Hybrid surveillance systems
Genetec Inc., the pioneer in enterprise physical security software, has announced the dates for its annual empower360 roadshow. Scheduled to take place in Saudi Arabia on 14th April and in the UAE on 17th April, the partner-focused event will bring together industry professionals to explore the evolving role of physical security in the Middle East region. Adaptable deployment models According to the Genetec State of Physical Security Report 2025, 66% of physical security consultants and...
Hanwha Vision, a pioneer in security and surveillance solutions, introduces the TNO-A26081, an ultra-high-resolution AI-powered camera designed to deliver unmatched imaging clarity and powerful analytical capabilities. With 26MP resolution at 30 frames per second, this camera captures every detail, making it ideal for large-area surveillance and high-security environments. Furthermore, its AI features ensure precise object detection, improved operational efficiency, and seamless integration in...
Secutech Thailand opens at the Bangkok International Trade & Exhibition Center (BITEC), showcasing the latest advancements in security and fire safety and building solutions. The event features a concurrent Fire & Safety event and co-located Building and Architect Thailand, enhancing the exploration of integrated safety and design innovations. Adoption of approaches Visitors have extensive networking opportunities at and beyond exhibitors’ booths With 200 exhibitors from 14 cou...
Axis Communications, a pioneer in network video, has launched two new developments within the AXIS Camera Station (ACS) ecosystem: AXIS Camera Station Edge (ACS Edge) and AXIS Camera Station Cloud Storage. Both are designed to transform network video management through cutting-edge cloud capabilities. From now, these new solutions will join the AXIS Camera Station suite of products, reinforcing Axis’s commitment to delivering secure, scalable, and flexible solutions. Solution with ACS Ed...
The new IDIS Lite Series, including ruggedized IP67 and IK10-rated NDAA-compliant cameras—turrets, domes, and bullets—is a cost-effective video surveillance option for small to mid-size applications. The IDIS Lite Series includes a range of 2MP and 5MP cameras equipped with lenses that enable clear identification right from the center to the edge of every scene. Value surveillance solution IDIS is offering the new range as a value surveillance solution that benefits systems...
Anviz, together with its key partner Solotec, participated in the 30th ESS+ International Security Fair, the most international and comprehensive security fair in Latin America, Central & South America, and the Caribbean, with exhibitors from 20 countries and regions around the world, attracting nearly 20,000 professionals from all sectors of the industry. In this exhibition, Anviz focused on the popular and innovative products of smart biometric access control and time & attendance so...
News
ThinCats, the alternative finance provider to mid-sized SMEs has supported Ranger Fire and Security with their latest acquisition of fire door business, Fire Door Specialists Ltd (FDS). First acquisition Ranger, which launched in February 2024, has already acquired four other businesses following Transitional Capital from ThinCats and private equity backing from Hyperion Capital – all in the active fire space – AFIL Ltd, Ignis Fire Protection Ltd, Syncro Group Ltd and IPH Fire Solutions Ltd. This is Ranger’s first acquisition in the passive fire safety space, broadening out the Group’s offering beyond active fire safety. Fire door compliance Ian will join the senior leadership team at Ranger Fire and Security, supporting the Group’s growth Based in Nottinghamshire, but offering national coverage, FDS provides comprehensive fire door compliance, including building inspections, fire door maintenance, and installation. FDS boasts a wealth of experience equating to more than 150 years in the fire and safety industry. Led by Operations Director Ian Maciejewski, FDS has expanded rapidly over the past few years, with the company broadening its services to cater to all types of buildings, student accommodation, schools, factories, and offices. Ian will join the Ranger Fire and Security senior leadership team, supporting the Group’s growth over the coming years. Inspections and maintenance Ranger evaluated numerous fire door companies before identifying FDS as the passive fire business that best met its stringent criteria and guardrails, including employing skilled engineers, delivering high-quality service, and consistently showing strong growth in its inspections and maintenance services. It also has an existing long-standing, reputable client base, including the NHS and Ministry of Defense. One-stop solution FDS will benefit from the Group’s scale, technology, and broader services, which will enhance its customer offering The acquisition of FDS is a key part of Ranger’s aim to provide quality service for its clients and a comprehensive one-stop solution by offering all fire and security services under one umbrella. FDS will benefit from the Group’s scale, technology, and broader services, enhancing its customer offering. While Ranger’s longer-term strategy continues to be actively fire-focused, the acquisition of FDS complements the Group’s existing service propositions and enhances its customer experience. Funding for the acquisition was provided by ThinCats. New and key service Stuart Thompson, Head of Transitional Capital, ThinCats, “We're delighted to be supporting Ranger with another acquisition. Mark and his team continue to expand their services and are fast becoming a national player in the industry.” Mark Bridges, CEO of Ranger Fire and Security, said, “Fire Door Specialists is a well-known, respected business in the passive fire space that will add a new and key service to the Ranger Group. This acquisition marks another milestone for Ranger in our journey to provide the highest quality, complete service offering and opens up significant cross-selling opportunities." Maintenance-focused business offering “We are excited to welcome Ian and his team to the Group. As we continue to grow, Ranger remains a dynamic, maintenance-focused business offering a turnkey solution for all fire and security services across the UK and Ireland.” Ian Maciejewski, Operations Director at Fire Door Specialists, said, "Our decision to partner with Ranger was an easy one – it’s a company I have admired since its launch and presents huge opportunities for our business." High-quality service Ranger to enhance its offering in all key areas of fire and security services, such as fire detection and alarms “Ranger is the best partner for us going forward given our shared focus on providing a high-quality service for customers, and I look forward to working closely with Mark and the team to grow Fire Door Specialists while enhancing our systems and insights, fostering collaboration and exploring new avenues of growth." The announcement builds on Ranger Fire and Security’s previous acquisitions of AFIL, Ignis Fire Protection Ltd, Syncro Group Ltd, and IPH Fire Solutions Ltd, which together have helped Ranger to enhance its offering in all key areas of fire and security services, such as fire detection and alarms, extinguisher maintenance, suppression, and security services. Fire and safety solution provider Since launching in 2024, with backing from the private investment firm Hyperion Equity Partners, and Transitional Capital from ThinCats, Ranger has embarked on a mission to establish itself as the pioneering one-stop solution provider in the fire and safety sector, offering a comprehensive range of services through both regional and national operations, and providing a seamless customer experience.
Digital Projection is debuting an all-new video wall designed exclusively for residential applications at CEDIA Expo 2024. Systems integrators can now offer their high-end clientele an exciting imaging solution that brings large-scale visuals to life. Featuring 4K resolution, HDR support, REC 2020 color space, high contrast, Wi-Fi connectivity, and seamless integration with third-party control systems, Digital Projection’s groundbreaking Radiance Home LED Video Wall delivers exceptional video performance along with all the advantages of a cutting-edge home entertainment system. New Radiance Home video Systems integrators can see Digital Projection’s Radiance Home video wall at CEDIA Expo 2024 As always, Digital Projection provides its white-glove design and installation service, enabling dealers to execute Radiance Home projects with confidence and efficiency. Systems integrators can see Digital Projection’s Radiance Home video wall at CEDIA Expo 2024, Booth #2108. At CEDIA Expo 2024, Digital Projection broadens its micro and dvLED video wall offerings with the introduction of a line designed exclusively for residential applications. The new Radiance Home video wall gives Digital Projection dealers a compelling new large-scale imaging solution to offer their luxury home clients. Demand for video walls “LED video walls have long been a staple of commercial projects, but are relative newcomers in residential spaces. That’s because most solutions have been designed specifically for commercial environments,” says Digital Projection Senior Executive, George Walter. He adds, “Demand for video walls optimized for home environments is escalating at an incredible rate, so we took the initiative this year to develop one of the first video walls engineered and designed exclusively for residential applications.” Cutting-edge design and technology Radiance Home incorporates cutting-edge design and technology to streamline deployment Purpose-built for high-end home applications, Radiance Home incorporates cutting-edge design and technology to streamline deployment, support common residential applications, and meet the imaging demands of discerning residential clientele. Built into this revolutionary LED video wall are technologies and controllers to enable fast configuration of user-defined presets, Wi-Fi connectivity and integration with third-party control systems. Support of HDR (high dynamic range), 4K resolution, and REC 2020 Color Space along with a special optical coating for higher contrast optimizes the image quality. Digital Projection’s design Whether an AV integrator is specifying an LED video wall for a high-end home theater or a projection system for a multi-purpose media space, Digital Projection has the right products for the application, backed by legendary dealer service and support. Through Digital Projection’s white-glove design and installation service, systems integrators can tackle even the most complex residential projects quickly and confidently.
