Institute security
SaaS Alerts, the cybersecurity company purpose-built for MSPs to protect and monetize their customers’ business SaaS applications released the results of its first-ever SASI (SaaS Application Security Insights) Report. The report, scheduled to be released semi-annually, reveals a shocking trend of over 3,000 Brute Force Attacks per day [against the current SMBs being monitored by the platform] and sheds light on risky file-sharing behavior and the top countries where bad actors are origin...
SaaS Alerts, the cybersecurity company purpose-built for MSPs to protect and monetize their customers’ business SaaS applications unveiled the findings of its latest edition of the SaaS Application Security Insights (SASI) Report. Published semi-annually, the free downloadable report is the only one of its kind to analyze approximately 136 million SaaS security events across 2,100 small and medium businesses (SMBs) globally and identify cyber trends negatively impacting businesses. SAS...
Alibaba Cloud, the digital technology and intelligence backbone of Alibaba Group, announced it will launch its second data center in South Korea by the end of June 2025 in response to the growing demand for cloud computing and AI services from local businesses. The investment – made three years after the establishment of Alibaba Cloud’s first data center in South Korea in 2022 - demonstrates its continued commitment to investing in South Korea, fostering AI transformation among loca...
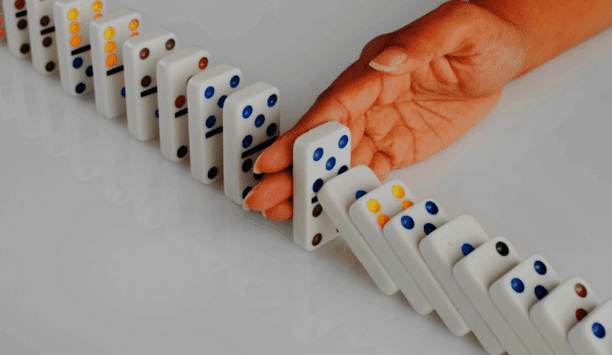
Domino Data Lab, provider of the pioneering Enterprise AI Platform trusted by the world’s largest AI-enabled enterprises, announced its Spring 2025 Release — a major platform update that helps enterprises ship trusted AI products faster. The release introduces a unified system for productivity, governance, and delivery—turning fragmented initiatives into an AI factory for trusted, repeatable outcomes. It also announced Zero-to-AI, a new service offering designed to catalyse pr...
ZeroEyes, the creators of the first AI-based gun detection video analytics platform to earn the full U.S. Department of Homeland Security SAFETY Act Designation, today announced the appointment of Peter Langman, Ph. D., as Senior Advisor on Violence Prevention. Dr Langman, a major authority on the psychology of school shooters and mass violence perpetrators, brings decades of research and expertise to help guide ZeroEyes product development. Deploying proactive technology “I am ho...
Iris ID, the pioneer in iris recognition technology, is demonstrating its advanced iris and facial recognition technologies now through 18 June at Identity Week Europe, taking place at the RAI Exhibition Center in Amsterdam. Visit booth 508 to experience powerful, multimodal touchless ID authentication solutions engineered for secure access, workforce operations, and high-security environments—from enterprise access to national ID programs. Real-world challenges “A...
News
Thomas Pilsl will take over the role of Vice President of Public Safety from Robert Nitsch. He will be responsible for the worldwide Public Safety business of the Frequentis Group. Currently Vice President of New Market Solutions, Thomas Pilsl has been instrumental in driving Frequentis’ software-centric business model and has played a key role in the successful market introduction of LifeX for Public Safety. Pilsl leadership roles Pilsl took over the newly formed Business Unit New Market Solutions and grew the Frequentis portfolio Since joining Frequentis in 2016, he has held several senior leadership roles, including Director Competence Center LifeX and Director Products and Program Delivery Public Safety. In 2020, he assumed the role of Vice President Product Management and implemented a corporate product management framework across the Group. In 2023, he took over the newly formed Business Unit New Market Solutions and expanded the Frequentis portfolio with forward-looking innovations. Pilsl leadership experience Prior to joining Frequentis, Thomas Pilsl held pioneering international management positions in the IT and software sectors for many years. In addition to his extensive leadership experience, he brings in-depth industry knowledge, as well as high expertise in business transformation, change management, and program and product management. He will follow Robert Nitsch, who joined Frequentis in 1991 and has led the global Public Safety business as Vice President since 2012. Robert's leadership Robert will continue to support the Group, focusing on business development in the area of MCX Besides other positions, Robert was COO and President of Frequentis USA, where he guided the company through a period of steady expansion. In 2012, Robert returned to Austria as Vice President of Public Safety. Under his leadership, Public Safety has achieved many significant successes and has been able to continuously expand its market presence. After 34 years with Frequentis, Robert will continue to support the Group, focusing on business development in the area of Mission Critical Services (MCX). Global success of LifeX “Robert Nitsch has shaped the development of our Public Safety business like no other. He has built strong international partnerships and has been the driving force behind the global success of LifeX." "On behalf of the Executive Board, I would like to thank Robert for his outstanding contribution and continued commitment,” says Norbert Haslacher, CEO Frequentis. Delivering results and driving innovation Haslacher added: “Thomas Pilsl combines strategic thinking with deep operational experience and a clear customer focus. He has a proven track record of delivering results and driving innovation, and I wish him every success in his new role.” Frequentis will be exhibiting at Critical Communications World (CCW) 2025 in Brussels, Belgium, from 17–19 June at Booth #K40 where they will be exhibiting MissionX – the end-to-end solution for public safety/public transport.
Elite Interactive Solutions, a remote video guarding innovator using patented intelligence and integration to achieve proven crime prevention, announces the third installment of its educational webinar series. Featuring some of the industry’s foremost subject matter experts and thought leaders, Elite Education Webinar sessions aim to inform security practitioners about the latest developments in security technologies and methodologies, crime and loss prevention, vertical market challenges, law enforcement, and more. New webinar The newest offering in the free series, “Driving Directions to Your Secure Auto Destination,” is set for Tuesday, July 15, at 11 a.m. Pacific Time / 2 p.m. Eastern Time. In addition to preventing automotive and property crime, the hour-long presentation will cover how the solution profoundly impacts losses, liability, and false alarms. substantial financial deficits More than a million vehicles were stolen in 2023, up more than 40% since 2019 More than a million vehicles were stolen in 2023, up more than 40% since 2019. Compounding those crimes are auto parts and accessories thefts, particularly of catalytic converters — a crime that can take as little as 30 seconds. A large percentage of the thefts take place at car dealerships, which suffer substantial financial deficits that also include staff time and insurance costs. The bottom line: traditional deterrents are not working, resulting in a loss of sales and revenue. Ineffective unmonitored surveillance cameras Over time, the effectiveness of unmonitored surveillance cameras has become marginalized. Criminals are no longer put off by cameras and realize video images are not investigated by law enforcement. Security guards are an immediate, onsite solution, but they are expensive and contracted only to observe and report. They do not physically engage intruders. The good news is there is one prominent security solutions provider that is drastically reducing losses for its customers. Elite Interactive Solutions’ remote guarding Elite’s command center agents directly prevented more than 16,000 crimes for automotive clients Whether it’s an auto dealership, parking facility, car rental lot or anywhere vehicles are kept — Elite Interactive Solutions’ remote guarding is the ultimate security and crime prevention answer. This solution prevents crime before it happens. During 2024, Elite’s command center agents directly prevented more than 16,000 crimes for automotive clients and assisted in nearly 500 arrests/detainments when it became necessary to engage law enforcement. The Elite difference is the unique integration of advanced AI-driven security technologies managed by highly trained remote security professionals and partnerships with law enforcement ensuring response. Session’s panel This session’s panel of leading crime prevention, auto dealer, technology, and community policing experts will help you evaluate how remote video guarding can help better protect your properties and vehicles — including augmenting or replacing security guards. Participating are Elite National Sales Director Jon Kromroy, former law enforcement executive Mitch Tavera, principal liaison for Elite’s Law Enforcement Advisory Board, and The Niello Company Director of Operations Matt Ryan. Discover the automotive storage solution to prevent: Vehicle & Parts Theft Vandalism of property Loitering & Trespassing Insurance Losses Legal Liabilities False Alarms
Global security manufacturer, Gallagher Security has announced the release of the latest addition to its award-winning controller product range, the High Security Controller 7000 (High Sec C7000) to the American market. US General Services Administration (GSA) compliant, the High Sec C7000 provides customers with the confidence that Gallagher will continue to meet the highest standards of countries in the Five Eyes Alliance and ensure they’re meeting their compliances with confidence and a future-proofed vision. High Sec C7000 The High Sec C7000 has been designed with all the features of the recently released C7000 The High Sec C7000 has been designed with all the features of the recently released C7000 Enhanced, a FIPs approved micro, and cybersecurity at the heart. It also incorporates all the core functions of the award-winning C7000 Standard variant released 18 months ago, while expanding capabilities in key areas to deliver customers enhanced reliability, resilience, redundancy, and cybersecurity. Authority comment Gallagher Security Product Manager, Jim Rayner, who led production on the High Sec C7000 says: “While the Controller 7000 Standard already has excellent cybersecurity functionality, the High Sec C7000 goes a step further with higher security government and commercial applications firmly in mind.” He adds: “We’re increasingly seeing an appetite for large users who need solutions that are certified to be used on critical national infrastructure. These are not necessarily government sites, but also commercial enterprises seeking to mitigate risk to ensure business continuity. These users are wanting devices that are PIV-ready to get that extra level of security – they want to get ahead of emerging threats.” Meeting compliance The High Sec C7000 is built with FIPS compliant components and as with previous High Sec generations The High Sec C7000 is built with FIPS compliant components and as with previous High Sec generations, has been approved by the GSA and is PIV-compliant (FIPS 201-3). It has also achieved UL/ULC compliance and meets Class 5 standards which require monitoring of cabling between device and controller for Australia and New Zealand high security customers including government, defense, prisons, and data centers. Providing End Users with industry-leading protection against attacks on firmware in the supply chain and a platform ready for the future, Gallagher’s C7000 product range are IP based controllers that can manage all localized access control, intruder alarms, perimeter security, business automation and logic needs for an organization. Independent operation Able to operate independently from the Command Centre server, the C7000 product range ensures predefined responses to monitored events, site safety, and continuity, and features a highly scalable system design, able to scale from single door systems to global systems with up to 10,000 controllers per server. The release of the High Sec C7000 brings Gallagher’s controller product range to a total of four, including the C7000 Single Door, C7000 Standard, and C7000 Enhanced variants.
