Facility security
A wedge barrier system is one of the most effective physical security measures for stopping unauthorized vehicles from accessing a restricted area. Designed for high-threat environments, these barriers prevent breaches that could cause significant harm to people, property, or critical infrastructure. Understanding what a wedge barrier is will help they determine if it’s the right solution for the security plan. What does a wedge barrier system do? A wedge barrier is a heavy-du...
DoorBird, a global pioneer in IP video door intercom systems, is proud to announce a new integration with Telecor’s eSeries Public Address and Intercom Solution. This collaboration brings together DoorBird’s advanced IP video technology with Telecor’s robust communication platform, delivering a unified solution for smarter, more secure facility access and communication. DoorBird’s high-definition IP video door stations are trusted worldwide in residential, commercial, a...
Allied Universal®, the world’s pioneering security and facility services company, announced that its Unified Command Center Solution has been named a runner up for the 2025 Project of the Year by Security Distributing and Marketing (SDM) magazine. SDM’s annual Project of the Year Award recognizes exceptional commercial security projects in North America and the dealers and integrators behind them. Integrates real-time video analytics The solution optimizes logi...
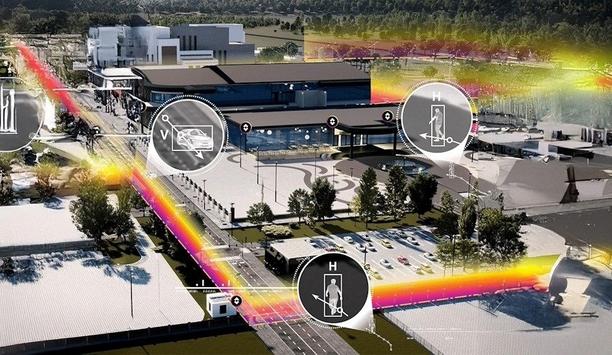
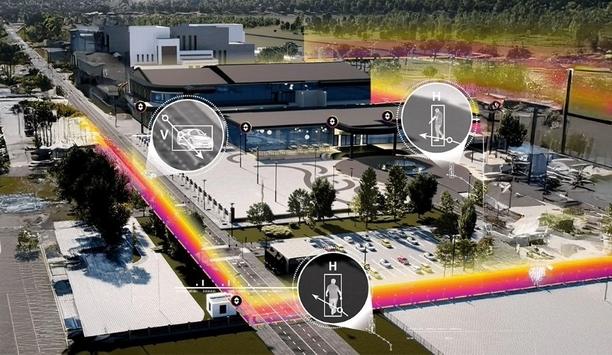
The need for the security response to be accurate, fast, and adaptive has never been more important. A single security breach has the power to impact beyond that immediate ‘moment in time’. It can spiral into potential financial, operational, and reputational damage, taking years to recover from. Not to mention that regulatory and compliance violations can be costly, and legal action and liability claims can be debilitating. The impact to reputational damage and loss of trust caused...
Allied Universal®, a pioneering security and facility services company, is proud to report some of the brave acts its security professionals performed during the second quarter of 2025. “Security professionals go to work knowing that they may encounter unpredictable situations where fast, critical thinking is vital,” said Steve Jones, Allied Universal global chairman and CEO. “I am honored that Allied Universal is consistently represented by heroic individuals who are abl...
Hanwha Vision, a pioneer in security and surveillance solutions, introduces the Audio Beacon, SPS-A100M, an advanced AI-powered audio surveillance solution that ensures users can be alerted and respond rapidly to critical situations. Equipped with a powerful 90dB speaker, five integrated microphones, and intelligent sound classification, the Audio Beacon is engineered to enhance situational awareness and real-time communication. Immediate awareness The LED ring provides a visible and reassu...
News
At GSX 2025, global security manufacturer Gallagher Security is inviting attendees to reimagine what security can achieve when limitations are removed. Visitors to booth #3339 will experience firsthand how Gallagher is redefining the role, function, and value of security in the workplace of the future. “Security has traditionally been seen as a cost center or a barrier,” says Melissa Vidakovic, Director of Marketing – The Americas. Innovation and imagination “But what if it could be more? This year’s booth is about showing attendees what security reimagined looks like when innovation and imagination come together. If I had to describe it in one word, it would be ‘transformation.’” “We’ve had an eventful year of new products and solutions released to market, and GSX is the opportunity to see how they come together to produce a platform that delivers more capability, less friction, and greater results,” concluded Melissa Vidakovic. At booth #3339 attendees are invited to get a front row view of Gallagher’s most recent product innovations driving that transformation, including: QuickSwitch, the much-discussed migration tool transitioning businesses away from legacy systems to Gallagher's award-winning platform. The complete Controller 7000 Suite, featuring the newly released PIV-ready High Security variant that meets GSA standards, UL/ULC compliance, and additional international high assurance benchmarks. OneLink, the cloud-based solution that makes distance a problem of the past and redefines the definition of remote connectivity. A sneak peek at AccessNow, a cloud-native solution that automates access and credential requests end-to-end, slashing admin for security teams all while delivering instant, self-service access to End Users. And that’s just the beginning. “There’s so much happening at our booth this year that I can’t give it all away just yet,” Vidakovic adds. “We’ve got big announcements in the works, and I hope attendees stop by to see what’s next.” World’s first electric fence For Gallagher, innovation on this scale is nothing new. “Our company’s 85-year history is filled with moments of breakthrough thinking that reshaped industries,” says Gallagher Security Chief Executive, Mark Junge. “From the world’s first electric fence to today’s unified security platforms, innovation is at the heart of who we are. The GSX 2025 booth is a powerful example of how we continue that legacy today while looking boldly to the future.” Gallagher Security invites GSX attendees to visit booth #3339 from September 29 – October 1 in New Orleans. Use code EV246 for discounts on all-access passes or free expo passes when registering to attend.
In recent years, ram raids have become an increasingly common criminal tactic, particularly against businesses with storefronts facing public streets. The impact not only causes property damage but can also shut down operations for days or weeks. For both small retailers and large enterprises, the financial and reputational costs can be devastating. Ram raid bollards are a simple and effective way to prevent would-be raiders. What is a ram raid? A ram raid is when a perpetrator deliberately drives a vehicle into a building, typically a commercial property, to gain unauthorized access. Street-facing retail stores are prime targets, especially those selling electronics, jewelry, or high-demand consumer goods. But ram raids can also threaten warehouses, government facilities, event venues, and even military supply depots. Vehicles traveling at high speed can deliver enough force to breach most standard building facades. This means even properties with heavy doors or window bars can be vulnerable if their perimeter isn’t adequately protected. How can bollards help prevent ram raids? Bollards play a critical role in an integrated ram raid prevention strategy. By serving as physical barriers, they stop vehicles before they reach a building’s vulnerable points. However, the effectiveness of bollards depends heavily on strategic placement. Security planners position bollards to block the most direct vehicle approach paths. For example, installing crash-rated bollards along the curb in front of a storefront creates a barrier that prevents a car or truck from aligning with entry doors. In some high-risk areas, bollards are arranged in staggered formations, forcing vehicles to slow or stop while still allowing pedestrian access. As part of a Crime Prevention Through Environmental Design (CPTED) approach, bollards can be integrated with landscaping, lighting, and other environmental features to naturally deter criminal behavior. What are the best types of bollards for security against ram raids? Not every type of bollard on the market is designed to stop a vehicle. Some are purely aesthetic or intended only for pedestrian or traffic control. For true ram raid prevention, businesses and agencies must select impact-rated bollards engineered to withstand deliberate, high-speed collisions. High-impact bollards vs. traffic control bollards High-impact or anti-ram bollards are built with reinforced steel cores, deep foundations, and engineered designs to dissipate collision forces. These are the bollards that can stop a moving truck in its tracks. In contrast, traffic control or decorative bollards are often made from lighter materials like plastic or thin-gauge steel. Their primary function is to guide vehicles, block parking in restricted areas, or protect pedestrians, not to withstand a full-speed impact. While they can play a role in safety and traffic management, they are not a substitute for crash-rated security bollards. Steel, concrete, or retractable Material choice impacts both performance and appearance. Steel bollards are common for anti-ram applications because of their strength and ability to be filled with concrete for added mass. Concrete bollards, like the iconic red spheres outside many Target stores, are a more straightforward solution for specific sites. They are purely static barriers, highly visible, and effective against vehicle intrusion. Retractable bollards offer flexibility. They provide the same vehicle-stopping power when deployed, but can be lowered or removed to allow approved vehicle access. This makes them ideal for military bases, government facilities, or event spaces where controlled access is essential without compromising security during high-risk periods. Assessing the risk before choosing bollards Before investing in anti-ram solutions, it’s important to understand your specific level of risk. A busy city storefront, a government facility near a public roadway, and a private distribution center all face different threat profiles. Reviewing crime statistics in the area, evaluating site access points, and noting any previous incidents can help determine the level of protection they need. Partnering with a security consultant or engineer experienced in anti-ram applications ensures that the bollard system is tailored to their building security needs. Choose high-quality ram raid bollards to protect the infrastructure Whether the priority is protecting a sidewalk café, securing a public facility, or fortifying a sensitive military installation, the right bollard solution can mean the difference between a near miss and a catastrophic breach. At Delta Scientific, they manufacture anti-ram bollards in multiple designs, materials, and impact ratings to match diverse operational environments. The engineering team can help they determine the correct placement, material, and rating to meet their security objectives. Browse the range of high-security bollards to see which options align with their threat profile and site requirements. The right choice of bollard for ram raid protection can protect their assets, safeguard their people, and deter criminal activity before it begins.
