ASSA ABLOY Opening Solutions - Experts & Thought Leaders
White papers from ASSA ABLOY Opening Solutions
Modernizing Access Control
DownloadHow Biometrics Are Reshaping Security In A Connected World
DownloadThe Key To Unlocking K12 School Safety Grants
DownloadAccess Control System Planning Phase 2
DownloadAccess Control System Planning Phase 1
DownloadMulti-Residential Access Management And Security
DownloadSecuring Data Centers: Varied Technologies And Exacting Demands
DownloadBoost Efficiency And Streamline Security With Integrated Access Control
DownloadSchool Security Checklist
DownloadThe Wireless Access Control Report 2023
DownloadLatest ASSA ABLOY Opening Solutions news & announcements
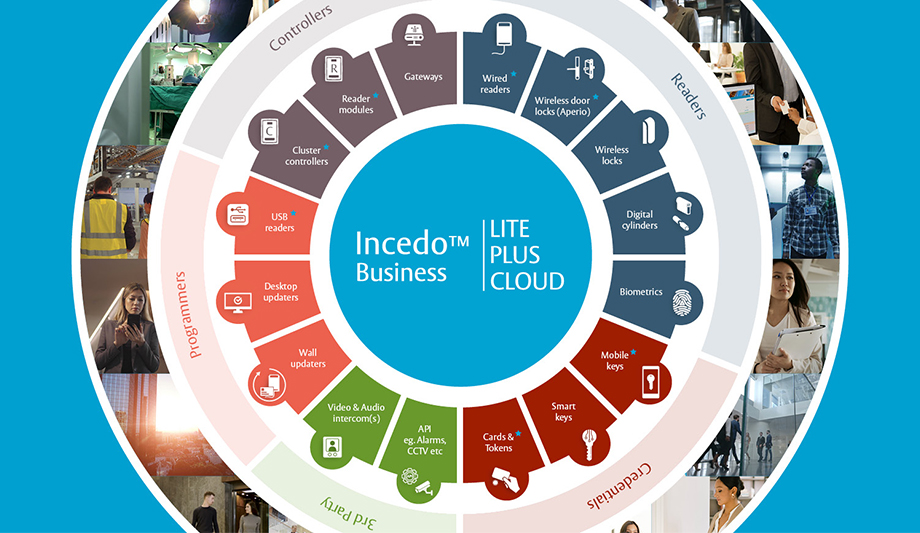
The world is constantly changing, with people, data and goods moving more fluidly than ever before. The security solution needs to move with it. New Incedo Business connects all security software and hardware within one platform. One can easily scale it up or down, based on one’s needs, to keep people moving and business growing. Together. People need different access times and entry points, and the access and security requirements change day to day – so, a static solution is no longer an option. Instead, a single, all-encompassing security platform should deliver connectivity, convenience and simplicity, keeping one’s premises secure and filtering access to manage the ever-changing movement of people. This is where Incedo Business comes in: a new solution for all types of premises, handling security while leaving one free to focus on growing the business. Incedo ensures employees, customers and goods are where they need to be. Incedo makes life and tasks easier and more efficient for everyone, from installers to end users. Facility managers enjoy more control and flexibility than they ever thought possible, maximizing return on investment, with Incedo Business able to scale quickly when needed. System administrators can do more within available budgets: initiating, cancelling or amending access profiles, and monitoring movement around their site in real time. Building users, meanwhile, get the individual access times and entry permissions they need. They can move freely without compromising the security of other people and equipment. Integrators can upgrade connected technologies and systems quickly, minimizing risk and meeting customers’ raised expectations of modern technology. Installers no longer need to wrestle with incompatible systems: easy interoperability is built into Incedo, meaning no more delays or unnecessary complexity. With Incedo’s modular platform approach, one simply chooses the security hardware and credentials one needs and the appropriate management system option. One can set exactly who can access which doors, and when, from the user-friendly Incedo Business software interface. When Incedo Business launches, one can pick the most suitable options from a growing range of Incedo-enabled security and access control hardware. Road-tested, award-winning ASSA ABLOY wireless digital locks and wired ASSA ABLOY wall readers secure all interior and exterior doors. Also already available, a choice of card and token credentials helps users enjoy safe and convenient access to, and movement around, the premises. Incedo mobile keys add the flexibility to open doors with a smartphone. Incedo’s system management options, Lite, Plus and Cloud, scale from entry level up to cloud-based administration. One can manage multiple sites and third-party integrations, including security solutions like CCTV. Scale up and down, add or remove hardware and credentials on demand, or switch system management options, all within a single environment. Migration between Lite, Plus and Cloud options is always seamless in any direction, ensuring total flexibility for the business. Incedo moves with you, today and in the future However your business moves, an Incedo system moves along. Having a flexible platform, able to adapt as the organization changes, reduces total cost of ownership: one never needs to retrain