Milestone Systems announces updates across its complete security technology portfolio with releases for XProtect video management software, BriefCam AI-powered analytics, and Arcules cloud video security. Each of these products give security professionals more powerful tools to protect people and assets while streamlining operations. Providing integrated security solutions Security teams can now benefit from improvements across all three platforms The releases demonstrate Milestone's commitment to providing integrated security solutions that address the full spectrum of modern security challenges, from on-premises operations to cloud-based deployments and advanced analytics. Security teams can now benefit from improvements across all three platforms. Access control visualization Security operations often struggle with switching between different interfaces to monitor video and access control systems. The new XProtect 2025 R2 addresses this challenge by bringing access control directly onto Smart Map. Operators can now see doors and access points, such as card readers, entry gates, turnstiles, and other controlled entry devices, on the same map as their cameras, making it easier to monitor facility security at a glance. When an access-related event occurs, the door icon on the map automatically updates, allowing operators to quickly identify issues. Teams can acknowledge alarms and control doors directly from the map interface, saving valuable time during security incidents when every second counts. Practical workflow improvements Operators will notice several practical improvements in their daily workflow Operators will notice several practical improvements in their daily workflow. When creating image snapshots in investigations, operators can now include time stamps and camera information directly on the images, a frequently requested feature that improves traceability in reports. The Smart Client also combines previously separate HTML and image/text functions, making it easier to build comprehensive security dashboards. For development partners, XProtect 2025 R2 enhances the Milestone Integration Platform with geographic positioning for access control units and expanded video codec support for web applications. The Milestone AI Bridge 2.0.0 is now officially available for production, making it easier for organizations to integrate artificial intelligence with their security video. Enhanced analytics portfolio The latest updates from BriefCam focus on delivering more reliable performance and intuitive operation for security teams using video analytics. Key enhancements include: Enhanced stability through modernised infrastructure and strengthened security frameworks for consistent performance when analyzing large volumes of video data New Home Research Dashboard with tailored views for specific use cases, making it easier for different types of users to access the tools they need most Improved visualization capabilities through enhanced mapping in the Respond Module to help better understand incident patterns and locations Streamlined workflows for creating custom classifications and improved synchronization with video management systems Flexible cloud security solutions For organizations transitioning to cloud-based security, Milestone's Arcules platform has received substantial enhancements that address the growing demand for flexible, scalable video surveillance solutions. The updated platform delivers: Improved enterprise scalability, allowing organizations to expand their video security coverage without compromising performance or management complexity Enhanced user management capabilities that provide administrators with better control over access permissions and system configurations Expanded analytics features that help security teams extract more value from their video data and identify patterns more effectively Better integration capabilities with existing security infrastructure, making it easier to adopt cloud-based video surveillance without disrupting established workflows These improvements enable organizations to deploy hybrid security architectures that seamlessly integrate cloud and on-premises components, providing the flexibility to adapt security strategies as needs evolve.
At a time when quantum computing is rapidly emerging as an entirely new security challenge for organizations and governments around the world, Commvault, a major provider of cyber resilience and data protection solutions for the hybrid cloud and one of the first cyber resilience vendors to support post-quantum cryptography (PQC), announces enhancements to its PQC capabilities. These advancements are designed to help customers protect their highly sensitive, long-term data from a new generation of imminent but unknown cyber threats, creating an additional layer of support, when needed. Quantum computing 63% of technology and cybersecurity professionals say quantum will increase or shift cybersecurity risks Quantum computing uses quantum mechanics to process data and solve complex problems that could take decades with classical computers. However, these advancements bring unprecedented security challenges, along with the potential for threat actors to use quantum computing to decipher and unlock traditional encryption methods. According to the Information Systems Audit and Control Association’s (ISACA) Quantum Computing Pulse Poll, 63% of technology and cybersecurity professionals say quantum will increase or shift cybersecurity risks and 50% believe it will present regulatory and compliance challenges. Now is the time to prepare and take action. Support for quantum-resistant encryption standards Commvault has provided support for quantum-resistant encryption standards, like CRYSTALS-Kyber, CRYSTALS-Dilithium, SPHINCS+, and FALCON, as recommended by the National Institute of Standards and Technology (NIST) since August 2024. It was then that Commvault introduced a cryptographic agility (crypto-agility) framework, enabling its customers, via the Commvault Cloud platform, to address rapidly evolving threats without overhauling their systems. With today’s announcement, Commvault has built on that framework by adding support for Hamming Quasi-Cyclic (HQC), a new error correcting code-based algorithm designed to defend against threats like 'harvest now, decrypt later' where adversaries are intercepting encrypted network traffic and storing it for a later time when quantum computers are powerful enough to decrypt it. Quantum threat “The quantum threat isn’t theoretical,” said Bill O’Connell, Chief Security Officer at Commvault. “We were among the first cyber resilience vendors to address post-quantum computing, and by integrating new algorithms like HQC and advancing our crypto-agility framework, we are providing our customers with the tools to navigate this complex landscape with confidence.” “Our goal is simple and clear: as quantum computing threats emerge, we intend to help our customers keep their data protected.” Post-quantum cryptography For industries where long-term data storage is required, like finance and healthcare, Commvault's expanded post-quantum cryptography capabilities provide access to a variety of safeguards that can help fortify network tunnels against quantum-based attacks. With Commvault’s Risk Analysis capabilities, customers can discover and classify data to determine where these cryptographic capabilities may be helpful. In addition, Commvault’s capabilities are simple to implement, often using a checkbox configuration, making it easy for customers to utilize when needed. The evolving quantum landscape – the need for speed As investments pour into the quantum field, the time to address emerging threats is shrinking As investments pour into the quantum field, the time to address emerging threats is shrinking. This makes proactive adoption of post-quantum cryptography critical. “Quantum readiness has become a business imperative, particularly for industries which handle data that remains sensitive for decades. The time when currently encrypted data can be decrypted using quantum technology is closer than many people think,” said Phil Goodwin, Research VP, IDC. “Commvault’s early adoption of quantum-resistant cryptography and commitment to crypto-agility positions it at the forefront among data protection software vendors in proactively addressing quantum threats. Organizations with sensitive, long-term data need to prepare now for a quantum world.” Commvault: An invaluable partner “Commvault has been an invaluable partner in our journey to enhance cyber resilience. Their leadership in adopting post-quantum cryptography, combined with their crypto-agility framework, is exactly what we need to meet stringent government security mandates and protect highly sensitive information from emerging quantum threats,” said Jeff Day, Deputy Chief Information Security Officer, Nevada Department of Transportation. “Safeguarding sensitive data is paramount, and the long-term threat of quantum decryption is a significant concern. Commvault's rapid integration of NIST's quantum-resistant standards, particularly HQC, gives us great confidence that our critical information is protected now and well into the future,” said Peter Hands, Chief Information Security Officer, British Medical Association. “Their commitment to crypto-agility is important for healthcare organizations like ours.” Availability Commvault’s post-quantum cryptography capabilities, including support for NIST’s HQC algorithm, are immediately available to all Commvault Cloud customers running software version CPR 2024 (11.36) and later, enabling seamless adoption of quantum-resistant protection.