Allied Universal, a world pioneering security and facility services provider, is expanding further in the northeast region of the U.S. with the acquisition of Mulligan Security. For more than 30 years, Mulligan Security has provided security and fire safety services to clients in and around New York City. Its clients range from commercial properties and corporate facilities to hospitals and museums. Combining the strength “Combining the strength of our businesses and leadership teams will create new opportunities to expand our innovative security solutions to meet the needs of our clients,” said Steve Jones, global chairman and CEO of Allied Universal. “Mulligan Security’s deep expertise and strong presence in Greater New York City help strengthen Allied Universal’s footprint in the region. Together, we’ll continue serving clients in New York City and beyond with outstanding service, greater value, and continued innovation.”
The need for the security response to be accurate, fast, and adaptive has never been more important. A single security breach has the power to impact beyond that immediate ‘moment in time’. It can spiral into potential financial, operational, and reputational damage, taking years to recover from. Not to mention that regulatory and compliance violations can be costly, and legal action and liability claims can be debilitating. The impact to reputational damage and loss of trust caused by negative media and public scrutiny can ruin competitive advantage. Sophisticated intrusion threats The rise in sophisticated intrusion threats is also running alongside a shift in the way operations are handled The rise in sophisticated intrusion threats is also running alongside a shift in the way operations are handled. The introduction to 'always-on' facilities and flexible workforces means traditional security models are no longer sufficient for these new environments. Advanced situational awareness is the ability to rapidly perceive, process, and respond in dynamic environments. It is achieved by creating a proactive security framework that brings together heightened observation, pattern recognition, and predictive thinking to not only react to threats but actively prevent them. Multi-layered security This ability to not just see but to know more about threats in real time, respond with precision, and continuously adapt to emerging risks is crucial for maintaining safety, business continuity, and operational stability. The combination of security technologies strengthens each stage of the security journey Multi-layered security is how FLIR does that. By creating several barriers for potential intruders, it becomes more difficult for them to breach the facility. The combination of security technologies strengthens each stage of the security journey from initial detection through to identification and tracking, stopping threats before they can cause harm. Intelligent imaging FLIR’s multi-layered security solutions integrate intelligent imaging and sensing solutions, along with tools that continuously enhance action and response. The products are designed to provide accurate detections through all hours of the day and, critically, in low light and night. Greater site coverage Increased deterrence and risk mitigation Increased detection accuracy Faster response to incidents Reduced false alarms and increased response dispatch confidence Reduced total cost of ownership Enhanced regulatory compliance and reputational resilience Critical technologies For more than 45 years, FLIR has been at the forefront of the critical technologies that support the protection of people and assets. Their commitment and investment in research and development have delivered some of the key game-changing technological advances in the field. These include the development of thermal solutions for commercial applications and the NEXUS protocol, which enables edge-to-edge communication for fast and accurate tracking. They see beyond products and systems to solutions and behavior. By combining thermal, visible, and ground-based radar imaging with their pioneering video analytics, FLIR’s multi-layered solutions provide users with the strategic building blocks to detect, identify, track, and act over a long range and in any weather condition. Integrated security systems FLIR knows a business is unique, which is why the FLIR multi-layered approach is not ‘one size fits all’ Advances in technology, automation, and integrated security systems have broadened their use, making this level of comprehensive protection more accessible than ever, not just in deployment but importantly, in cost. This means the affordability of strategic security is no longer a question. FLIR knows a business is unique, which is why the FLIR multi-layered approach is not ‘one size fits all’. Users can have the confidence of accurate detection and communication that are specifically designed to be scalable, flexible, and adaptable. Working with FLIR means every organization can implement a strategy that aligns with its own specific risks, operations, and infrastructure. multi-layered security FLIR is launching a series of articles and expert insights designed to help organizations move beyond the limitations of conventional measures to integrate advanced multi-layered security into a forward-thinking security strategy. FLIR will drill down into each stage of the security solution implementation journey, with in-depth analysis of how FLIR’s integration of advancements in thermal, visible, and ground-based radar solutions is transforming detection, identification, tracking, and response. Explore how a strategic, layered approach enhances protection, mitigates risks, and ensures business continuity. Deep dive into FLIR’s next general video analytics and the digital layer of security. Discover how advances such as FLIR vAI (AI-based alarm verification) are offering significant improvements in performance over traditional AI analytics. That’s the FLIR advantage: the combination of their expertise, innovation, and technologies to deliver strategic advantage. It is the power of integrated, tailored security layers that enables users to achieve a more resilient and proactive defense against evolving threats
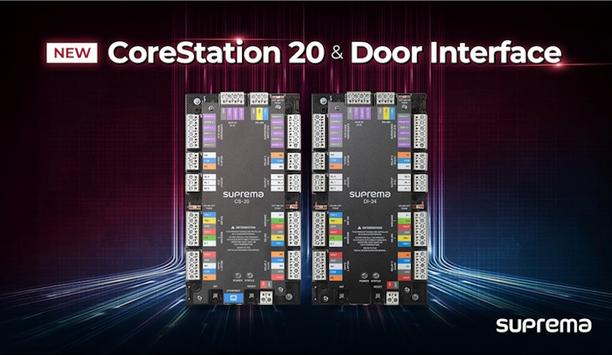
Suprema, a pioneer in AI-powered access control and security solutions, announced the launch of a new 2-door access controller, CoreStation 20 (CS-20), and Door Interface (DI-24) module for 2-door and 4-reader. With these additions, Suprema has expanded its ACU (Access Control Unit) portfolio, further enhancing the portfolio’s security, flexibility, and scalability. New Door Interface module Suprema offers a comprehensive ACU portfolio designed to support building access control systems that can flexibly adapt to a wide range of operational requirements from small facilities to large-scale enterprises. Suprema’s flagship controller CoreStation (CS-40) supports biometric matching suitable for advanced high-level security environments. CoreStation 20 is a compact yet powerful RFID-only controller, supporting up to 500,000 users and offering native PoE+ support and encrypted communication. The new Door Interface module is designed to simplify wiring and operate reliably even without a live network connection. Suprema’s ACU products Suprema’s ACU products provide high deployment flexibility, supporting both centralized systems Suprema’s ACU products provide high deployment flexibility, supporting both centralized systems for large-scale sites and distributed architectures for smaller facilities with simplified connection structures. This flexibility not only enables the deployment of access control systems tailored to diverse environments but also facilitates cost-effective upgrades of legacy infrastructure through cable reuse, simplified installation, and streamlined maintenance—ultimately reducing overall deployment time and cost. Suprema’s access control system “The launch of CoreStation 20 and Door Interface has further strengthens the scalability and flexibility of Suprema’s access control system. These additions enable system designs tailored to a wide range of customer environments, while reducing installation costs, reinforcing security through encrypted communication, and ensuring stable operation, even during unexpected events such as power outages,” said Hanchul Kim, CEO of Suprema Inc. “Moving forward, Suprema aims to help customers operate their systems with greater confidence and expects these advancements to further strengthen the brand’s reliability in the global market.”
