Abnormal Security (Abnormal AI) News
Abnormal AI, the pioneer in AI-native human behavior security, announced its updated Security Posture Management product, bringing AI-driven protection, automated prioritization, and remediation guidance to customers’ Microsoft 365 environments. As Microsoft 365 environments become more complex, accidental misconfigurations are now a major cause of cloud email vulnerabilities. The growing number of applications, layered settings, and fragmented ownership create blind spots and accidental...
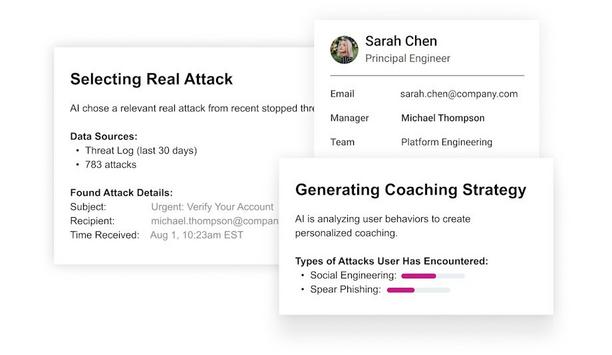
Abnormal AI (Abnormal Security), the globally renowned company in AI-native human behavior security, has unveiled its most ambitious product release to date — introducing autonomous AI agents that revolutionize how organizations train employees and report on risk, while also evolving its email security capabilities to continue to stop the world’s most advanced email attacks. In a year defined by the explosive use of malicious AI for cybercrime, Abnormal is doubling down on its missi...
Abnormal Security, the pioneer in AI-native human behavior security, announced it has been recognized as a pioneer in the first-ever Gartner® Magic Quadrant™ for Email Security Platforms. A complimentary version of the full report can be found. Gartner evaluated 14 vendors across the email security market and placed Abnormal in the Leaders Quadrant. They feel this placement recognizes Abnormal for excelling in both Completeness of Vision by addressing current and future email threats,...
Business email compromise (BEC) attacks involve manipulating or impersonating email accounts to deceive employees, often leading to financial fraud, breaches or data loss. According to Verizon, BEC attacks doubled last year and comprised nearly 60% of all social engineering incidents. To deal with this growing frequency of BEC attacks, MSPs need advanced strategies, such as user behavior analysis and employee training programs. Let’s look at the key BEC protection strategies for MSPs. Wh...
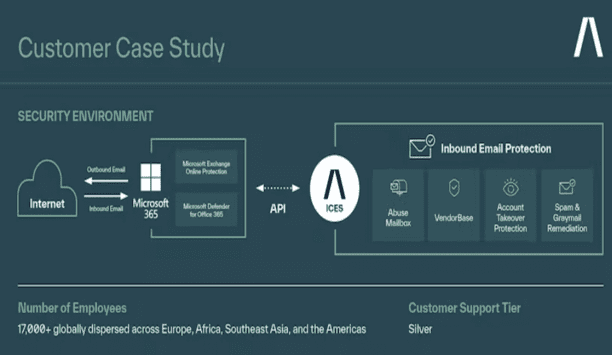
Coats is the provider of industrial thread manufacturing, with more than 17,000 employees producing enough fiber daily to stretch to the sun and back four times. The 250-year-old company has stayed at the forefront of textile innovation as demand evolved from sewing thread to healthcare PPE and carbon composite fibers for aerospace manufacturing. Coats leverages new technologies and market expertise to develop products for customers in the apparel, luggage, footwear, home and recreation, perso...
Abnormal Security announced the Abnormal Integrated Cloud Email Security (ICES) platform. Abnormal ICES is the only all-in-one email security platform that provides unparalleled precision against the full spectrum of email attacks. Powered by Behavioral AI technology and deeply integrated with Microsoft 365, Abnormal unifies and simplifies customers’ email security architecture by removing the need for multiple email security products, modernizing the end-user experience, and reducing t...
Abnormal Security, provider of a cloud-native email security platform that leverages behavioral data science to stop modern email attacks released its Q3 2021 Email Threat Report. It examines the escalating adverse impact of socially-engineered and never-seen-before email attacks, and other advanced email threats both financial and reputational to organizations worldwide. Findings of Q3 2021 Email Threat Report The report surveyed advanced email attacks across eight major industry sectors, in...
With school starting this month, cybercriminals are back in action, targeting university students in an attempt to steal valuable personal information. In a recent attack, uncovered by Abnormal Security, a credential phishing attacker used a legitimate email account and created false urgency, in order to steal student credentials, through a phishing website. Credential phishing attack In this attack, cybercriminals used the real university email of a person on the ‘Student Services Team&...
Abnormal Security, the provider of the cloud-native email security platform that leverages behavioral data science to stop modern email attacks, announces the appointment of Anita Grantham as Chief People Officer. Grantham leads all aspects of Abnormal’s talent and culture strategy, including employee experience, recruiting, rewards, retention, and career development. Abnormal protects 100% of the employees at 5% of the Fortune 500. Grantham enables Abnormal to continue expanding worldwid...