staff or start over from scratch. New Incedo-enabled hardware from ASSA ABLOY and third-party providers will continue to be connected to, and made available within, the evolving Incedo platform. One picks the hardware and software configuration one wants, and can change one’s mind as often as one likes. Incedo guarantees flexibility and scalability in every way, to meet the security needs today and in the future. And because the security and operational challenges at a university, small hotel or hospital are not the same as those faced by a public building or corporate HQ, the Incedo ecosystem will introduce new, advanced user interfaces for the specific industry. “Incedo Business transforms the experience of using and managing a building. It is also the seed from which our revolutionary Incedo ecosystem will grow in the months and years ahead,” says Stephanie Ordan, VP Digital and Access Solutions at ASSA ABLOY Opening Solutions EMEA. “A future where doors are smarter, connectivity and movement are seamless, and access management is genuinely intelligent. This is our vision for Incedo and for those who will be using it.” Incedo™ Business embodies ASSA ABLOY’s vision to create a safer and more open world, keeping everyone on the move. Together. To learn more and download a free solution guide, visit https://campaigns.assaabloyopeningsolutions.eu/Incedo-business
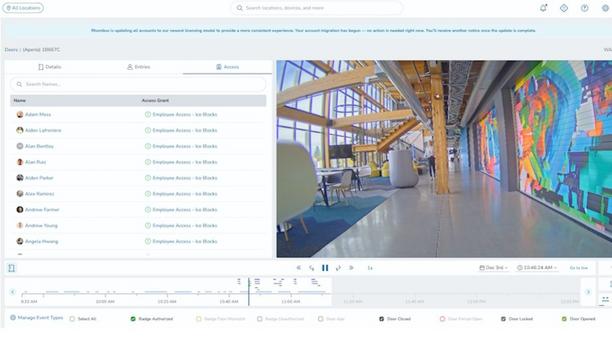
ASSA ABLOY Opening Solutions completed the integration of its Aperio® wireless lock technology with access control from Rhombus, an open, cloud-managed physical security platform that brings security cameras, access control, sensors, alarm monitoring, and software integrations together under a single pane of glass. Aperio wireless locks “With this integration, customers can now extend the power of Rhombus into doors and areas where wired access control simply isn’t practical. Pairing ASSA ABLOY’s industry-pioneering Aperio wireless locks with the Rhombus cloud platform gives a flexible, scalable, and truly unified approach to security." "From schools to hospitals, manufacturers to enterprises, this partnership is further enabling organizations to manage access, video, sensors, and AI-driven intelligence through a single, cloud-based experience; no on-prem servers or complex deployments required,” said Brandon Salzberg, Chief Technology Officer at Rhombus. New and existing access control installations The Aperio integration offers Rhombus customers an easy way to connect additional openings to both new and existing access control installations. Aperio is a global wireless platform that works with extensive locking hardware options from ASSA ABLOY Group brands, offering the flexibility to address a variety of applications throughout any facility. The platform uses wireless communication (IEEE 802.15.4) between the lock and an Aperio hub to provide real-time communication with the access control system, simplifying installation and reducing costs. Rhombus access control suite The Rhombus access control suite is a sophisticated enterprise solution that pairs seamlessly with Rhombus cameras, sensors, and alarms creating a complete ecosystem for managing building security - helping drive faster, smarter investigations, increase security visibility and reduce threats. Rhombus Console then becomes the central nervous system of your physical security; a user-friendly, cloud video management system designed to unify and streamline camera, access control, and live monitoring applications, easily scaled to unlimited cameras, doors, users, devices, and locations. Cloud-native approach “Rhombus brings a modern, cloud-native approach that makes it easier for organizations to unify and manage security across their entire environment,” said Angelo Faenza, Head of Access Control Solutions at ASSA ABLOY. “Through this integration, customers can experience the flexibility of Aperio locks alongside the simplicity and scalability of the Rhombus platform—removing the barriers of traditional access control and enabling smarter, more connected facilities.”