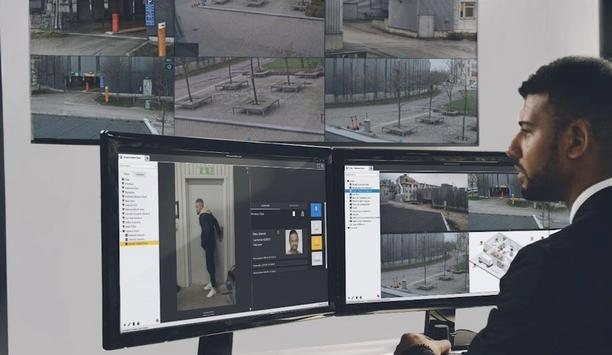
Integrating 3xLOGIC’s INFINIAS Access Control and VIGIL Video Management solutions allows them to easily monitor security events in real-time. This combination offers a comprehensive security system and allows them to monitor and manage access seamlessly. Real-time monitoring One of the standout benefits of integrating VIGIL Video with INFINIAS access control is the real-time monitoring of events. Security personnel can view video footage from any door event or alarm as it happens, allowing for swift and effective responses to any incidents. View Live Video: Keep an eye on ongoing activities directly from the mobile app or browser. Instant Event Playback: Easily review and analyze incidents by playing back clips from past events. Push Notifications: Get instant alerts on the mobile device for access events or security breaches. Email Alerts: Receive images captured by the door camera via email from any event trigger. Security management with INFINIAS Cloud + VIGIL The INFINIAS Cloud platform, when paired with VIGIL Video integration, takes security management to the next level. It offers automatic software updates and provides remote access to the system, adding significant value to the security infrastructure. Automatic Software Updates: They handle updates for them, ensuring the system is always current without the hassle of on-site server maintenance. Additional Features at No Extra Cost: Unlock new software features without additional charges. RMR Revenue: Enable Recurring Monthly Revenue through continuous service agreements. Remote Access: Manage the system from anywhere, providing flexibility for them and their customers. Mobile app benefits Integrating VIGIL Video into INFINIAS mobile apps significantly enhances functionality and user experience, making security management more accessible and efficient. Live or Playback Video: Instantly access live feeds or review recorded footage. Unlock/Lock Doors: Control door access directly from the app. User Management: Easily add or remove users on the go. Push Notifications: Stay updated with real-time notifications about security events. Comprehensive solutions for various industries INFINIAS and VIGIL provide versatile security solutions suitable for multiple industries, ensuring that a wide variety of businesses can benefit from advanced access control and video monitoring. Integrating INFINIAS access control with VIGIL Video offers a robust, user-friendly, and cost-effective security solution. This integration provides real-time monitoring, simplified management, and enhanced functionality, ensuring flexibility and peace of mind for them and their customers. Embrace the future of security with this powerful combination and experience the ultimate in access control and video integration.
As the anticipation builds for the 2024 Paris Olympics, security concerns are heightened. While this long-awaited event will showcase the world’s most accomplished athletes, the safety of all participants and spectators is paramount. Extensive preparations have been underway to achieve this crucial goal. Security challenges The threat landscape in the historical context The security challenges facing the Paris Olympics are underscored by ongoing global conflict, an ever-evolving threat spectrum and a broad concern over the vulnerability of large gatherings to potential risks. Throughout history, the Olympic Games have unfortunately been a prime target for hostile actors. Throughout history, the Olympic Games have unfortunately been a prime target for hostile actors One of the most notable incidents occurred during the Munich Olympics in 1972, where the Israeli team suffered a tragic terrorist attack, resulting in the deaths of 11 athletes and coaches. The Atlanta Olympics in 1996 was the target of a bombing attack that claimed two lives and injured more than 100 people. This incident prompted a reassessment of security protocols and the adoption of stricter measures to protect athletes, spectators, and infrastructure. The Rio Olympics in 2016 faced challenges related to crime and civil unrest in the host city, requiring extensive security measures to ensure the safety of participants and visitors. Few key areas These global, center-stage incidents are a stark reminder that when it comes to venue security, nothing is more important than a comprehensive and layered risk mitigation program. Let’s look more closely at a few key areas to consider. Comprehensive Training: Many organizations fail to recognize the importance of ongoing training for personnel. From security officers to venue staff to volunteers, thousands of individuals involved in event operations must be trained in awareness, escalation, and response. Depending on the role, training might include emergency response procedures, crowd management techniques, or surveillance systems. Security Camera Monitoring: In the 2017 suicide bombing at the U.K.’s Manchester Arena, the attacker hid in a CCTV blind spot after carefully identifying the location from repeated reconnaissance trips. When planning large venue attacks, terrorists frequently conduct pre-operational surveillance to locate areas of security weakness and vulnerability. Thorough and diligent reviews of security camera footage are essential in the months leading up to high-profile events. Checkpoint Explosive Screening: Large-scale public events require many access points to ease guest entry and exit. Unfortunately, this creates access opportunities for hostile actors. X-ray screening at venue checkpoints is critical for the deterrence and detection of improvized explosive devices (IED), firearms, and weapons. Rigorous screening very often dissuades a perpetrator from attempting to enter areas with a greater concentration of people and a detonation would have a larger impact. Explosive Detection Canines: Detection canines offer an effective, efficient, and flexible solution for explosive and weapons detection at high-volume facilities. Canine teams sweep large areas and crowds for trace amounts of these odors in a short time with little to no operational or public disruption. Their presence alone serves as a strong prevention measure. Challenges and contingency planning These are just four of the many layers recommended for an effective security plan. While significant enhancements have been made in security preparations for large-scale public events over the decades, challenges persist. Security professionals must respond to the dynamic nature of the threat with flexibility. They must merge the lessons learned from past incidents with innovative solutions to protect people, property, and brands. As the world eagerly anticipates the Paris Olympics, the organizers' steadfast commitment to safety ensures that athletes, spectators, and staff can focus on the thrill of competition in a secure environment. To learn more about event security, speak with an Allied Universal subject matter expert.
Ajax Systems is proud to announce its victory at the PSI Premier Awards 2024. The company's KeyPad TouchScreen Jeweller device has been named the winner in the Access Control Product of the Year category. The PSI Premier Awards, organized annually by PSI Magazine, a top professional security media outlet in the UK, celebrate the pioneering technologies and businesses in the security sector. Winners are selected by security installers and systems integrators through votes on the PSI website. DESFire® technology and BLE support Device offers intuitive group management, a familiar Ajax app-like interface, and top-of-the-line security powers “We are excited to be named the winner of the PSI Premier Awards once again! The UK is one of our biggest markets, where Ajax company is making significant progress. The knowledge and expertise of UK security specialists have been invaluable to us, and we are immensely grateful to them for their support and today’s victory,” Valentine Hrytsenko, CMO at Ajax Systems. KeyPad TouchScreen Jeweller is a wireless keypad with a touch screen that seamlessly merges security and smart home device management. Its high-resolution display features all necessary controls, providing users with a visually stunning and high-quality image. The device offers intuitive group management, a familiar Ajax app-like interface, and top-of-the-line security capabilities, such as DESFire® technology and BLE support, which make it possible to control the keypad via smartphone using the Ajax app. PSI Magazine readers This is the fourth award that Ajax Systems has received from the British professional security community. Last year, the Ajax Academy project was recognized at the PSI Premier Awards as the “Manufacturer Training Program of the Year.” In 2020, PSI Magazine readers selected MotionCam, Ajax’s indoor motion detector with photo verification, as the “Intruder Product of the Year.” Prior to that, in 2017, Ajax was named “Intruder Alarm of the Year” at IFSEC International, a pioneering integrated security event in London.