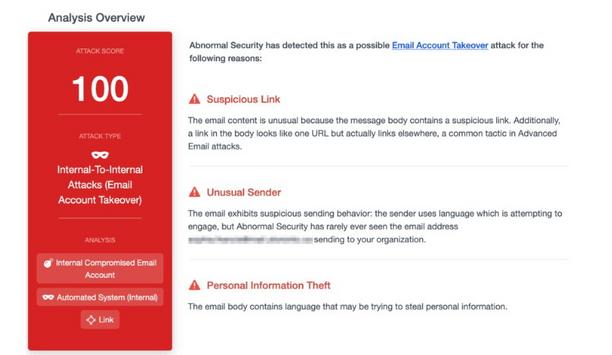
Business email compromise (BEC) is the most significant cybersecurity threat to enterprise organizations, with $1.8 billion in reported losses in 2020 alone. This type of email attack occurs when a cybercriminal uses social engineering to impersonate a trusted contact—typically an executive, coworker, vendor, or partner—to steal money or valuable information. Because these emails rarely contain malicious links or attachments, they are difficult to detect by standard email security p...
On March 17, the FBI released its seminal annual Internet Crime Report. Once again, socially-engineered attacks (including business email compromise, spoofing, and phishing) by far were the number one cybercrime by financial loss, accounting for $2.1 billion of the $4.2 billion in losses to U.S. businesses and consumers. These attacks utilize impersonations to get companies to transfer money to fraudulent accounts and pose significantly more financial danger to an organization than well-known ta...
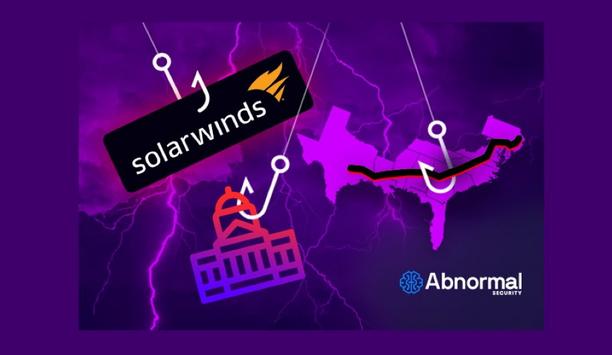
The threat actor behind the SolarWinds attack, the Russian-based Nobelium, has orchestrated another successful vendor email compromise attack, this time targeting the United States Agency for International Development (USAID). According to the Microsoft Threat Intelligence Center (MSTIC), Nobelium compromised the USAID’s Constant Contact account, so as to send phishing emails that included links containing malware. Zero-day phishing attacks The incident highlights how zero-day, never-se...
As the details emerge on the ransomware attack that sent a major U.S. oil pipeline operated by Colonial Pipeline offline for a week, what Abnormal does know is that the likelihood the attack emerged from a malicious phishing email attack is extremely high. Ransomware attacks Recently, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) tied the threat actors behind the attack, DarkSide, to prior phishing-related attacks as a way to deliver ransomware to their targets....
Abnormal Security, provider of the cloud-native email security platform that leverages behavioral data science to stop modern email attacks announced the appointment of Mike Britton as Chief Information Security Officer. Mike brings Fortune 500-calibre security leadership experience that will not only drive the company’s security and privacy program but also help influence the development and support of the Abnormal Security platform to ensure it delivers lasting value to customers. Mike...
Abnormal Security announced the company has been named one of 10 finalists for the RSA Conference 2021 Innovation Sandbox Contest for its breakthrough cloud-native email security platform that stops modern email attacks through behavioral data science. On May 19, Abnormal Security will present its email security platform to a panel of renowned industry judges and a live virtual audience in a three-minute pitch, competing for the coveted title of “Most Innovative Start-Up” at RSA Con...
In the RFQ cyber-attack, attackers disguise harmful malware as a ‘Request For Quote’ (RFQ), in order to encourage recipients to download dangerous files. This attack is an impersonation of a ‘Request For Quote’ (RFQ) from a legitimate, outside organization. The attack originates from the throwaway address - info@req-allparts.com, with the reply-to address - glennmauldin@zidnei.com. RFQ attack By using urgent language, the attacker attempts to coax the recipient to click...
IRS email impersonations are widespread across all industries. These attacks vary in scale and victim, targeting both individuals and companies as a whole. This particular attack follows the growing trend of utilizing social engineering strategies for malicious engagement, allowing attackers to easily bypass email security solutions that focus on link or attachment-based threat vectors. Summary of attack Platform: Office 365 Mailboxes:5K-50K Bypassed Email Security: Office 365 V...
Abnormal Security has announced its placement on Fast Company’s prestigious annual list of the World’s Most Innovative Companies for 2021 for its breakthrough cloud-native email security platform that stops modern email attacks through behavioral data science. The list honors the businesses that have not only found a way to be resilient in the past year, but also turned those challenges into impact-making processes. Innovative, data science approach Abnormal Security’s innov...