Matrix is set to participate in Electronic Security Expo (ESX) North America 2025, on June 16 and 17, at the Cobb Galleria Centre, Atlanta. ESX gathers North America’s top integrators, security consultants, and tech leaders to explore innovations shaping the future of electronic security. As demand grows across the U.S. for intelligent, scalable, and regulation-aligned security infrastructure, video surveillance and access control remain at the heart of this transformation. With the U.S. surveillance market projected to exceed USD 37.27 billion by 2030 (Grand View Research) and cyber threats on the rise, the focus is shifting to solutions that go beyond monitoring—systems that not only protect people and property but also secure the data behind them. Critical infrastructure projects Matrix enters this conversation with its NDAA-compliant video surveillance solutions—a mandatory requirement in the North American market. Without NDAA compliance, surveillance systems risk being disqualified from government and critical infrastructure projects. Matrix will showcase its end-to-end cyber-secure video surveillance portfolio At the event, Matrix will showcase its end-to-end cyber-secure video surveillance portfolio, featuring network cameras aligned with ISO/IEC 27402 standards and Video Management System (VMS) designed to guard against the OWASP Top 10 Desktop Security Risks. This setup ensures that surveillance footage is protected from tampering, hacking, and unauthorized access—crucial as video increasingly serves as legal evidence and a compliance requirement. Access control solutions In addition, Matrix will present its VAPT-compliant access control solutions, built to secure not just doors, but also digital credentials, software interfaces, and third-party integrations. With over 40% of security breaches involving stolen or compromised credentials (IBM, 2024), securing every access point—physical and digital—is essential. Matrix access control systems track, verify, and protect each interaction, helping enterprises stay in control with confidence. “North America is a strategic market for us, and we’re here to grow with the people who know it best—local partners,” said a Matrix spokesperson. Addressing evolving security needs “Our goal is simple: deliver cybersecured, NDAA compliant solutions that help integrators and consultants win customer’s trust, and build long-term relationships.” With over 30 years of industry experience, deployments across 50+ countries, and end-to-end in-house R&D and manufacturing based in India, Matrix brings to North America a portfolio that is both globally trusted and regionally relevant. Visit Matrix at ESX to see how its secure-by-design solutions address the evolving security needs of the U.S. market.


Expert commentary
In the ever-evolving struggle between cyber offense and defense, attackers have almost always moved first. In the emerging domain of artificial intelligence, this pattern appears to be repeating itself. Yet, global cybersecurity pioneers appear disconcertingly disengaged. Just over half even agree that AI-driven attacks are set to become dramatically more complex and widespread. Equally concerning is the widespread apathy regarding AI’s role in expanding an already sprawling corporate attack surface. This is no small oversight. A recent global Trend Micro study showed that 73 percent of organizations have already suffered cybersecurity incidents due to unknown or unmanaged assets. In an era where digital blind spots are both common and consequential, hesitation is a risk few can afford. Security has to shift from reactive protection to proactive risk exposure management. The opportunity and the risk of AI Threat actors are now using jailbroken versions of legitimate generative AI tools such as ChatGPT The potential for AI to transform enterprise operations is enormous, but so is the risk. The warnings have been loud and clear. As early as the first quarter of 2024, the UK’s National Cyber Security Center (NCSC) stated that AI would “almost certainly increase the volume and heighten the impact of cyber-attacks over the next two years.” Their prediction is proving accurate. Threat actors are now using jailbroken versions of legitimate generative AI tools such as ChatGPT, freely traded as services on the dark web, as well as malicious models like FraudGPT, built on open-source large language models (LLMs). These tools are no longer just about automating tasks; they are turbocharging the entire attack lifecycle. From more convincing phishing emails and precise target selection, to sophisticated malware creation and lateral movement within breached systems, AI is driving a step-change in threat actor capability. Integrating open-source models However, this is only one side of the coin. The other, often overlooked, is AI’s impact on the corporate attack surface. Even well-meaning employees can unintentionally expand organizational risk. The widespread use of AI-as-a-service tools like ChatGPT introduces significant shadow IT concerns, especially when sensitive business information is input without proper oversight. Data processing and storage practices for many of these services remain opaque, raising additional compliance concerns under regulations like the UK GDPR and the EU’s AI Act. For those organizations that choose to build or customize their own LLMs, the risks multiply. Integrating open-source models may expose businesses to vulnerabilities, misconfigurations and flawed dependencies. Each new tool and environment adds to the complexity of an attack surface already strained by remote work setups, sprawling cloud deployments, IoT ecosystems, and accelerating digital transformation programmes. Managing the expanding risk landscape Many have already shared security incidents where a lack of asset visibility was the root cause Many security pioneers do understand what is at stake. Nine in ten agree that effective attack surface management is tied directly to business risk. They cite a long list of potential consequences, disruptions to operations, reputational damage, declining competitiveness, strained supplier relationships, financial losses and reduced staff productivity. Many have already experienced security incidents where a lack of asset visibility was the root cause. Despite this recognition, however, the response remains largely inadequate. Fewer than half of global organizations use dedicated tools to monitor their attack surface proactively. On average, only a quarter of cybersecurity budgets are allocated to managing cyber risk exposure. Third-party risk management is similarly neglected: fewer than half of firms actively monitor their vendors for vulnerabilities. This inertia creates an obvious contradiction. Security pioneers understand the business implications of unmanaged risk, but they are not equipping themselves with the tools or processes to respond. That needs to change—and fast. How AI can help defenders take the lead There is good news: AI is not only a weapon for cybercriminals. It can also be a powerful ally for defenders, particularly in the field of Cyber Risk Exposure Management (CREM). The best tools in this category use AI to continuously scan an organization’s entire digital footprint. They can automatically detect vulnerabilities, spot misconfigurations, identify rogue or shadow assets, and provide prioritized remediation recommendations. CREM platforms apply contextual filtering to reduce false positives and elevate the most urgent threats Intelligent algorithms can also analyze network behavior to identify anomalies that could signal a breach in progress. Unlike traditional tools, which often drown analysts in noise, CREM platforms apply contextual filtering to reduce false positives and elevate the most urgent threats. For overburdened security teams, this enables a far more focused and effective response. However, the keyword here is “continuous.” The nature of today’s IT environments, especially in the cloud, is dynamic and fast-moving. Assets appear and disappear within minutes. Static, point-in-time assessments are no longer sufficient. Yet more than half of organizations still lack continuous scanning processes. This leaves them exposed to risks that might persist undetected for weeks or months. Overcoming barriers to adoption So what is holding organizations back? In many cases, it’s not the technology itself but the internal politics of investment. Security pioneers interested in CREM tools often prioritize real-time alerting, clear dashboards, and seamless integration with their existing environments. All of this is now achievable. The challenge lies in securing board-level support. Many security teams still work in silos, disconnected from the broader business Boards are often cautious when it comes to cybersecurity investment, particularly when immediate ROI is not clear. To gain their trust, security pioneers must learn to speak the language of business risk, not technical threat. They must frame cyber exposure in terms of reputational impact, regulatory liability, operational continuity, and investor confidence. There is also a cultural component. Many security teams still work in silos, disconnected from the broader business. This limits their influence and makes it harder to embed security as a strategic enabler. In the AI era, this divide must be bridged. Cybersecurity must become a board-level concern, and risk exposure must be treated as a fundamental operational issue. Time to act We are at a critical inflection point. The AI revolution is not on the horizon, it is already here. Threat actors are moving rapidly to exploit it, leveraging tools and techniques that were unthinkable just a few years ago. Meanwhile, organizations remain slow to respond. Too few are investing in the tools, processes, and people needed to manage their risk exposure effectively. AI can be used not only to attack but to defend. CREM tools powered by AI offer a powerful way to regain visibility, restore control, and build lasting resilience. They enable proactive rather than reactive security. And they help organizations align their cybersecurity strategy with their broader business objectives. Security teams have to elevate the conversation. They must advocate not just for new tools, but for a new mindset, one that treats cyber risk as an enterprise risk, and one that prioritizes continuous visibility as a prerequisite for resilience.
Access control solutions will continue their evolution in 2025 as organizations assess and adapt to dynamic and increasingly dangerous threats. Trends to watch include the growing adoption of mobile access credentials and digital IDs, and the integration of digital and physical security and other technologies. Other ongoing trends include the integration of AI into access control solutions and the increasing adoption of contactless biometrics for enhanced convenience. New access control innovations As these trends gather momentum, they highlight the pivotal role access control systems play in combining security and convenience, every hour of every day. Organizations must strike the ideal balance between a secure environment and satisfying user experience if they are to meet increasingly vocal demands for both. Achieving this balance not only delivers the expected user experience but also delivers multi-layered threat protection while introducing exciting new access control innovations. Digital technologies and open standards Modern access control solutions deliver a faster pace of innovation and dramatically improved capabilities Modern access control solutions deliver a faster pace of innovation and dramatically improved capabilities as compared to what was possible in the past. The primary objective is no longer simply to secure places and assets so they are beyond the reach of the wrong people. Now it also must be as easy as possible for authorized individuals to enter a building or access digital assets. Mobile access credentials and digital IDs are increasingly a preferred solution for achieving this seamless and convenient access experience. Technology convergence is happening at a rapid pace and this convergence makes it possible to integrate digital and physical security with real-time location systems and other technologies. Together, these converged technologies provide multi-layered protection against both cyber and physical threats while also enabling valuable new capabilities. 2024 State of Physical Access Control Report As AI is increasingly incorporated into access-control solutions, we will see even more powerful ways to leverage access control data for analytics use cases. Almost 40% of respondents to our 2024 State of Physical Access Control Report said they were looking to do this. Equally consequential is the rise of fast, frictionless and easy contactless biometrics solutions in a wide range of applications including healthcare, where 32% of respondents to our recent 2024 State of Healthcare Security Report said their facilities have already implemented this technology for authentication. Looking at the broader marketplace, nearly one in four (23%) respondents to our 2024 State of Physical Access Control Report cited biometrics when asked to “name the top three trends shaping the wider access control industry in the near future.” Evolution of access control solutions As access control solutions become increasingly central to secure and convenient daily life, these and other trends will have an ongoing impact on all market sectors from healthcare and banking to the corporate real estate enterprise and business and college campuses. At the same time, those responsible for a facility’s digital and physical assets know that these trends – and security in general – will never be a static proposition. The only constant is change. Threats will never stop evolving, and those tasked with protecting organizations against these threats must never stand still. The evolution of access control solutions that we saw during 2024 will continue through 2025 and beyond, and organizations will need to remain thorough and vigilant as they address today’s ever-expanding attack surfaces and ever-evolving attack schemes.