SailPoint Technologies, Inc., a pioneer in unified identity security for enterprises, unveiled a series of new features and capabilities in its Data Access Security and Non-Employee Risk Management offerings within SailPoint Identity Security Cloud. Updates to these add-on capabilities offer customers increased visibility and security across all varieties of identity types and their access to critical data, enabling a strong enterprise-class identity security program. Data Access Security Designed as a cloud-native solution on the Atlas platform, SailPoint Data Access Security provides customers with holistic visibility of access to unstructured data such as text files, presentations, IOT logs, PDFs, and more. SailPoint continues to expand its Data Access Security capabilities with integrated data access certification, activity monitoring, and sensitive and regulated data classification. With new resources at their fingertips, customers gain improved visibility and deeper context on critical data to help secure sensitive information as a core component of their identity security program. Updates include Organizations can review and certify access to sensitive, regulated, and critical data. These expanded certification capabilities help organizations easily identify over-provisioned access, meet complex compliance requirements and regulations, and ensure that only authorized users can access critical data – all while proactively managing secure access. Activity Monitoring: New activity monitoring capabilities enable organizations to track and analyze activities taking place on data assets in real time, giving security teams improved visibility along with the tools they need to identify anomalous activity. Organizations can monitor activities and better inform governance decisions to minimize risky access and holistically reduce their attack surface. Sensitive and Regulated Data Classification: Customers can leverage out-of-the-box data classification policies and predefined classification rules within their environment to automatically classify and catalog regulated and sensitive data. This includes personally identifiable information (PII), payment card information (PCI), medical records regulated under HIPAA, and information covered under data protection laws like GDPR. Organizations can also catalog content based on internal identifiers and dynamic policies to secure intellectual property, parented information, and classified restricted content. Non-Employee Risk Management Non-Employee Risk Management enables customers to better manage identities and access for third-party non-employees SailPoint Non-Employee Risk Management enables customers to better manage identities and access for third-party non-employees, an emerging threat vector for enterprises. New updates drive better time-to-value and productivity for customers, helping to rapidly establish configurations for common non-employee identity types. Updates include Non-Employee Risk Management QuickStart Templates: Customers can use QuickStart templates, pre-configured setups, to address their non-employee onboarding, modifying, and offboarding identity requirements to drive efficiencies. Enterprises can instantly focus on managing non-employee identities effectively, enabling enterprises to reallocate critical IT resources. New Language Expansion: Non-Employee Risk Management offers additional language support for Traditional Chinese, Brazilian Portuguese, and Korean, providing additional global support for the non-employee identity solution. Improving security “SailPoint’s Non-Employee Risk Management solution has given us a single source of truth for a range of identities, from fixed-term contractors to machines,” said Evan Fraser, Enterprise Architect, Absa Bank Limited. “This complements our identity management processes for employees, streamlining onboarding and provisioning while also improving security.” Additional enhancements to SailPoint Identity Security Cloud Recent updates to SailPoint Identity Security Cloud help customers better manage and secure identities, with a keen focus on strengthening inactive identity management. New features include Management of Inactive Identities: Users can classify and define inactive identities via designated identity states within SailPoint Identity Security Cloud to better mitigate the risk of delivering access to the wrong identities. The new feature allows customers to designate identities “inactive” from select functionality in the product, improving user experience and performance. SailPoint expects customers will benefit by having an increasingly accurate view of their managed identities and better security in their solution. Account User Interface (UI) Improvements: SailPoint has a redesigned Identity UI to give users a scalable and comprehensive way to manage and access items through a single pane of glass. This compact and configurable new experience offers added capabilities, such as the attribute-copy tool, and is auditor-friendly, delivering an enhanced identity management experience to all customers. Enterprise-class solution “Enterprises need a holistic view into their vast and varied identity landscape and their complex access needs across every application, and the data within those apps,” said Grady Summers, EVP, Product, SailPoint. "These new Data Access Security and Non-Employee Risk Management updates further underscore our continued commitment to supporting our customers with an accelerated, enterprise-class solution, driven by the strong and dynamic governance needed to help safeguard every type of enterprise identity.” Availability All capabilities will be available to current customers this month (June 2024).


Expert commentary
The autumn equinox, which marks the start of autumn, occurs this weekend on Saturday, September 23. With darker evenings ahead, the experts at ADT have shared five ways to maximize your home's security. Author's quote Michele Bennett, General Manager at ADT UK&I comments: “Opportunistic thieves use darkness to their advantage, so it’s no surprise that the number of burglaries committed increases when the darker nights draw in." He adds, "Our 2022 burglary report found that burglaries are most common at night, with 58% of burglaries occurring between 6 p.m. and 6 a.m. Taking steps to optimize your home’s security before the clocks go back this year will provide reassurance that your property is as secure as possible.” Five ways to secure your property: Get a monitored alarm installed: A visible alarm system is a strong deterrent to potential burglars, as criminals are less likely to target a home that is protected. In the event of a break-in, a monitored alarm will alert you, your keyholders and depending on the package you take out, the police, ensuring a swift response to an alarm activation. Light up the dark: Well-lit exteriors make your home less appealing to potential intruders. Install motion-activated lights around any entry points, particularly porches and gardens, which alert you to movement on your property. This will also prevent burglars from operating under the cloak of darkness and increase the chance of a passerby spotting suspicious activity. Trim your garden landscape: Thieves look for escape routes and hiding spots when deciding which homes to break into, making gardens with high, overgrown hedges more likely to be targeted. This is especially true in the darker evenings, so be sure to give your garden a thorough tidy-up to make your property less likely to be targeted. It’s also advisable to ensure any tools are locked away in sheds and garages that could assist a burglar such as ladders, or a garden spade to force entry. Be smart with your lights: Using smart plugs allows you to turn on a few well-appointed lights and radios or televisions from any location from your phone. Used in conjunction with an outdoor camera or video doorbell, you can have lamps plugged into smart plugs come on when motion is detected. Programming lights to come on at different times throughout the night will help to deter burglars by making your property look occupied. Purchase a smart doorbell or outdoor camera: Smart doorbells are an effective way to deter burglars as they provide evidence in the event of a break-in, package theft, or other suspicious activity around your home. They also notify you when someone is at your door reducing the chance of you being caught out by a late evening or early morning robbery. Further encroachment Smart doorbells also act as a deterrent to unscrupulous door-to-door sellers and con artists, as video footage is recorded. In the event of a late-night door knock, you can see and speak to whoever is at your front door, without having to open the door. ADT’s new outdoor camera also has two-way audio and a high-pitch deterrent siren so you can warn off anyone from your property to deter any further encroachment.