Allegion US, a pioneering provider of security products, technology, and solutions, announced the launch of Overtur™ Key System Management, a cloud-based subscription solution that offers authorized users a simpler way to view, manage, track, and update a building’s key system – regardless of complexity. Overtur Key System Management is an extension of the Overtur digital environment, which empowers project teams to collaborate in real time on the design, specification, construction, and management of openings – helping them to be more effective and efficient all while improving project outcomes and client satisfaction. Complementary key system design One of the subscription-based levels of Overtur Key System Management can unlock features With the new Overtur Key System Management offerings, facility managers, locksmiths, and distributors can now access complementary key system design tools that empower users to survey conditions, collaborate, filter data, design hierarchies, assign symbols, utilize cloud-based features, and create detailed key schedules. Moving to one of the subscription-based levels of Overtur Key System Management can unlock features that will help protect sensitive information, manage key control and building access, helping to create secure and efficient management of key systems. Use of innovative solutions “Overtur was created to facilitate collaboration, with the mission of making it easier for project teams to design, construct, and manage door openings and the corresponding hardware,” said Holly O’Haver, Overtur Business Pioneer at Allegion. “Overtur Key System Management is the evolution of this vision, offering advanced tools to streamline key system design and management, helping to preserve the integrity and simplify management of the key system through the use of innovation solutions.” Three tiers of Overtur Key System Management Overtur Key System Management is available to security professionals in three tiers: Overtur Key System Design is complementary for Overtur users and streamlines key system design and data capture with features that allow users to: Build and visualize a key system hierarchy and schematic Survey existing conditions on site using the mobile app Conduct key meetings using the collaborative tools and add notes directly within the platform Assign and view as many key symbols as needed per building and per opening Focus on specific data using customizable data filters Enjoy unlimited users, automated updates, and secure cloud storage Generate comprehensive key schedules with fully configured part numbers Level 1: Key System Design + Manage Bitting/Pinning: A level 1 subscription lets you do more by utilizing all the complementary aspects of the Overtur digital environment plus: View available bittings Request next available change keys and get results within minutes Get on-demand bitting lists and pinning charts Import key symbol descriptions and associated openings Get started with an online hour-long training session with an onboarding specialist Level 2: All Level 1 Features + Key Control: The level 2 subscription builds on previous levels with customized onboarding and advanced features that include: Track issuance and return of keys and key rings Upload the key holder list View and manage key holder by opening/associated symbol Create key rings Identify a specific key holder by key assignment using system-designated serial numbers Store key holder agreements as attachments Create and save custom views to quickly filter and search information Enjoy customized training and personalized step-by-step setup assistance for a faster start Significant challenges of the key system management solution Without a proper key system management solution, organizations can face significant challenges such as difficult auditing, security risks, and inefficient tracking of key issuances. Overtur Key System Management addresses these issues by providing a comprehensive, cloud-based solution that provides the tools for secure data storage, efficient key control, and accurate tracking. By leveraging Overtur software, organizations can enhance their security, streamline operations, and maintain precise control over their key systems.


Expert commentary
Physical security isn’t a one-time project or a static system. It’s a dynamic, ongoing process and program that requires constant attention and management to remain effective. While the initial implementation of a security system — what we often call Day 1 — is critical, the ongoing maintenance, service, and adjustments made after systems are operational, or Day 2, are equally essential. Security program long-term Organizations that fail to focus on post-occupancy security operations risk falling victim Organizations that fail to focus on post-occupancy security operations risk falling victim to a phenomenon known as "program drift," where systems and policies gradually deviate from their intended standards over time. To manage your security program long-term, you often need an outside perspective. By engaging a security partner to provide managed services, organizations can achieve a strategic solution for maintaining their security programs' integrity, effectiveness, and efficiency over the long term. Let’s look at the reasons why. Moving beyond Day 1 Day 1 is the milestone moment when a security system is launched — whether it’s a new system, an upgraded access control platform, or a transition to advanced surveillance technology. On this day, all components align with established policies and standards. Yet, Day 1 is only the beginning of a security program's lifecycle. What happens on Day 2 and beyond is often where the real work begins. Without a robust plan for ongoing service and maintenance, security systems can quickly fall out of compliance. Policies become outdated, configurations drift, and vulnerabilities emerge. This gradual degradation — program drift — occurs not due to neglect but as a natural result of decentralized management; competing operational priorities; and the lack of dedicated, knowledgeable resources to oversee the systems. Avoiding program drift Drift is particularly pronounced in physical security because, unlike other building systems Program drift occurs when a security program’s elements — such as access controls, camera placements, or intrusion detection settings — gradually become misaligned from their intended standards. Think of a straight line representing perfect compliance on Day 1. Over time, various factors push individual components off this line. Left unchecked, these deviations accumulate, leading to significant vulnerabilities and deferred remediation costs that would be much easier to manage and predict with a more proactive approach. Drift is particularly pronounced in physical security because, unlike other building systems such as lighting or HVAC, security measures are often viewed as inconveniences. Even when systems function as designed, features like turnstiles, visitor management, or additional access controls may face pushback for being "in the way" of daily operations. This resistance and the Day 2 problems that often result — along with the lack of centralized oversight — exacerbate the risk of misalignment and ongoing inefficiencies. Why centralized post-occupancy management matters Post-occupancy management is critical for maintaining the long-term health of a security program. Facility managers, who are often tasked with overseeing security systems, may lack the technical expertise or bandwidth to handle the complexity of modern security infrastructure. Partnering with dedicated professionals to help meet these responsibilities ensures systems are managed effectively and vulnerabilities are addressed proactively. It also helps improve system availability and uptime, accelerate break/fix response and resolution times, lower ownership costs by reducing unnecessary and repeat service dispatches, and achieve a more consistent end user experience. Moreover, centralized management provides a consistent framework for handling security systems across multiple sites. This consistency is vital in preventing Program Drift, ensuring that local variations or individual decisions do not undermine the organization’s overall security posture. The case for managed services Hiring outside consultants offers a proactive and professional approach to mitigating program drift Hiring outside consultants offers a proactive and professional approach to mitigating program drift. Specialized providers have the expertise, tools, and resources to manage complex security systems effectively and ensure those systems remain aligned with organizational policies and performance expectations. By acting as a dedicated external resource and interfacing regularly with your security team, your consultant can help you build, manage, and optimize a variety of services that help keep your program on track. These services range from system health and availability management (break fix); move, add change management; system configuration administration; and program/project management offices. Key benefits in the following areas Let’s look at how a managed services a partner can yield key benefits in the following areas: Standards compliance. Centralized management ensures that security systems and processes remain in compliance with established policies and standards, reducing vulnerabilities caused by ad hoc changes or decentralized management. Operational efficiency. Managed services streamline maintenance and support workflows, minimize downtime, and ensure quick issue resolution. Enhanced security resilience. Proactive monitoring and maintenance reduce the likelihood of system failures and improve overall system reliability. Standardized processes for move-add-change (MAC) activities ensure that security configurations remain consistent across locations. Cost savings. Outsourced providers help organizations optimize resources, avoid errors, and benefit from economies of scale in service delivery. Strategic focus. Outsourcing also allows internal teams to shift their focus from routine operational tasks to higher-value activities, such as strategic planning, threat analysis, and incident response. Long-term value of security investments While Day 1 success is the foundation of a comprehensive program, what happens on Day 2 determines your ability to realize the long-term value of your security investments. As the complexity of security challenges grows, leaders must prioritize sustained management and professionalized oversight to protect their organizations, making the conversation around post-occupancy security more critical than ever. By adopting innovative strategies, implementing mature toolsets and processes, and leveraging specialized expertise, organizations can ensure their programs remain robust, aligned, and prepared to meet the challenges of tomorrow.
