Corporate Security
AI is one of the fastest-growing technologies in the history of modern business, with the ability to revolutionize industries, optimize operations, and drive innovation, but it is also introducing security gaps, risks, and vulnerabilities. According to McKinsey, 78% of organizations are using AI in at least one business function, up from 55% two years ago. As a result, 73% of them are investing in AI-specific security tools, either with new or existing budgets, according to the 2025 Thales Data...
ZBeta, a pioneer in delivering comprehensive physical security consulting services, now announced that senior executives Conal O’Doherty and Jesse “JJ” Knutson have been named principals of the firm. In their respective roles as Chief Growth Officer and Chief Operating Officer, Conal and JJ have been instrumental in shaping ZBeta’s identity by elevating the brand, enriching the client experience, advancing corporate strategy, strengthening operational performance, and un...
As the Committee on Foreign Investment in the United States (CFIUS) continues to expand its oversight and enforce compliance, it is crucial for legal, compliance, and business pioneers to stay ahead of the latest developments. This premier conference provides in-depth discussions on the evolving CFIUS landscape, including filing requirements, risk mitigation strategies, and the impact of new regulations. Safeguarding national security interests Attendees will gain exclusive insights from gov...
Milestone Systems’ CEO Thomas Jensen is stepping down from his position with immediate effect, and the company is now searching for a new pioneer. ”To further strengthen cohesion and collaboration across the organization, the board of directors has agreed to initiate a search for a successor for the position of Chief Executive Officer. As a result, Thom-as Jensen has stepped down from his role as CEO. The Vice-Chairman of the board since 2015, Jeppe Frandsen will be acting CEO...
Zitko Group is pleased to announce the appointment of James Strickland as Non-Executive Director, effective 1st November. James brings a standout track record in recruitment M&A, strategic growth, and board-level advisory. He has worked with a range of high-performing organizations and is widely respected for helping niche engineering talent businesses scale with clarity, strong governance, and cultural alignment. His appointment comes at a pivotal time for Zitko as the Group cont...
VIVOTEK, a global security solution provider, continues to deepen its commitment to sustainability and has been recognized with two distinctions at the 18th Taiwan Corporate Sustainability Awards: the Silver Award for Sustainability Report for the Information, Communication, and Broadcasting Industry and the Taiwan Corporate Sustainability Excellence Award. Facing the challenges of net-zero and climate change, VIVOTEK continues to strengthen its ESG actions by gradually completing its global c...
News
Nutanix, a pioneer in hybrid multicloud computing, announced at Microsoft Ignite 2025 that its Nutanix Cloud Platform solution will support Microsoft Azure Virtual Desktop for hybrid environments. This will enable organizations to run Azure Virtual Desktop on premises on the Nutanix AHV hypervisor, offering a new level of flexibility in how virtual desktops are deployed and managed. This effort aims to meet the evolving needs of distributed workforces and will give IT teams more infrastructure choices while optimizing control, performance, security, and cost efficiency. Nutanix Cloud Platform “The Nutanix Cloud Platform delivers a performant, resilient, cost-efficient, and secure infrastructure base for virtual desktop infrastructure (VDI) workloads,” said Tarkan Maner, Chief Commercial Officer at Nutanix. “This collaboration with Microsoft will empower our customers with more options for virtual desktops, whether they’re modernizing on premises or extending into hybrid cloud environments.” Critical compliance and regulatory requirements Azure Virtual Desktop for hybrid environments addresses critical compliance and regulatory requirements in industries such as financial services, healthcare, and government, where data residency and sovereignty are paramount. Customers will benefit from running Azure Virtual Desktop locally on Nutanix AHV while using the Azure Virtual Desktop brokering and management stack on Azure Arc–enabled servers to connect securely to Azure. Key benefits of Azure Virtual Desktop Key Benefits of Azure Virtual Desktop for hybrid environments on Nutanix AHV will include: Hybrid Flexibility: Combine on-premises performance with Azure scalability for burst capacity and disaster recovery. Ability to run Microsoft applications: Native support for Microsoft 365, Teams optimisations, Microsoft Entra, and security services. Optimized for Performance: Ideal for latency-sensitive and graphics-intensive workloads. Cost Efficiency: Leverage existing Microsoft licensing and Nutanix infrastructure for predictable economics. Nutanix support for Azure Virtual Desktop “Azure Virtual Desktop is built to deliver a secured, scalable, and deeply integrated experience with Microsoft 365, Microsoft Teams, and Windows,” said Scott Manchester, Vice President of product for Windows 365 and Azure Virtual Desktop at Microsoft. “Nutanix support for Azure Virtual Desktop will give customers more choice, whether they deploy in the cloud or on premises — without compromising on the modern security model or licensing efficiencies.” Possibilities for VDI Nutanix is expanding the possibilities for VDI, which will enable organizations to tailor their environments to meet business needs - without being locked into a single deployment model. The Nutanix Cloud Platform’s support for Azure Virtual Desktop is currently under development.
Wavelynx, a pioneer in open and secure access control solutions, announced the appointment of S. Jay Lawrence as Chief Executive Officer, effective immediately. Mr. Lawrence brings more than three decades of technology leadership experience, with a proven track record of scaling companies from startup to billion-dollar operations. Mr. Lawrence most recently served as Chief Executive Officer of Equus Compute Solutions, where he drove significant revenue growth and market expansion. His extensive background includes CEO positions at NexxCom Wireless, and GigaBeam Corporation, where he consistently delivered breakthrough innovations and exceptional financial results. Milestone in Wavelynx's evolution "Jay's appointment marks an exciting milestone in Wavelynx's evolution," said Hugo Wendling, Founder of Wavelynx. "His deep expertise combined with his customer-first philosophy, makes him the ideal pioneer to accelerate our growth while maintaining the innovation and service excellence our customers expect." "His vision aligns perfectly with our mission to simplify and modernize access control for organizations worldwide. I look forward to supporting him in this transition and will continue to focus on making our customers win with our technology." Prior roles of Lawrence Throughout his career, Mr. Lawrence has demonstrated exceptional ability to identify market opportunities and translate emerging technologies into commercial success. He has pioneered innovations including ultra-low latency networks for financial markets, advanced AI systems, cybersecurity for edge computing, and has led successful technology transformations for Fortune 500 companies across multiple industries. Wavelynx's interoperable platform approach "Wavelynx has built something truly special – a company that combines cutting-edge technology with an unwavering commitment to customer success," said Mr. Lawrence. "I'm honored to join this exceptional team and excited about the opportunity to accelerate our growth trajectory. The access control industry is at an inflection point, and Wavelynx's interoperable platform approach and innovative solutions like the APEX reader position us perfectly to lead this transformation." Expansion into new international markets The CEO appointment follows a period of significant momentum for Wavelynx, including the recent launch of its APEX reader, expansion into new international markets, and recognition on the Deloitte Technology Fast 500 list. Since Triton Partners' investment in October 2023, the company has strengthened its executive team and accelerated product development to meet growing market demand for modern, adaptable security solutions. Resources to innovation Dave Hansen, Chairman of the Board, added, "Jay's appointment enhances our capacity to serve customers while Hugo and the executive team remain deeply engaged in the business." "This leadership expansion allows us to dedicate even more resources to innovation and direct customer engagement, ensuring we continue to deliver the most advanced, interoperable access control solutions in the industry." Rob's contributions Rob Lydic will be transitioning from the business at year-end to take a long-awaited break and determine his next chapter. Rob has been instrumental in building Wavelynx into what it is now—his industry expertise and dedication have shaped both our business and culture. He's working closely with Jay to ensure a seamless transition, and will continue cheering us on as an investor. We're deeply grateful for Rob's contributions and look forward to his continued success. Wavelynx's continued success "It's been an incredible privilege to help build Wavelynx into the industry pioneer it is today," said Robert Lydic, President of Wavelynx. "Jay brings exactly the right experience and vision to take Wavelynx to the next level, and I'm confident the company will thrive under his leadership. I look forward to watching Wavelynx's continued success as both an investor and champion of the brand."
