Cyber security - News
With the ever-changing post coronavirus (COVID-19) world, the ability to communicate virtually has never been more important. This is why ASSA ABLOY Opening Solutions UK & Ireland is improving its customer experience with the launch of the ASSA ABLOY Customer Support app. ASSA ABLOY Customer Support app Free to download on Apple and Android mobile devices, the app enables customers to quickly and conveniently contact the right customer service team within ASSA ABLOY in the UK. The app prov...
Check Point Research, the Threat Intelligence arm of Check Point Software Technologies Ltd., a renowned provider of cybersecurity solutions globally, has published its latest Global Threat Index for October 2020. Researchers reported that the Trickbot and Emotet trojans continue to rank as the top two most prevalent malware in October, and that the trojans have been responsible for the sharp increase in ransomware attacks against hospitals and healthcare providers globally. File-encrypting rans...
Eagle Eye Networks, a pioneer in cloud video security, publishes their latest whitepaper ‘Smart Cities: Cloud Video for Connected, Secure Cities.’ A valuable resource for city leaders looking to build a smart infrastructure, the paper delves into applications, public use, key technology requirements, and smart city engineering and architecture. “Recent successes have shown that cloud-based solutions are indispensable elements of smart city infrastructure, which includes both p...
Sectigo®, a provider of automated digital identity management, embedded security, and web security solutions, and Green Hills Software, the pioneer in high-assurance operating systems, have announced a global reseller agreement. The agreement enables Green Hills Software to offer Sectigo's Icon LabsTM Embedded Firewall, integrated and optimized for use with Green Hills Software’s INTEGRITY® real-time operating system (RTOS) and its embedded high-performance TCP/IP v4/v6 host and r...
3xLOGIC, the globally renowned provider of server and cloud-based technology, has announced the launch of its VIGIL suite of video solutions, across the UK, Europe, Middle East and Africa (EMEA) regions. VIGIL suite of video solutions The ecosystem, comprising software and hardware components, such as cameras, recorders, thermal imagers, people counters, and accessories, is designed to provide a scalable security solution that’s tailored to every business need. Business executives have...
MicroWorld Technologies Private Limited has signed a Memorandum of Understanding (MoU) with the Indian Computer Emergency Response Team (CERT-In), Ministry of Electronics and Information Technology, Government of India for collaboration in the area of cyber security. Social security Through this MoU, CERT-In and MicroWorld Tech Private Limited propose to work together to enhance the overall security of the computing environment in India and to address the increasingly complex problems associat...
Ping Identity Holding Corp., the Intelligent Identity solution for the enterprise, announced that it has acquired Symphonic Software, a provider of dynamic authorization for protecting APIs, data, apps and resources through identity. Dynamic authorization gives IT teams ultimate flexibility to control what users can see and do, enabling enterprises to more easily prevent fraud, improve cybersecurity, and comply with regulations. Over the past two years Ping Identity and Symphonic have enjoyed a...
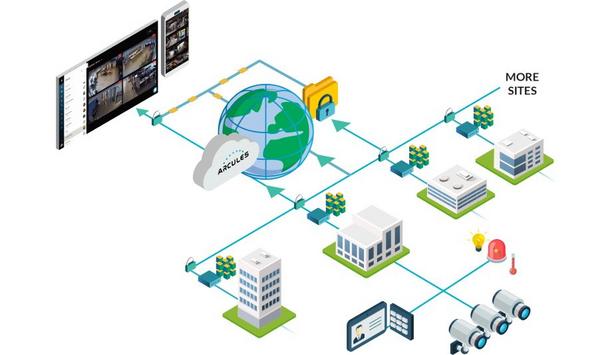
Arcules, the globally renowned provider of unified, intelligent security-as-a-service solutions, has announced the addition of its new Edge Cloud solution to its platform, which will address the changing needs of an organization’s video surveillance and security data capture and storage. Arcules Edge Cloud solution With the introduction of the Arcules Edge Cloud solution, businesses now have the ability to store all video data locally to address low-bandwidth challenges and usage for the...
Vanderbilt Industries US has utilized the company’s engineering expertise to create efficient and effective Recurring-Monthly-Revenue (RMR) security solutions. RMR security solutions RMR results in systems that are as simple to fit as they are to use. Not only are these systems easy to specify and secure to setup in moments, but they also guarantee a recurring monthly revenue stream. Below are some of the most standard frequently asked questions regarding Recurring-Monthly-Revenue (RMR)...