Digital access control has well-known benefits over traditional security, of course, but also costs attached to each stage of its lifetime. However, these costs are not fixed. Many factors – including building size, shape, type, location, national regulations and more – impact affordability and efficiency calculations. Crucially, the type of access solution a business selects – wired or wireless – impacts total operating costs, including during installation, running, and any potential expansion or reconfiguration stages. Wireless installation Wiring premises can be expensive. So, the potential cost savings from choosing wireless digital access begin at the very start. Installation stage is the largest contributor to potential cost savings when businesses go wireless. In calculations for one report, access experts at ASSA ABLOY examined projected costs for a fictional 100-door installation. Labor savings for those who chose wireless over wired locks were 82.5%. Why? Firstly, because wireless installation is much faster. It is also less intrusive. Most wireless locking devices require little or no drilling of the door, whereas wired security needs cabling through and partly around a door – which means not just door damage, but the contracting of specialist electrical installers who may require multiple site visits. These costs add up. Digital access technology Torus aims for the highest level of LEED certification for all its new properties In Poland, for example, developer Torus aims for the highest level of LEED certification for all their new properties around Gdansk. Where possible, they choose products with Environmental Product Declarations (EPDs) and Green Circle documentation, favoring access solutions which reduce their carbon footprint. Wireless digital access technology is a natural choice. “The lack of wiring significantly reduces materials use, reduces costs, and ensures quick installation,” confirms Torus’ Roman Sokolowski. There’s no cabling, which cuts power consumption. There’s less damage to the building fabric and fitters make fewer journeys to and from the site. Adaptable locking solution By choosing a wireless solution, organizations also upgrade building security with little disruption. A wireless system makes it easier to improve security at an existing building via a retrofit process which does not inconvenience staff or disturb work routines. This was one goal at Plexal, a £15 million flexible work environment for London enterprise and academia. Plexal chose battery-powered wireless locks integrated with DoorFlow, NetNodes’ online platform for managing and auditing building access. “Plexal required an adaptable locking solution for a range of different doors and, with no wiring required, it was quick and easy to install ASSA ABLOY Aperio® devices with minimal disruption,” confirms Stewart Johnson, Director at NetNodes. Cost savings with improved energy efficiency Choosing wireless over wired locking can play a vital role in reducing ongoing energy use Choosing wireless over wired locking can play an important role in reducing ongoing energy use – and, therefore, expenditure. Wholesale electricity prices in Europe are approximately double what they were in 2019, according to the IEA’s “Electricity 2024” report. For a variable cost such as energy, where businesses have little control over unit prices, it is critical to control usage, especially if high and/or changeable energy prices become what analysts at ING called “the new normal for business”. Thus, the fact that battery-powered locks consume much less energy than traditional wired solutions is increasingly relevant and important. Additional savings on energy costs Traditional wired door access devices often work via magnets connected permanently to mains electricity. These doors draw power around the clock to remain locked. Wireless locks work differently. They only “wake up” when presented with a credential, to make the access decision. This translates to an additional saving on energy costs during operation: more than 70%, or thousands of euros over a typical access system’s lifetime. Wireless digital access Wireless locks only need a change of their standard battery, which may be rechargeable Related energy and materials costs during in-use stage are also lower. Wireless locks only need a change of their standard battery – which may be rechargeable – typically once every two years. No specialist maintenance is required, saving on specialists and their travel to and from the site(s). By choosing wireless digital access, businesses help protect themselves against these ongoing costs, notably energy price increases and volatility. Cost-efficient flexible working, for staff and facilities managers Perhaps harder to quantify, but equally easy to imagine, the financial benefits of choosing a wireless digital solution are felt in the increased convenience and efficiency of daily operations. In the co-working sector, for example, flexible access to offices is a priority. As “fixed” office space rented by corporations continues to fall, co-working spaces are expected to keep growing, with one estimate suggesting almost 18% CAGR to 2030. To stand out from the competition, the founders of ULab in Alicante sought the latest innovations in access and design to create their 21st-century business center. Part of the suite of digital access solutions from ASSA ABLOY, a SMARTair® system gave ULab real-time access management via battery-powered locks and Openowä, the Mobile Key solution for SMARTair, without any need to wire doors and other openings. SMARTair TS1000 Web interface With SMARTair and Openow, workspace residents can carry virtual keys on their smartphone With SMARTair and Openow, workspace residents can carry virtual keys on their smartphone; ULab’s security team update their rights over the air. An office manager can perform any operation remotely from the SMARTair TS1000 Web interface. In case of an emergency, they could lock-down the site or open doors remotely, for example. It’s convenient, efficient and boosts ULab’s security, benefiting users and managers. And because of SMARTair’s flexibility, they can comfortably welcome many more than their usual 100 daily users. “In addition to regular daily traffic, weekly traffic can almost multiply by 10 if an event is held,” says Enrique Burgos Pérez, Director at ULab. “We needed an access control system as flexible and convenient as SMARTair.” ASSA ABLOY benchmarking report Choosing wireless locks also adds flexibility – and can reduce costs – when an organization reconfigures or expands their commercial space. High-quality wireless devices like SMARTair can typically be reinstalled at another opening without impacting reliability. They move to wherever is convenient. If a business is rethinking workspace to encourage flexible or hybrid work patterns, for example, cost efficiencies could be significant. Typical savings on office relocation or expansion are estimated at around 30% with wireless over wired locking, according to the same ASSA ABLOY benchmarking report. Cost efficiency and more control with ASSA ABLOY digital access To refit and improve their student accommodation, managers at the University of St Andrews sought energy- and cost-efficient access control. They chose Aperio, another innovative digital access solution from ASSA ABLOY. Approximately 1,600 doors so far are equipped with battery-powered Aperio escutcheons – without cabling. Aperio devices integrate fully with both the university’s existing central security system and their student ID card. University security managers continue to enjoy the efficiency benefits of monitoring and controlling access from a single point and in real-time, including for doors across multiple buildings. Aperio, another innovative digital access solution from ASSA ABLOY. Benefits of cost-efficiency In comparison to a wired solution, Aperio offers significant cost-efficiency benefits. Devices are wireless, so can be installed with little energy use and no need for wiring to the mains. They consume near-zero energy when idle and run on standard batteries, consuming little power during operation. Through the entire product life-cycle, Aperio combines reliability with cost effectiveness. “Aperio gives us central management and control,” says Pauline Brown, Associate Chief Information Officer at the University of St Andrews, “and contributes to our award-winning track record in energy efficiency.”