DigiCert, a global pioneer in intelligent trust, and Citrix, a business unit of Cloud Software Group, Inc., have announced an integration that automates the entire lifecycle of SSL/TLS certificates, from issuance to renewal. This collaboration pairs DigiCert’s capabilities with Citrix NetScaler’s Zero-Touch Certificate Management (ZTCM) and ACME protocol integration, empowering enterprises to maintain continuous security and compliance across hybrid and multi-cloud environments. The ACME integration supports both DigiCert CertCentral and DigiCert Trust Lifecycle Manager (TLM), giving enterprises flexibility in how they automate certificate workflows. Organizations using TLM gain additional advantages through advanced policy enforcement, delegated administration, and centralized visibility across multi-cloud and hybrid environments. DigiCert integration with Citrix NetScaler’s ZTCM As certificate lifetimes are shortened across the industry from 398 days to 47 days, the need for automation has become critical. Manual processes are no longer scalable, leaving organizations vulnerable to outages, configuration errors, and compliance lapses. Together, DigiCert and Citrix NetScaler are helping enterprises adapt to this shift by delivering a fully automated, certificate management framework that minimizes risk while reducing operational overhead. The DigiCert integration with Citrix NetScaler’s ZTCM is managed directly through the ACME protocol, enabling fully automated certificate issuance, installation, and renewal across NetScaler-managed applications and environments. Key benefits include: Operational Efficiency: Eliminates manual certificate tasks and reduces administrative overhead. Continuous Security: Ensures consistent and compliant encryption across distributed systems. Reduced Downtime Risk: Prevents outages caused by expired or misconfigured certificates. Scalability: Supports hybrid and multi-cloud deployments through centralized automation. Crypto-agility: Centralized management and automation enable fast, organized implementation of advances like post-quantum cryptography. Rapid transformation “The cryptographic landscape is undergoing rapid transformation, and shorter certificate lifetimes are just one part of that change,” said Anthony Ricci, AVP of Solutions Engineering at DigiCert, adding “Our integration with Citrix NetScaler enables enterprises to automate every stage of certificate management — from issuance to renewal — ensuring uptime, compliance, and crypto-agility across hybrid and multi-cloud environments.” “Enterprises are being forced to rethink how they manage encryption at scale,” said Steve Shah, SVP/GM at Citrix NetScaler, adding “As certificate lifetimes shrink, the margin for error disappears. Our collaboration with DigiCert helps organizations automate certificate management from end to end, simplifying operations, improving reliability, and ensuring that security keeps pace with the speed of modern business.”
Gallagher Security wrapped up GSX 2025 with a powerful reminder that protecting what matters most extends beyond technology. Through their Security Meets Solidarity initiative, the global security manufacturer raised more than $7,000 for the Breast Cancer Research Foundation (BCRF), more than doubling their original goal. “We went into GSX hoping to raise $3,000, and our team was thrilled to reach that goal on day one,” says Melissa Vidakovic, Director of Marketing – the Americas. “We all hoped to surpass our goal, but we were blown away by the incredible response from attendees and are grateful for the support. Every donation makes a difference. Our industry is built on protecting people, and at GSX we saw that extend to something deeply personal.” Critical funds for life-saving research Miriam Shaw, Head of Communications and Public Relations, met with BCRF at their New York headquarters to deliver donations and elaborates: “The support we received from GSX attendees was overwhelming. Our team had many moving conversations with people whose families, friends, and colleagues have been impacted by this disease. We were deeply grateful for the connections made and opportunity to raise critical funds for life-saving research, and to deliver a message of unity and compassion that goes far beyond security.” “We’re deeply grateful to Gallagher Security and the GSX community for their generosity and commitment to advancing breast cancer research,” said Sadia Zapp, Managing Director at the Breast Cancer Research Foundation. “Every dollar raised helps fuel BCRF’s mission to end breast cancer by funding the most promising research around the world.” GallagHER fundraising t-shirts The initiative was anchored by limited-edition GallagHER fundraising t-shirts sold at GSX, with 100% of proceeds benefiting BCRF. GSX attendees embraced the cause enthusiastically, helping Gallagher shatter their fundraising expectations. “Security Meets Solidarity shows what happens when purpose and people come together,” says Melissa. “Seeing our peers rally behind such an important cause reinforced that protecting what matters most goes far beyond the technology we create - it’s about the impact we make together.” Vital funds for breast cancer research Gallagher Security extends a heartfelt thanks to everyone who contributed to Security Meets Solidarity. The initiative not only raised vital funds for breast cancer research but also strengthened connections across the security community, reminding us that compassion and collaboration are as critical as innovation when it comes to protecting what matters most.
DeterTech, a major innovator of risk management and crime prevention solutions, has donated £5,000 to National Crimebeat, a youth-focused charity that supports community-led crime reduction initiatives across the UK. National Crimebeat is passionate about empowering the next generation and DeterTech’s donation will aid the charity in continuing to support young people across the UK, rewarding a broad range of initiatives led by young people to reduce crime. National Crimebeat holds yearly awards, inviting finalists to the Royal National Hotel in London to recognize and celebrate the young people shaping impactful initiatives. Grass-root initiatives National Crimebeat, the official youth-focused charity of the High Sheriffs’ Association of England and Wales champions grass-root initiatives that empower young people to take the lead in community projects. In support of this mission, DeterTech has also donated £5,000 to the High Sheriff of Shropshire’s Fund to help fuel these impactful efforts. Beyond financial support, DeterTech is actively involved in community education around safety and crime prevention. Furthermore, the company sees this partnership as a shared mission, to get young people engaged in local policing efforts. Making communities safer “National Crimebeat truly resonates with everyone at DeterTech – making communities safer and providing greater peace of mind to all,” explained Megan Marsh, Partnerships and Events Lead, DeterTech. “Supporting National Crimebeat’s incredible work aligns perfectly with our mission to deter crime and protect what matters most, and we are proud to contribute to initiatives that give young people the opportunity to make positive change and thrive. We can’t wait to see what impactful projects are to come.” Youth led community projects Mandy Thorn MBE DL, Chair, National Crimebeat, added: “We are extremely grateful for DeterTech’s generous donation. With their support, we can continue to celebrate and reward youth led community projects that give young people hope, purpose, and the tools they need to make positive choices.” This partnership underscores DeterTech’s ongoing commitment to corporate social responsibility and community engagement, demonstrating that preventing crime is not only about technology, but also about empowering people and creating safer futures for all.
Princeton Identity, a pioneer in advanced iris biometric identity solutions, is proud to announce that Brian K. Tuskan has joined the company as its newest Executive Advisor. Tuskan brings more than two decades of experience in law enforcement and corporate security leadership, having served as Chief Security Officer for both Microsoft and ServiceNow, where he helped define industry-pioneering programs in global security, safety, and intelligence-driven operations. Deep strategic security expertise At Princeton Identity, Tuskan will leverage his deep strategic security expertise and visionary approach to help guide the company’s growth in existing markets while advancing new applications for its industry-pioneering iris and multimodal biometric technologies. “Brian is an industry icon with a remarkable ability to bridge real-world security needs and emerging technologies,” said Bobby Varma, CEO of Princeton Identity. “His leadership and insights will be invaluable as we continue to expand the reach of our Iris-on-the-Move™ technology into new markets and use cases. We’re thrilled to have him on board as a trusted advisor during this exciting stage of growth.” Tuskan’s career Tuskan’s career spans over 20 years in both public service and the private sector. Beginning as a police detective and SWAT officer, he transitioned into the corporate world to lead security operations for two of the most influential technology companies in the world. Today, he advises startups focused on AI, safety, and security innovation, and is the founder of Cop to Corporate, a nonprofit organization helping law enforcement professionals transition successfully into private-sector careers. Iris-on-the-Move™ technology “I’m honored to join Princeton Identity at such a pivotal time in the evolution of biometrics and identity assurance,” said Brian Tuskan. “The company’s iris-based authentication technology is redefining what secure, seamless access can be — and I’m excited to help guide its continued innovation and impact across global markets.” For over 20 years, Princeton Identity has developed and manufactured state-of-the-art iris biometric solutions for access control, time and attendance, point of sale, and border applications. With proven installations worldwide, the company’s Iris-on-the-Move™ technology and scalable identity management software deliver unparalleled accuracy, convenience, and security.


