Cyber security - News
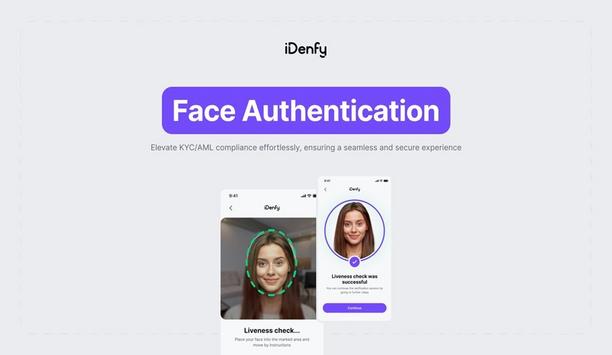
iDenfy, a Lithuania-based RegTech solutions provider best known for its variety of KYC tools, has launched a new Face Authentication service. The new cutting-edge technology is designed to detect fraudulent biometrics and add extra protection without unnecessary friction to the end user. Face Authentication enables online platforms to create a more secure network by flagging suspicious activities in real time, helping to prevent fraud at every stage of the customer journey. Face Authentication...
Matrix, a prominent pioneer in the Security and Telecom sector, has wrapped up its successful participation at FSIE 2024 in Mumbai. Drawing on more than three decades of industry expertise, Matrix connected with industry peers gained valuable insights, and explored new opportunities for collaboration. Technology-driven solutions Matrix is resolute, in its commitment to delivering technology-driven solutions with a strong focus on customer satisfaction. This dedication is reflected in th...
A North East tech specialist has doubled sales revenues in the last 12 months following a raft of major contract wins across the region’s manufacturing, hospitality, and education sectors. Providing technology support services including cybersecurity, data networks, and IP camera and access control systems to regional and national organizations from its Follingsby Park-based head office, Advantex has seen turnover increase to £12 million in FY24. DMARC service The firm, which al...
Cyware, the pioneer in threat intelligence management, security collaboration, and orchestrated response, announced the appointments of Sachin Jade as Chief Product Officer and Ashok Kumar as Head of U.S. Engineering. Sachin Jade Sachin Jade joins Cyware as the Chief Product Officer. Sachin’s experience stems from both the entrepreneurial world & Fortune 100 firms. Sachin has been involved in the risk and security space, is extremely customer-centric, and brings a customer lens to s...
Node4, a cloud-led digital transformation Managed Services Provider (MSP), has announced a strategic partnership with cybersecurity company Elastio. This collaboration is set to provide Node4 customers with enhanced protection against ransomware by ensuring the integrity of Veeam recovery points, minimizing post-attack data loss and downtime. Backups are crucial for protecting against ransomware, but modern threats can infiltrate and hide within data without being detected. This can lead...
Capital.com, the high-growth retail trading platform, and global fintech group has announced the launch of its public bug bounty program hosted on the crowdsourced security platform, Intigriti. This initiative highlights the company’s proactive approach to cybersecurity and commitment to maintaining the highest standards of cybersecurity and the safety of its users' assets and data. Bug bounty program The bug bounty program invites security researchers and ethical hacker...
Convergint, a global pioneer in systems integration, announced the expansion of its Middle East & Africa (MEA) operations into Saudi Arabia. Security, IT infrastructure, and AV The company will offer customers a comprehensive suite of advanced solutions in security, IT infrastructure, and audio-visual systems. With the largest technical workforce in the market, including 10,000 colleagues across 220 global offices, Convergint leads the industry in developing seamless, next-generatio...
SailPoint Technologies, Inc., a pioneer in unified identity security for enterprises, announces that the company was named an Overall Leader, Product Leader, Innovation Leader, and Market Leader in the latest Leadership Compass Identity Governance and Administration (“IGA”) report from KuppingerCole Analysts AG. Identity lifecycle management The report provides an overview of the IGA market, as well as a compass to help businesses identify the right vendor and solution to meet thei...
Quod Orbis, the London-based Continuous Controls Monitoring (CCM) firm, has announced a strategic partnership with YASH Technologies, a global IT solutions and services partner. The partnership will see businesses benefit from holistic monitoring solutions with real-time visibility across their entire IT infrastructure, encompassing cybersecurity risk management and compliance. Enhanced performance YASH Technologies has a proven track record in delivering battle-tested consulting, technology,...