GSX 2023 marks a poignant moment for the security industry as an increasingly complex risk landscape converges with the acceleration of technology innovation. Emerging from this environment are three key trends that will dominate the conference and the future of the security industry: (i) the adoption of AI, (ii) the use of predictive analytics, and (iii) a hybrid global and local risk management approach. As Chief Security Officer of Crisis24, a GardaWorld company, I regularly advise clients on how these trends are evolving and impacting their security and risk management approach. Here’s how we can expect to see them discussed at the show next month: Trend 1: Artificial intelligence is the new industry standard. AI is this year's buzzword. While AI is not new to the industry, this year it has become a standard to operate with AI being adopted or expanded more ubiquitously. Legacy AI-enhanced security offerings that have been years in the making are becoming more advanced and are being integrated into expert analyst teams to leverage the best of both man and machine. Limitations AI augments the data processing ability; however, human-led intelligence is still necessary AI can generate unparalleled levels of data and insights, but it also has its limitations. AI does not have the emotional intelligence that can influence decision-making. For instance, our Crisis24 analyst teams know that every one of the intelligence alerts they provide to leadership may save a life or protect a business. AI augments the data processing ability; however, human-led intelligence is still necessary to effectively elevate knowledge of those threats through an organization to incite action. Trend 2: Predictive analytics powered by AI will transform security operations. Predictive analytics enabled by AI will allow for more precise planning and execution of true emergency management. Those living or operating in conflict zones must be ready to spring into action and predictive analytics can help better evaluate risks, threat levels, and the probability of certain events. When I served in Iraq in 2003, our greatest challenge was operating in an unpredictable environment and navigating the many unknown threats. With these large-scale threats, it was difficult to account for the vast array of variables involved and ensure that all parties were protected. Broad and instant visibility Predictive analytics provides broad and instant visibility into numerous potential outcomes, impacts, and mitigation strategies for a wide variety of threats. When dealing with risks that are constantly evolving and quickly accelerating, the insights from predictive analytics can have a direct impact on risk management, mitigation strategies, and preparedness levels. Predictive analytics can anticipate the ripple effect that threats can have on organizations, their people, and their assets and enable security teams to plan. Trend 3: Risk mitigation is increasingly both global and hyper-local. A company’s workforce is often scattered across the country or the world, working from home or on the go Remote work and a flood of 24/7 data sources have driven demand for timely, accurate, and hyper-local intelligence. Where before an organization may have had a handful of facilities around the world where its employees gathered, now a company’s workforce is often scattered across the country or the world, working from home or on the go. Preventive mitigation steps To keep their people and assets safe, business pioneers need to know what’s happening in all corners of the globe, while also easily accessing details on what is happening at the street corner level. How a business takes care of its people, including anticipating risks and taking preventive mitigation steps as well as responding quickly in the face of threats, can directly affect its reputation. Every company is in the business of safety and security when it comes to looking after its people on a global, national, and increasingly hyper-local scale.
Daniel May of Consort reviews the integration of access control systems in healthcare settings, outlining the benefits and key considerations decision-makers must make throughout product specifications. From patient safety and traversal to the protection of sensitive data and pharmaceuticals, healthcare environments are faced with several operational challenges. And where security remains at the forefront of decision-making, modern access control systems may often hold the answers. Physical security systems Hospitals in particular have developed into multi-faceted spaces that house hundreds to thousands of patients, staff, and visitors at any one time. In England for example, research has found in the three months leading to June 2023, an average of 44,626 people visited major hospital A&E departments each day, with over 16 million attendances typically recorded over the course of a year-not to mention an additional nine million logged at other minor units. For any building, this level of sustained footfall can request severe security difficulties For any building, this level of sustained footfall can invite severe security tests. With that, the need to deploy effective physical security systems in healthcare is clear. And so, as access control continues to become more readily adopted and new products enter the market, decision-makers are reminded to consider the requirements of their building, ensuring they select the solutions most suited to their settings and budget. Security controlled Patient safety will always remain the top priority in healthcare settings, and where matters of health and social care come into question, a diverse set of professional regulatory bodies are tasked with setting and maintaining high standards. When it comes to healthcare premises specifically, patient security and perimeter security often come hand in hand and are amongst the most pressing of challenges that decision-makers must face. To help address operational planning and potential design concerns in the NHS, the Health Building Note (HBN), provides general design guidance for healthcare buildings under HBN 00-01-citing the use of access control measures as a way of maintaining security and protecting the safety of patients, staff, and visitors. Use of access control Hospital buildings control varied levels of access for a number of security purposes Hospital buildings, for example, must control varied levels of access for a number of operational and security purposes. Routine scenarios exist where vulnerable patients are under monitoring and thus refrained from exiting the premises for their own safety, while at the same time, permitted staff must be able to reach their patients and medicines when required. For this, the use of access control is key. Equally, access credentials can also help management teams keep track of those who may be entering or exiting rooms with equipment and pharmaceutical supplies, deterring any unwanted visitors and opportunists in the process. Incorporation of access control systems On a similar note, regulations have set a minimum standard for how personal data should be stored and managed in healthcare environments, giving decision-makers an added responsibility to regulate staff-controlled areas with patient medical records. While instances of personal data breaches are rare, healthcare facilities and professionals are at legal risk should confidential data be found misused or missing. As such, the incorporation of access control systems has become essential in keeping data storage areas secure, with intuitive online systems capable of permitting access to staff with the correct credentials while simultaneously tracking who has requested clearance at digital entry points. HBN guidance Healthcare experts are better fitted to control the sheer volume of people entering and exiting To function effectively, healthcare facilities must always be perceived as safe places by the people who reside within them, and as HBN guidance implies, a unified physical security system can help address key safety and security concerns while enhancing patient and staff experience. Opportunely, access control systems are more accessible and adaptable than ever and combine several technologies such as mechanical locks and automatic doors with electronic access credentials in the form of smartphone apps, badge readers, and biometric scanners. By integrating these systems into the building’s existing infrastructure, healthcare professionals are better equipped to control the sheer volume of people entering and exiting the premises without impairing the general flow of movement and coordination around the facility. Better by design Despite the clear benefits offered to healthcare facilities, there are a number of considerations to be mindful of when choosing an access control solution. Poorly implemented systems can have an adverse effect on security and functionality - quickly costing healthcare organizations time and budget to rectify and replace the inadequate products that don’t meet the building’s requirements. For that reason, decision-makers and design teams are reminded that there is no single solution that fits all healthcare buildings. As such, it’s crucial for decision-makers to understand the systems that are being put in place throughout each of the touchpoints in their facility. Clear collaboration is required during periods of specification, where together, teams can ensure the selected product works on all angles, from meeting fire safety and sustainability standards to aesthetics and scalability. Modern access control products Scalability is a key area that decision-makers must review when selecting access control systemsFrequently overlooked, scalability is a key area that decision-makers must review when selecting access control systems. Such is their diverse nature; healthcare facilities can often change and develop as years go by, and by selecting a system that facilitates growth, such as a cloud-based solution-security and efficiency is long-established. While modern access control products are known for seamless integration, there are some systems that may restrict the ability to use different vendors throughout the remainder of the building’s infrastructure. This, in effect, causes a monopolization of products throughout the estate, which can have an adverse effect on growth by increasing costs and reducing the levels of service associated with the security system already in place. Improve security and safety A scalable and reliable access control system will continue to improve security and safety by adapting to a building’s new requirements-and all while having minimal impact on its operational network. And so, while technology will no doubt continue to influence and transform the access control market, healthcare facilities and their professionals must continue to remain educated on their own systems, ensuring they have the best options in place to keep their patients, staff, and visitors safe and secure for years to come.