Expert commentary
A key characteristic of many successful companies is that good ideas come from everyone, not just specific departments or job titles. What one person sees as obvious may be questioned by someone else who is less familiar with the product or process. This simple interaction can spark a whole new, faster, and better approach. While valuing tradition is important, if someone uses the phrase “that’s how we’ve always done it,” it’s essential to analyze the process to ensure it remains optimal. Business conditions change rapidly, and what was considered a perfect process last week may need adjustments this week. Comprehensive approach to innovation This comprehensive approach to innovation fosters continuous improvement across all aspects of the organization Innovation should permeate every level of an organization, from product development and customer experience to sustainability practices and employee training. This comprehensive approach to innovation fosters continuous improvement across all aspects of the organization, allowing companies to stay agile, competitive, and in tune with their customers' constantly evolving needs. Addressing real-world challenges At the heart of pervasive innovation in the security industry lies the development of smart products and solutions that address real-world challenges. This approach integrates advanced technologies to enhance security while improving user experience. For instance, the integration of mobile credentials, biometrics, real-time wireless locks, intelligent keys, and cloud-connected access control systems exemplifies how technology can streamline operations and provide users with seamless and secure access. Offering user-friendly solutions These advancements reflect a deep understanding of user needs and preferences, offering solutions that are not only secure but also convenient and user-friendly. A notable example is UniKey's Kēvo, the first Bluetooth-enabled touch-to-open smart lock, introduced in 2013. Developed in partnership with Kwikset, this innovative product allowed users to unlock doors simply by tapping the lock with a compatible smartphone. By continuously innovating across various aspects of security products and solutions, companies can ensure that their offerings remain relevant and effective in addressing the evolving challenges of the security landscape. Design-driven features Products designed for quick and straightforward installation reduce labor costs and minimize downtime Innovation extends beyond technology to encompass design-driven features that prioritize user convenience and satisfaction. For instance, ease of installation is a critical factor in the adoption of new door hardware. Products designed for quick and straightforward installation reduce labor costs and minimize downtime, making them more attractive to both installers and end users. For electronic locks, long-lasting battery performance is essential for minimizing maintenance and ensuring reliability. Products with extended battery life reduce the frequency of replacements and enhance user confidence. Incorporating antimicrobial finishes into door hardware addresses growing concerns about hygiene and cleanliness. Taking hygiene a step further, touchless technology in door hardware minimizes physical contact, reducing the potential for cross-contamination and enhancing user convenience. Sustainability initiatives Sustainability initiatives in door hardware have evolved from niche considerations to central pillars of modern product development, not least of which is the growing consumer demand for sustainable products, which is influencing purchasing decisions. According to a Nielsen report, 66% of global consumers are willing to spend more on a product if it comes from a sustainable brand, leading many companies to prioritize the use of recycled and recyclable materials in their products. Beyond material selection, manufacturers are also refining their production processes to minimize environmental impact. Finishing processes are evolving to use non-toxic and low-impact finishing methods, such as powder coating and physical vapor deposition. Energy-efficient door hardware Energy-efficient door hardware plays a significant role in the overall energy conservation of buildings Energy-efficient door hardware plays a significant role in the overall energy conservation of buildings. Properly designed door hardware can help maintain a building’s thermal envelope, reducing heating and cooling demands. For instance, the HID® Signo™ access control reader includes improved power supply technology and energy-saving features that ensure reduced energy consumption when the reader is in a resting state. Environmental Product Declarations To further demonstrate their commitment to sustainability, many manufacturers seek certifications validating their environmental efforts. Environmental Product Declarations (EPD) and Leadership in Energy and Environmental Design (LEED) certifications have become key indicators of a product’s environmental performance. An EPD provides detailed information about the environmental impact of a product throughout its lifecycle, aiding in the transparency that architects and builders require to make informed choices. Similarly, LEED certification emphasises energy savings and broad environmental priorities, including water efficiency, CO₂ emissions reduction, and improved indoor environmental quality. Customer service and training Innovation is also making great strides in the behind-the-scenes efforts of customer service and training. Predictive maintenance technologies are revolutionising how companies manage product performance and customer support. By utilizing data analytics and IoT technologies, companies can offer maintenance alerts, remote diagnostics, and connected support services that anticipate issues and failures before they occur. This shift from reactive to predictive maintenance minimizes service disruptions and enhances customer trust by ensuring products operate at optimal levels. Digital training initiatives Digital training initiatives equip employees and customers with the skills needed to utilize new technologies In parallel, digital training initiatives equip employees and customers with the skills needed to utilize new technologies in a cost-effective and accessible manner. Digital installer certification programs, learning portals, and customer enablement initiatives are all part of a comprehensive strategy to equip stakeholders with the knowledge and skills they need to succeed. By investing in comprehensive training programs, companies foster a culture of adaptability and competence, ensuring that customers can fully leverage technological advancements. This approach not only enhances operational efficiency but also strengthens customer relationships by empowering them with the knowledge to make informed decisions. Incremental improvements While groundbreaking innovations often capture headlines, it’s the steady, incremental improvements that consistently deliver real-world value. Companies can achieve sustained growth and success by focusing on continuous innovation across all facets of the organization. This quiet progress, though less visible, is often more impactful as it builds a solid foundation for long-term achievement. In a world where change is the only constant, fostering a culture of pervasive innovation is the key to sustained relevance and growth.
March is Women in Security Month, a time dedicated to celebrating and promoting the contributions of women in the security field—particularly in cybersecurity. This observance aligns with Women’s History Month, providing an opportunity to reflect on the progress made and the work still needed to advance gender equity in security. evolving role of women in security The security industry has witnessed a steady increase in women's participation. According to ISC2 Research in its “Women’s Role in Filling the Workforce Gap” report, women make up an estimated 20 to 25 percent of the security industry. Promisingly, younger generations are entering the profession at higher rates, with 26 percent of working professionals under 30 identifying as women. The security industry has witnessed a steady increase in women's participation The research tells us that women are thriving in a variety of roles, from engineering and system administration to sales, marketing, and project leadership. Key factors driving this transformation include mentorship programs, male allies advocating for gender equality, and cultural shifts recognizing the unique perspectives and strengths women bring to security challenges. These efforts are fostering more inclusive environments and ultimately strengthening the industry. The value of diverse perspectives in security Security is not a one-size-fits-all industry—each organization and facility has unique needs that require varied perspectives. Greater representation of women has introduced fresh approaches to problem-solving, fostering collaboration and driving innovation. By integrating diverse viewpoints, security professionals can create more effective solutions that better address end-user needs. Industry support for women’s professional growth SIA's WISF offers subcommittees such as NavigateHER, SupportHER, and UpLiftHER Organizations like the Security Industry Association (SIA) and ASIS International have established networking platforms and initiatives to support women in security. Events such as the Security LeadHER Conference provide valuable professional development and networking opportunities. Companies are also investing in science, technology, engineering, and mathematics (STEM) initiatives, hands-on training, and recruitment programs to attract more women into the field. Additionally, SIA's Women in Security Forum (WISF) offers subcommittees such as NavigateHER, SupportHER, and UpLiftHER, which provide pathways for engagement and growth. Challenges women in security face Despite progress, challenges remain. Many women still feel it necessary to repeatedly prove their expertise, take on additional informal responsibilities, or carefully navigate workplace dynamics. Imposter syndrome can be another hurdle, even for accomplished professionals. However, women in security are addressing these challenges by setting boundaries, advocating for themselves, and supporting one another through mentorship. By excelling in leadership and technical roles, women are reshaping outdated perceptions and advocating for more inclusive workplace policies. Steps industry pioneers can take To further support women in security, industry pioneers could: Provide targeted professional development and career advancement opportunities. Foster strong, supportive communities that recognize and mentor women. Implement structured mentorship programs that connect experienced professionals with newcomers. Promote workplace flexibility to help employees balance personal and career commitments. Actively challenge biases and advocate for meaningful change within organizations. Advice for women entering the security field Here are key pieces of advice for women considering a career in security: Own Your Expertise – Have confidence in your knowledge and skills. Seek Out Mentors & Allies – Connect with supportive professionals who can guide your career. Build a Strong Network – Join organizations like ASIS Women in Security, SIA Women in Security Forum, or Women in CyberSecurity (WiCyS), and attend industry events to expand your connections. Speak Up & Take Space – Confidently share your ideas and challenge outdated norms. Develop Resilience & Advocate for Yourself – Push past biases, demand the respect you deserve, and negotiate for fair salaries and promotions. Keep Learning & Stay Ahead – Continually build your expertise to stay competitive in the evolving security industry. The future of women in security As the security industry evolves with technological advancements and global changes, opportunities for women will continue to expand. Women are not just participating in the industry’s growth—they are shaping its future. With growing mentorship programs, male allies advocating for gender equality, and ongoing cultural shifts, the focus is no longer just on breaking barriers but on building bridges to new opportunities.
