security director manages a staff of security personnel, implements and enforces security policies and procedures, and generally ensures the safety of personnel and visitors to the organization’s premises. Over the years, the role of security director has expanded to include new disciplines such as cybersecurity. More and more, security directors are also taking a “seat at the table” as integral and critical members of a company’s management team. We asked this week’s Expert Panel Roundtable: How is the job of "security director" expanding, and what is the impact on technology?
There is safety in numbers, or so the expression goes. Generally speaking, several employees working together tend to be safer than a single employee working alone. Even so, some environments require that workers complete their jobs alone, thus presenting a unique combination of security vulnerabilities. The U.S. Occupational Safety and Health Administration (OSHA) defines a lone worker as “an employee working alone, such as in a confined space or isolated location.” We asked this week’s Expert Panel Roundtable: How can security technologies help to protect "lone workers?"
White papers

Guide For HAAS: New Choice Of SMB Security System
Download
Access Control: The Enterprise Buyer's Guide
Download
Combining Access Control And Intercoms For Better Security
Download
Video Technology Strategies For Hospitals Are Moving Beyond Security
Download
Smart Surveillance In The Workplace
Download
Creating A Secure And Positive Healthcare Experience
Download
Top 5 Ways to Ensure Visitor Safety and Security
Download
Beyond Security - Access Control For Multi-Tenant Sites
Download
Financial Institutions Require Future-Ready Physical Security Technologies
Download
Is Your Access Control System as Secure as You Think?
Download
Visitor Management: A Guide To Selecting And Employing A New Solution
Download