Security beat
The practice of executive protection changed forever on Dec. 4, 2024, when UnitedHealthcare CEO Brian Thompson was shot outside a Manhattan, New York, hotel. The shocking event raised awareness in board rooms around the world about the need for, and challenges of, executive protection. Questions followed immediately, including why was the high-level executive not protected? Combination of risk and reward UnitedHealthcare’s stock price has gone down more than 20% since the shooting The event also highlighted what is at stake for companies, extending beyond the safety of executives and impacting many factors, even including a company’s stock price. UnitedHealthcare’s stock price has gone down more than 20% since the shooting, equating to tens of billions of dollars. “Companies are considering the combination of risk and reward like never before when it comes to executive protection,” says Glen Kucera, President of Allied Universal Enhanced Protection Services. “What are the chances this could happen? Before Dec. 4 many thought it was zero. And what are the financial implications for a company if it happens? Executive protection is a small investment to protect against a worst-case scenario.” Evaluation of an executive protection Before the UnitedHealthcare shooting raised awareness, fewer than 50% of executives had protection. But concerns that previously fell on deaf ears now have the full attention of companies, says Kucera. “Boards of directors are having to figure this out,” he adds. “They may not have executive protection, but now they have to do it.” A threat assessment, conducted by a company such as Allied Universal, provides an independent evaluation of a company’s executive protection needs. The assessment evaluates factors such as an executive’s travel habits, the safety of their home, etc. Does the executive need protection 24/7, or just when they travel into more dangerous areas? Risks increase related to corporate earnings Sometimes, cases increase the need for executive protection, such as an internal threat In assessing threats, security professionals also look beyond the individual to consider the safety of a corporate facility, for example. “Is there a visual deterrent, controlling who comes and goes?” asks Kucera. “If there is good security, it all ties together. We do home assessment, facility assessment, route assessment, and travel assessment as needed.” Sometimes, circumstances increase the need for executive protection, such as an internal threat. Timing is a factor, and risks increase related to corporate earnings releases, new product announcements, and corporate layoffs or consolidation. Monitoring social media tracks shifting threats that impact the need for executive protection. UnitedHealthcare shooting “He didn’t have it and probably didn’t think he needed it,” comments Kucera about the UnitedHealthcare executive who was gunned down in the streets of New York City. “He was staying at the hotel across the street and was used to walking down the street every day.” “Sometimes executives want to preserve their privacy and be able to walk down the street,” says Kucera. “Getting protection can be seen as a sign of weakness. Some CEOs in the past have said they just didn’t want it.” However, the UnitedHealthcare shooting raised the stakes of the need for more vigilance. “The bottom line is you have to yet beyond objections and make the investment to protect against a worst-case scenario,” says Kucera. Anti-capitalist sentiment in the general population An internal police bulletin warned of an online hit list naming eight executives and their salaries Threats to executives sometimes arise from anti-capitalist sentiment in the general population about perceived inequalities in wealth and power. Executives provide symbolic targets for anyone who fights the system, and social media has amplified the voices of those who oppose capitalism. For example, a "Most Wanted CEO” card deck seeks to shine a spotlight on "titans of greed." Also, in the aftermath of the UnitedHealthcare shooting, CEO "wanted" posters appeared across New York City, threatening various executives of large companies. An internal police bulletin warned of an online hit list naming eight executives and their salaries. Careful monitoring of social media posts Careful monitoring of social media posts and other sources enables executive protection professionals to analyze data and separate the dangerous threats from the merely negative ones. Sadly, positive support of the UnitedHealthcare shooting was expressed by the 300,000 or so followers of the shooter, who became a celebrity of sorts. A huge outcry of negative sentiment toward the insurance industry led to fear that copycat incidents might occur. “There has been an unprecedented amount of positive support for committing murder,” commented Kucera. Executive protection requests HR executives can be at risk, especially at a time of layoffs or consolidation “Let’s face it, there has been a lot of controversy, from COVID to the Middle East crisis, to the political campaign, and there is negativity on both sides,” says Kucera. “People have opportunities to pick sides, and there is a lot of sentiment going both ways, and there is a small percentage of people who will act aggressively.” Executive protection requests now extend beyond the CEO to include others in the management ranks of companies. Basically, any public-facing executive is at risk, including anyone who makes statements to the press. Human resource (HR) executives can be at risk, especially at a time of layoffs or consolidation. Private information on the Internet Typically, an executive is assigned a single armed operative for protection. The firearm serves primarily as a visual deterrent that hopefully makes a potential perpetrator think twice. “When they plan an event like this, their expectation is that it will be a soft target,” says Kucera. “If there is an officer, it gives them pause.” Controversial or high-profile CEOs are typically protected 24/7, including when they travel with their family. Adding risks is the fact that private information is now posted on the Internet, including where an executive lives and where their children go to school. Internet monitoring Internet monitoring also includes the “dark web,” which includes sometimes dangerous information “We offer social media monitoring, and we advise them to be more careful with what they post,” says Kucera. “We monitor reactions to posts including any that might be threatening. We watch social media carefully if a company announces earnings or a change in their service or product offering.” Internet monitoring also includes the “dark web,” which includes sometimes dangerous information that is intentionally hidden and requires specific software, configurations, or authorization to access. Own layer of protection Public and government officials can also come under fire in a variety of scenarios. FEMA officials faced threats after the recent floods in the Southeast, for example, among other situations where perceived unfair treatment promotes thoughts of retribution. Although government agencies have their own layer of protection, there are instances when they call on companies such as Allied Universal for additional help. Ad hoc protection for various executives In the aftermath of the UnitedHealthcare shooting, calls to Allied Universal’s Command Center increased by 600%, reflecting requests for ad hoc protection for various executives. These requests are in addition to the company’s business providing “embedded” operatives that travel with executives all or some of the time. On that side of the business, requests for services are up probably 300%, says Kucera.
GSX 2023 has its share of new product announcements, although many of the new products are enhancements to technologies shown at last spring’s ISC West show in Las Vegas. Booth traffic on the first day seemed busy at the Kay Bailey Hutchison Convention Center in Dallas, although one exhibitor complained that it takes some time for the traffic to make its way to the farthest areas of the show floor. Apparent throughout the GSX show is an expanding idea of what constitutes security. Increasingly, ‘security’ technologies offer benefits throughout other parts of a company or institution. Security is also being broadened to encompass ‘safety,’ including emergency response and wider issues of keeping a company safe. Managing multiple systems People look at the systems they have, and they are looking for more information" Manufacturers at GSX are talking about more than new products. Rather, they are offering new approaches to turn products into ‘solutions’ for customers. Among the benefits of new systems is the availability of more data. “People look at the systems they have, and they are looking for more information and data and insights from their systems,” says Kyle Hurt, Genetec’s Area Vice-President of Sales for the US and Canada. “In the past, if I’m managing multiple systems and spending time and resources, I am making sure systems are operational. Today, it’s more like: How do I make my enterprise more efficient? I spend less time on making sure systems are working together but more time on how we can use the information.” Manufacturers at GSX are talking about more than new products Security control room Genetec is enhancing its Security Center 5.11 version with a newly redesigned web client that provides new capabilities related to system audio, including the ability to trigger a public address from a mobile device in an emergency, two-way audio to and from the security operations center, and the ability to record an incident. The new web client offers new levels of “Security on the go,” says Hurt. A mobile device becomes an extension of the security control room. “Customers want to have more remote capabilities and have their security personnel out and about, not tied to a desk,” says Hurt. The new web client works to unify the four pillars of the Security Center— video, access control, license plate recognition, and now audio. Single source manufacturer Audio can now be used to broadcast a message, respond to an incident, and notify people" “Audio has taken time to develop legs in our ecosystem,” says Hurt. “We have been developing partnerships and use cases beyond an intercom at the door. Audio can now be used to broadcast a message, respond to an incident, and notify people en mass of what’s going on.” Manufacturers are also fine-tuning how they work to meet customers’ needs. “Customers want one point of contact, a single source manufacturer, and a solution that reflects the manufacturer is listening to the voice of the customer,” says Jerry Burhans, Managing Director of ASSA ABLOY Global Solutions - Critical Infrastructure, which seeks to be a global partner to critical infrastructure industries. The Critical Infrastructure business works across the various product groups of the notoriously siloed company to bring together solutions aimed at meeting each customer’s need. Manufacturers are also fine-tuning how they work to meet customers’ needs Best-in-class technology “We try to have best-in-class technology and collaborate within ourselves to make sure we have what customers need,” says Burhans. Critical infrastructure industries such as water, power and energy, oil and gas are developing standards to help support preparedness of the nation’s infrastructure, and ASSA ABLOY Global Solutions is helping operators secure access and provide audit trails on locking hardware and keys within their security perimeters. Managing customer assets Johnson Controls’ new OpenBlue Service for the security device market seeks to proactively manage customer assets (equipment) as a service. The company’s software platform of connected solutions monitors and manages security devices across vendors and provides remote support services including skilled engineers who can work to ensure that a company’s assets, including cameras and access control readers, operate dependably. Working remotely, OpenBlue analyzes the performance of each system component Johnson Controls estimates that, unfortunately, up to 25% of a company’s security assets may not be working as intended, whether they lack the latest firmware update or are not connected. Working remotely, OpenBlue analyzes the performance of each system component and responds to ensure equipment operates as intended. “We believe we can close that gap with our solutions,” says Greg Parker, Vice President, Innovation & Portfolio Management for Johnson Controls. Physical security equipment A big advantage of OpenBlue for security customers is the ability to manage cybersecurity and threats at the edge, which may not currently be addressed by the IT department. The OpenBlue offering includes an embedded ‘air wall,’ which is a zero-trust architecture for physical security equipment. OpenBlue also helps customers manage the ever-changing lifecycles of various assets. Another concept prompting discussion at GSX 2023 is the gap between what a customer expects from a product and what the product can realistically deliver. With endless promotion in the last several years centering on concepts such as artificial intelligence (AI), is it any wonder that customers may sometimes have unrealistic expectations about what a technology can accomplish? The good news at GSX is that, as progress marches on, newer technologies are getting closer and closer to delivering on customers’ most ambitious expectations. The forward momentum of technology development is evident throughout the GSX 2023 show floor, reflecting the promise of even greater product capabilities in months and years to come.