From where I sit in talking to security pioneers every day, the traditional Global Security Operations Center (GSOC) stands at a critical inflection point. Security teams are up against challenges in staffing, operational efficiency, and more threat complexity, which means “thinking outside the box” is becoming critical. The use of artificial intelligence (AI) is emerging as more than a buzzword in these situations; it’s becoming a game-changing force multiplier in security operations. Reaching a breaking point Today's GSOCs face a perfect storm of operational challenges. Security operators, typically earning between $20-40 per hour, require extensive training periods lasting weeks or months as a result of the numerous applications they’re tasked with using. Yet the industry grapples with insane turnover rates of 100-% to 300% annually, creating a costly cycle of continuous recruitment and training. Meanwhile, operators are drowning in video feeds and alarms, leading to fatigue, missed incidents, and delayed response times. Practical applications for AI The reality of many GSOCs, however, is a disjointed mess of multiple applications The GSOC is the center of an organization’s security and in a perfect world, all of the data related to safety across multiple facilities flows through there, giving operators a clear picture of what’s going on at any given time. The reality of many GSOCs, however, is a disjointed mess of multiple applications. Think about all the platforms needed to respond to a single incident – access control alarm, video to verify, standard operating procedures (SOPs) stored on a shared drive, radios to get a hold of a guard to dispatch, finding a list of emergency numbers and corresponding it to where the incident is happening, and manually logging the results. Steps into a single platform Not only is there a case for unifying all of these steps into a single platform that pulls in data from various sources, but layering response with AI-enabled technology to achieve the following: Real-time video analysis and threat detection. AI-enabled systems are revolutionizing surveillance operations by simultaneously monitoring multiple video feeds, detecting and classifying objects, people, and behaviors in real-time. The technology excels at identifying suspicious activities such as loitering, abandoned objects, or unauthorized access attempts, automatically alerting operators to potential threats – or even identifying false alarms that can take human operators away from the work they’re doing – all while maintaining vigilance across numerous camera feeds. Intelligent alarm management. One of AI's most immediate impacts is in addressing the chronic problem of false alarms. By analyzing multiple data points simultaneously, AI technology can intelligently filter and verify alerts, dramatically reducing false positives that traditionally consume valuable operator time. An AI GSOC operator, for example, can assess an incoming alarm and either identify it as a real threat (then escalate to its human supervisors) or use SOPs to determine that the alarm is false, providing feedback and reasoning that’s collected and assessed. This intelligent triage ensures security teams focus on genuine threats rather than chasing false alarms, significantly improving response efficiency. Automated incident response. When security incidents occur, AI systems can instantly gather relevant data from multiple sources – including video feeds, access control logs, and sensor data – to generate preliminary incident reports and initiate appropriate response protocols. This automation ensures consistent application of security procedures while maintaining detailed documentation for compliance and analysis purposes. Predictive analytics and pattern recognition. By analyzing historical data, AI systems can identify patterns that might indicate emerging security risks before they materialize. This includes detecting unusual access patterns, anomalies in foot traffic, or behavioral patterns that suggest potential future security threats, enabling proactive rather than reactive security measures. The benefits to the business While AI can be used in so many ways to reduce false alarms, create more efficiencies, and help GSOC operators elevate their roles to be more strategic, there is still a stigma associated with its use. However, a lot of the conversations around this kind of investment can be elevated to reflect positively on the business, which can help achieve more buy-in from leadership. Here are some of the ways: Operational improvements: Dramatic reduction in false alarm rates through intelligent verification systems that analyze multiple data points simultaneously Response times cut significantly through automated triage and threat assessment protocols Standardized and consistent application of security protocols across all shifts and incidents More efficient resource allocation through AI-driven staffing recommendations based on historical patterns Expanded security coverage without proportional staffing increases, enabling monitoring of multiple locations simultaneously Enhanced incident documentation through automated report generation and data collection Improved situational awareness through real-time correlation of multiple data sources Reduced training time for new operators through AI-assisted guidance systems Better compliance management through automated protocol enforcement and documentation Business impact: Significant cost savings through reduced false alarm response and more efficient staffing Decreased liability exposure through comprehensive incident documentation and consistent protocol application Enhanced regulatory compliance through automated record-keeping and standardized procedures Improved risk management through predictive analytics and early warning capabilities Better return on investment for security technology through integrated AI-driven optimization Increased scalability of security operations without proportional cost increases More robust business continuity through improved threat detection and response Enhanced protection of critical assets through constant AI monitoring Personnel impact: Reduced operator burnout through automation of routine and repetitive tasks Enhanced job satisfaction as operators focus on strategic decision-making rather than routine monitoring Improved work-life balance through more efficient resource allocation New career development opportunities in AI-enabled security operations Better retention rates through reduced stress and increased job engagement Enhanced skill development as operators learn to work with advanced technology Improved team collaboration through AI-assisted information sharing More effective decision-making support through AI-driven insights Greater operator confidence through AI-backed verification of security events AI and the road ahead Integration of AI into the GSOC is about more than simply technological advancement While security historically hasn’t changed as quickly as its cyber counterparts, its evolution is imminent. Integration of AI into the GSOC is about more than simply technological advancement; it’s a seismic shift in how organizations approach security operations. The future of this is in the partnership between human expertise and AI capabilities, where technology handles routine monitoring and initial threat assessment, allowing security personnel to focus on complex decision-making and strategic security initiatives. Transformation of security operations For security pioneers looking to implement AI in their GSOCs, success lies in thoughtful integration that considers both technical requirements and human factors. By carefully balancing automation with human oversight, organizations can create more effective, efficient, and responsive security operations that deliver tangible value to the enterprise. The transformation of security operations through AI isn't just about doing more with less – it's about doing better with what we have. As threats become more sophisticated and security demands continue to grow, AI-enabled GSOCs will be better positioned to meet these challenges while delivering enhanced protection for people, assets, and operations.
Security beat
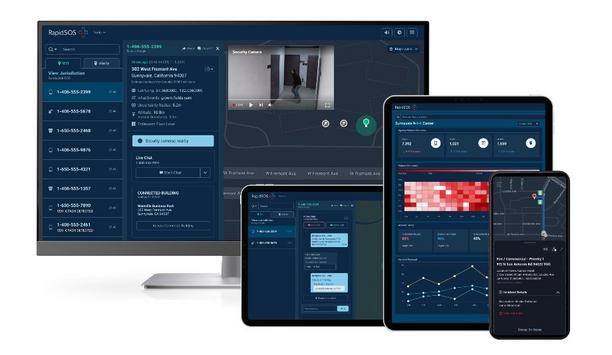
In an emergency, information is pivotal. More information provides better understanding of an emergency and empowers potentially life-saving decision-making. Emergency response teams depend on information to guide their efforts and to deliver targeted assistance. On the front lines of emergency response are 911 and field responder agencies, which must direct reaction to life-or-death situations rapidly and efficiently. Historically, 911 operators had to respond based on very little information, perhaps just a voice on the phone or a location on their screen. Providing critical information Today, there are literally millions of information sources available, ranging from connected buildings to vehicle telematics to live video streams to health information from wearable devices. In fact, there are 540 million connected devices, any one of which could provide critical information in an emergency. But how can those information sources be leveraged to improve emergency response? That’s the mission and value proposition of RapidSOS, an ‘intelligent safety platform’ company that connects 911 operators with the vast universe of information available to promote better and faster emergency response. Highly sophisticated operation The platform is integrated into every major public safety software system and first responder agency “RapidSOS fuses human and artificial intelligence to put critical information from any connected device directly into the existing systems and operating procedures of first responders across the United States,” says Michael Martin, CEO of RapidSOS. RapidSOS is widely used by first responders. The platform is integrated into every major public safety software system and first responder agency. There are more than 4,600 software integrations that serve more than 21,000 first responders and 911 agencies. In 2023, RapidSOS supported the lifesaving work of public safety across 171 million emergencies with 3.3 billion data payloads. The system is adaptable and configurable to support any agency, from a highly sophisticated operation in New York City to a local sheriff running their own 911 center. Intelligent analytics and reporting RapidSOS Unite is the latest evolution of the product, a single solution that includes AI automation, rich content pathways, redundant connection to caller phones, and access to millions of connected devices. In an emergency, Unite intelligently fuses data from among millions of sensor feeds into a unified picture of an incident, allowing public safety officials to view real-time location, health profile, telematics, alarm data, and more. RapidSOS Unite is the latest evolution of the product, a single solution that includes AI automation RapidSOS offers core modules that handle call, text, video, sensor, mapping, and administration tools, and that provide partner data from connected devices. Additional modules provide enhanced geographic information system (GIS) data, and automated translation and transcription. There is also a single sign-on (SSO) upgrade, intelligent analytics and reporting, and seamless integration into field responder applications. Field responder applications Consider how an emergency might unfold and how RapidSOS can help. In a car accident, data from a modern automobile telematics system can alert a 911 operator of the accident as it happens. Data from a passenger’s wearable device might provide information about their health and condition. A nearby video or traffic camera could fill in details of how the accident occurred. Useful information in an emergency might come from any one of thousands of sources, including public safety data, sensor feeds, enterprise security systems, smart phones, etc. In a train derailment, electronic access to the cargo manifest can identify which train cars contain hazardous materials and how to manage the specific type of hazmat. This information could save valuable time when responding to incidents like the Feb. 3, 2023, Norfolk Southern train derailment involving 38 cars in East Palestine, Ohio. Consider how an emergency might unfold and how RapidSOS