ASSA ABLOY has acquired International Door Products (“IDP”), a US manufacturer of standard and custom fire-rated steel door frames. "I am very pleased to welcome IDP to ASSA ABLOY. This acquisition delivers on our strategy to strengthen our position in mature markets through adding complementary products and solutions to our core business,” says Nico Delvaux, President and CEO of ASSA ABLOY. "This acquisition marks an exciting milestone for ASSA ABLOY Opening Solutions Americas as we welcome International Door Products Inc. into our family," says Lucas Boselli, Executive Vice President of ASSA ABLOY and Head of the Americas Division. Broader range of solutions "This acquisition allows us to offer an even broader range of solutions to our customers. IDP’s premium product portfolio and rapid lead times complement our existing capabilities, ensuring we can meet the evolving needs of construction markets with speed and excellence," continued Lucas Boselli. IDP was founded in 1977 and has some 80 employees. The main office and factory are located in Southfield, Michigan, USA. Sales for 2024 amounted to about MUSD 29 (approx. MSEK 300) with a strong EBIT margin. The acquisition will be accretive to EPS from the start.
Insights & Opinions from thought leaders at ASSA ABLOY Opening Solutions
A lot has been said about door security — from reinforced door frames to locking mechanisms to the door construction — all of which is crucial. But what security measures are in place beyond the perimeter door in case the worst happens and it’s somehow breached? Hopefully, many more levels of access control are in place to prevent, or at least slow down, a perpetrator’s ability to compromise protected assets. Additional interior layers Interior security measures must operate as an integrated, multilayered system that eliminates single points of failure. These inner protections safeguard not only the physical infrastructure but also the operational integrity, confidentiality, and availability of the systems housed within. Beyond simply preventing unauthorized individuals from getting inside, the goal is to create a controlled, monitored, and resilient environment in which every movement, action, and access attempt is verified, logged, and, when necessary, challenged. As modern buildings, data centers, and infrastructure sites host critical functions and potentially sensitive intellectual property, these additional interior layers become essential to protecting both organizations and their proprietary assets. Interior security controls One of the most important interior security controls is granular access segmentation One of the most important interior security controls is granular access segmentation. While a perimeter door may verify an individual’s right to enter the building, the interior should treat every room, cage, and corridor as its own security zone. Role-based access control and strict least-privilege principles should limit personnel to only the areas they absolutely require. For example, a network engineer may need access to routing equipment but not storage racks; a janitorial contractor might be allowed into shared hallways but not any equipment rooms at all. These access restrictions should be enforced using intelligent keys, biometric scanners, mantraps, and, at particularly sensitive locations, two-factor authentication. Segmenting access in this way limits the potential damage from a single compromised badge or insider threat and ensures that a single breach does not cascade into a total facility compromise. Low-light and infrared capabilities Biometric authentication within a building adds a layer of confidence beyond perimeter controls. Technologies such as facial identification help prevent the use of stolen, cloned, or borrowed credentials. These systems complement anti-tailgating measures, such as sally ports or mantraps, which ensure that only one authenticated person passes through at a time. Interior surveillance is another essential measure. High-resolution cameras equipped with low-light and infrared capabilities should cover every hallway, door, rack row, and logistical pathway. Camera feeds must be continuously recorded, and retention policies must align with regulatory requirements. Intelligent video analytics, such as motion pattern recognition and heat mapping, enable the detection of atypical behaviors — such as someone lingering near a cage they are not authorized to