The average business owner or investor has some kind of security precaution in place, especially in the after-hours when there are fewer deterrents to inhibit criminal activity. Security guards, video surveillance systems, motion sensor lights, or even just fake cameras placed around the property are some of the common options people choose. Future of overnight security Smart business owners are starting to realize, however, that some of these traditional security measures are becoming antiquated and no longer cutting. The now and future of overnight security is in remote guarding. Pioneered by companies like Los Angeles-based Elite Interactive Solutions, which was founded back in 2007, remote guarding is revolutionizing the overnight security business. Minimizing criminal activity Remote guarding is fast becoming the most popular choice among commercial end-user property owners Remote guarding utilizes a combination of cutting-edge technology, “digital guards,” highly trained security agents, and local law enforcement if and when necessary to minimize the potential of criminal activity. For those adequately enlightened to its overwhelmingly impressive crime prevention capabilities, remote guarding is fast becoming the most popular choice among commercial end-user property owners to secure and protect their investments. What Is Remote Guarding? Remote guarding is a revolutionary concept and increasing trend in security systems that utilize a combination of methods to effectively analyze potential threats to property. Cameras and/or other monitoring devices running highly advanced algorithmic software are installed in strategic areas or vulnerable places onsite and remotely located security agents are immediately notified of any activity within a designated perimeter of the property. A blend of AI, cybersecurity, and video analytics When properly deployed by an expert provider, the technology stack includes a proprietary blend of video analytics, artificial intelligence, cybersecurity, and more. Done right, “noise” is effectively filtered out, allowing agents to act on legitimate alerts and achieve zero false alarms communicated to first responders. Today, there are a lot of terms and descriptions tossed around about remote guarding, remote video, virtual guarding, etc., but those attributes must be present to represent the true definition of the offering and its many virtues. Realtime situational awareness Many systems have a two-way speaker that allows the security agent to give a verbal warning When specially trained security agents are alerted to trespassers, possible intruders, or other suspicious activity, they analyze the situation in real time and determine the necessary level of action. Many systems have a two-way speaker that allows the security agent to give a verbal warning, known as a voice-down, to the individual(s) that they are being watched. Most perpetrators, often believing the response is emanating directly from security personnel on the property itself rather than from a remote command center, flee immediately. However, if the threat persists, the security agent enlists local law enforcement to get on the scene. Customized remote guarding When properly deployed, remote guarding systems are also customized to specific properties. A team of consultants visits the client’s property to evaluate its vulnerabilities and where to best place cameras and/or other monitoring devices for system efficacy. Traditional Security Shortfalls According to Keith Bushey, a retired commander for the Los Angeles Police Department, there is much frustration between law enforcement officers and potential victims of crime due to the historically unreliable performance of traditional burglar alarm systems and central monitoring stations. He states about 90% of security-related calls are false alarms, a problem that has been well-documented through the years. Onsite challenges When a legitimate emergency does occur, the perpetrators have often already done their damage When a legitimate emergency does occur, the perpetrators have often already done their damage and/or escaped by the time law enforcement arrives. Onsite security guards are not the remedy either as they bring their own set of issues and challenges. Unexpected costs Traditional security systems can also have unexpected costs. The cost is not only in the security guards’ paycheck or the cost of the equipment itself. The cost comes when an actual incident occurs. In worst-case scenarios, the security guard(s) are injured, the business suffers inventory loss, and/or damage is sustained to the property. The medical and other costs for the security guard(s), the loss of inventory, property damage, deployment of law enforcement resources, and possible fallout of legal expenses all add up. Even in the best-case scenario, false alarm expenses incur if law enforcement is dispatched. These, among many others, are some of the primary issues that remote guarding resoundingly answers as a superior alternative. A Bounty of Benefits Remote guarding systems have been proven to cut costs and be more effective than traditional security systems. Even though the monthly monitoring costs of remote guarding are significantly higher than traditional intrusion detection system monitoring, the much higher effectiveness in crime reduction, elimination of false alarms, and augmenting or replacement of manned guards result in a substantially higher return on investment (ROI) to the end user. Easy tracking of threats The security cameras already have their image captured on record, making them easier to track down For example, case studies have demonstrated reduced security costs for clients by 60%, on average. These reductions have come from the costs of security staff, inventory, or property loss, plus saving money on insurance premiums and deductibles. The nature of remote guarding reduces the risk and costs of false alarms, with professional security agents able to determine an actual threat before law enforcement is called. In a rare instance when a perpetrator escapes before law enforcement arrives or can detain the individual(s), the security cameras already have their image captured on record, making them easier to track down and identify. Reduction of false alarms The significant reduction in false alarms is greatly appreciated by law enforcement, as it allows them to focus on real emergencies or crises. Better relationships are also developed between clients and law enforcement, as remote guarding systems are highly reliable in providing accurate and real-time information to officers as they approach the scene. In short, it assists law enforcement in doing their job more effectively, as well as more safely thanks to having eyewitness information before engaging in an active crime scene. Partnership When you combine the decreased cost with the increased efficiency and success rate, it is easy to see why many commercial end-user property owners across the country are making the shift to remote guarding. It’s also an outstanding opportunity for professional security dealers and integrators to partner with a remote guarding services provider to bring a superior solution to their end customers and pick up a recurring monthly revenue stream in the process.
It’s no secret that the data security sector is constantly changing. It has an annual CGR of about 12.3%. Future trends in data security Much of this has to do with the rise of cybercrime in recent years, with reports showing that cyberattacks happen as often as every 39 seconds. To combat the growing rate of cybercrime, data security has been on the rise. As we journey further into this era, it becomes evident that a spectrum of significant trends is molding the future of data security. This exploration delves into a selection of these trends, unraveling their importance and the potential implications they carry 1. AI security tools will increase Artificial Intelligence is also being used in the development of smart attacks and malware The introduction of Artificial Intelligence in the data security industry brought significant changes, especially in cybersecurity. AI has been the golden standard for face detection, natural language processing, automated threat detection, and automated security systems. Additionally, Artificial Intelligence is also being used in the development of smart attacks and malware, bypassing even the latest security protocols in data control. And as time progresses, AI security tools will flourish and dominate the scene. Let’s take a more in-depth look at three of the top AI security tools. Targeted attack analysis tool Manufacturers utilize targeted attack analysis tools to uncover targeted and stealthy attacks. Artificial Intelligence can be applied to the program’s capabilities, processes, and knowledge. For instance, Symantec launched this tool to combat the Dragon 2.0 attack in 2022. The phishing attack reprimanded multiple energy companies while trying to gain access to their operational networks. Targeted Attack Analysis Tools can analyze incidents and look for similarities from previous situations. They also help detect suspicious activities and collect all the necessary data to determine whether a specific action is malicious. Intercept X tool Results from the Intercept X Tool feature high accuracy and a low false positive rate Sophos, a British security hardware and software company, launched the Intercept X Tool. It engages a neural network that records and analyses data like a human brain. Sophos’ Intercept X Tool can extract features from a single file and perform a deep analysis. It detects malicious activities within 20 milliseconds. Plus, it’s also trained to work on bi-directional sharing and real-world feedback of threat intelligence. Results from the Intercept X Tool feature high accuracy and a low false positive rate. IBM Watson Technology IBM’s QRadar Advisor uses IBM Watson Technology, a unique AI tool for fighting cyber attacks. Artificial Intelligence can auto-investigate activities and indicators for potential exploitation or compromise. With cognitive reasoning, IBM Watson Technology can present critical insights to accelerate the response cycle. Security analysts can utilize this technology to search for threat incidents, reducing the risk of letting them fly under the radar. 2. Blockchain as a security solution It guarantees no points of failure or hackable entrances that can expose datasets inside the system Blockchain is a type of distributed ledger technology (DLT) that aims to establish trust within an untrusting ecosystem. Today it’s one of the most robust cybersecurity technologies in the industry. Blockchain utilizes a decentralized ledger system, but your team members can still gain access to transparent information in the cloud. Members can also record, pass along, and view necessary transactional data in the blockchain. The entire blockchain process maintains data integrity within the system while establishing trust among team members. It guarantees no points of failure or hackable entrances that can expose datasets inside the system. Cybersecurity, biometrics Cybersecurity primarily benefits from these features because blockchain can create a secure and robust wall between data and hackers. On top of that, blockchain ledgers can include biometrics like fingerprints and retina scans. These prevent hackers from accessing any private data. Because blockchain is decentralized, it also limits hackable data. Together with the technology’s record-keeping system, each node is provided insight into data manipulation exposing real-time cybercrime attempts. 3. Increased and widened access control Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data Access control is critical in data security. More than a valuable security tool, business leaders can use access control to regulate people accessing any given resource. A company with an IT security setting can control who has the liberty to edit certain files. One of the primary goals of access control is to minimize threats or attacks to organizations and businesses to keep people and data secure. Without access control, expect your company to be open to security issues, including theft, data loss, and breach of data protection laws. Benefits The benefits of increased and widened access control include: Identifying who can access and control your data at specific time intervals. Protecting data from overwriting, accidental deletion, and malicious intent. User permissions that can be readily changed. Compliance and regulation with data privacy laws. Central management of access to data through a reporting portal or a dashboard. Multi-factor authentication Access control comes in various types and systems, so it’s critical to know the features of what you’re looking for. The most common type is multi-factor authentication or MFA. It involves multiple steps before logging in, requiring the user to enter other relevant information besides the password. Some other examples of information include biometrics, answering a security question, or entering a code sent to the user’s email address. Two-factor authentication, role-based access control Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession Two-factor authentication further prevents unauthorized entries that can result in unnecessary data possession. Another type of access control is role-based access control. In this setup, only one individual can set up access guidelines and grant permissions to specific team members within an organization. 4. Greater use of the zero-trust security model The zero-trust security model is a framework that requires every user within and outside the organization to undergo authentication, authorization, and validation. These are all essential to ensure proper security configuration before access is granted to the company’s applications and data. A zero-trust model assumes that anyone can cause data breaches and that a traditional network edge is not taken into effect. Moreover, it addresses the following modern-day challenges: Hybrid cloud environments. Security of remote workers. Ransomware threats. This framework utilizes the combination of multiple advanced technologies, including: A risk-based multi-factor authentication. Endpoint security. Identity protection. Cloud workload technology. The zero-trust model uses all these innovative tools for system identification, user verification, access consideration, and system security maintenance. Constant validation and monitoring Enforcing strict policies and compliance with data privacy laws are also essential Additionally, it also considers data encryption, email security, and asset verification before establishing connections with applications. The architecture of a zero-trust framework requires constant validation and monitoring of the users and the devices they are using. Enforcing strict policies and compliance with data privacy laws are also essential. More importantly, the zero trust architecture requires all organizations to be aware of all their available services and accounts to gain complete control of data handling and manipulation. 5. Increased privacy regulations Privacy regulations and policies guide organizations in proper data control, handling, and security. These policies guide organizations in proper data control, handling, and security. As a responsible business owner, you must comply with these regulations to avoid legal issues. With cybersecurity attacks becoming common, expect increased and stricter privacy regulations to be released in the next few years. While current policies are still taken into effect, various modifications and adjustments will occur to compete with the rising numbers of data breaches, thefts, data loss, and more. California Privacy Rights Act (CPRA) Currently, the California Privacy Rights Act (CPRA) is the most comprehensive legislation on state data privacy. It only started to take effect on January 1, 2023. The CPRA introduces the following principles: Broad individual consumer rights. Significant duties of people who need to collect sensitive and personal information. Additional definitions of data privacy and security. An individual’s duties include releasing information about data collection to concerned data subjects and proper access, correction, and deletion of information. Final thoughts 2023 is a big year for data security. Trends such as increased adoption of zero-trust policies, a greater reliance on AI security tools, and the implementation of blockchain as a security solution are all things we expect to see shortly. Staying up-to-date with these trends is important for keeping your business current and ensuring that you’re adhering to new and changing regulations. Doing so can give you an edge over the competition and keep you out of legal hot water.