can help Institutional security partners Norfolk Southern is one of the companies that provides information to first responders using RapidSOS; in effect, the company provides a direct digital link from their rail security operations to any first responder in the United States. Amazon’s global operations centers also interface with RapidSOS to provide critical information to first responders. Partnering with corporate security helps to better support the flow of data from institutional security partners and their solutions. Information can transform and guide emergency responses. For example, in a structure fire, real-time sensor feeds throughout a building can help 911 and first responders understand how the fire is progressing. Real-time security camera footage Having access to live feeds can save lives as 911 provides pre-arrival instructions such as CPR Leading the way to providing video feeds from private camera systems to 911 operators is an agreement between Eagle Eye Networks and RapidSOS, which was announced in April 2024. The agreement allows an enterprise to opt-in to share real-time security camera footage from an Eagle Eye video stream during a live 911 call. Having access to live feeds can save lives as 911 provides pre-arrival instructions such as CPR. “Security cameras are crucial in many locations, including schools, but previously those cameras could not be accessed by 911 during an emergency but were only used for investigation after an incident,” says Martin. Improving fire and life safety systems RapidSOS is also integrated with Honeywell’s Connected Life Safety Services (CLSS) system, a cloud platform that combines software and hardware to improve fire and life safety systems. Technology integrations between the two companies further modernize and digitize the public safety communications process to provide faster, more accurate communications with emergency centers (i.e., 911 agencies). RapidSOS technology securely transmits detailed data about an emergency CLSS provides real-time visibility and connectivity to help systems integrators and facilities managers make informed decisions and manage fire systems more efficiently. When combined with Honeywell's solutions, RapidSOS technology securely transmits detailed data about an emergency, such as the type of hazard, severity, and location within the impacted building, to emergency response centers. Video object detection Rapid SOS’s emerging Harmony artificial intelligence (AI) product serves as a ‘co-pilot’ for 911 operators, helping them manage the high volume of emergencies by making their response more efficient. Harmony pulls all the sensor feeds in an emergency and works to make only the most important information available in the hands of 911 and first responders. Harmony can take key insights from text and video data, use ‘sentiment analysis’ to determine the emotion tone of a message, and help 911 professionals using language translation, keyword alerts and video object detection. Harmony can help local agencies as they address a 25% average staffing shortage by providing additional support to 911 professionals while lessening the workload. Harmony is also working to help RapidSOS expand the ecosystem, stitching more data together and quickly making it more actionable than ever. Emergency response system RapidSOS also interfaces with Iamresponding, a comprehensive end-to-end emergency response system for first responders in the fire and other emergency sectors. Iamresponding’s field responder application is used by RapidSOS to get information out to first responders in the field. More than 650,000 first responders use RapidSOS’s field application RapidSOS’s recent acquisition of Iamresponding helps the company improve the connection with the last mile “in-the-field” piece of the puzzle, ensuring partners across computer-aided dispatch (CAD), integrated applications, mobile data terminals, body cameras and other responders have access to critical data. More than 650,000 first responders use RapidSOS’s field application. Enhancing emergency response RapidSOS’s Safety Pioneer Program formalizes the important partnership between RapidSOS and public safety agencies. Participants in the program receive early access to new platform features, contribute to the platform roadmap, and drive feedback to enhance emergency response. “911 and first responders do incredible lifesaving work,” says Martin. “Everything we have done and built at RapidSOS is a direct result of the engagement, partnerships, inside advice and insight we have gotten from public safety. We have learned from them, developed new technologies and tested them.” Martin adds: “Companies have data and we now know how to make that data actionable into the hands of 911 and first responders to save lives. This is an exciting moment for us continuing our mission in partnership with public safety, and for technology and security companies to have a major hand in that.” {##Poll1719488782 - What is the most valuable benefit of artificial intelligence (AI) in an emergency call center?##}
Already a strong player, particularly in New Zealand and Australia, Gallagher is still climbing in the U.S. market, which it sees as a big opportunity to invest in the company. Active in the United States for 10 years, Gallagher undertook a more aggressive growth strategy about five years ago. There are 52 employees in Gallagher’s U.S. security business, and about half the workforce has been hired in the last couple of years. They have grown from three sales territories to 16, operated by a full sales and engineering staff. Culture of innovation sets As it happens, Gallagher’s U.S. headquarters is located a short drive from my home office in the wider vicinity of Atlanta. I missed seeing them at GSX in Dallas, so we scheduled an in-person visit to catch up on their company. Gallagher’s strong culture of innovation sets them apart, as does their “people-first” commitment, says Scott Elliott, Gallagher’s Executive Vice-President, The Americas. “We have intentionally recruited for a diversity of thought that drives the business,” says Elliott. “We are a people business.” Melissa Vidakovic, Director of Marketing, Americas; and Scott Elliott, Executive VP, Americas, at Gallagher Security's office in Canton, GA. Unified approach An advantage Gallagher has in the market is total ownership of their supply chain; it manufactures each of the hundreds of products used across their solutions, from plastic components to readers to controllers to their own software systems. Among other advantages, the unified approach enables tighter control from a hardening and cybersecurity perspective, enabling them to minimize any threat vectors or vulnerabilities. The strategy also avoids dependence on third-party suppliers, which was a huge advantage during recent supply chain disruptions. While competitors struggled with availability issues related to third-party manufacturers, Gallagher’s supply was uninterrupted. Gallagher’s commitment Gallagher uses the same norms as the nation and subjects its effects to inner and outer penetration As a manufacturer serving a broad spectrum of markets, it’s Gallagher’s commitment to the high end of the market (e.g., high-security applications), where the company incorporates core tenets such as authentication and encryption. Gallagher uses some of the same standards as the government and subjects its products to internal and external penetration testing. These core strengths are also integral to Gallagher’s complete product line. “If it’s good enough for a high-level customer, it’s good enough for Mr. Business Owner,” says Elliott. The New Zealand company was founded in 1938 and was the first company to commercialize the electric fence, which it still uses for its agriculture business sector, separate from the security business. Gallagher entered the access control business 35 years ago in 1988 when a product used to restrict access to fuel pumps evolved into broader access control. Gallagher platform In the intervening years, the product has grown into a unified platform that incorporates access control, intrusion detection, and perimeter detection in a single ecosystem. “The platform is all-encompassing,” says Elliott. “No other platform does all three.” Augmenting access control, intrusion, and perimeter protection, there are other applications available in the Gallagher platform, such as workforce management, health and safety functions, and a spectrum of features useful to a wider stakeholder community. Fatigue management applications For example, Gallagher can implement routine randomized checks to proactively mitigate potential risks such as drug or alcohol abuse, thus ensuring workers are fit to work, to operate various machinery and that they do not pose a threat to fellow employees or the company. “Fatigue management” applications can monitor the use of equipment to avoid repetitive injuries or manage how long an employee works at a job site, requiring a worker to swipe or tap a card to a reader mounted on a machine to monitor and limit the time they operate that machine. Mobile mustering provides location and identification of evacuees in case of an emergency. Impact of digital transformation Gallagher’s “Better Ways of Working” concept zeroes in on the impact of digital transformation Gallagher is also embracing the “digital transformation” of the industry. Security companies must adapt to a more agile workforce and shifting processes, says Elliott. Gallagher’s “Better Ways of Working” concept zeroes in on the impact of digital transformation on their workforce. They also seek to address the changing workforce, where Gen-Z’ers work side-by-side with tenured, experienced workers, and where creating trust is the best approach to closing the generational gap. Gallagher also seeks to educate the market on trends such as artificial intelligence (AI), machine learning, cloud adoption, various service delivery models, and other issues. Industry consolidation Gallagher has more than 1,200 employees; operates in 140 countries, from South America to Canada, Europe to the Asia-Pacific and Australia; and serves almost 16,000 customers. Gallagher is part of New Zealand’s growing technology export sector, which is growing 30% faster than the overall economy and is now the second-largest export sector in New Zealand. In an age of industry consolidation and a market dominated by corporate conglomerates, Gallagher is a privately held organization seeking to be agile and innovative, and to deliver customer value more quickly. Gallagher re-invests about 15% of its profits into research and development. “Our customer service is the primary reason people buy from us,” says Elliott. Security integrators Security integrators quickly appreciate the breadth and strength of the product line Gallagher positions itself as an alternative in a market in the midst of disruption. Brand awareness continues to be a challenge in the United States, and the sales team often hears the question: “Who is Gallagher?” Once the introduction is made, security integrators quickly appreciate the breadth and strength of the product line, says Elliott. “We allow our customers to select among best-of-breed platforms, and [using open systems,] we are not limited by the technology we offer,” says Elliott. “Our value proposition to the integrator channel is our focus on the relationship,” says Elliott. Supporting end users through an authorized, certified channel, Gallagher also emphasizes value, cost-competitiveness, and cybersecurity. “Our partner relationships are built around cultural alignment,” says Elliott. Product innovation perspective What’s ahead for Gallagher and for the industry as a whole? Hard to say, notes Elliott, given the unfolding of unpredictable geopolitical and financial trends. However, from a product innovation perspective, Gallagher will continue to evolve, balancing a dependence on “cash cow” legacy product lines with investment in leapfrog innovations such as frictionless access control, cloud platforms, and mobile systems. In general, Elliott predicts AI will yield an opportunity to analyze a person’s pattern of behavior and intent, thus enabling a security system to adapt down the road. “With the ability to predict with some degree of certainty what might happen, these capabilities will evolve,” says Elliott.