access or movement at odd hours. Physical tamper-detection mechanisms Cabinet security provides a vital layer of granularity in the access hierarchy, ensuring that even within secure facilities Integrating surveillance with access control systems creates a strong correlation; when someone successfully passes through a secured door and enters a room, the system can track whether the number of people seen on camera matches the number authenticated, and alert security if a discrepancy occurs. However, it is increasingly important that access control not stop at the room level, because the most sensitive assets are often housed in cabinets, racks, or storage units within already-secured spaces. Cabinet security provides a vital layer of granularity in the access hierarchy, ensuring that even within secure facilities, assets remain protected. Physical tamper-detection mechanisms on racks, cable trays, and server chassis add another dimension: they can detect if a panel is opened, a cable is unplugged, or a device is removed without authorization. Secure destruction protocols Another internal measure is the use of secure storage and chain-of-custody procedures for any components that contain intellectual property or personally identifiable information. Hard drives, backup media, and even printouts should be stored in locked cabinets accessible only to people with proper clearance. When decommissioning hardware, secure destruction protocols such as shredding or degaussing should be performed in controlled areas and thoroughly logged. Every movement of sensitive equipment should be traceable, from installation through end-of-life disposal. Such processes reduce the risk of data leakage from improperly discarded or undocumented devices. Consequences of improper behavior Staff should be trained to recognize social engineering attempts, unusual behaviors, and procedural deviations Operational security procedures also contribute significantly to interior protection. Background checks, ongoing employee vetting, and mandatory training ensure that individuals with access to sensitive areas understand their responsibilities and the consequences of improper behavior. Staff should be trained to recognize social engineering attempts, unusual behaviors, and procedural deviations. Maintaining a strict visitor escort policy prevents non-employees from wandering unobserved. All visitors should wear highly visible identification badges and be monitored continuously by authorized personnel. The building's interior should be treated as a controlled environment at all times, not merely a workspace. Continuous auditing and logging form Continuous auditing and logging form another pillar of interior security. Access logs from intelligent keys, biometrics, video, and environmental systems must be stored securely and evaluated regularly for anomalies. Automated systems can flag irregular patterns, such as repeated attempts to access unauthorized areas or entering rooms at odd hours. Manual audits validate that the access control list remains accurate, that no inactive or former employees retain credentials, and that documentation matches reality on the floor. These logs are indispensable during investigations, compliance assessments, and incident response efforts. Interior security controls Security networks should be isolated from the main IT networks to prevent a cyber incident Finally, redundancy and resiliency must be built into interior security controls. Electrical power for access control, intelligent keys, biometrics, and video systems should be backed by secondary sources, generators, or uninterruptible power supplies. Security networks should be isolated from the main IT networks to prevent a cyber incident from disabling physical protections. The goal is to ensure that interior security remains functional even during outages, disasters, or cyber disruptions. Multilayered approach Together, these additional interior measures create a layered defense that makes a secure building, data center, or infrastructure site extremely difficult to compromise. Rather than relying on a single barrier at the entrance, the environment becomes an ecosystem of mutually reinforcing controls — physical, operational, digital, and procedural. This multilayered approach allows structures to maintain high levels of protection even as threats evolve, ensuring that the systems inside remain secure, resilient, and trustworthy.