Security beat
Collaboration among manufacturers in the physical security industry can result in systems that are easier to install for integrators and that provide a better customer experience for end users. Illustrating the point is the recent collaboration among a turnstile technology company, a supplier of short-range wireless readers/writers, and a biometric business focused on ‘frictionless’ access control. “The more manufacturers collaborate with each other, the more benefits for end users,” says Steve Caroselli, the Chief Executive Officer (CEO) of Orion Entrance Control. Better collaboration means a better user experience We look for opportunities to collaborate and make sure the experience is above and beyond" Steve Caroselli adds, “Better collaboration means a better user experience. We look for opportunities to collaborate and make sure the experience is above and beyond.” Orion’s collaboration with ELATEC RFID Systems and SAFR touchless biometrics by RealNetworks Inc. highlights the advantages of manufacturers working together to ensure technologies operate smoothly in the real world. Taking ownership of the customer experience When Orion Entrance Control provides a SpeedGate swing-glass optical turnstile, they take full ownership of the customer’s experience. That means ensuring the turnstile application operates as it should, regardless of which component of the broader system might be at fault. To the customer experience, a card reader that doesn’t work is the equivalent of a turnstile that doesn’t work. Which component is at fault is irrelevant, and in fact, invisible, to the overall customer experience. Importance of dependable operation of turnstiles As the most visible element in many access control systems, dependable operation of turnstiles reflects positively on the manufacturer and on the entire system. Orion tests various third-party components with their turnstiles To ensure an optimum customer experience, Orion tests various third-party components with their turnstiles, in order to ensure flawless operation before a turnstile is delivered to a customer. Customers buying an Orion turnstile send the card readers they want to use to Orion’s corporate headquarters in Laconia, New Hampshire, USA, where Orion engineers ensure seamless operation. Ensuring optimum customer experience All readers are designed to be bolted to the wall rather than installed inside a turnstile In addition to scenario-based testing, readers are placed inside the turnstile for a streamline appearance, which can be a challenge given the variety of sizes and types of readers a customer might choose. All readers are designed to be bolted to the wall rather than installed inside a turnstile, which complicates adaptation efforts. In short, historically for Orion, ensuring the optimum customer experience involved extra time and effort, although obviously it was worth it. Providing flexibility for any environment Seeking to simplify the process, Orion has found an alternative to using many different types and models of card readers for its turnstiles. Deploying an RFID reader/writer from ELATEC provides flexibility to operate in a variety of card and reader environments, including almost all 125 kHz and 13.56 MHz contactless technologies. The product is compatible with low-frequency (LF), high-frequency (HF), near field communication (NFC) or Bluetooth Low Energy (BLE) signals. An integrated BLE module supports mobile ID and authentication solutions. There is an integrated antenna for LF and HF to ensure excellent contactless performance. ‘Universal’ configuration of the ELATEC reader hardware Using applicable firmware, the ‘universal’ configuration of the ELATEC reader hardware is compatible with any card system. It works with all the access control protocols, including SEOS, OSDP and other open protocols. “We can stock an open SKU and flash the firmware as per the customer requirement,” says Steve Caroselli. The small form factor (around 1 1/2 inches square) of the ELATEC module lends itself to easy installation inside the turnstile housing. Easy availability of the ELATEC readers helps Orion continue to serve customers, despite recent disruptions in the supply chain. And, ELATEC’s reader hardware has earned global certifications that enable Orion to use their products for customers around the world. Testing to ensure smooth operation ELATEC was responsive at every stage as the relationship evolved, providing sample equipment for testing Before embracing the ELATEC reader module, Orion tested it for several months to ensure compatibility with its turnstiles. ELATEC was responsive at every stage as the relationship evolved, providing sample equipment for testing and working closely with the Orion team. Everyone in the ELATEC sales and engineering team, right up the company’s C-suite, worked to support Orion during the testing phase. In the end, in addition to other advantages, ELATEC’s detection speed and read range compares favorably to competing technologies. “We move really fast as an organization, so we are looking for other organizations that move very fast,” says Steve Caroselli, adding “We met with ELATEC one week and had the equipment for testing the next week. We like to work with companies that move fast, and they are culturally aligned with how we do business.” Orion turnstiles with ELATEC TWN4 Palon Compact panel The Orion turnstiles incorporate an ELATEC TWN4 Palon Compact panel, a versatile panel-mount reader designed for integration into third-party products and devices. It supports enhanced interfaces, especially RS-485, and reflects the advantages and integrated tool support of the ELATEC TWN4 family. Orion is implementing SAFR SCAN biometric technology using hardware and software from RealNetworks Inc. “The selection of ELATEC products allows Orion to provide their customers and partners with a flexible RFID reader solution that supports numerous credential options and virtually all transponder technologies,” said Paul Massey, the Chief Executive Officer (CEO) of ELATEC, Inc., adding “This is especially valuable in multi-tenet, multi-credential environments.” Orion works with all the various stakeholders – architects, consultants, integrators, and end users – to ensure total satisfaction with an installation. Biometric technology for ‘frictionless’ access control Orion is also implementing SAFR SCAN biometric technology into their turnstiles using hardware and software from RealNetworks Inc. The facial recognition reader technology, designed for mainstream commercial access control, provides a ‘frictionless’ experience, and allows users to pass through turnstiles at a walk. The system can authenticate up to 30 individuals per minute with 99.9% accuracy, despite varied lighting conditions. SAFR’s system provides a good user experience Orion designed a mounting system to incorporate the biometric reader into their turnstile design Orion designed a mounting system to incorporate the biometric reader into their turnstile design. SAFR’s system provides a good user experience, when it comes to enrollment. On each turnstile, the SAFR technology can operate separate from the ELATEC reader or in conjunction with it for multi-factor authentication in higher-security applications. Innovation for new applications A broad approach to the customer experience reflects Orion’s positioning as a technology company, in addition to being a manufacturer of turnstiles. Their Infinity software is the ecosystem ‘nerve center’ platform to ensure operation and connected through a single ‘pane of glass.’ The need to protect more entrances beyond the lobby led Orion to develop its recently patented DoorGuard, a LIDAR-based solution that detects each person who passes through a doorway and prevents tailgating (like a turnstile) for applications, such as stairway doors, perimeter doors, data centers, IDF closets, etc. The software mimics the advantages of a turnstile to monitor access control and occupancy. Removing friction during installation and beyond Orion’s Constellation is a presence detection system that uses UWB (ultra-wideband) radar to sense where people are in a building for emergency response and building utilization applications. “One of our core values is to remove friction and make customers’ lives easier,” says Steve Caroselli, adding “Our people-first philosophy is: What can we do to make your life better? We want to be systematic, and everything must be repeatable in terms of how we react and interact with customers.”