Active shooter situations grab the most attention, but there is a long list of other threats facing schools, including bullying, vandalism and emergency medical situations. Broadly speaking, a comprehensive approach to school security should prioritize prevention, preparedness and response to all threats. Holistic security approach “Fostering a culture of safety within a school, which involves strong relationships, trust, and communication, is highly effective and does not require significant costs,” says Christin Kinman, End User Sales Consultant with Allegion, a security manufacturer. “It is crucial to educate stakeholders about the unintended consequences of quick fixes, like barricade devices, to ensure informed decision-making and a holistic security approach. The goal should be to promote safety and security for all, every day, in every situation.” Integrated and successful security plans While this might solve a particular challenge, it can also create unintentional conflicts" "Creating an integrated security plan requires a multi-faceted approach," says Kinman. "Too often, security measures are implemented as a reaction to either an event or a specific vulnerability. While this might solve a particular challenge, it can also create unintentional conflicts," adds Kinman. “Creating a successful security plan involves a comprehensive approach,” she says. “An effective, systematic approach begins with assessing, identifying, and valuing assets, identifying threats and vulnerabilities, quantifying the impact of a loss, analysis, and prioritization, and finally, development of mitigation measures.” Safety and Security An effective resource is the Partner Alliance for Safer Schools (PASS), which provides a framework to help with school assessments, including identifying and valuing assets, identifying external threats and internal vulnerabilities, assessing the impact of loss, and analyzing and prioritizing mitigation measures. Safety and security are words used seemingly interchangeably when it comes to schools, but they mean different things. “How we define these terms influences planning and addressing challenges,” says Kinman. “It is easiest to think of these terms as being either external or internal to the individual.” Coordinated security Safety is internal to the individual and relates to the individual’s perception of being free from harm Security is external to the individual and encompasses the protective physical, emotional, and environmental measures implemented in conjunction with policies, procedures, and training, as well as mental health measures and social and emotional learning. Safety is internal to the individual and relates to the individual’s perception of being free from harm or danger. Coordinated security measures create an environment of safety. Four main elements of physical security Kinman lists four main elements of physical security, often referred to as the 4D’s. These elements are deter, detect, delay, and deny: Deter refers to measures implemented to prevent an attack or threat from happening. These are usually visual deterrents that communicate legitimate use. Detect refers to measures that can detect the presence of a threat, such as video surveillance and monitoring. Delay refers to measures that slow down an attack or increase the level of effort needed for an incident to occur. Finally, deny refers to measures that prevent or restrict access to valued assets. Four layers of ground perimeter A layered approach to school security creates “layers” that must be defeated for an event to occur, says Kinman. Typically, the four layers are the ground perimeter, the private grounds around the building, the building perimeter, and the building interior. The ground perimeter layer demarcates public vs private space, and deterrence is the primary objective. The grounds layer allows for identification of legitimate vs illegitimate users and detection is the primary objective. The building perimeter layer prevents illicit users’ intent on harm from gaining access. The primary objectives at this layer are delay/deny. The building interior protects the most valuable assets, and the denial of an unauthorized individual is the primary objective. Report on Indicators of School Crime and Safety The second element is impact, also rated on a scale of 1-5 and ranging from negligible to catastrophic “Quantifying loss and assessing risk is one of the most important steps in creating an integrated security plan,” says Kinman, who explains that the two elements that guide this step are probability and impact. Probability is the likelihood that an event will occur, typically rated on a scale of 1-5 ranging from rare to almost certain. The second element is impact, also rated on a scale of 1-5 and ranging from negligible to catastrophic. “Probability multiplied by impact equals risk, which has a score ranging from 1-25,” says Kinman. “The higher the score, the higher the risk.” An analysis of vulnerabilities and threats using a matrix yields a systematic approach to prioritize improvements and identify mitigation measures. For statistics on crime and safety in schools, visit the Report on Indicators of School Crime and Safety: 2022. Security improvements “The costs of school security encompass various aspects, including physical measures, personnel, training and policy enforcement,” says Kinman. “While there is no fixed amount, it often involves investments in technology, such as access control and emergency response systems. Many security improvements do not require additional funding, like training staff and students on security protocols and implementing policies to create a culture of safety.” Generally, funding for public school security is a shared responsibility among federal, state, and local governments; communities also contribute. “Striking a balance between shared responsibility and ensuring adequate resources is crucial for effective school security,” says Kinman. K-12 school security Community members and parents can donate by being vigilant and noting any suspect activities Various stakeholders play crucial roles in enhancing K-12 school security in addition to schools and communities. Stakeholders include community members, parents, local government, local law enforcement, first responders, and non-profit organizations. “Engaging these stakeholders fosters a comprehensive approach to school security,” says Kinman. Community members and parents can contribute by being vigilant and reporting any suspicious activities. Local government can support schools with funding and resources, while local law enforcement and first responders can provide expertise, conduct drills, and establish emergency response protocols. Safe and secure learning environment In addition, non-profit organizations can offer valuable resources, training, and support programs to address specific security concerns. “By involving all these stakeholders, schools can tap into a diverse range of expertise, resources and perspectives, pioneering to a more effective and comprehensive approach to school security,” says Kinman. “Collaboration and communication among these entities are vital to ensure a safe and secure learning environment for students and staff.”