In this attack, attackers impersonate a message from the United States government, claiming to provide information on the Paycheck Protection Program in an attempt to steal valuable credentials. Summary of the attack target Platform: Office 365 Mailboxes: Less than 10,000 Bypassed Email Gateway: Proofpoint Victims: Employees Payload: Link Technique: Impersonation What was the attack? 1) Setup: Fraudulent actors continue to capitalize on the ongoing pandemic by intercepting...
In the ‘LinkedIn Identity Theft’ attack, the attacker impersonates a policy change notification from the company, LinkedIn, in order to steal highly confidential information, such as the victim’s social security number. ‘LinkedIn Identity Theft’ attack Cybercriminals constantly search for unique social engineering tactics, in order to dupe their victims. However, in this type of cyber-attack, attackers rely on the reputability and trust bestowed in social media an...
With holiday delivery deadlines quickly approaching and online orders continuing to pour in, courier services are facing increasing pressure from anxious consumers. This rise in shipping demand has made Amazon, USPS, UPS, and FedEx targets of increasing impersonation attacks aimed at their unsuspecting customers. In this attack, attackers impersonate a USPS package tracking page to steal credit card credentials. Credit card phishing attack This attack mimics a delivery notification email from...
In this attack, scammers impersonate the IRS to collect a fraudulent payment from their target. Summary of the attack target Platform: Office 365 Bypassed Email Gateway: Proofpoint Mailboxes: 50,000 to 70,000 Payload: Text Technique: Spoofing / Impersonation What was the attack? 1)Setup: The IRS has long been a popular target for impersonation by attackers. This email highlights a more sophisticated IRS impersonation, where a targeted attack is sent from a spoofed sender domain...
This week, Abnormal Security researchers have been tracking recent well-disguised attacks from a Russian criminal enterprise, which are using the Emotet Trojan to drop Ryuk ransomware and BazarLoader for financial gain. Ryuk ransomware attack The Federal Bureau of Investigation (FBI) and the Department of Homeland Security (DHS) issued a warning of an impending attack, using Ryuk ransomware, earlier this week, noting that healthcare and the public sector are the intended targets. Abnormal Sec...
Abnormal Security, a pioneer in protecting large enterprises from cybersecurity attacks, announced a global strategic alliance with Microsoft to deliver comprehensive security solutions to enterprises. Customers can purchase Abnormal’s security offering directly from Microsoft’s Azure Marketplace. Abnormal Security is one of the only cloud-native security platforms that dozens of Fortune 1000 companies trust to protect their cloud environments. Abnormal’s data science app...
Abnormal Security, a pioneer in protecting large enterprises from Business Email Compromise (BEC) attacks, published research data that shows a 200 percent increase in BEC attacks focused on invoice or payment fraud from April to May 2020. This sharp rise continues the trend observed by Abnormal Security throughout the year. Invoice and payment fraud According to the Abnormal Security Quarterly BEC Report for Q1 2020, invoice and payment fraud attacks increased more than 75 percent in the...
Abnormal Security has observed attackers impersonating social media platforms like Instagram, Facebook, and Twitter to steal the login credentials of employee’s major enterprise organizations. In the past two months, it has seen a 60% increase for several organizations with key social media presences. What are the attacks? These attacks impersonate popular social media platforms to deliver phishing emails to influential users of each platform by impersonating Instagram, Facebook, and Twi...
Abnormal Security, a pioneer in protecting large enterprises from Business Email Compromise (BEC) attacks, introduces VendorBase, a global, federated database that tracks the reputations of an organization’s vendors and customers, and improves the detection accuracy of advanced social engineering attacks. With VendorBase, the Abnormal Cloud Email Security platform aggregates communication in one place to provide customers with deeper insight and visibility into a vendor’s reputation...
Abnormal Security, a pioneer in protecting large enterprises from business email compromise (BEC) attacks announced it has been included in the list of Cool Vendors in Cloud Office Security by Gartner. The report recognizes vendors with “innovative approaches to cloud office security, email, and collaboration.” Business email compromise Business email compromise continues to plague organizations, leading to $26B in losses according to the FBI As the primary communication channel f...
Abnormal Security, the platform that protects large enterprises from the most sophisticated, targeted email attacks announced the appointment of Kevin Moore as Chief Revenue Officer. With over 20 years of success leading high-performing global sales teams in the security industry, Kevin is responsible for scaling Abnormal’s worldwide sales team, operations, and go-to-market engine. About Kevin Moore Kevin joins Abnormal Security from Vectra Networks, where he led all direct and channel...
Abnormal Security, a pioneer in protecting large enterprises from Business Email Compromise (BEC) attacks announced the availability of Microsoft Teams protection and integration with Okta to extend email security coverage and protect remote workforces from social engineering attacks. Seamlessly delivered through Abnormal Security’s API-based integration with Office 365 and Okta’s Identity Cloud, respectively, these new integrations give enterprises more visibility, extended protect...