The Global Security Exchange (GSX 2022) in Atlanta in September 2022 is the latest example of the energetic post-COVID resurgence of security trade shows. On the vibrant show flow, discussions centered on topics such as the security industry’s need for more employees and the lingering impact of a months-long supply chain crisis. Against a backdrop of continuing industry challenges, exhibitors and attendees were diverted by a wealth of new opportunities as the industry rebounded. Several major players had big product announcements at GSX 2022 in Atlanta. Manufacturers unveil the latest technology The big news at Genetec was “5.11.” That’s the newest version of Security Center, which is “all in,” i.e., providing everything Genetec offers in a single “unified” platform. The unified approach streamlines the process for systems integrators, makes quotes easier, and adds value for customers. Standard, Pro, and Enterprise versions provide video, access, and LPR “right out of the box.” Genetec is also launching a new web and mobile client for the “next generation operator.” Paid intern program Kyle Hurt says the security industry’s biggest challenge is attracting personnel Kyle Hurt, Genetec’s Senior Sales Director, North America, says the security industry’s biggest challenge is attracting personnel (even more challenging that the supply chain.) Genetec’s response is a robust paid intern program, welcoming 120 interns into various departments for a full semester. The program helps to feed Genetec’s need for new talent. “You can’t coach passion,” said Hurt. WiseNet Edge Hanwha Techwin introduced a “serverless camera” at GSX 2022, named the WiseNet Edge. It is a video camera with a built-in solid-state hard drive for storage. The camera can store its own video and take in other camera feeds. In effect, it operates like an NVR but is less expensive and with an internal solid-state drive. Video can be viewed through a cloud browser, and Hanwha’s WAVE software, loaded on the camera, enables the management of several cameras at a site. High-res video is stored inside the camera, and any information can be shared with the cloud according to the needs of the application. i-PRO Mini i-PRO launches its own Video Insight video management system and MonitorCast access control i-PRO has fully transitioned away from Panasonic and is charting its own ambitious future path. Seeking to be “bold, trusted, and flexible,” the company is releasing a raft of new products, filling in previous gaps in the line, and bringing forward new innovations, including a full complement of AI. In addition to hardware, they have their own Video Insight video management system and MonitorCast access control, which was part of the Video Insight acquisition in 2015. An i-PRO Mini is a tiny camera, smaller than a smartphone. All cameras are NDAA compliant. People are coming together “The show has been phenomenal,” said Josh Letourneau, Chief Commercial Officer, Prosegur USA. “It’s very nice to see that people are coming back. After the pandemic, we are finally in a position of coming together. Lots of organizations are coming to see us.” Intelligence-led risk management Prosegur is a global company looking to expand aggressively in the United States, creating multiple “metropolitan service areas,” where the company’s fully integrated offerings are available. What makes the company unique is its “intelligence-led risk management,” says Josh Letourneau, adding “It’s more than AI, it’s about human intelligence, too." Prosegur sees evolution and growth opportunities in the U.S. market. “We are one of the largest companies no one has heard of,” adds Letourneau. “The show seems as back to normal as possible,” said Keith Bobrosky, President of Delta Scientific, who attended the show although his company did not exhibit, adding “There seems to be a generally positive spirit about the show this year.” Physical security protocols Bobrosky sees data centers as the next big market for his company’s vehicle barriers Bobrosky’s company has worked aggressively to avoid the impact of supply chain issues, ordering plenty of extra inventory to avoid the possibility of a part running out of stock. “We got ahead of it and are past the worst of it,” he said. Bobrosky sees data centers as the next big market for his company’s vehicle barriers. “The government will mandate physical security protocols for cybersecurity locations because they house data that affects national security,” he says. Robots and indoor drones ADT Commercial highlighted robots and indoor drones for security apps at their booth. The newest versions of the humanlike robots offer extra padding, more fluid movement, and 360-degree viewing for a better virtual reality (VR) experience, including better peripheral vision. Robots can operate for four hours without a charge and “know” when to return to the charger (to “top off” every hour). Fully autonomous indoor drones can also replace guards, flying near the ceiling and generally after business hours. The use of either robots or drones can lower costs when compared to hiring human guards. Varied uses for canines in security Glen Kucera, Chief Executive Officer, MSA Security, highlighted the capabilities of canines for explosives and firearms detection. “People don’t realize the flexibility of what they can do,” he said. Kucera says canines provide a sophisticated solution to address the escalating active shooter and criminal threat. MSA Security was acquired last year by Allied Universal, adding to the company’s varied offerings for threat detection and management. Rather than individual products, Allied Universal’s emphasis at the show was on bringing solutions together. Their message: Risk is multi-dimensional and different from one client to the next. Access control Access control needs to develop more modern interfaces to compete with new technology companies AMAG’s news at the show included a new president, David Sullivan, who highlighted AMAG’s role as one of the “last independent access control companies.” He said, “The beauty of AMAG is its installed base and loyal integrator channel.” Sullivan sees changing trends in how office space is managed in the wake of the pandemic. More workplace management applications will emerge, with one of the elements being access control. Access control also needs to develop more modern interfaces to compete with new technology companies entering the market. An encouraging sign is that AMAG had its best year ever in 2021. Orion Entrance Control Orion Entrance Control showed off one of its modern new turnstiles at the RealNetworks/SAFR booth at GSX 2022. The turnstile incorporates an access control module from Elatec to update and expand card reader functionality. Using the module streamlines Orion’s processes and avoids having to update a customer’s readers individually. The turnstile at GSX also incorporated a facial recognition system from SAFR, which could be used instead of, or in addition to, the access control reader. Balancing the cloud and on-premise systems Salient Systems is looking to balance the use of on-premise and cloud systems and emphasize data instead of video. Rather than a single market, Salient sees security as a variety of smaller markets, each focused on different needs. Salient’s customers are typically larger and have multi-site deployments with thousands of cameras. On-premise systems appeal here because they offer an element of control. Open-platform APIs Internal teams at customer sites are seeking out and finding new ways to leverage the data from video systems “People have a keen interest in control and ownership of their data,” says Sanjay Challa, Chief Product Officer, Salient Systems. Internal teams at customer sites are seeking out and finding new ways to leverage the data from video systems, and some of the uses fall outside the traditional “security” market. Open-platform application programming interfaces (APIs) enable more integration with various systems, and broader applications enable customers to leverage budgets from other stakeholders in an organization. Add-on services “They’re unwilling to shift the entire solution to the cloud, but they want to leverage cloud technologies,” says Challa. For Salient, a cloud system provides remote access to monitor and service video installation remotely. “We enable the integrator to reach into your system to provide a higher level of service,” says Sanjay Challa. He concludes, “Our add-on services bring the best of the cloud to on-premise systems, and integrators don’t have to roll a truck to solve a problem with the system. We are focused on helping integrators succeed.”
As new technologies incorporate artificial intelligence (AI) and overall uses of AI continue to expand, what protections are in place to prevent its misuse? Artificial intelligence, like any technology or security measure, is not inherently bad. It can, however, be used for nefarious purposes and in ways that were never intended or thought of. ‘Responsible AI Policy’ to protect users Prosegur has created a ‘Responsible AI Policy’ to protect users from potential AI threats As an AI company, Prosegur has created a ‘Responsible AI Policy’ to protect users from potential AI threats, and to prevent employee and partner misuse of AI-enabled technology, with guard rails in place to hold them accountable, if artificial intelligence is being used nefariously. “Any security or similar company that utilizes AI with its products should monitor for potential misuse and implement a similar policy for protection,” contends Mike Dunn, the Chief Technology Officer (CTO) at Prosegur USA. Requirements of Prosegur’s ‘Responsible AI Policy’ include: Human action and oversight - Prosegur heavily monitors their agents using an integrated international security operations center (iSOC). Floor and shift supervisors ensure that everything is working properly and that incidents are handled. They also ensure employees are logging into AI-enabled cameras and other technologies for the right reason. Transparency - As with any new company-wide policy, Prosegur wants to ensure that every employee learns about the policy and their duties to uphold it. “In doing this, we are making sure that all processes involving AI development are transparent, so any employee can understand and implement the policy into these processes,” says Mike Dunn. Non-discrimination and equity - Prosegur seeks to make sure employees are using AI-enabled technology to look for known criminals, for example, and not profiling or singling people out. Having a policy in place ensures agents are aware. Accountability - The most important part of the policy is to hold people accountable, if AI-enabled technologies are misused. Violation of the policy will result in disciplinary actions, which can range from HR (Human Resources) intervention to possible suspension. For partners, Prosegur would cease and desist using their products immediately upon finding out about any misuse. Leading the charge for ethical AI practices Prosegur is proud to lead the charge for ethical AI practices, by creating this first policy of its kind" “Prosegur is proud to lead the charge for ethical AI practices, by creating this first policy of its kind, and we hope that other security organizations follow suit,” says Mike Dunn. Technology can do wonderful things. In security, technology can help to stop crimes and even to prevent them from happening with deterrents and alarms. Important to take action to stop ‘bad actors’ However, as with any industry or group of people, there will be ‘bad actors.’ Mike Dunn said “It is important to take actions to stop those people, but it is also important not to condemn all technology or practices when this happens.” Even proven, effective technologies can be used for bad (as well as good). An example is TSA Scanners at the airports. They were designed to provide safer air travel, picking up things that normal metal detectors could miss. Misuse of AI technology can cause lot of harm However, it came to light that a few ‘bad actors’ were using this technology and sharing silhouetted nude pictures of passengers. This has since been patched and fixed, but nonetheless, it’s a great example of how misuse can break people’s trust. As a whole, technology can be dangerous. If not used as intended, it can be used to hurt people. The U.S. government has found that China was using facial recognition and demographic analytics to classify and identify people, based on their ethnicity and that technology singled them out for tracking. Important to ensure analytics and AI used as intended As a society, I think it’s important for us to take that first step and self-police any use of these analytics" “As a society, I think it’s important for us to take that first step and self-police any use of these analytics,” said Mike Dunn, adding “At a minimum, (we should) set policies and procedures to make sure these analytics and AI are being used as intended.” As use of artificial intelligence (AI) continues to increase, an industry standard would ensure companies have protections in place for their employees, clients, and partners. Having a policy is the first proactive step in ensuring AI protections. However, companies need to enforce accountability too. Effectively handle security threats and vulnerabilities Mike Dunn continues, “By heavily monitoring for unethical AI practices and enforcing disciplinary actions when needed, companies will be better prepared to handle security threats and vulnerabilities.” At Prosegur, monitoring agents are heavily trained, taught procedures and then closely supervised by several methods. “This is something that should be common practice in the security industry,” says Mike Dunn, adding “We have employed a compliance officer to help us stay ahead of the curve. Fortunately, we have seen many manufacturers and end users adopt this practice as well.” Compliance officers can act faster than new laws enacted Compliance officers can act faster than new laws being enacted, and often will hold their company to higher standards than a minimum threshold. Mike Dunn concludes, “Putting a responsible AI procedure in place is Prosegur’s way of taking on this problem we see in our everyday work.”