Case studies
How do you rethink and transform building access for a 241-year-old company? BNY started by asking employees. The response was encouraging. The BNY team found that employees embraced the concept of mobile access solutions. The thought of implementing access solutions was already being considered by the company and the team was excited about the idea of providing a modern experience that allows employees worldwide to conveniently access their building spaces with a simple iPhone or Apple Watch. How powerful of a concept “The whole idea of people navigating around our facilities globally — it just brings a smile to your face,” said Ken Damstrom, Global Head of Corporate Security at BNY. “But it really brings a smile to their face because when they come to work they come with their iPhone they don’t necessarily need to come with their (physical) ID badge and how powerful of a concept is that?” Getting started with the right team To put everything in motion, BNY engaged connected access network provider SwiftConnect and mobile access provider, HID. Selecting experienced and reputable partners was important for BNY, along with the technologies that they brought to the table. For this project, those technologies included employee badge in Apple Wallet alongside HID’s mobile-enabled Signo readers and the reliability of the SwiftConnect connected access network. How does the technology work? Two key components of BNY’s initiative were essential to its success. Employee badge in Apple Wallet, paired with HID’s mobile-enabled Signo readers gives employees and their guests easy and secure access to corporate spaces using only their iPhone or Apple Watch. Users can simply hold their device near a reader to access doors, turnstiles, elevators, spaces and more. SwiftConnect unifies identity and physical access into one effortless experience, connecting systems and spaces into a unified network. It supports on-demand access via mobile credentials and optimizes existing methods like fobs and cards for secure, consistent access — replacing friction with fluidity at every interaction. “What we learned by partnering with SwiftConnect and HID was employee badge in Apple Wallet was absolutely ready for prime time,” said Ken Damstrom. “We’ve had nothing but confidence in rolling it out in our organization.” Making mobile access technology a reality With full support from their partners, BNY launched their new mobile access solution at their headquarters in New York City, then expanded to other offices in Boston, London and India, as well as others. They’ll continue until every BNY office worldwide is using the technology — at 110 locations in 35 countries. Regardless of which country the technology is implemented, employee badge in Apple Wallet will work the same across BNY’s facilities. That’s important because their employees can seamlessly and securely enter and move around multiple locations. Also, with Express Mode, employees do not need to unlock their device to use their employee badge in Apple Wallet. Even if the phone needs to be charged, the device can still be used to access spaces with Power Reserve mode. Advantage of privacy and security When an employee has an employee badge in Apple Wallet, their data is never shared with Apple or stored on Apple servers. If their iPhone or Apple Watch is misplaced, the owner of the device can promptly use the Find My app to lock the device and help locate it. Employee badges in Apple Wallet are stored on personal devices and take full advantage of the privacy and security built into iPhone and Apple Watch. “We wanted consistency across our real estate portfolio, so whether you’re in New York, Lake Mary or London, you know how to access the site because you know how to use employee badge in Apple Wallet,” said Dafna Alsheh, Global Head of Workplace Experience & Design, BNY. Combination of technologies The combination of these technologies is now helping BNY create that convenient, quick access experience for employees — while ensuring a secure workplace. “One of the things that makes employee badge in Apple Wallet really impactful is that it works the same at work as it does when they’re at the store or on the subway because you don’t have to teach people how to use it,” said Dafna Alsheh. “We’ve had people who are like, ‘wow this just works.’ But when they realize they can use their Apple Watch, then they’re like, ‘this is magic.’”
Omnilert, a pioneer in AI-driven safety solutions and AT&I Systems, announced that Amerant Bank has chosen Omnilert’s AI technology to help bolster the security at all of its locations in Florida. AT&I Systems, a longtime security partner of Amerant Bank, was chosen as the security integrator. Omnilert’s software, which recently received the full SAFETY Act Designation by the U.S. Department of Homeland Security (DHS), will be integrated into more than 160 existing Amerant Bank cameras to provide advanced 24/7 surveillance with automated response capabilities. Key layer of security “Omnilert technology has become a key layer of security that can transform traditional surveillance capabilities and ensure a fast, robust and automatic response in an emergency,” said Dave Fraser, CEO of Omnilert. “With our software running non-stop in the background, Amerant can focus on carrying out their daily business knowing their workers and patrons are being kept safe from harm.” New and innovative ways to enhance the safety “At Amerant Bank, we are always looking for new and innovative ways to enhance the safety of our bank locations, and Omnilert’s AI technology will be an important part of our overall security infrastructure,” said Orlando Gonzalez, Head of Corporate Security at Amerant Bank. “Integrating the software into our existing cameras made the installation quick and seamless, and once installed, it transformed these cameras into powerful, intelligent surveillance devices that are constantly detecting potential threats.”
The slit lamp examination is one of the most important diagnostic techniques in ophthalmology. It enables a detailed examination of the anterior, middle and posterior segment of the eye. Ophthalmologists can use it to recognize the smallest changes, anomalies or damage. This procedure is used for the early detection and monitoring of the progression of eye diseases such as corneal injuries, eye infections, retinal detachment or macular degeneration. However, the eye with its fast movements is a challenging subject to photograph; motion blur and shaking are typical image errors. IDS USB3 Vision industrial camera OCULUS Optikgeräte GmbH develops instruments for eye diagnostics for ophthalmologists To facilitate diagnostics for ophthalmologists and opticians, improve the workflow and at the same time shorten examination times, fast and reliable slit lamp documentation systems are required. They must provide meaningful images and be designed to be user-friendly and ergonomic. The German company OCULUS Optikgeräte GmbH develops instruments for eye diagnostics for ophthalmologists, optometrists and opticians. Part of the extensive portfolio: one of the world's smallest and lightest image documentation systems for slit lamps. A powerful, high-resolution USB3 Vision industrial camera from IDS is integrated, especially for applications in medical technology and microscopy. Efficient system The OCULUS ImageCam®3 universal slit lamp image documentation system is not only intuitive and easy to use, but also sets high standards in digital slit lamp photography. This includes an outstanding field of view that enables highly precise diagnoses of the anterior, middle and posterior segments of the eye. The images are captured by a particularly low-light, high-performance IDS camera from the USB3 uEye+ CP family. OCULUS ImageCam® 3 OCULUS ImageCam® 3 makes this possible without any loss of quality "Only a fast camera delivers low-noise images in the difficult recording situations at the eye," explains Michael Moos, Product Manager at OCULUS, the choice of camera model. Another important requirement criterion is speed. "The advanced camera features enable continuous shooting at up to 60 frames per second. Among other things, these series recordings make it possible to record the eye during breaks in movement. The innovative frame-out-of-video function enables simple documentation of the entire examination process at the slit lamp, whereby the best quality individual images can then be selected for evaluation," says Michael Moos. The OCULUS ImageCam® 3 makes this possible without any loss of quality while minimizing the time required. Powerful camera The IDS camera from the CP family is predestined for use in medical technology, as it offers extensive pixel pre-processing and has an internal 120 MB image memory for buffering image sequences. This enables a high data rate of 420 MByte/s, low CPU load and easy integration. The Sony Pregius IMX265 in the model used here is considered one of the best CMOS image sensors in the 3 MP class. The USB3 Vision industrial camera U3-3270CP Rev.2.2 with the 1/1.8" global shutter sensor thus achieves a resolution of 3.19 megapixels (2064 x 1544 px). IDS test camera functions The IDS camera from the CP family is predestined for use in medical technology "In this case, however, the image is scaled down using AOI in order to achieve a significantly higher frame rate," explains Phillip Schissler, Sales Manager Medical and Microscopy at IDS. OCULUS has integrated the camera with the IDS peak software development kit. "IDS peak allows users to test camera functions in detail and optimize them for your own applications," says the IDS Medical expert. Decisive selection criterion for the model However, the camera is not only recommended for medical technology and microscopy in terms of sensitivity, dynamic range and linearity. In addition to the required light intensity and speed, the size of the camera was also a decisive selection criterion for the model. At around 50 grams, the camera's small 29 x 29 x 29 millimetre magnesium housing is as light as it is robust, underlining its suitability for space-critical applications. Facilitated slit lamp diagnostics A beam splitter divides the light between the camera and the eyepiece of the slit lamp To deliver optimum diagnostic images, the system includes a high-quality beam splitter in addition to the camera. A beam splitter divides the light between the camera and the eyepiece of the slit lamp to simultaneously illuminate and view the eye, allowing a detailed examination of each eye segment. The beam splitter of the OCULUS system has a purely mechanical iris diaphragm that significantly increases the depth of field, regardless of the position of the pathological findings. It can also be adapted to all commercially available slit lamps. Highest quality standards in laboratory and diagnostics "The camera unit and the beam splitter are extremely small and light. This means in daily practice: It is barely noticeable, is very easy to attach and delivers images like no other in this size. This makes daily slit lamp diagnostics easier in the truest sense of the word," says the manufacturer. In terms of image quality, reliability and long-term availability, IDS stands for the highest quality standards in laboratory and diagnostics. Benefit from the image documentation system The slit lamp photos of the OCULUS ImageCam® 3 help factual documentation of eye states The slit lamp photos of the OCULUS ImageCam® 3 enable objective documentation of eye conditions in order to monitor the progress of diseases and compare treatments. Patients also benefit from the image documentation system. The visual references of the diagnosis created in this way help them to better understand their state of health and the doctors' treatment plan. The medical findings can be saved and archived accordingly. Outlook Innovative image processing systems such as OCULUS ImageCam®, which use powerful industrial cameras to deliver informative, high-contrast images with a high depth of field, help to improve diagnostic accuracy, efficiency and patient care in ophthalmology. Artificial intelligence (AI) is increasingly being integrated into the analysis of slit lamp images in order to automatically recognize diseases, support diagnostic decisions, improve the workflow for doctors and develop new treatment methods. Further development of technologies The company develops first-class instruments for eye diagnostics for this clearly defined group of users The company OCULUS Optikgeräte GmbH has been a partner for ophthalmologists, optometrists and opticians worldwide for 125 years. The company develops first-class instruments for eye diagnostics for this clearly defined group of users. The measure of all things is the high demands of customers and the continuous further development of technologies. Over 55% of OCULUS' sales are realised in foreign markets. OCULUS customers' service More than 400 employees work at the OCULUS headquarters. More than 60 % of them work in research and development, production and customer service. With 12 company-owned subsidiaries and more than 200 wholesalers in over 80 countries, OCULUS is at its customers' service around the globe. Founded in 1895, the family business is now jointly managed by the third and fourth generations.