Check Point® Software Technologies Ltd., a pioneering AI-powered, cloud-delivered cyber security platform provider, has published its Global Threat Index for July 2024. Despite a significant drop in June, LockBit re-emerged last month to become the second most prevalent ransomware group, while RansomHub retained the top spot. Meanwhile, researchers identified both a campaign distributing Remcos malware following a CrowdStrike update issue, and a series of new FakeUpdates tactics, which...
Over half (54%) of Chief Information Security Officers (CISOs) feel their security team is unprepared for evolving AI-powered threats, according to research from Absolute Security. The findings were uncovered in the Absolute Security United Kingdom CISO Cyber Resilience Report 2024 which surveyed 250 UK CISOs at enterprise organizations, via an independent polling agency Censuswide, to assess the state of cyber resilience, AI, and the cyber threat landscape in the UK. NCSC findings According...
Over the last several years, cyber security, a crucial component in any servicer's operation, has taken on an increasingly visible role due to numerous high-profile data breaches impacting various industries. According to the cyber security research firm Check Point Research, the average number of cyber attacks per organization per week rose 38% in 2022 from 2021, and increased by 28% in the six-month period ending March 31, 2024. The average number of weekly events has also grown year ov...
Matrix, a pioneer in advanced security and telecom solutions, is pleased to announce its participation in FSIE 2024, taking place from August 22nd to 24th at the Jio World Convention Center, Mumbai. This prestigious event will serve as a platform for Matrix to showcase its innovative solutions in IP Video Surveillance, Access Control, Time-Attendance, and Telecom technologies. Transforming security and communication Ruggedized IP Camera At FSIE 2024, Matrix will showcase its comprehens...
Cequence, a pioneer in API security and bot management, is proud to introduce revolutionary advancements to its Unified API Protection (UAP) platform. These enhancements mark a significant milestone in API security, specifically tailored to support the secure use of AI applications like Generative AI and Large Language Models (LLMs). Cequence’s solutions protect applications deployed in the cloud, on-premises, and hybrid environments, and also support serverless environments, ensuring an...
CovertSwarm, a global ethical hacker, red team, and cybersecurity solution provider, launched its Academy Program last September and is welcoming its second intake at the same time this year. The first iteration of the Academy Program proved to be a huge success, with all three academy members kick-starting successful ethical hacking careers at CovertSwarm. The program aims to make careers in cybersecurity more accessible, providing a clear pathway for individuals from any background to receive...
DigiCert, a provider of digital trust announced its speaker lineup for its World Quantum Readiness Day event, set to take place virtually on September 26, 2024. Announced on the eve of RSAC 2024, the event is an opportunity to gain strategies that will help safeguard organizations and accelerate their path to preparedness for the quantum era. Quantum computing “Quantum computing is transforming the landscape of digital security, and we are excited to help organizations prep...
CyberSecurity Malaysia (CSM), the national cybersecurity specialist agency under the purview of Malaysia’s Ministry of Digital signed a Memorandum of Understanding (MoU) with Flexxon and AI MSP. Flexxon is a global pioneer of AI-powered hardware security solutions, and AI MSP is an IT and cybersecurity company that offers Flexxon’s X-PHY AI Cybersecurity Solutions and professional services in Malaysia. Digital transformation The MoU aims to establish a comprehensive framewor...
Rubrik, Inc., the Zero Trust Data Security™ company, announces a new partnership and technology integration with Mandiant, part of Google Cloud. The collaboration brings together pioneers in data security, incident response, and threat intelligence, aiming to expedite customers’ threat detection and path to cyber recovery. “This partnership will gations leveraging Rubrik’s backup solutions to identify threats in their backups powered by Mandiant’s industry-pio...
Rapid7, Inc., a pioneer in extended risk and threat detection, announced the release of its Ransomware Radar Report in conjunction with the company’s presence at Black Hat USA. The all-new research report provides a fresh perspective on the global ransomware threat by analyzing, comparing, and contrasting attacker activity and techniques over an 18-month period ending June 30, 2024. According to the report, ransomware groups continue to refine their craft, building and scal...