Security beat
IFSEC International took place over three days at the ExCel in London, presented alongside shows covering fire safety, intelligent buildings, facilities management, and safety and health. While perhaps not on the same scale as pre-pandemic events, the atmosphere was convivial and spirits high, everyone glad to be back amongst their peers in the industry. Predictably, the trending topics were steered by issues in the wider world: sustainability, moving services to a subscription-based model, and new ways of working inspired by COVID-19 safety measures. A place for cutting-edge innovation After a challenging couple of years, companies were keen to meet customers, showcase their products and reveal the latest innovations. Integrated Design Limited displayed their new Glassgate 400 Plus turnstile, a sleek design for the corporate market. Tony Smith, Major Accounts and Marketing Manager, Entrance Control and Turnstile Security, told SourceSecurity.com, “I feel trade shows are a very important part of IDL’s marketing effort. We are more than pleased to display alongside our peers and have customers make direct comparisons with our products and theirs.” Biometric access reader Biometrics, as ever, generated a lot of interest, including the European launch of RealNetworks’ new SAFR SCAN biometric access reader, which combines facial recognition, computer vision, and image capture technologies for a range of applications. “Overall, there was a really good footfall, and we met an excellent mixture of end-customers, system integrators, distributors, and consultants from both Europe and the Middle East who are exactly the types of people we were hoping to demonstrate SAFR SCAN to,” commented Charlie Bennett, Vice President UK & Europe – SAFR, RealNetworks. Access control systems going green HID Global is one company leading the way in the move away from plastics to focus on mobile access The eco-friendly trend and the need to be more sustainable is becoming a real force in the security industry, particularly in access control where there is considerable pressure to ditch the plastic. HID Global is one company leading the way in the move away from plastics to focus on mobile access. Gerald Grattoni, Vice President, Physical Access Control Solutions Regional Business Unit Vice President at HID Global (part of the ASSA ABLOY Group), explained in a press briefing, “Making buildings smarter and more eco-conscious is high on the corporate responsibility agenda of many companies as the sustainability credentials of new buildings are now very important. With digitalized mobile identities there is less plastic waste and lower emissions.” Flexible, remote, and contactless Innovation in smart buildings is also being led by changes to how we work, live, and play, inspired in part by the recent pandemic. New technology is required to meet the needs of the hybrid workspace, as employers adopt more flexible working models and demand for contactless access control increases. Now, the most technologically sophisticated buildings are controlled by an app on a mobile phone, giving ease of access and full control without the need for plastic cards. Remote monitoring Advances in remote monitoring have escalated due to COVID-19, particularly in high demand in the health and education markets. Connecting via industrial standard network protocols allows for remote communication Ian Bridgewater, Director, Technical Sales Manager, TOA Corporation (UK) Ltd, explained further, “Connecting via industrial standard network protocols allows for remote communication. Working with specialist software developers has expanded this, giving greater flexibility to monitor and maintain systems remotely from a central hub.” AI-based autonomous access solution AI also has a role to play in this new high-tech, touchless world and various companies are utilizing this technology. Alcatraz AI found IFSEC the perfect opportunity to exhibit their new Rock autonomous access solution. "We now live in a time in which AI can make precise real-time decisions at the door to authenticate or deny access using your face as a credential,” said Greg Sarrail, Senior Vice President of Sales at Alcatraz AI. “IFSEC 2022 allowed Alcatraz AI to demonstrate the speed and accuracy of autonomous access control. The number of qualified partners and end-users representing a broad international scope in attendance at IFSEC was encouraging.” Meanwhile, the Eagle Eye Networks stand attracted a lot of visitors keen for a demo of their new Eagle Eye Smart Video Search, which allows users to search for people, vehicles, or objects, and immediately find the exact video across all cameras in all sites. "AI and cloud are two trends that Eagle Eye, the media, and the security business community have been talking about for a while. We were excited to showcase Eagle Eye's new AI-powered technologies at IFSEC 2022," added Rishi Lodhia, Eagle Eye Networks Vice President and Manager Director EMEA. "Our stand was buzzing with activity and AI was the main topic of discussion for all three days. All in all, a great show." Investing in a secure future Engineers of Tomorrow gave apprentice finalists the chance to show off their skills in front of thousands of peers and professionals from the security sectors live on the show floor. The winners will go on to the WorldSkills UK (WSUK) LIVE competition – the nation’s premier skills, apprenticeships, and careers event. Although the products on display at IFSEC promised a contactless, digital future, this was a good reminder of the importance of the people who install and maintain these systems and the vital role of engineering apprenticeships in the industry.
The mission of the North American Electric Reliability Corporation (NERC) is to ensure the reliability of the North American bulk power system (BPS). While electric utility companies are responsible for administering the day-to-day operations of the electric grid, regulators such as NERC and the Federal Energy Regulatory Commission (FERC) are charged with the overall responsibility of ensuring reliability and security. NERC develops and enforces Reliability Standards, annually assesses seasonal and long-term reliability, monitors the bulk power system through system awareness, operates the Electricity Information Sharing and Analysis Center (E-ISAC) and educates, trains and certifies industry personnel. Normal everyday operations of the system are the responsibility of utility owners and operators. Protecting critical infrastructure An attack by a disgruntled former employee, ideologically motivated activist, or a criminal could inflict significant damage Currently, a significant reliability threat to the U.S. grid is associated with squirrels and balloons, and not religiously inspired terrorists. However – and more applicable to grid operators – we have recently seen noteworthy interest in disabling or destroying critical infrastructure. Coordinated attacks can target the grid, and an attack by a disgruntled former employee, ideologically motivated activist, or a criminal stumbling across a “soft target,” could inflict significant damage. With an interconnected grid of over 450,000 miles of high voltage transmission lines (100 kV and higher) and over 55,000 substations (100 kV and larger), the targets of opportunity are endless. Data capture form to appear here! According to the Department of Energy, the number-one cause of most power outages in the U.S. is bad weather, which costs the economy between $18 billion and $33 billion every year in lost output and wages, spoiled inventory, delayed production and damage to grid infrastructure. The number-one cause of most power outages in the U.S. is bad weather, which costs the economy between $18 billion and $33 billion every year Large power transformers A large power transformer (LPT) is an enormous, custom-built piece of equipment tailored to customers’ specifications. They usually are not interchangeable with each other, and they are not produced for spare-part inventories; so if one blows, a lot of companies and homes could be without power for more than six months. They are not cheap, either. According to EEP (Electrical Engineering Portal), $10 million is a fairly average cost, but that doesn’t include transporting the gargantuan piece of equipment or installing it, which usually adds an additional 35 percent to the bill. Protecting power grids is essential to deliver electricity that serves millions of consumers. Transmission substations are a component of the power infrastructure that presents unique security challenges. These important facilities often sit out in the open, in remote locations, and were historically protected by little more than cameras or chain-link fences. According to EEP, $10 million is a fairly average cost for a large power transformer NERC/CIP guidelines The North American Electric Reliability Corporation’s Critical Infrastructure Protection (NERC/CIP) guidelines address security needs of electrical substations. Every facility has a baseline requirement for perimeter security protection around the site, although medium- and high-impact sites will have more stringent requirements. The geography surrounding sites – Is it an urban area or rural? Does the surrounding elevation provide additional lines of sight? – also impacts the types of systems they require. Electricity coming from coal, nuclear or hydroelectric plants goes to local utilities The U.S. power grid is divided into three sections: The Eastern Interconnection for states east of the Rocky Mountains, The Western Interconnection for states from the Pacific Ocean to the Rocky Mountains, and the smallest—the Texas Interconnected system—covering most of Texas. Electricity coming from coal, nuclear or hydroelectric plants goes to local utilities and they distribute power to homes and businesses, to millions of personal devices, lights, refrigeration, computers, and to other “loads,” that tap it. Inherited challenges According to the American Society of Civil Engineers (ASCE), the nation’s electric infrastructure is “nothing but a patchwork system” that has evolved wildly since the first substation was erected by Thomas Edison in 1882, on New York City’s Pearl Street. Contributing to the challenges of securing the grid are the crazily disparate ages and capacities of the grid’s equipment. There are many possible targets, too. Approximately 300 control centers around the country monitor voltage and watch the data from SCADA (supervisory control and data acquisition) systems, which are placed at transformers, generators and other critical areas. Ideally, this allows engineers to monitor the data for signs of trouble and then communicate with each other to deal with whatever is happening to the grid, but SCADA has cybersecurity issues.