ZeroEyes, the creators of the only AI-based gun detection video analytics platform that holds the full US Department of Homeland Security SAFETY Act Designation, announces that the Northeastern School District (NESD) in York County, Pennsylvania has adopted ZeroEyes' AI gun detection and intelligent situational analysis solution. This proactive step will help protect students, staff, and visitors from gun-related threats. The cutting-edge security system identifies firearms in real-time and delivers actionable intelligence to first responders. Extensive security cameras Gun-related violence continues to be a pressing issue in the United States. Data from the ZeroEyes Gun Violence Research Center shows that 35.9% of shootings analyzed in Pennsylvania occurred on K-12 school campuses. ZeroEyes’ technology will serve as a key additional layer of security to enhance these efforts NESD’s existing security measures include two full-time school resource officers and extensive security cameras. Additionally, the district is transitioning to electronic key card access for all doors, replacing traditional hard keys, and is reviewing remote lockdown capabilities and mass internal notification systems. ZeroEyes’ technology will serve as a key additional layer of security to enhance these efforts. Mass internal notification systems "A colleague introduced us to ZeroEyes, and we were immediately impressed by the potential of their AI gun detection technology," said Dr. Jason Bottiglieri, Superintendent of NESD. "When we learned about the Pennsylvania Commission on Crime and Delinquency (PCCD) grant, which focuses on enhancing school safety in Central Pennsylvania, we saw an opportunity to bring this critical solution to our district.” NESD is a midsized, suburban public school district located in the South Central region of Pennsylvania. NESD comprises eight buildings, including four elementary schools, two intermediate schools, one middle school, and one high school. The district serves over 4,000 students and employs approximately 300 teachers and 500-600 staff members. Law enforcement veterans If these experts determine the threat is valid, they dispatch alerts and actionable intelligence ZeroEyes’ AI gun detection and intelligent situational awareness software layers onto existing digital security cameras. If a gun is identified, images are instantly shared with the ZeroEyes Operations Center (ZOC), the industry’s only U.S.-based, fully in-house operation center, which is staffed 24/7/365 by specially trained U.S. military and law enforcement veterans. If these experts determine the threat is valid, they dispatch alerts and actionable intelligence — including visual description, gun type, and last known location — to local law enforcement and school security as quickly as 3 to 5 seconds from detection. Cutting-edge technology "It’s inspiring to see schools like NESD take decisive action to enhance campus security,” said Mike Lahiff, CEO and co-founder of ZeroEyes. “We are thrilled to support their mission to protect students, faculty, and staff. Our collaboration reflects a shared commitment to leveraging cutting-edge technology to help mitigate potential tragedies and save lives."
As a real estate development firm’s facility was nearing completion, the firm identified potential concerns with limitations in the facility’s control infrastructure. Before the building reached full occupancy, the firm engaged with Wesco Anixter’s entroCIM team for a comprehensive cybersecurity and use-case audit. As a result, the facility pivoted to a cloud-hosted instance of the entroCIM platform to deliver on the organization’s lofty vision for a truly connected space. Solution Constant commissioning with site-specific scripting means operators know the moment The entroCIM platform helps bring their vision to life among operational technology as well; disparate technologies with unique communication protocols come together in a single interface, providing stakeholders with mission-critical actionable insight. As all commercial real estate of this type has changed in the past several years, entroCIM has changed with it, offering direct, API-based connection to detailed predictive utility data to leverage the site’s flexibility in maximizing efficiency. Constant commissioning with site-specific scripting means operators know the moment a system begins to show signs of decline. Since initial deployment, the depth of actionable insight through analytics has more than doubled, with more than 130 analytical rules running continuously to give operators the upper hand in the management of occupant comfort, energy efficiency, and proactive maintenance Scope Cloud-based entroCIM license access Dashboarding and graphics Analytics and reporting Preventative maintenance Investigation API-based utility integration Commissioning Global remote access Use-case gap analysis Cybersecurity audit New construction consulting Subject matter expert support Project stakeholders C-suite IT Organization-level engineering Site-level mechanical Site-level engineering Tenant program management Communication protocols BACnet Modbus Integrated services Automated Logic Semco Lutron Siemens Honeywell York
Jacksons Fencing has successfully completed the installation of an innovative sound reduction barrier and security fencing system for Matthews Haulage at their Essex logistics facility. The project, completed in 2024, was designed to address the haulage company's dual needs for noise control and site security, providing a durable, compliant, and efficient solution. Robust security Matthews Haulage, a long-established player in the transport and logistics sector, sought to minimize noise pollution generated by its 24-hour operations while protecting its valuable assets. With residential areas and commercial properties nearby, the Essex facility required a solution that not only adhered to stringent environmental noise regulations but also provided robust security against unauthorized access and theft. Expertly engineered The barrier was engineered to meet the dual requirements of sound absorption and site security Jacksons Fencing installed a 3.5 meter high, 141.5-meter-long absorptive sound reduction barrier around the perimeter of the warehouse. The barrier was engineered to meet the dual requirements of sound absorption and site security. Using advanced sound-absorptive materials, the barrier effectively dampens high-frequency noise from haulage and loading activities, preventing it from reaching nearby residential and commercial areas. This noise reduction is crucial in maintaining Matthews Haulage’s compliance with local environmental regulations, helping to reduce noise complaints and strengthen relations with the surrounding community. Certified safety Given its proximity to a busy road, Jacksons Fencing ensured that the barrier met UKCA standards; it is certified as a whole system that complies with strict safety and performance standards necessary for the mitigation of road noise. This UKCA marking guarantees the long-term reliability of the barrier under challenging conditions, including traffic-induced vibrations and environmental stressors, reinforcing Matthews Haulage’s commitment to regulatory compliance and operational resilience. Combining noise reduction with security Beyond noise mitigation, the 3.5-meter-high barrier functions as a robust security fence Beyond noise mitigation, the 3.5-meter-high barrier functions as a robust security fence. Its solid construction provides a strong physical deterrent against unauthorized access, effectively preventing trespassing, theft, or vandalism. Additionally, the height and opacity of the barrier afford the facility excellent privacy and concealment, reducing the chance of opportunistic targeting by blocking the visibility of assets such as vehicles and cargo. Unique requirements Peter Jackson, Managing Director of Jacksons Fencing, commented on the project’s success: "The acoustic barrier we installed is a reflection of our commitment to providing bespoke solutions that not only meet regulatory requirements but also enhance the operational performance of our clients." "Our team worked closely with the client to ensure the barrier met their unique requirements, from regulatory compliance to site-specific security needs. It’s a prime example of how tailored solutions can make a real impact on both operational efficiency and community relations."


Round table discussion
As cutting-edge trends go, convergence has been around for at least two decades. The meaning has shifted over the years, and if anything, the idea of convergence has gotten even more aspirational. Unfortunately, the widespread use of the term has also paradoxically undermined its meaning and power. However, today's concept of convergence has matured to provide new levels of benefit for security professionals. We asked our Expert Panel Roundtable: How has the meaning of “convergence” evolved in the security market? How are systems today more converged than ever?
The security marketplace has its share of buzzwords, which are words or phrases that become popular and widely used in a specific industry. Buzzwords can be useful for conveying complex ideas quickly, but they can also be misused or misunderstood. Within a specific industry, such as security, buzzwords can create a sense of shared understanding and belonging. We asked this week’s Expert Panel Roundtable: What new buzzword have you heard, and what does it mean for the security industry?
By all accounts, technology development is moving at a rapid pace in today's markets, including the physical security industry. However, market uptake of the newest technologies may lag, whether because of a lack of clear communication or not enough education of potential customers. We asked this week's Expert Panel Roundtable: How can the industry do a better job of promoting emerging technologies in physical security environments?
Products
White papers
Preventing Loss, Securing Assets
Download
Intelligent Video Security Solutions
Download
12 Questions To Ask Your Access Control Provider
Download
The Borderless Control Room
Download
Preparing Your Organization With Quality Situational Awareness
Download
Making Your Surveillance Cyber Secure
Download