SaaS Alerts, a cybersecurity company delivering an automated software-as-a-service (SaaS) security platform that enables managed service providers (MSPs) to detect and stop unauthorized activity in client SaaS applications, announced the integration of Microsoft Defender for Endpoint into its SaaS security platform. Integrating Defender into the SaaS Alerts platform provides MSPs with a single pane to view Microsoft’s Identity monitoring, Microsoft 365 application suite, and the endpoint...
Commvault, a provider of cyber resilience and data protection solutions for the hybrid cloud announced an expansion of its cyber and data security ecosystem through strategic integrations with an array of security partners: Acante, Dasera, Google Cloud, Splunk, and Wiz. Cyber resilience These integrations play a key role in helping joint customers advance cyber resilience in a variety of ways across on-premises, hybrid, and cloud environments from identifying potential th...
Censys, the pioneering Internet Intelligence Platform for Threat Hunting and Attack Surface Management, announced the Censys Community Forum, a moderated, online platform for security professionals to discuss topics focused on threat hunting, attack surface management, general security expertise, and more. Designed with security professionals in mind, the space provides over 70,000 members with free resources and data-driven security solutions through a centralized, accessible platform. Securit...
Lucid Software, the pioneer in visual collaboration software announced the launch of Enterprise Shield, an enhanced layer of fortified security and granular control that organizations can add to Lucid’s already highly secure platform. Safeguarding data "Our customers are building incredible things, with many working in highly regulated industries with very sensitive material that requires their intellectual property to be protected at the highest level,” said David Torg...
Cohesity, a pioneer in AI-powered data security and management, extended its first-mover advantage in GenAI detection and recovery capabilities with the addition of significant new enhancements to the Cohesity Data Cloud. These improvements allow customers to use Cohesity’s built-in AI capabilities to rapidly detect, investigate, and address potential threats within their environment, enabling them to restore operations far more quickly. New enhancements to Cohesity’s threat detect...
Genetec Inc., a pioneering technology provider of unified security, public safety, operations, and business intelligence solutions, announced that the lawsuit filed by Sensormatic against Genetec had ended definitively in the company's favor with Genetec exonerated of any patent infringement and with the court awarding Genetec attorney fees. Sensormatic Electronics, LLC, a subsidiary of Tyco International, which is now merged with Johnson Controls, filed suit against Genetec in Delaware in June...
Regula, a developer of forensic devices and identity verification solutions, prepared a dedicated package of expert articles focused on document verification, tailored to meet the needs of carriers, border verification authorities, the hospitality industry, and businesses during the 2024 Olympics. These resources aim to address the unique challenges posed by the influx of international visitors, ensuring seamless and secure experiences for all. security and Access management France...
Bugcrowd, the pioneer in crowdsourced security, has signed Dubai-based Axon Technologies as a value-added partner in the EMEA market. Axon Technologies AXON specializes in managed security services, SOC consulting, security engineering, advanced testing, and incident response services. It has more than 60 customers in 12 countries across financial services, healthcare, government, and other verticals, with a particularly strong presence in its UAE base and Saudi Arabia. Bugcrowd...
Hanwha Vision, the global vision solution provider, has launched the TNO-C8083E, its first explosion-proof camera with artificial intelligence. The compact 5MP explosion-proof AI model features AI object detection and classification alongside intelligent video analytics. It has a wide range of explosion-proof certifications, including IECEx, ATEX, KCs, and JPEx, making the camera ideal for environments at a higher risk of an explosive atmosphere due to gas or dust - such as oil refineries, gas...
Check Point Research (CPR) releases new data on Q2 2024 cyber attack trends. The data is segmented by global volume, industry, and geography. These cyber attack numbers were driven by a variety of reasons, ranging from the continued increase in digital transformation and the growing sophistication of cybercriminals using advanced techniques like AI and machine learning. Need for robust cyber security Economic motivation for income from attacks like ransomware and phishing as well as attacks f...
Sophos, a global pioneer of innovative security solutions for defeating cyberattacks announced that Teresa Anania has joined the company as Chief Customer Officer (CCO). Anania will play a key role in accelerating Sophos’ customer and partner success initiatives to maximize the value of Sophos’ portfolio of cybersecurity solutions and services, including Managed Detection and Response (MDR) services and endpoint, network, email, and cloud security. Teresa Anania Anania has more th...