A pioneer in the access control sector since 1971, AMAG Technology is looking to the future and the next generation of products that will expand its services to customers. “In our vision, we have advanced approaches that will not only provide our partners with advanced technologies but also ones that are easier to install with tools to expand their services,” says David Sullivan, who was appointed President of the venerable access control company in September 2022. New challenges at AMAG Sullivan brings a new outlook to the AMAG business, a part of Allied Universal, and a new vision to lead the company into the future. We caught up with David Sullivan to discuss his new challenges at AMAG and the journey ahead as the company looks to the future. Q: How does your background inform your approach to leading AMAG? I believe that it helps me to define a vision for AMAG that will be unique and on the leading edge of our industry David Sullivan: With the exception of only a few short years, my career has been in access control. I have experience with several systems and have had the privilege to manage several successful access control companies. As a result, I bring a great deal of experience into my role at AMAG. I believe that it helps me to define a vision for AMAG that will be unique and on the leading edge of our industry. Q: How would you describe AMAG’s journey over the last several years and how do you see the future? Sullivan: Prior presidents of AMAG always shared their leadership vision and direction with senior leaders located in the United Kingdom. This had an impact on the full direction of the business, sometimes limiting its ultimate success. Before I became a part of AMAG, these senior leaders that were located in the UK retired, placing for the first time the full management responsibilities of the president. This has allowed me to integrate the business into a single team, with single objectives, and a single vision. We expect to begin to reveal this new vision in the coming weeks. We are excited about the future of AMAG and believe we will surprise the industry with our new products and approach in the coming months and years. Q: How important is it that a manufacturer provides both hardware and software solutions? How does AMAG’s approach (in general) differentiate it in the market? We can design the complete solution, providing functionality that others may find more difficult to accomplish Sullivan: Regardless of the manufacturer, we all provide hardware and software. An access control solution is not complete without both. Some of us choose to make our panels, and others do not. Those who are dependent on third-party suppliers are restricted to the developments and direction of that company, and while it might be perceived to be an open technology, it still is proprietary to the hardware manufacturer. AMAG has controlled its manufacturing of panels from day one. The result means that we can design the complete solution, providing functionality that others may find more difficult to accomplish. Q: How does the breadth of AMAG’s product suite provide advantages to customers and/or integrators? Sullivan: AMAG’s product portfolio is unique and provides the end user with an end-to-end identity management solution from one company. Our Control Room PSIM, Symmetry CONNECT Identity Management Solution, Symmetry Access Control, and Symmetry GUEST solutions all integrate to provide the user with a broad set of features and capabilities from a single provider. There is no finger-pointing when we come to support your system. We hold full responsibility for making it work and can quickly provide a resolution to any application difficulties the user may be experiencing. Q: How does AMAG address the divide between on-prem and cloud systems? How do you help customers make the transition and/or plan for the future? We are in the early stages of developing our next generation of access control in which we intend to provide on-prem Sullivan: In our current product portfolio, we have three products that are cloud-based. Our mobile credential platform (Symmetry Mobile), our visitor management solution (Symmetry GUEST), and our physical identity and access management solution (Symmetry CONNECT) are all offerings that operate in the cloud. We are in the early stages of developing our next generation of access control in which we intend to provide on-prem, web client, and cloud-based offerings. One of the primary objectives is to ensure that the large installed base of systems that are out there today will be able to migrate not only to our next generation but as well to the cloud if the client so desires. Q: What is AMAG’s approach to mobile credentialing? Sullivan: As an access control provider, adding Symmetry Mobile credentialing to our portfolio just made sense. We want our customers to have a forward-thinking solution with the opportunity to save money not only on the physical badges but the cost of printing and distributing badges. Mobile credentials can be easily issued and revoked remotely, reducing administrative overhead, and eliminating the need for physical inventory management. Organizations can centrally configure what devices are used and the read range for each type of device and operating system, thus providing flexibility. Symmetry Mobile offers a customized questionnaire that controls access and reduces liabilities. Q: What has surprised you the most in your first year or so leading AMAG? Not many companies are blessed with such a broad portfolio that is supported by a resource-rich company Sullivan: I wouldn’t say I was surprised by this as much as happy to see, but I would say that the quality of our people was a pleasant surprise. As well, the AMAG product offering is broad and has some unique elements. When coupled with the depth of the resources that we have in AMAG, I know that we are second to none. Not many companies are blessed with such a broad portfolio that is supported by a resource-rich company that has so many talented people. Q: Please describe your dealer channel, and how you are seeking to expand it. Sullivan: The AMAG products are sophisticated and typically are installed for higher-end applications. With this sophistication comes a need to be well able to install such a solution. We have a strong group of certified and loyal partners who help us to deliver these enterprise solutions. We desire to provide our existing partners with updated and competitive systems to offer to their end users. Q: What is the security industry’s (and/or AMAG’s) biggest challenge in the next five years? We need to find ways to provide both our channel partners and the customers with solutions that are easily integrated Sullivan: I believe that the advancements that we are seeing in technology provide our industry with the opportunity to truly change how security is provided to our collective customers. As we advance these solutions, we will need to do so responsibly and in a way that helps the channel’s abilities. We need to find ways to train our partners to both install and support these more complex solutions. At the same time, we need to find ways to provide both our channel partners and the customers with solutions that are easily integrated, moving away from proprietary closed systems to open and cohesive solutions. This will ensure that the users get the best, and most complete solutions. Q: What does the industry as a whole misunderstand about AMAG -- time to set the record straight! Sullivan: Well, I am not ready to openly share where we are heading. We are in the process of putting together some advanced approaches to how we will do business with our partners. We are focused on providing tools that will enhance their services to their customers, and with products that are leading edge. I can only state that all should keep their eyes on AMAG, because over the next few years, we are going to surprise some people, and more importantly make our loyal partners quite powerful.
Case studies
The Link School of Business provides education and training through innovative teaching methods and practical approaches focused on the application of knowledge to create new businesses. Located at the heart of São Paulo, Brazil, this educational institution, established in 2020, is home to both aspiring entrepreneurs and experts in the field. With its mission to positively impact the world by transforming education, offering cutting-edge educational facilities that are safe and conducive to learning is imperative for this dedicated college. Challenges Safeguarding a modern 6-storey building is not an easy task. Monitoring the safety of students and school staff at all times is of utmost importance. Access control must be in place in order to regulate the flow of people and vehicles entering and leaving the school premises. In terms of classroom optimization, several aspects must be achieved such as automatic attendance, behavior analysis, usage of interactive whiteboards for collaboration, and more. Integration with third-party software and hardware is also difficult and challenging to accomplish. Access control must be in place in order to regulate the flow of people. Solution In order to create a secure and innovative learning environment and provide intelligent and real-time learning experience to its students, Link School of Business partnered up with Dahua and deployed the Dahua Smart Education Solution around its campus. ANPR access cameras and bracket cameras were set up at the parking lot of the school to automatically recognize authorized vehicles and monitor the area 24/7. ANPR access cameras and bracket cameras were set up at the parking lot. Face recognition terminals At the entrance, intelligent turnstiles with face recognition terminals were installed to instantly recognize authorized people and efficiently streamline access to the building. In common areas such as hallways, lobbies and stairways, 3MP behavior cameras equipped with video metadata algorithms were strategically installed to accurately recognize students’ non-recurring activities to help prevent accidents (e.g., fall) from happening. It can also predict crowd formation and conflicts among students in real time. 3MP behavior cameras equipped with video metadata algorithms. Dahua DeepHub smart interactive whiteboards Dahua DeepHub smart interactive whiteboards offer an artillery of academic tools and features In the classrooms, the Dahua Smart Education solution goes beyond monitoring. It enables automatic attendance by recognizing the students that are present in the classroom, as well as those who are late or left the class before it ends. The Dahua DeepHub smart interactive whiteboards offer an artillery of educational tools and features to boost learning and collaboration in the class. It can also connect students’ computers and transmit lecture content to other rooms or locations in real time. What’s more, intelligent cameras installed inside the classroom can also recognize students’ behavior such as exchanging items during an exam, using mobile phone, and even sleeping during a class session, informing the teacher about such actions and enabling them to act accordingly. Results The Dahua Smart Education Solution successfully redefines education and security at Link School of Business by connecting students, teachers and lecture content in an innovative and interactive way, while also ensuring their safety and security at all times. It offers an intelligent high-tech system that strengthens learning experience, innovates teaching methods, and sets new security standards in the school. Dahua Smart Education Solution successfully redefines education and security. Innovation and technology “Innovation and technology are very important to us. Alongside pioneering companies like Dahua, we seek to create a very favorable environment to showcase everything that is state of the art (such as) campus access and classroom cameras,” says Alvaro Schocair, Founder and Chairman of the Executive Board of Directors of Link School of Business. “Our main goal is to provide students and teachers with the best possible ecosystem so they can create products, develop service, build their companies, and through their organizations, improve society and make the world a better place,” he added.
Iveda®, a pioneer in AI-driven video surveillance and smart-city technologies, announced that Subic Sun Development, Inc. has chosen the IvedaAI™ platform as the video surveillance solution for the soon-to-open Subic Sun Resort, Convention & Casino. IvedaAI was selected early in the build-out to inform camera placement and ensure frictionless integration with future-ready, AI-powered analytics. Focus on safety and service Located on the former U.S. naval base in the Subic Bay Freeport Zone—a special economic hub that hosts thousands of international and local businesses—the resort will feature 500 guest rooms, a state-of-the-art convention center, a luxury casino, and two Accor-brand hotels, Ibis Styles and Mercure, scheduled to open in December 2025. The decision comes as global resort operators sharpen their focus on safety, service, and operational efficiency. The global resort market generated $347 billion in 2024 and is projected to reach nearly $945 billion by 2030, an 18.5% CAGR. IvedaAI’s AI-enabled video analytics IvedaAI’s AI-enabled video analytics will help property staff lower security costs, respond to incidents faster IvedaAI’s AI-enabled video analytics will help property staff lower security costs, respond to incidents faster and unlock data-driven insights that boost both guest satisfaction and bottom-line performance. “Iveda being selected as a premier security and surveillance provider before the first Subic Sun Resort guest ever checks in is a powerful endorsement of our commitment to providing state-of- the-art monitoring technology,” said David Ly, CEO and Founder of Iveda. IvedaAI’s real-time analytics Ly added: “By designing camera layouts around IvedaAI’s real-time analytics, Subic Sun can optimize coverage, reduce blind spots, and deliver safer, smoother guest experiences—without a costly equipment overhaul. We expect more ground-up projects to follow this blueprint.” Iveda Philippines—Iveda’s joint venture focused on nationwide smart-city deployment—secured the Subic Sun contract and will oversee the on-site rollout. The win represents the team’s first major hospitality project and advances its plan to generate US$ 3 million in smart-city revenue by FY 2026, building on the broader initiative it announced last year.