Intelligent solutions, such as those derived from artificial intelligence, help critical infrastructure organizations make sense of vast amounts of data. These integrated applications, such as advanced video analytics and facial recognition, can automatically pinpoint potential breaches and significant events, and send alerts to the appropriate personnel, departments, and agencies. These solutions can be powerful in unifying disparate command center technologies, fusing critical data input from emergency calls and responder activity to enhance situational awareness. Electrical substations are particularly vulnerable (and in need of extra security) due to their role in power distribution and the nature of their equipment. The challenge power utilities worldwide are facing is finding an affordable solution, which can help detect, deter and facilitate an informed response to a substation security event. Data capture form to appear here! U.S. regulations In the United States, this need is furthered by the physical security mandate CIP-014 issued by the North American Electric Reliability Corporation (NERC), calling for identification of security issues, vulnerability assessments and deployment of appropriate processes and systems to address. CIP-014 identification of security issues, vulnerability assessments and deployment of appropriate processes and systems to address CIP-104 specifically calls for implemented security plans that include measures to deter, detect, delay, assess, communicate, coordinate and respond to potential physical threats and vulnerabilities. Manufacturers of video and other systems are designing products to serve the critical infrastructure market. For example, Dahua Technology offers explosion-proof cameras with a combination of rugged reliability and superior optics that is a fit for surveillance of explosive and corrosive environments, including chemical plants, refineries, and other facilities in the oil and gas industry. This explosion-proof series of cameras are housed in enclosures that are certified to the ATEX and IECEx standards for equipment in explosive atmospheres. Each explosion-proof camera features Dahua’s Starlight technology for ultra low-light sensitivity and high-definition sensors that deliver clear images in real-time. They are IP68-rated to prevent water and dust ingress. Each explosion-proof camera features Dahua’s Starlight technology for ultra low-light sensitivity and high-definition sensors that deliver clear images in real-time Video footage in extreme temperatures Another manufacturer, Videotec, offers a range of cameras and housings that provide video footage regardless of aggressive external factors, such as ice cold, scorching heat, desert sand, the force of sea or wind, total darkness, pollution, corrosion and even explosive agents. SightSensor thermal systems enable a utility to detect and respond to substation security incidents across multiple sitesSightLogix smart thermal camera systems have been deployed to protect substations for electric utilities and other critical infrastructure facilities. SightSensor thermal systems enable a utility to detect and respond to substation security incidents across multiple sites, ranging from copper theft to vandalism while also meeting regulatory compliance. At each substation facility, Thermal SightSensors are positioned along the perimeter, and are paired with a high-resolution pan-tilt-zoom camera for alarm assessment. When a Thermal SightSensor detects an intruder, the target’s location information is sent over the network to a SightTracker PTZ controller, which automatically zooms and steers PTZ cameras to follow the intruder. The target’s location is also displayed on a topology site map to provide real-time situational awareness. Alarms are sent to the utility’s 24-hour security operations center, which will contact law enforcement in real time when unauthorized intrusions are detected. Integrated intrusion detection and lighting systems The Senstar LM100 hybrid perimeter intrusion detection and intelligent lighting system is simplifying security at one U.S. electrical utility company. For years, the utility company had integrated its perimeter intrusion detection and lighting systems. The company has now installed the Senstar LM100 which provides detection and lighting in one product and saves them over $80,000 per site. The savings are a result of the reduction of electrical requirements, conduit, grounding, and associated labor, as well as the removal of certain equipment from project scope that are required for the two-system integration. The Senstar LM100’s perimeter LED-based lighting acts as an initial deterrent. If an intruder persists and an attempt to cut, climb or otherwise break through the fence is detected, the closest luminaire begins to strobe, and an alert is sent via a security management system. The intruder knows immediately they have been detected and that their exact location is known by security and others in the vicinity.
Case studies
The City of Centennial, Colorado, operates a state-of-the-art Traffic Management Center (TMC) to monitor regional traffic conditions. Serving a population of over 108,000, Centennial’s TMC ensures smooth traffic flow, supports city operations such as snow management, and engages the public with initiatives like Centennial 101, which provides residents with a behind-the-scenes look at city departments. In August 2023, Centennial installed RGB Spectrum’s Galileo® video wall processor to address its operational needs. The city sought a solution that would enable operators to monitor live feeds from 60 CCTV cameras, improve situational awareness, and facilitate content management for real-time operations and training purposes. The challenge The Momentum Group provided exceptional service and support throughout the project Centennial’s Traffic Management Center required a reliable, flexible system capable of displaying numerous video streams simultaneously. Operators needed the ability to monitor critical intersections and road conditions in real-time. Beyond daily operations, the TMC needed a tool to support public presentations and internal reviews, offering intuitive control of the video wall through a desktop interface. Planning for the new operational center began in 2021. After evaluating various options, Centennial chose to follow the example of neighboring Douglas County, which had successfully implemented RGB Spectrum’s Galileo system in its TMC. This decision was influenced by positive feedback on Galileo’s reliability, flexibility, and performance. The city collaborated with the Momentum Group, a nationally recognized and award-winning manufacturer’s representative firm in the Rocky Mountain region. The Momentum Group provided exceptional service and support throughout the project. “We’ve been very happy with the system reliability and functionality. The Galileo allows us to monitor real-time traffic and engage with the public—all in one powerful platform,” Libby Nordeen, Traffic Management Center Operator, City of Centennial. Why RGB Spectrum RGB Spectrum’s Galileo video wall processor met Centennial’s needs on multiple fronts. It offered a seamless solution for monitoring multiple video streams in real-time and allowed operators to move content effortlessly between a desktop interface and the video wall. The city appreciated Galileo’s robust design, which ensures 24/7 reliability, and its scalability to accommodate future operational growth. Libby Nordeen, Traffic Management Center Operator, described the decision: “We really liked that Douglas County uses Galileo and has been happy with it. It made sense for us to go with RGB Spectrum to align with our region and ensure seamless communication with other jurisdictions.” How the City of Centennial uses RGB Spectrum The Galileo processor also supports Centennial’s broader goals of public engagement and education At the heart of Centennial’s TMC is RGB Spectrum’s Galileo processor, which powers a Planar display that showcases live video feeds from 60 CCTV cameras. Operators, including Nordeen and her team, use the system daily to monitor traffic conditions and enhance citywide situational awareness. This capability has been especially beneficial during inclement weather, allowing snow crews to assess road conditions and prioritize their efforts using live video feeds. The Galileo processor also supports Centennial’s broader goals of public engagement and education. During events like Centennial 101, a program designed to familiarize residents with city operations, the TMC uses the video wall to demonstrate how the department monitors traffic and supports real-time operations. The ability to move content from the desktop to the video wall enables operators to create dynamic and engaging presentations for visitors and city officials alike. Looking ahead, Centennial plans to expand the TMC’s capabilities to include enhanced incident management and greater system-to-system communication with neighboring jurisdictions such as Englewood, Greenwood Village, and Littleton, all of which use the same traffic signal platform. Results and benefits Since installing RGB Spectrum’s Galileo video wall processor, the City of Centennial has seen significant improvements in traffic monitoring operations. Operators now benefit from enhanced situational awareness and streamlined decision-making. Galileo’s seamless integration with desktop control has simplified workflows, enabling more efficient management of daily monitoring and presentations. Libby Nordeen highlighted the system’s impact: “We’ve been very happy with the system reliability and functionality. Galileo allows us to monitor real-time traffic and engage with the public—all in one powerful platform.” The TMC’s enhanced operations provide a solid foundation for future growth. As Centennial expands its capabilities to include incident management and regional collaboration, the Galileo processor will continue to be a cornerstone of efficient traffic monitoring and control.