In today’s connected world, attacks are more likely to target digital than physical entry points. From ransomware and firmware tampering to remote hijacking, AI-driven phishing and automated vulnerability discovery, the nature of threats is evolving rapidly, and no industry can afford to neglect them. As our industry has moved from mainly mechanical to increasingly digital solutions, we have long recognized the importance of constantly monitoring and assessing the risks we face. This means not only meeting mandatory regulations but also voluntarily adopting international standards such as ISO 27001, which protects data and systems through a structured and independently audited framework. Today’s fast-changing risk environment is also why the EU introduced the Network and Information Security Directive 2 (NIS2) – to raise the bar for cybersecurity across Europe. But what do measures like NIS2 and the Cyber Resilience Act (CRA) mean in practice? How does the rise of AI fit in? And most importantly, what should our industry be doing to stay secure in such an unpredictable digital landscape? The new regulations Compliance is not just about meeting regulations, it is also a competitive advantage NIS2 is reshaping cybersecurity expectations by setting higher standards to reduce risk, improve transparency, and protect data and services. Alongside it, the CRA introduces mandatory requirements for products with digital components. This makes “secure by design,” regular updates, and compliance checks essential before products can enter the EU market. For companies in our industry, responsibilities now extend well beyond internal systems. Organizations must also ensure that suppliers and service providers comply, with regular risk assessments forming a central part of the process. The consequences of falling short are severe, ranging from significant fines and audits to the potential withdrawal of products from the market. For our customers, the message is clear: security must be built in from the start. Compliance is not just about meeting regulations, it is also a competitive advantage. At ASSA ABLOY Opening Solutions EMEIA, security is part of our DNA. We embed these standards into everything we do, giving customers solutions they can trust to be compliant and resilient. The rise of AI Artificial intelligence is transforming the digital security landscape and it cannot be separated from the regulatory framework shaping our industry. With AI advancing rapidly and new regulations coming into force, we have established a digital compliance framework to stay ahead of the curve and use AI as an enabler for improving security and achieving compliance. On one hand, AI brings powerful benefits, including more intelligent monitoring, faster anomaly detection, and smarter tools for operational efficiency. These capabilities directly support NIS2 and the CRA, particularly in the areas of proactive risk management and incident response. AI and building cybersecurity standards On the other hand, AI introduces new risks. The attack surface is expanding and threats such as deepfakes and smarter phishing create serious threats that regulators are determined to address. Both NIS2 and the CRA emphasize continuous monitoring, transparency and accountability, principles that must now also guide the responsible use of AI. At ASSA ABLOY Opening Solutions EMEIA, we see AI not just as a risk to mitigate, but as a capability to strengthen resilience and trust. That is why we are embedding strong governance practices around AI and building cybersecurity standards into every stage of product development. By doing so, we help our customers align with new regulations while ensuring AI serves as a tool for greater security and confidence. Trust and compliance Beyond our own operations, we are also committed to supporting customers on their compliance journey At ASSA ABLOY Opening Solutions EMEIA, we are taking NIS2, the CRA and the rise of cyber-threats seriously, ensuring compliance and enhancing trust with all our customers. We have reinforced supplier oversight, streamlined incident reporting, and embedded cybersecurity into every stage of product development and lifecycle management. Our teams also conduct ongoing risk assessments and post-incident reviews, ensuring that lessons are learned and improvements are made. By taking these steps, we not only meet regulatory requirements but strengthen the resilience of our supply chain and the trust customers place in us. Beyond our own operations, we are also committed to supporting customers on their compliance journey. Initiatives such as our recently released whitepaper “Enhancing Cyber–Physical Resilience with Digital Access Solutions” and a detailed NIS2 whitepaper developed in Germany last year provide clear, practical guidance. By showing what these regulations mean in practice and how intelligent access solutions can directly support compliance, we aim to make the path forward less complex and more achievable for our customers. Looking ahead The days when security threats to businesses and products were only physical are long passed. Today, we find ourselves in a world where the digital realm poses even more serious and constantly evolving challenges. It is therefore crucial that, as an industry, we take the necessary steps to meet the directives of NIS2 and the CRA and also constantly monitor the rise of AI. Only by doing so can we protect our customers, preserve our reputations, and build the trust that defines true leadership in security.
When it comes to protecting the environment, the security industry has historically been perched on the sidelines. For instance, the amount of electricity that physical security systems use is minimal when compared to the total energy usage in a typical building. However, as awareness of environmental issues has surged, and as some of the "low-hanging fruit" has been harvested, attention has come back to opportunities for additional, if small, savings. The lifecycles of security products are also being more closely examined, including the environmental impact of using plastics and other chemicals. We asked this week's Expert Panel Roundtable: How can the security industry contribute to protecting the environment?