VIVOTEK, the global pioneer security solution provider, has partnered with dechant hoch- und ingenieurbau gmbh, a prestigious, family-owned construction company with over 140 years of industry experience. Renowned for its expertise in exposed concrete construction, dechant has contributed to iconic projects such as the Deutsche Bundestag and the Galileo Control Centre. Seeking to elevate construction site security, dechant turned to VIVOTEK for an integrated security solution, seamlessly facilitated by its subsidiary, Compu-House GmbH. Significant security concerns Challenge The construction industry is often vulnerable to theft and vandalism, resulting in financial losses and project delays. dechant faced similar challenges at their construction sites, where large areas and valuable materials presented significant security concerns. Monitoring such expansive zones and responding to incidents in real-time posed logistical challenges, especially at night or in remote locations. Solution To address these challenges, VIVOTEK developed an innovative, AI-driven security solution integrated with dechant’s Security SEC-WATCH Tower—a mobile system specifically designed for construction site security. By combining VIVOTEK's technology with the flexibility of the SEC-WATCH Tower, dechant was able to effectively address its unique security needs, setting a new benchmark for construction site protection. Key features of the solution: VIVOTEK 5mp Speed Dome SD9384-EHL: Offering high-resolution imaging and exceptional pan-tilt-zoom capabilities, this speed dome camera ensures comprehensive coverage of large construction sites. VIVOTEK 5mp Bullet IB9387-EHTV-v3: This bullet camera provides superior image quality and low-light performance, making it ideal for monitoring outdoor areas with challenging lighting conditions. VIVOTEK Advanced AI-Powered Video Analytics: By harnessing the power of artificial intelligence, the surveillance station is equipped with advanced video analytics capabilities, including motion detection, intrusion detection, and object tracking. Vision Object Analytics: VIVOTEK's vision object analytics further enhance the station's capabilities by enabling the detection and classification of objects in real-time, facilitating proactive security measures and incident response. Two-Way Communication: The IP Audio Speaker allows remote communication and pre-recorded announcements to deter intruders. Real-Time Monitoring and Alerts: Integrated with AI-driven analytics, including intrusion detection, line crossing detection, and loitering detection. Additionally, the backend solution provided by VIVOTEK partner artec AG ensures seamless integration and centralized management of video feeds and analytics data. Notifying security personnel Results VIVOTEK's AI-driven security solution, integrated with dechant’s Smart Security SEC-WATCH Tower, demonstrated its effectiveness during a real-world incident. During a real-world incident, VIVOTEK's system detected an unauthorized individual on-site after hours, triggering an alarm and notifying security personnel in real time. Leveraging VIVOTEK’s Smart Tracking and advanced PTZ cameras, the system automatically tracked the individual’s movements, capturing high-quality video evidence. The footage and real-time alerts enabled swift action, ensuring the individual was safely removed from the premises without further disruption. This success of the security solution was highlighted by German BR Frankenschau news on January 10, 2025, showcasing its effectiveness in real-world scenarios. Key benefits Enhanced Security: Real-time monitoring and AI-driven analytics deter theft and vandalism. Cost Efficiency: Reduced financial losses from theft and minimized project delays. Flexibility: Mobile video towers can be relocated as project needs evolve. Reliability: Durable equipment ensures uninterrupted operation in all weather conditions. Peace of Mind: Comprehensive security solutions protect assets, personnel, and progress. Conclusion & customer feedback VIVOTEK’s innovative security solution, integrated with the dechant Security SEC-WATCH Tower, has set a benchmark for construction site security. By combining cutting-edge cameras, AI analytics, and mobile flexibility, dechant has successfully addressed the challenges of site security, ensuring the safety of its projects and assets. This success underscores the value of robust and innovative security solutions in the construction industry. Johann Steuer, Founder of Compu-House GmbH, emphasized: "Empowering construction sites with cutting-edge technology is not just about security; it's about enabling progress and ensuring the safety of those who build our future."
Inaugurated on May 25, 1999, the Museo Antropológico de la Comunidad de Madrid began construction in 1987. It wasn't until ten years later, in 1997, that the decree establishing the museum was issued, thus formalizing the institution's existence. As part of the museum’s modernization, the client needed an SMD LED solution that includes a glass in front of it to avoid dead pixels and any possible damage or accidents caused by museum visitors. Dahua, together with Epsilon Media, provided an innovative solution that overcame these limitations and optimized the museum experience. Renovation of The Museum The Museo Antropológico de la Comunidad de Madrid was converted from the former Dominican Convent of the Mother of God, built in several phases between the 17th and 18th centuries. As an old establishment, the client wanted to renovate the installation step by step, with the first stage comprised of an LED wall in the main entrance. Their first idea was to install an SMD LED solution with a glass front in order to protect the LED wall and avoid issues with all visitors visiting the museum. Building such a solution is costly and may not be the right solution due to the lack of front-line maintenance. Flip COB Indoor Fine Pixel Pitch LED The Dahua Flip COB Indoor Fine Pixel Pitch LED offers mini flip Chips on Board (COB) technology Together with the Epsilon Media and the Dahua team, the museum evaluated the Dahua Flip COB Indoor Fine Pixel Pitch LED solution in person. After a deliberate discussion, the client agreed that it is the right solution for their facilities. The Dahua Flip COB Indoor Fine Pixel Pitch LED offers mini flip Chips on Board (COB) technology that enables full illumination and softer light without pixel particles, effectively combating digital visual fatigue. Key Features Another notable feature of this LED is its dustproof and anti-fingerprint surface that leaves no visible traces when touched It allows full front maintenance that makes disassembly and maintenance highly efficient. With the full control of the ink color parameters on the surface of the light board, the ink color at all angles is guaranteed to be uniform, which helps solve the industry’s issue regarding ink color differences in batches. Other benefits include high contrast of 10,000:1, energy-saving and power-saving capabilities (less than 75 watts per box, 40% lower than other SMD products), and 160° super wide viewing angle. Another notable feature of this LED is its dustproof and anti-fingerprint surface that leaves no visible traces when touched. It is also waterproof and moisture-proof, with a low rate of dead pixels and high hardness against knocks. Doesn’t Require Additional Glass Protection These features effectively meet the requirements of the client regarding additional protection against damage to the LED during operating hours. Dahua continues to drive technological innovation to improve the way people experience history. With the Dahua Flip COB Indoor Fine Pixel Pitch LED and the Quality Service Epsilon Media offered, the Museo Antropológico de la Comunidad de Madrid was able to install an LED wall without the need of additional glass protection, providing an exceptional digital display of historical images inside the museum while enhancing visitor experience and saving costs. Remarks From The Museum Director “With the video wall that Dahua installed for us, we were able to renovate the first unit that was originally there. This type of technology is significantly important in transmitting knowledge about the past. The overall collaboration was very satisfactory,” says Mr. Enrique Baquedano, Director of Museo Antropológico de la Comunidad de Madrid. “The Dahua team was always ready to help whenever we encountered any issue. What’s more, the LED wall is balanced and cohesive with the overall aesthetic of the museum, which is an added bonus,” concluded Mr Enrique.