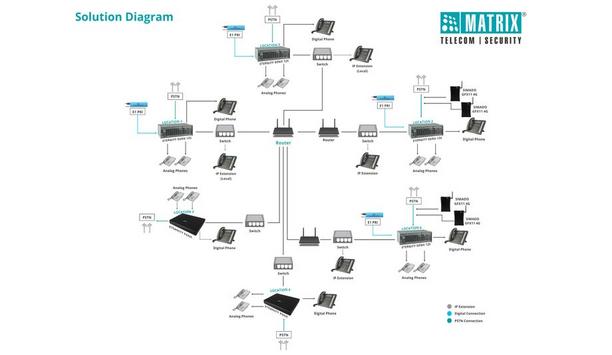
The university in rural Maharashtra is committed to providing a holistic and inclusive education that focuses on character building, intellectual growth, and community service. Its mission is to develop knowledgeable, compassionate citizens. With an emphasis on interdisciplinary studies, experiential learning, and cultural heritage preservation, the institution aims to foster creativity, innovation, leadership, and responsible global citizenship. Featuring one of the largest campuses in Mumbai, the university offers a diverse range of programs across nine different disciplines. Challenge/requirements The client faced considerable difficulties with their current communication system. The wired configuration demanded frequent maintenance, and ongoing problems with voice communication quality persisted. The primary challenges they encountered included: Problems with wired communication: The wired system experienced issues like corrosion, pioneering to a decline in communication quality. Call Quality: The communication system faced problems like dropped calls and interruptions during active conversations. Multi-location and Unified Communication Solution: Upgrading the infrastructure was essential to connect and unify various sites across the campus. Integration with Existing Infrastructure: The new solution had to be compatible with their current setup to bring modernization. Redundancy: To guarantee minimal or no downtime, especially in emergencies, incorporating redundancy was essential. Solution Matrix, in partnership with Shreeji Comsec, designed a solution that greatly improved the university's communication capabilities. The key aspects of this solution are summarized below: The current infrastructure relied on copper PRI lines, which needed to be upgraded to IP. To support this transition, two Matrix VoIP-PRI gateways, the SETU VTEP2P and SETU VTEP4P, were utilized. The VoIP-PRI gateways are now compatible with two Matrix IP Phones: the SPARSH VP510 and SPARSH VP210. The IP connection can now be routed through SIP (TATA) trunks via the Matrix server-based PBX, ANANT. The server-based PBX, ANANT, provided seamless communication with integrated redundancy, effectively eliminating downtime. Results The solution enabled the university to consolidate multiple sites into a single communication network. Legacy systems were smoothly integrated with modern VoIP technology, optimizing existing investments and enhancing the overall communication infrastructure. This upgrade notably increased operational efficiency. Here is a detailed overview of the solution: Multi-location Solution: Multiple sites were integrated into a unified, comprehensive communication system. Unified Communication Solution: Integrating with the server-based PBX, ANANT, facilitated seamless collaboration and ensured uninterrupted information transfer and reception. Investment Optimization: The integration of SIP with the Matrix Solution, seamlessly incorporated into the existing network infrastructure. This approach maximized the use of existing resources and avoided the need for additional investments. Operational Efficiency: The redundancy built into ANANT ensured minimal or no downtime, facilitating a continuous flow of information and significantly enhancing workflow efficiency. This feature was crucial for maintaining critical communications and handling emergencies effectively. Modern Features: The office now benefits from advanced functionalities provided by Matrix Standard SIP desk phones, including the SPARSH VP510. These features, such as call-back and auto-answer over secure SIP communication, greatly enhance the university’s communication capabilities. The Matrix communication solution allowed the university to both enhance and modernize its communication capabilities, equipping them with advanced, state-of-the-art call features.
Athena Security’s Concealed Weapons Detection System was selected by Champions Club Texas to protect patrons, members, and staff at a first-of-its-kind hospitality destination in Houston that features a full-service hotel, lounge, and bar with Southern-inspired cuisine and private-membership poker. Located in Houston’s expanding Westchase community, Champions Club Texas is celebrating its grand opening as a destination offering something for everyone, from business travelers seeking comfortable accommodations with well-appointed amenities to locals looking for a unique night out. Weapons detection system Athena's Concealed Weapons Detection System (WDS)/Walk Through Metal Detector is engineered to detect a wide range of mass casualty threats like handguns, shotguns, and rifles without requiring individuals to stop as they pass through the detector. There is no need to have individuals remove phones, wallets, or other extraneous items from their pockets due to the proprietary multiple-sensor detection method. The system adheres to Federal Standards while allowing both auditory and visual alert options, as seen in the best practices of Homeland Security for WDS. The concealed weapons detection system is designed to scan walking at an average speed of one person per second. Unintimidating approach Athena Security is a solution that detects weapons upon entry and is one of the many layers of security “At Champions we are raising the bar in hospitality and gaming, and that includes ensuring the most comfortable and safe atmosphere for our valued customers,” said Trent Touchstone, Director of Security, Champions Club Texas. “Athena Security is a solution that detects weapons upon entry and is one of the many layers of security protocols in place at Champions that improves the operational efficiency of our security team as a workforce multiplier.” Athena Security’s low profile, unintimidating approach is a welcome differentiator from historic metal detector tech by eliminating the need to check cell phones and keys, allowing for a better flow into the venue. Modest-full time security team Advanced analytics and management protocols allow for deep visibility and flexibility to maintain staffing levels providing the highest level of safety. Touchstone, a 28-year veteran of the United States Marshals Service Chief with a long history of threat analysis, notes that given the hotel and membership club will require 24/7 attention with a modest-full time security team, he appreciates Athena Security’s ability to provide a feature-rich entryway security experience with the ability to automate and accomplish so much remotely.
Like most stadiums worldwide, the Alsancak Mustafa Denizli Stadium suffers from vandalism and riots by individual fans. To be able to better identify and track perpetrators and thus reduce financial and non-material damage, the operator opted for a video security solution from the German manufacturer Dallmeier. The Alsancak Mustafa DenizIi Stadium in Izmir–named after former Turkish football player and current football coach Mustafa Denizli–is a multipurpose stadium that mainly hosts football matches. With over 15,000 seats, it is one of the medium-sized stadiums in Türkiye. Originally built in 1929, it was demolished in 2015 and reopened after reconstruction in November 2021. Up to 15% fewer spectators due to riots Outcomes have been painful, ranging from classic fines to the closure of an entire block of viewers In Türkiye, stadiums are usually owned by the Ministry of Sport, which then grants the rights of use to an operator. In the case of the Alsancak stadium, the operator is “Altay Izmir”, an Izmir-based football club that currently plays in Türkiye’s top professional league. The club, like so many other football stadiums, has had its fair share of repeated incidents and threats to spectators and players. These have included verbal abuse and even the throwing of objects onto the pitch. In addition to the intangible damage to the image, the consequences have been painful, ranging from traditional fines to the closure of an entire block of spectators–a loss of 1,000 to 2,000 spectators per home game, and that on a regular basis. How is image quality defined to recognize perpetrators? Under these conditions, the operators were looking for a solution that would allow them to reliably detect and track potential offenders. The tender specified a minimum resolution density of 144 pixels per meter (px/m), which is also required by law. This means that there must be at least 144 pixels in the camera image to represent every meter of “reality” in the stands. This value is between the “recognition” (125 px/m) and “identification” (250 px/m) qualities specified in the IEC EN 62676-4 standard for video surveillance systems. Only ten cameras to monitor the stands The Ministry of Sports decided to invite various manufacturers to a comparative test To find the most suitable solution for the Alsancak Stadium, the Ministry of Sports decided to invite various manufacturers to a comparative test. After receiving the proofs of concept (PoCs) of several companies, the owner chose a solution from the German manufacturer Dallmeier Electronic. In addition to around 140 single-sensor cameras for corridors, outdoor areas, and entrances, only ten “Panomera®” multifocal sensor systems are required for the particularly critical grandstand surveillance. 39% more resolution than required The low number of camera systems required for grandstand surveillance is due to the patented multifocal sensor technology: Panomera® cameras combine the images from up to seven detail sensors and one overview sensor in a single camera system. This provides the user with a high-resolution overview of the entire area to be monitored, which acts as a single image of a vast environment. Within this overall picture, system operators can now open any number of detail views at the same time, while the overall scene is always available in high resolution–even during recording, which is essential for possible prosecution. This provides an optimal overview of the situation and ensures that all events can be followed in real-time, in high resolution and in detail. Thanks to this technology, a minimum of 200 px/m is now available throughout the Alsancak stadium instead of the required 144 px/m – 39 percent more than originally required. No surprises: Remote “FAT” and training from Dallmeier Türkiye Due to the COVID-19 pandemic, the stadium's technicians were unable to travel to Dallmeier's headquarters in Regensburg, Germany, to commission the system and attend classroom training. For this reason, the so-called Dallmeier Factory Acceptance Test (FAT) took place online. The entire system was set up, configured, and remotely accepted in the FAT center in Regensburg. The training of the technicians and operators was carried out by Dallmeier Türkiye experts on-site The training of the technicians and operators was carried out by Dallmeier Türkiye experts on site. Serkan Atalar, CEO of RESA Construction Electromechanical Inc. Co, the installer company that implemented the project, is very pleased: “Dallmeier's sincere and collaborative approach, as well as the high-tech products and after sale support they offered were very impressive. We thank Dallmeier Türkiye for the great cooperation.” Author's quote “The customer is very satisfied with the Panomera® systems. The benefits are equivalent to combining a powerful megapixel camera with any number of high-resolution 'virtual' PTZ cameras. At the same time, the systems reduce the total cost of ownership for infrastructure, cables, masts, screens, workstations, etc.,” Serkan Atalar summarizes. “Alsancak Stadium only needs three system operators with one monitor each. They also have two workstations for the police and management. The solution always gives them 100% control of the security situation in the stadium, allowing them to react immediately and reliably track down perpetrators. And all this at a low total cost of ownership and with minimal manpower thanks to the unique multifocal sensor technology.”
