Sentrycs and Omnisys have announced a strategic collaboration to enhance the deployment of sensor systems in multi-domain operations by integrating their respective technologies.
Sentrycs, recognized for its expertise in Protocol Manipulation-based counter-drone technology, commonly known as Cyber over RF, and Omnisys, a specialist in mission optimization for defense and homeland security, aim to address the increasing demand for precision in sensor deployment.
Joint Technology Integration
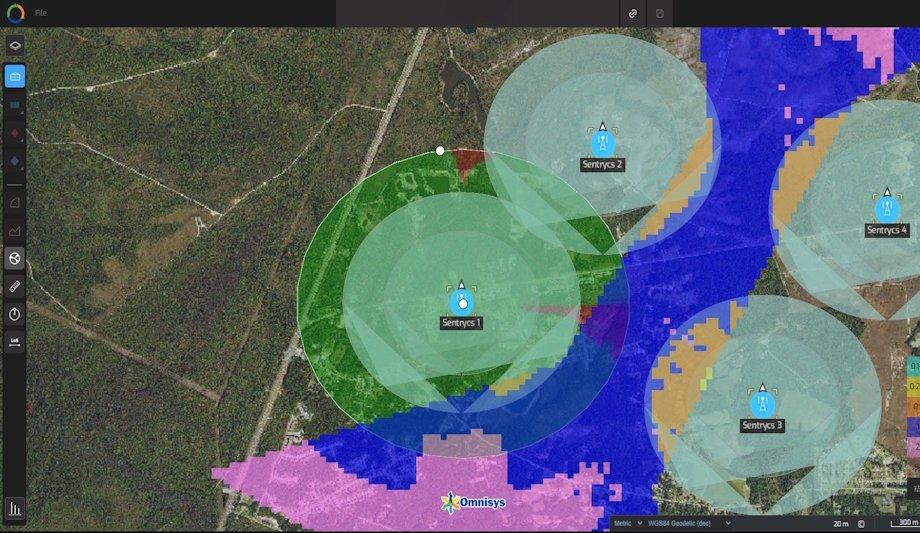
The collaboration combines Sentrycs’ proven counter-unmanned aircraft systems (C-UAS) with Omnisys’ BRO-AD
The collaboration combines Sentrycs’ proven counter-unmanned aircraft systems (C-UAS) with Omnisys’ BRO-AD (Battle Resource Optimization for Air Defense) platform.
This integration enables defense and security forces to consider operational constraints like terrain topography and electromagnetic interference when determining optimal sensor layouts.
Omnisys' BRO-AD models different operational scenarios to help decision-makers identify blind spots and optimize coverage, thereby enhancing the entire deployment process.
Enhancing Operational Readiness
With these technologies working in unison, sensors are more precisely positioned to maximize effectiveness, increasing operational readiness and improving resource allocation.
This collaboration promises improved system performance and enhanced protection, reducing unnecessary deployment and ensuring the most effective sensor placement in the field.
Commitment to Security Solutions
“This collaboration reflects a shared commitment to delivering operationally relevant solutions that meet today’s evolving security challenges,” stated Meir Avidan, VP Business Development and Strategic Partnerships at Sentrycs.
Furthermore, Dov Pearl, Chief Business Officer at Omnisys, remarked, “By integrating BRO-AD’s powerful modeling capabilities with Sentrycs’ counter-drone systems, we’re helping customers plan and execute sensor deployments with greater accuracy, efficiency, and mission success.”
Stay ahead of the trends on securing physical access control systems through layered cybersecurity practices.