The Torrance Unified School District is a cornerstone of the Torrance community, dedicated to providing a high-quality education that prepares students for success in college, career, and life. Serving a diverse student population, Torrance USD delivers a comprehensive and enriching educational experience from kindergarten through high school. The school district comprises 17 elementary, eight middle, and five high schools, one continuation high school, and one alternative high school. Vendor solutions Torrance USD had a mashup of different technologies and vendor solutions across its schools Like many school districts, Torrance USD had a mashup of different technologies and vendor solutions across its schools regarding the ability to broadcast announcements and alerts. Each school had separate systems for bells, clocks, and loudspeakers. There was no central management of these systems, and the school district couldn't create pre-recorded messages for emergencies. Many system components were also end-of-life, and maintaining everything was cumbersome at best. Focusing on consolidation for reliability and consistency Torrance USD began planning district-wide communication improvements in 2020, with the overarching goal of deploying one uniform system through all 32 campuses, with one dashboard to manage communications. The school district achieved its goal by deploying Cisco Call Manager coupled with Singlewire’s InformaCast communications software and hundreds of IPX endpoints from AtlasIED. Vetted integration technology partners like Cisco, Singlewire, and AtlasIED ensure that interoperability, reliability, and usability have all been verified and validated through extensive testing. Surveillance cameras for emergency alerting Torrance USD began planning district-wide communication improvements in 2020 “This project was part of a larger strategic plan to secure each campus — improve perimeter security, add surveillance cameras, allow for emergency alerting, consolidate the speaker systems, and standardize the bells,” said Gil Mara, Chief EdTech and Information Services Officer at Torrance USD. “For example, when you went from one campus to another, campuses had different bell sequences for scenarios like lockdowns. So, there was no consistency of the alerting mechanisms, and we wanted to ensure it was consistent across all the schools.” Digital and physical security of K-12 schools District staff contacted Nilkanth Radadia, Senior Account Manager at NIC Partners, to design the desired district-wide communications solution. NIC Partners has over two decades of experience enhancing the digital and physical security of K-12 schools and was well-suited to take on a project of Torrance USD’s scale. Focusing on what’s most important “Many stakeholders were involved in this project,” said Radadia. ”Given the project’s scope and requirements, there were a lot of conversations beforehand to get the district comfortable with understanding how the system would work." "Some key elements were customizability, two-way talk, multicolor visual message capabilities, and ADA compliance for the visual and hearing impaired. When AtlasIED came out with their full LCD screen speaker, that was a game changer.” Feature set and industrial design NIC Partners installed nearly 1700 IP-SDMF speakers throughout the schools to ensure messages AtlasIED was chosen as the vendor for the system upgrades after a thorough evaluation of various vendors. Their feature set and industrial design, particularly the full LCD screen speaker, stood out. NIC Partners installed nearly 1700 IP-SDMF speakers throughout the schools to ensure messages were audible, visible, and intelligible. WAN or LAN network architecture Leveraging standard WAN or LAN network architecture, each speaker is equipped with an integrated talkback microphone, LCD, and LED flasher, supporting both visual text and audio broadcast to enhance physical security while improving day-to-day communications through advanced alerting, bell schedules, and pre-recorded and scheduled announcements. For example, at 8:30 each morning, the Pledge of Allegiance is broadcast to all schools with a patriotic color palette appearing on the IPX endpoints. LED blinker “We needed to implement a solution that would serve the needs of all the students, including those with visual or audio impairments,” said Mara. “That's why having the LED blinker and the message crawler was essential. That solved the issues regarding accessibility for our students and staff to ensure they got the message(s) every time.” Network-wide communication For campus exteriors, NIC Partners chose the IP-HVP speaker from AtlasIED For campus exteriors, NIC Partners chose the IP-HVP speaker from AtlasIED. The IP-HVP is a vandal-proof, IP45 weather-resistant, wall-mount IP speaker well-suited for environments where network-wide communication is desired, and high output is required to overcome excessive ambient noise or large spaces. Almost 600 IP-HVP speakers were installed district-wide. Additionally, the Power over Ethernet (PoE+)-enabled IPX endpoints connect through the same IT network the school uses to deliver Internet access. InformaCast mass communications software The platform simplifies the installation process for integrators and reduces the need to introduce multiple cable types to a project. The IPX platform also offers scalability benefits, allowing schools the flexibility to expand their systems as the district’s communications evolve. The IPX Series also helped Torrance USD incorporate new and expanded campus safety capabilities with the help of InformaCast mass communications software. IPX LCD screens Torrance USD is trying out various color combinations on the IPX LCD screens to indicate alerts Using InformaCast, designated school personnel can initiate an alert from a mobile device wherever they are. The software then sends text messages to faculty, students, and parents' mobile devices, alerts law enforcement, and activates attention-grabbing audio alarms and LCD text messages on the installed IPX devices throughout the school or district. Currently, Torrance USD is trying out various color combinations on the IPX LCD screens to indicate different kinds of alerts, including earthquakes, shelter-in-place, and all-clear messages. Intentional and Phased Deployment Leads To Consistent Use NIC Partners started with the smallest school to establish best practices for implementation. Once the first school was completed and future implementation methods documented, NIC Partners went full-on with the remaining schools, working second shift during the school year and completing all the upgrades district-wide in less than five months. The communication system is in the final phase of upgrading all the schools to InformaCast Fusion servers and upgrading Cisco Call Manager to Webex calling. These updates will allow select school and district staff members to make emergency announcements or push out notifications directly from their cell phones. NIC Partners and AtlasIED Staff and students appreciate the audio upgrades, albeit for different reasons. Teachers are relieved by the improved audio clarity, as they can finally hear things “loud and clear,” and emergency alerts include visual messaging. Students love the music played at the end of each period to indicate a class transition. “Before the upgrades, you couldn't make a good page,” said Mara. “Now, the audio clarity is way better. We’re delighted with the IPX products and even happier to have NIC Partners and AtlasIED as our partners for such a huge undertaking. We wouldn't have been successful without their help.”
HID, the worldwide pioneer in trusted identity solutions, announces that the University of Dundee is updating its city campus estate implementing HID® Mobile Access® and signature HID Signo™ readers throughout its buildings to guarantee it has a modern, secure and reliable access control system to allow staff and students to enter using both RFID cards and smartphones. The project will involve buying and installing new mobile-ready HID Signo readers at around 40 buildings – a staged rollout being completed over a two-year period by specialist security installer, Scottish Communications Group. HID Mobile Access licenses University has purchased 10,000 HID Mobile Access licenses to offer its academic community In addition, the University has purchased 10,000 HID Mobile Access licenses to offer its academic community the option to use their Apple and Android smartphones for touchless entry into its facilities. “We wanted a modern system which is safe, secure and easy for everyone to use,” says Colin Stebbing, the University’s Head of Precinct Services. HID solution: future-proof equipment Stebbing added: “Complying with forthcoming legislation was also another important project requirement. With bills like Martyn’s Law soon to be enacted, ensuring the University is ready for this was important given that we have a duty to protect to ensure everyone is safe." "The HID solution enables us to not only lock down buildings immediately, but it has built-in functionality which we can leverage over time, meaning we’ve invested in ‘future proof’ equipment which will last us long term.” Ambitious development plans University of Dundee is a research institute in Scotland, noted for its academic merit in dentistry The University of Dundee is a public research university in Scotland renowned for its academic excellence in dentistry, medicine, science and engineering, and life sciences. Based in the heart of the city, it is home to over 16,000 students, 3,300 staff and is ranked 33rd in the Sunday Times Good University Guide 2024. A thriving institution with ambitious development plans, it is currently building a new £40 million facility called the Innovation Hub. This will offer commercial organizations flexible laboratory, meeting and office space and, over the next 10 years, it is anticipated the Hub will help create up to 280 new high-quality jobs. New HID Signo readers The new HID Signo readers integrate with the University’s existing AEOS access control software from Nedap. Supporting both native Bluetooth® and Near Field Communication (NFC) connectivity, they allow touchless smartphone entry and are fast to install as the wiring uses common protocols like OSDP (Open Supervised Device Protocol) and Wiegand. Furthermore, existing access cards already in circulation can be used with the new HID Signo readers, thereby speeding up the rollout. RFID cards access buildings The university used to print and issue plastic RFID cards so staff and students could access buildings Historically, the University used to print and issue plastic RFID cards so staff and students could access buildings. This process was laborious and time-consuming, especially during peak times like Freshers Week, when some 2,500 – 3,000 undergraduate and postgraduate students enroll. Issuing cards was logistically complex due to the high demand and the need for thorough identity checks, which could take up to 10 minutes per card. HID Origo management software Shifting to HID Mobile Access – which utilizes cloud-based HID Origo management software integrating with the AEOS system – completely changes this and delivers wireless credentialing. This significantly simplifies all the licensing, allocation of credentials, setting of building access rights, validating or revoking of IDs – all of which is now done virtually and remotely. Improve the mobile credential “Once registered by Student Services in AEOS, a student simply gets an email to their phone, they tap on a link, the app automatically uploads and a mobile credential is granted,” says Paul Brady, HID’s End User Business Manager for Physical Access Control Solutions. “Not only does this improve the overall student experience because it’s substantially quicker and more efficient, but it’s far more sustainable as you’re not issuing PVC cards anymore.” Integrate with digital campus cards While the strategy and aspiration are for the university population to shift wholesale to mobile access While the strategy and aspiration are for the university population to shift wholesale to mobile access, its approach now is to operate a dual system. “We recognize that some visitors and staff still want to use a physical pass and not all employees have a university-issued mobile credential,” explains Stebbing. “HID Signo readers allow us to run both credential types in tandem, with HID Mobile Access giving us the option to scale up to include digital wallets from Apple and Google, as well as integrate with digital campus cards should we decide to go down this route in the future.” FARGO range of ID card printers Given that RFID cards are still required now, the University of Dundee utilizes its reliable FARGO DTC4500e printers to back up this transition to digital transformation. The FARGO range of ID card printers integrates easily with the AEOS software so that Student Services staff can easily issue physical IDs themselves. HID’s reputation University of Dundee utilizes its FARGO DTC4500e printers to back up this shift to digital change “HID Signo readers are going in now across the main buildings, including the new Innovation Hub site,” says Stuart Leslie, Scottish Communications Group’s director. “HID’s reputation is built on reliability and security with its solutions supporting the latest encryption, communications and authentication standards. Their devices have an open architecture so they’re easy to install and integrate which reduces the cost for the university and makes time to value that much quicker.” MOTORTRBO Ion smart radios In addition, Scottish Communication Group is supplying Motorola MOTORTRBO Ion smart radios to the University’s security staff. The radios will be configured to run HID Mobile Access so they can open doors fitted with the new HID Signo readers. Because these smart radios also link to the University’s CCTV, alarm systems and CriticalArc Safezone® App, security staff need carry only a single device to fulfill their duties.


Round table discussion
College campuses are meant to be places of learning, growth, and community. Fostering such an environment requires the deployment of policies and technologies that ensure safety and security. Considering the growing role of security technology in the higher education market, we asked this week’s Expert Panel Roundtable: What are the new applications for security technology in the college and university markets?
There is safety in numbers, or so the expression goes. Generally speaking, several employees working together tend to be safer than a single employee working alone. Even so, some environments require that workers complete their jobs alone, thus presenting a unique combination of security vulnerabilities. The U.S. Occupational Safety and Health Administration (OSHA) defines a lone worker as “an employee working alone, such as in a confined space or isolated location.” We asked this week’s Expert Panel Roundtable: How can security technologies help to protect "lone workers?"
Headlines of violence in our schools are a reminder of the need to keep educational institutions safe. In fact, if there is a positive aspect to the constant bombardment of headlines, it is that it keeps our attention perpetually focused on how to improve school security. But what is the role of physical security systems? As the new school year begins, we asked this week’s Expert Panel Roundtable: Are schools safer because of physical security systems? Why or why not?
Products