NEC Corporation and Cyber Defense Institute, Inc., an NEC Group company, announced their support for the INTERPOL Digital Security Challenge (DSC), a virtual cybercrime investigation event that took place from October 12 to 16. During the event, cybercrime investigation officers and experts in digital forensics from 50 countries came together to tackle a complex cybercrime scenario by exchanging knowledge and expertise. The DSC aims to improve the cybercrime investigation capabilities of the po...
Boon Edam introduces a new touchless button retrofit package suitable for all their automated revolving door models. With the Coronavirus having a lasting impact on the behavior of people interacting with products in public environments, and the emphasis on health and safety – there is a responsibility to cater to these changing global demands. Automatic revolving doors are excellent examples of naturally touchless entrance solutions, using advanced approach and safety sensors to begin mo...
Euralarm, the European association of the fire safety and security industry, has commented on the upcoming delegated act (DA) for internet-connected and wearable radio equipment, as part of the Radio Equipment Directive. The comments and proposals are given in view of the activation of the delegated act pursuant to article 3(3) of the RED (d, e and f) and cover the scope of the delegated act, the definition of ‘internet-connected devices’ and the implementation period. Relevant tec...
Ping Identity, the intelligent identity solution for the enterprise, announces PingZero, a suite of passwordless authentication features organizations can implement to deliver seamless digital experiences to employees and customers. By eliminating login friction, including the need for usernames and passwords, PingZero boosts employee productivity, improves customer retention and acquisition rates, and strengthens cybersecurity defenses — all with zero passwords and zero friction. PingZer...
Getac Technology Corporation (Getac), a globally renowned company in rugged computing and IT solutions, has announced that it is bringing integrated LiFi (Light Fidelity) technology, powered by PureLiFi, to the rugged computing and IT software market for the first time ever. Integrated Light Fidelity technology The announcement means customers across a wide range of professional sectors will soon be able to enjoy the benefits of fully rugged reliability and innovative LiFi connectivity in a si...
A workshop hosted by cyber risk analytics specialist CyberCube and global independent think-tank the Carnegie Endowment for International Peace (CEIP) examined how a severe cyber event involving cascading impacts from cloud infrastructure could result in business interruption and data loss across many different sectors. The conclusion was that such a multidimensional risk would require a multi-dimensional response. Some of the organizations that participated in the discussion are listed at the...
ExtraHop, a globally renowned company in cloud-native network detection and response solutions, has announced that it has achieved Amazon Web Services (AWS) Security Competency Status for Reveal(x) 360. AWS Security Competency Status This Security Competency Status designation recognizes the company’s demonstrated technical proficiency and proven ability to help customers secure workloads, applications, and data on AWS at the speed and scale of the cloud. “Earning AWS Security Com...
Pulse Secure, the globally renowned provider of Zero Trust Secure Access solutions, has announced that the COVID-19 pandemic has not impacted the adoption of Zero Trust technology globally. In fact, nearly two thirds of organizations (60%) said that they have accelerated Zero Trust implementation during the pandemic, according to the ‘Enterprise Zero Trust Networking Strategies: Secure Remote Access and Network Segmentation’. Enterprise Zero Trust Networking Strategies The’...
BCD International has announced the hiring of Kelly Carlberg to the newly created position of Strategic Alliances Manager - Dell Technologies. Carlberg brings with him, more than 20 years of surveillance and IoT expertise, and specializes in developing relationships and accelerating the use of appropriate indirect channels. Cloud computing expert Carlberg’s industry expertise includes cloud computing, virtualization, information security, identity and access management, policy management...
Claroty, the pioneer in operational technology (OT) security, announces new enhancements to the Claroty platform, making it the industry’s first OT security solution to offer remote incident management as a fully integrated capability that spans the entire incident lifecycle. The platform now enables cybersecurity teams to detect, investigate, and respond to security incidents on OT networks across the broadest attack surface area securely and seamlessly from any location. Standard opera...