Located in Kerala, India, the Somatheeram Ayurveda Hospital with a Resort Ambiance is the best place for not only visual rejuvenation but also physical and mental rejuvenation. Through Ayurveda, Somatheeram provides a means to shed all worries, anxieties, and illnesses. With the objective of combining Ayurveda and Tourism, the Somatheeram Research Institute & Ayurveda Hospital was founded in the year 1985, thus making it the world’s first-ever Ayurvedic Hospital in a Resort Ambiance. The Somatheeram Group of Companies came into being with the efforts of the Founder Managing Director, and Architect Mr. Baby Mathew. Challenges Multi-location transmission proves to be an expensive affair if devices are not chosen wisely Somatheeram has multiple resorts, located at different locations. Multi-location communication can prove to be an expensive affair if communication devices are not chosen wisely. Their dependence on public service providers for communication added to their woes of communication between their resorts. To elaborate: Feasibility of existing telephony: Existing telephony became impracticable considering the frequent communication between multi-located properties. Managing different protocols: Interface with different telecom networks requires managing different protocols, which can be cumbersome, time, and energy-consuming. Absence of modern phone features: The lack of advanced features like abbreviated dialing, call pick up, and internal call restriction, prevented them from becoming efficient in day-to-day operations. Transition to modern communication with existing infrastructure: Their investment in existing infrastructure needed protection while also a provision had to be made to modernize the communication using existing infrastructure. Solution The solution offered was based on the fundamentals of multi-location communication solutions Matrix analyzed the challenges of communications for Somatheeram and crafted a solution that was the best fit. The solution offered was based on the fundamentals of multi-location communication solutions. This included the Matrix range of IP-PBX (ETERNITY GENX12S) and GSM Gateway (SIMADO GFX11 and SIMADO GFX11 4G) that optimized the feasibility of communication and helped the firm become more efficient. Solution includes: The Hybrid IP-PBX included ETERNITY GENX12SAC, which enabled them up to 240 Analog users with 64 CO Ports. Another Hybrid IP-PBX included ETERNITY PENX, which allowed them access to 100 IP Users, onboard IP User Support, LDAP Client support, support of 4G VoLTE ports, COSEC Door Integration, and much more. The GSM gateway included SIMADO GFX11 and SIMADO GFX11 4G which enabled them to make and receive calls from analog extensions. The capability to integrate with almost all industry-pioneering PBXs enabled them a smooth transition to modern communication while maintaining existing infrastructure. Results The solution so implemented enabled all properties to work as a single communication platform and proved to be beneficial for Somatheeram and its properties in more than one way. The Hybrid IP-PBX enabled them, unified communication facilities like Email to SMS, audio/video calling, unified messaging facilities, and multi-location collaboration features like UC client integration, one-number reach, etc. The Hybrid IP-PBX also enabled, investment optimization through universal network connectivity, easy and centralized phonebook management through LDAP client support, mobility convenience through 4G VoLTE support, and much more. The GSM/4G gateway enabled them, GSM/4G connectivity to existing infrastructure, hotline extension dialing, emergency number dialing even in the absence of a sim card, etc. through secure network bridging.
Quanergy Solutions, Inc., a pioneering provider of 3D LiDAR (Light Detection and Ranging) security solutions, was chosen by a large municipality in California USA, in order to bolster pedestrian safety in the city's underground railways where fatality risks and costly liability issues were of growing concern. Traditional video surveillance The California city’s management had been grappling with a substantial number of missed alarms within its underground railroad system due to the intricate terrain and challenging lighting conditions. The absence of alarms when individuals trespassed onto train tracks posed a significant liability issue, endangering lives and increasing operating expenses. Traditional video surveillance systems had further proven ineffective in these environments due to inconsistent lighting and various obstructions that made it difficult to maintain a consistent field of view. Quanergy’s comprehensive solution Quanergy hyper-accurate detection and tracking of individuals in the city’s railroad system By deploying Q-track, a seamlessly integrated solution that combines long-range 3D LiDAR sensors with advanced perception software, Quanergy enables hyper-accurate detection and tracking of individuals in the city’s underground railroad system, most importantly those individuals who find their way onto dangerous railroad tracks. Quanergy’s comprehensive solution also effectively eliminates alarm fatigue by significantly reducing false alarms. This enables operators to focus on real threats and receive actionable insights with hyper-accuracy, ensuring that no urgent alarms are missed, averting possible injuries or even fatalities. Quanergy LiDAR security solutions Thanks to Quanergy's solution, the city now reports that they have 100% accurate detection when pedestrians are on train tracks. Quanergy LiDAR security solutions are currently deployed at hundreds of critical infrastructure sites around the world, addressing a wide spectrum of mission-critical applications including perimeter intrusion detection, server rack and cabinet security, mobile security towers, mantrap/vestibule access controls, rooftop security, and more.


Round table discussion
Migrating to the Cloud can be a cultural shift for some organizations, especially when it comes to physical security systems. Challenges such as concerns about data security and compliance, cost management, and a skills gap can make adopting the Cloud seem onerous. But the benefits are there, aren't they? We asked this week's Expert Panel Roundtable: Will the impact of the Cloud on physical security integrators be net-positive or net-negative?
When it comes to protecting the environment, the security industry has historically been perched on the sidelines. For instance, the amount of electricity that physical security systems use is minimal when compared to the total energy usage in a typical building. However, as awareness of environmental issues has surged, and as some of the "low-hanging fruit" has been harvested, attention has come back to opportunities for additional, if small, savings. The lifecycles of security products are also being more closely examined, including the environmental impact of using plastics and other chemicals. We asked this week's Expert Panel Roundtable: How can the security industry contribute to protecting the environment?
Video storage has come a long way since rooms full of VCRs stored video from an entire system of cameras. Video storage equates to data storage, and there are multiple options ranging from hard disk storage to the cloud to storage on each individual camera using SD cards. Increasingly, cloud-based storage is an attractive option to store video footage conveniently and safely. We asked this week’s Expert Panel Roundtable: How is expansion of video storage capabilities impacting the security industry?
Products


White papers

Milestone Cloud Deployment Guide
Download
Access and Security In The Age of Hybrid Working
Download
Securing Unmanned Infrastructure at the Network Edge
Download
Cloud Video and Smart Cities
DownloadSinaloa, Mexico: Connected Cities are Safer Cities
Download
Hybrid Hyperconverged Systems Benefit Growing Storage and Retention Needs
Download