Case studies
Xtract One Technologies announced its SmartGateway has been selected by Nova Scotia Health to strengthen security measures and provide AI-powered weapons detection across facilities province-wide, with an initial order of 25 systems. Nova Scotia Health, in tandem with its nurses’ union, is working to modernize and strengthen security across its facilities to ensure a safe environment for all patients, visitors, and staff. Adopting and deploying advanced technologies like SmartGateway is an important step toward achieving that goal. Safe and secure health care By helping to limit the number of potentially dangerous items entering their hospitals, this technology supports its commitment to providing safe and secure health care. Xtract One was selected for its proven efficacy to accurately detect knives, a top priority for the organization. Previously tested in Truro, Nova Scotia, over a 12-day trial period, SmartGateway successfully scanned 7,400 individuals entering the facility and detected 49 prohibited items during that period, mostly pocket knives and box cutters. Deploying SmartGateway “Violence against healthcare workers is a challenge that persists and demands addressing. By deploying SmartGateway, Nova Scotia Health is setting an important example for what it means to take meaningful action to protect frontline healthcare workers, patients, and visitors,” said Peter Evans, CEO of Xtract One. “This installation marks another key step in our expanding work with Canadian healthcare organizations, having deployed in Manitoba earlier this year. We look forward to continuing to deliver effective threat detection as more providers take proactive measures to prioritize security and peace of mind for their teams.” Overall approach to security “Our goal is to deliver first class healthcare, and ensuring the safety of all who enter our facilities is a critical step in providing that service,” said Dean Stienburg, Director of Security for Nova Scotia Health. “With SmartGateway, we’re making tangible strides in bolstering our overall approach to security. We were impressed by the system’s effectiveness during the trial period and are looking forward to the deployment helping us mitigate and respond to the threats of today’s environment.” Maximising security screening outcomes SmartGateway delivers fast, discreet, and accurate individual screening, utilizing AI-powered sensors to unobtrusively scan for weapons and other prohibited items upon entry. This technology replaces intimidating, traditional metal detectors and mitigates the need for individuals to remove personal items. This prioritizes individual privacy and comfort, all while maximizing security screening outcomes. SmartGateway is designed to enable seamless passage through checkpoints and promote the uninterrupted flow of movement.
Allied Universal®, the world’s pioneering security and facility services provider, has been selected by Seton Hall University™ to provide campus security programs. This moves strengthens the University’s commitment to providing a safe, secure, and welcoming environment for students, faculty, staff, and visitors. New security program Allied Universal will deliver comprehensive campus security services, including trained personnel, safety patrols, and emergency response support. The new security program is designed to enhance the University’s existing safety infrastructure, while helping to ensure that the campus community benefits from Allied Universal’s expertise in proactive risk management and security operations. New partnership “On behalf of Allied Universal, I want to express our sincere appreciation for this new partnership and for our shared commitment to creating a safer campus community,” said Steve Jones, Allied Universal Global Chairman and CEO. He adds, “As the pioneering security provider for higher education, we are excited to have been chosen to work with Seton Hall University as a higher education campus safety partner.” Seton Hall’s ongoing commitment The selection of Allied Universal builds on Seton Hall’s ongoing commitment to campus safety, combining the University’s strong public safety framework with Allied Universal’s proven expertise in higher education security. Together, the collaboration aims to provide a proactive, community-focused approach that reinforces a secure, welcoming environment for everyone on campus. Seton Hall’s mission “Allied Universal brings deep experience supporting higher education institutions across the country,” said Sergio Oliva, Associate Vice President for Public Safety and Security, adding “Their approach emphasises professionalism, training, and engagement with the communities they serve, values that align closely with Seton Hall’s mission and our own Public Safety philosophy.”
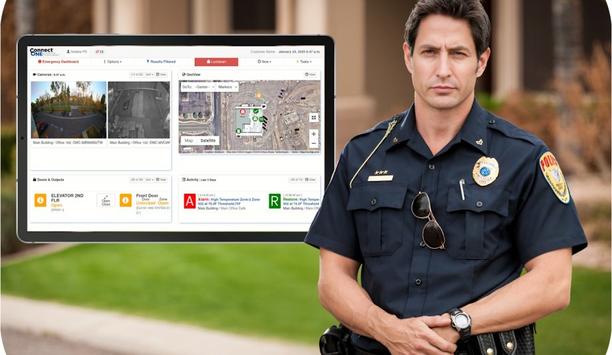
In an emergency, first responders, School Resource Officers (SROs), and responsible parties need to gain access to campus buildings to assess alerts and potential threats. With Connect ONE®’s new Emergency Response Platform (ERP), included with any service level at no additional charge, first responders and SROs can view cameras, unlock doors and outputs, activate task functions, initiate lockdown and see recent activity. Connect ONE ERP Connect ONE ERP unifies multiple school systems into one interface without separate site log-ins The Connect ONE ERP unifies multiple school systems into one interface without separate site log-ins. Integrators can offer 911 and dispatch centers viewing and access control of schools to assist responders during critical threats. The cloud platform ERP provides a separate agency login with specific designated permissions for first responders, who can only see customer site locations shared by the security dealer. Emergency Response Platform “The Emergency Response Platform allows Connect ONE dealers to partner with local law enforcement by providing the tools they need to diffuse an emergency quickly and effectively with powerful information to view and control facility security,” said Dan Simon, Technical Director, Connected Technologies. He adds, “It’s a great solution to heighten safety and create safer experiences for the public, while ensuring you keep a customer long-term with a valuable service.” ERP: Use-case in action Nightwatch Security & Telephone LLC has executed the ERP at several of the area’s school districts Nightwatch Security & Telephone LLC, Sedalia, Mo., has implemented the ERP at several of the area’s largest school districts serving more than 5,000 students. Nightwatch Owner, Jeff Kesterson said it’s simple to update proximity key fobs and input agency officer’s access codes to stay current with staffing changes or modifications to permissions. “First responders and SROs maintain access to schools with proximity access control key fobs, but staying current with staffing changes was unwieldy before the ERP,” said Jeff Kesterson. Key fob credentials The Sedalia Police Department, which has access to schools in the city, said the ERP is a huge timesaver for administering key fob credentials. “Ease of administering credentials was important and adding or removing personnel from the system was clunky before the ERP. Instead of logging into all the school systems separately, we can look at everything in one place,” said Commander Joshua Howell, Operation’s Support Bureau, Sedalia Police Department. Connect One’s GeoView System Mapping Viewing and controlling options are also available via Connect One’s GeoView System Mapping Viewing and controlling options are also available via Connect One’s GeoView System Mapping – a real-time Google mapping feature, which adds the capability of seeing floor plans of the building along with point and click control of doors and cameras. Dispatch can easily respond to officers on-site and unlock doors for quick entry by clicking on GeoView’s map and door icon. Other features of the ERP A single application screen to add or remove agency personnel system codes/access credentials from shared customer systems. System codes are included in profile templates, so permissions come pre-defined for simple additions by the agency. Permissions may only be modified by the dealer to prevent misconfiguration; customers will maintain the ability to view the permissions without making changes. Activity by agency personnel is reviewable by the customer in reporting and notifications. Integrates with leading intrusion, access control, video, fire, temperature, humidity, MNS, environmental and weather systems. Connect ONE and the ERP is the unified, cloud management platform for schools that’s making a difference with easier access while increasing situational awareness.
Interface Systems, a pioneering managed service provider delivering business security, actionable insights, and purpose-built networks for multi-location businesses, announced the successful completion of a major security upgrade for Bethesda Community Church and Bethesda Christian School in Fort Worth, Texas. Serving more than 530 students from preschool through 12th grade, Bethesda Christian School is recognized among the top private schools in Texas. Modern safety and security systems High level of activity required modern safety and security systems to protect students Between church services, school operations, and community events, the multi-building, 26-acre campus welcomes hundreds of people daily. This high level of activity required modern safety and security systems to protect students, staff, and parishioners while simplifying daily operations. Bethesda’s aging fire alarms, intercoms, and CCTV system were increasingly unreliable, creating false alarms and communication challenges. To address these concerns, the church turned to Interface to modernize its infrastructure. Deployed an integrated solution Interface designed and deployed an integrated solution that included: Fire Alarm System: Replacing the outdated system with a modern fire alarm system that communicates urgency effectively without causing unnecessary panic, particularly important for schoolchildren. Managed Access Control: Introducing a modern system that makes it easier for administrators to manage entry to the campus. The cloud-based setup means they can grant or restrict access remotely, without having to manage complex on-site servers. Video Surveillance Upgrade: Installing a 64-channel IP camera system on the new school building, with expansion capability to replace legacy analog cameras over time. The system provides remote monitoring and allows staff to verify alarms with live video before responding, helping to reduce unnecessary dispatches. Intercom and Paging: Replacing the outdated intercom with a flexible IP-based system that supports school bell scheduling, room-to-room communication, and all-campus announcements. It also integrates with access control, giving administrators a simple way to manage visitor entry. Remote access to cameras and alarms The installation was carefully phased to minimize disruption to classes and worship services “The new system is effective. It gets the point across that it’s time to evacuate, but it doesn’t create panic, especially among the kids,” said Rick Campbell, Facilities Manager at Bethesda Community Church. “Having remote access to cameras and alarms has been a huge help.” The installation was carefully phased to minimize disruption to classes and worship services. “Interface worked around the kids and kept us up and running during installation,” Campbell added. “The integration was seamless, and now everything is running smoothly.” Interface’s upgrades With Interface’s upgrades, Bethesda has significantly reduced false dispatches, streamlined communication across the campus, and gained the ability to scale its systems for future growth. “Initially, we were unsure about the cost, but the investment has been well worth it,” Campbell concluded. “I’d recommend Interface to other churches without hesitation.”