W Series, the international single-seater motor racing series for female drivers only, is delighted to announce a new cyber protection and security partnership with Acronis, a globally renowned provider of cyber protection solutions. Global Cyber Security Partner The multi-year agreement sees Acronis become W Series’ new Global Cyber Protection and Security Partner, providing bespoke technology solutions for W Series’ on-track racing program, which will resume in 2021 and the W Ser...
New interface expands functionality, increases compliance in highly regulated markets and simplifies administration and deployment LenelS2 announced an interface between the OnGuard® physical access control system and the DMP XR550 and XR550E intrusion detection systems. The interface expands functionality, increases compliance in highly regulated markets and greatly simplifies the administration and deployment experience. LenelS2, a pioneer in advanced security systems and services, is a p...
Renowned risk management company, SmartWater Technology Limited (The SmartWater Group), has teamed up with Vantage England & Wales to help protect its agricultural customers from rural crime. As a result of the partnership, SmartWater Technology, a division of The SmartWater Group, will supply forensic marking liquid for Vantage’s Trimble agricultural portfolio, including advanced navigation and machine control systems designed specifically for farming use. SmartTrace liquid Each Tr...
Eagle Eye Networks, the pioneer in cloud video surveillance, has raised $40 million of Series E funding from venture capital firm Accel to continue its growth and expand its technology leadership. Eagle Eye is leveraging artificial intelligence (AI) on its true cloud platform to dramatically reshape video surveillance and improve safety, security, operations, and customer service for businesses around the world. Video surveillance systems have multiple security features, such as motion detectio...
DigiCert, Inc., the globally renowned provider of TLS/SSL, IoT and PKI solutions, has introduced Secure Software Manager, a modern way to automate and manage PKI security across CI/CD pipelines. Secure Software Manager Secure Software Manager makes it easy for enterprises to integrate secure key management for code signing into their development processes, while delegating cryptographic operations, signing activities and management in a controlled and auditable way. The drive for agility leav...
As iPhone 12 shipments rollout, security experts at Check Point warn of the security risks in using 5G. Here’s how consumers can stay safe while using the new iPhone and other 5G carriers. Security experts at Check Point are warning of security risks around 5G as iPhone 12 begins to ship worldwide. What is 5G? And how does it work? 5G is the shorthand term that stands for the fifth generation of wireless cellular networks. Following previous wireless standards after 1G, 2G, 3G, and 4G net...
Most companies are in the midst of budgeting season right now. With the chaos caused by the events in 2020, technology leaders are all busy working out what to do, when to do it and how to pay for their information technology budgets in 2021. Nobody likes the term ‘budget-slashing’, but cost-cutting initiatives are now a reality for most businesses, following the tumultuous events of the past year. Given those precursors, there are still financial realities that must be addressed i...
GRAU DATA has announced the general availability of Blocky for Veeam, which protects Veeam backups by denying any file access from unauthorized application processes, amid heightened demand for protection from increasingly sophisticated malware attacks. More sophisticated and targeted malware attacks combined with work from home as a new normal, has opened a vulnerability when it comes to IT security, particularly within midmarket companies. Whereas in the past, businesses could count on restor...
Hanwha Techwin America, a global supplier of IP and analog video surveillance solutions, has announced the launch of its new high definition Wisenet X PTZ PLUS cameras. Available immediately from Hanwha’s extensive network of resellers and systems integrators, the new cameras feature AI-based object tracking, precise PTZ control, improved pre-set accuracy, adaptive IR illumination and enhanced cyber security. Designed for perimeter protection and large, open area applications such as airp...
The Physical Security Interoperability Alliance (PSIA) has announced that it has elected Jason Ouellette, as its Chairman and Ewa Pigna, the Chief Technology Officer for LenelS2, a part of Carrier Global Corporation, as its Vice Chairman. Standards-based digital data In addition, Peter Boriskin, the Chief Technology Officer for ASSA ABLOY Opening Solutions Americas, will continue in his role as the organization’s Treasurer. The PSIA membership develops specifications for enabling standar...
Most business today is conducted at the edge, with employees working from home on vulnerable, often personal, endpoint devices. As the amount of sensitive corporate data accessed by devices out of an organization’s control grows, so does the attack surface that the IT team must safeguard. In response to this complex reality, Acronis announced the development of an integrated solution for managed service providers (MSPs) designed to enhance the protection of their clients’ Citrix Wor...