A.C. Camargo Cancer Center, a pioneering oncology treatment center in São Paulo, Brazil, recognized for its history of innovation, announces that its partnership with Axis Communications has produced savings of more than $2 million over its first two years, all of which will be reinvested in patient care. A.C. Camargo has deployed more than 2,000 state-of-the-art video surveillance cameras throughout the Center’s corridors, complex care units, and parking lots, embracing a more holistic approach to security that emphasizes patient and employee safety along with improved quality of service. Hospital’s security infrastructure Founded in 1953, A.C. Camargo treats an estimated 100,000 patients annually and is one of the world’s largest healthcare institutions and a pioneering provider of cancer treatment and research. Prior to partnering with Axis, financial losses due to theft were a growing concern for A.C. Camargo The Center is not just a hospital, but a comprehensive care platform that includes prevention, investigation, staging, treatment, palliative care, and rehabilitation services for all types of cancer. Prior to partnering with Axis, financial losses due to theft were a growing concern for A.C. Camargo, and hospital pioneers sought to transform the hospital’s security infrastructure in a way that would both enhance its security posture and streamline patient care and services. Advanced new video surveillance devices “Nearly 15,000 people pass through our entrances each day, and caring for those patients extends far beyond operating or patient rooms,” said William de Souza, Corporate Manager at A.C. Camargo Cancer Center. “By deploying advanced new video surveillance devices, we are enabling our security teams to maintain round-the-clock vigilance and our medical personnel to provide the highest quality of care to our patients." "With cameras monitoring all areas, including cafeterias and parking lots, we are always looking for potential warning signs—even after patients have been discharged. If anything seems amiss, we can alert our team that additional medical care may be needed.” Key national and international certifications The Axis devices are equipped with video analytics that allow the Center to go beyond asset protection. These analytics are deployed with a high degree of sensitivity to ensure high-quality care for patients, their families, and the nearly 6,000 staff members on-site daily, while also protecting their privacy. Axis cameras have enabled the A.C. Camargo Center to improve operations and meet key national and international certifications through: Increased Operational Efficiency: The system enhances operational efficiency by proactively detecting critical issues such as power outages, water leaks, and equipment malfunctions – including refrigerators used for medication storage. This early detection helps prevent medication loss and limit downtime. Additionally, the system can identify nitrogen leaks and immediately trigger luminous alerts, enabling staff to respond quickly and prevent potentially hazardous situations from escalating. Optimized Parking Management: With more than 300,000 vehicles passing through the Center’s parking facilities each year, traffic management is critical. The new system helps streamline the process by automatically identifying license plates belonging to authorized vehicles. Enhanced Patient Care: By providing continuous monitoring in critical areas, such as surgical centers, and delicate procedure rooms, like cellular medicine and pathology, the system enhances patient safety while maintaining strict compliance with privacy regulations. Emergency Management Solutions: Cameras throughout the facility are equipped with analytics that detect falls and suspicious behavior and can even assist in identifying and preventing situations where individuals in distress might harm themselves. Integrating video surveillance cameras Both A.C. Camargo and Axis Communications remain committed to further implementing solutions “The implementation of Axis solutions at A.C. Camargo Cancer Center underscores what is possible when innovation is paired with a deep commitment to care,” said Carlos Machado, End Customer, Key Account Manager, Brazil at Axis Communications. “By integrating video surveillance cameras enhanced with analytics, the Center has made safety a central pillar of its operations, allowing staff to fully focus on what matters most: the health and comfort of their patients. By doing so, hospital leadership has set a compelling example for other institutions facing similar challenges.” Improvement in patient outcomes After initially implementing 300 cameras, A.C. Camargo quickly noticed a difference. The Center moved to further scale the system, adding hundreds of additional cameras to achieve greater coverage throughout its facilities. Now, there are a total of 2,100 cameras throughout the seven buildings that make up the Center. Looking to the future, both A.C. Camargo and Axis Communications remain committed to further implementing solutions that support continuous improvement in patient outcomes and operational effectiveness.
Genetec Inc., the global pioneer in enterprise physical security software, announced that Brigham Young University's (BYU) has optimized its security operations with the Genetec™ Operations Center work management system. Located on a 560-acre campus in Provo, Utah, BYU is home to nearly 34,000 students and over 5,000 faculty and staff. Enhancing campus security A robust security team of officers, supervisors, trained students, and staff ensures campus safety The university’s robust security program includes 25 sworn officers, 15 security supervisors, and up to 400 student employees trained through its Security Academy. To better coordinate multiple departments and manage a broad range of responsibilities, BYU sought a solution that would unify operations and improve efficiency. Simplifying operations The Genetec Operations Center is integrated with BYU’s existing Security Center platform, enabling the university to consolidate tasks like dispatching, work ticketing, and activity tracking into a single system. This streamlined approach replaces disconnected tools and manual processes, helping teams collaborate more effectively and maintain clear visibility of their operations. With Operations Center, BYU has automated several key processes. For example, routine tasks such as nightly code checks across campus divisions, equipment inspections, and building audits are now scheduled and managed automatically. This reduces the workload on dispatchers, minimizes the potential for errors, and ensures tasks are completed consistently. The mobile app also enhances situational awareness for field officers, providing real-time updates on assignments and facilitating compliance with operational procedures. Flexible and customisable workflows Operations Center ensures tasks are completed efficiently while reducing the learning curve The flexible design of Operations Center allows BYU to customize workflows and reports to suit specific departmental requirements. From tracking officer locations to managing inventory and generating incident documentation, the platform adapts to support the diverse needs of the university’s security teams. The system has also streamlined onboarding processes for new staff and student employees. By offering intuitive tools and tailored workflows, Operations Center ensures tasks are completed efficiently while reducing the learning curve for new team members. Enhancing collaboration and efficiency The implementation of Operations Center has significantly improved BYU's ability to coordinate security efforts, enhance communication, streamline data sharing, and centralize documentation and auditing processes. Automation of routine processes, such as inspections and daily reporting, reduces manual effort, freeing teams to focus on higher-priority responsibilities. "First-time users of Operations Center immediately see how it benefits their organization—no extensive training required. It delivers quick and accurate results. Without Genetec, I can't imagine how we’d manage all this information,” says Chris Autry, Managing Director of BYU Police and BYU Security.


Round table discussion
Headlines of violence in our schools are a reminder of the need to keep educational institutions safe. In fact, if there is a positive aspect to the constant bombardment of headlines, it is that it keeps our attention perpetually focused on how to improve school security. But what is the role of physical security systems? As the new school year begins, we asked this week’s Expert Panel Roundtable: Are schools safer because of physical security systems? Why or why not?
As physical security technologies become more complex, it is incumbent on the dealer/integrator to have the skills and expertise needed to ensure that a system operates smoothly. The value of integrators increasingly rests on the skill sets they bring to bear when installing a system. If the skills are missing, there is a problem. We asked this week’s Expert Panel Roundtable: What missing skills among security integrators can cause problems for customers?
Driving the smart homes market is the convenience of simple technology solutions. Almost every home now has a “smart speaker” that makes it easier than ever for homeowners to interface and control their technology. But where does security fit into the new landscape of smart home systems? We asked this week’s Expert Panel Roundtable: What’s new in smart homes and residential security systems?
Products
White papers

The Ultimate Guide To Mastering Key Control
Download
Securing Care Closer To Patients
Download
Video Technology Strategies For Hospitals Are Moving Beyond Security
Download
Modernizing Facilities Management
Download
5 Ways To Strengthen Physical Security With An Integrated System
Download
How Analytics Engines Mitigate Risk, Ensure Compliance And Reduce Cost
Download
Preparing Your Organization With Quality Situational Awareness
Download
Is Your Access Control As Effective As You Think?
Download
Is Your Access Control System as Secure as You Think?
Download
High-Security Electromechanical Locking Solutions For Critical Infrastructure
Download